Captive Portal: Restrict Ports for Allowed IP Address?
-
Hi everyone,
We have a public Captive Portal configured in pfSense.
Before authentication, we need to allow access to a NAS (for PXE boot and file retrieval), so we've added its IP to the "Allowed IP Addresses" list in the Captive Portal configuration.The issue is: once an IP is added to "Allowed IP Addresses", all ports and protocols to that IP become accessible — which is too permissive for our needs.
 Is there a way to define "Allowed IP Addresses" with restrictions by port and/or protocol?
Is there a way to define "Allowed IP Addresses" with restrictions by port and/or protocol?We only want to allow specific traffic (e.g., TFTP/UDP 69, HTTP/TCP 80) to that IP before authentication, while still blocking everything else.
Thanks in advance for your help or ideas!
-
I've added my NAS IP, 192.168.1.33, :
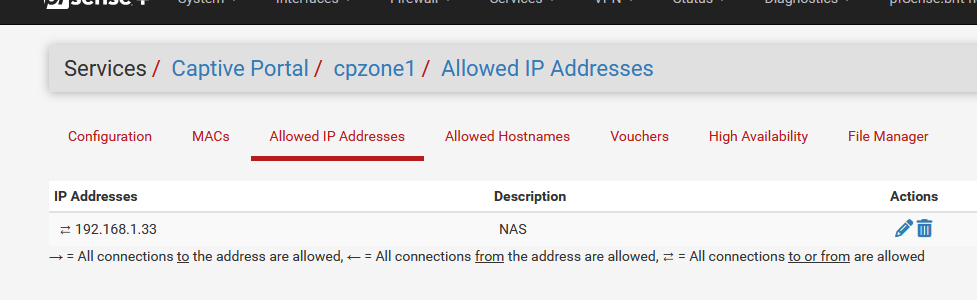
Btw : My captive portal lives on 192.168.2.1/24
I had to add a pass ping rule (at the top) :
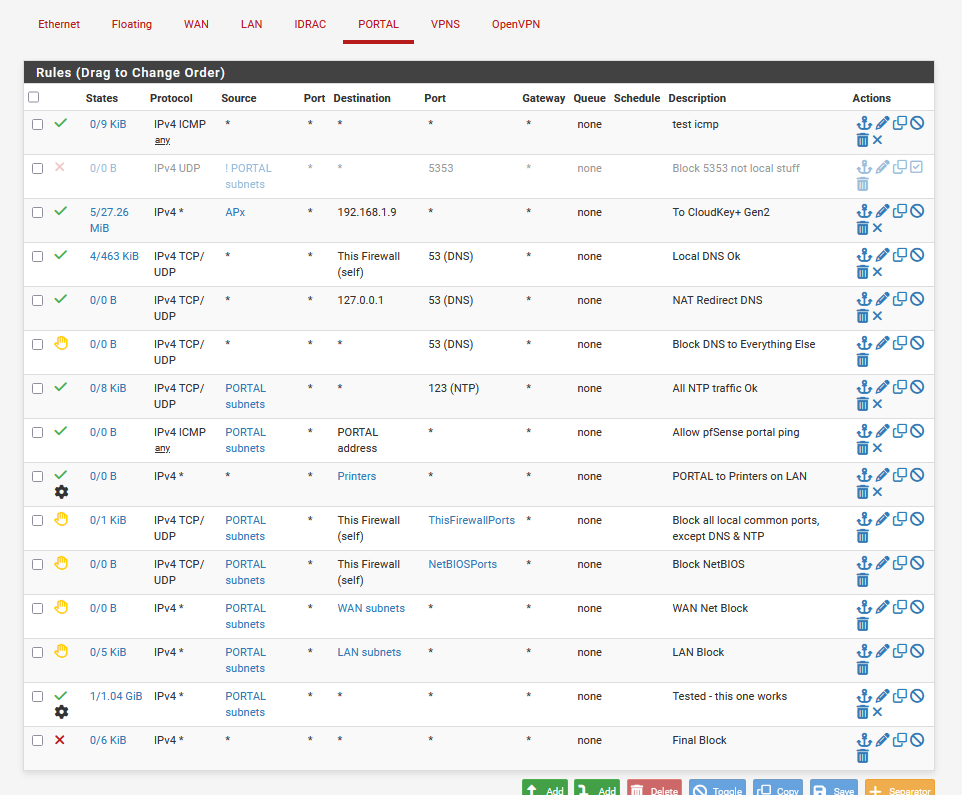
as I the third line from below blocs all traffic going to LAN so I had to punch a hole for ICMP.
When adding the rule, a portal connected
@rds25 said in Captive Portal: Restrict Ports for Allowed IP Address?:
Is there a way to define "Allowed IP Addresses" with restrictions by port and/or protocol?
So, for me :
Is there a way to define "Allowed IP Addresses" with restrictions by port and/or protocol?
Yes.
-
Thanks for your reply. However, in your screenshot, you added "192.168.1.33" in the "Allowed IP Addresses", which means that even before being officially authenticated on the hotspot, it's possible to access all ports of the "192.168.1.33" address.
Moreover, it clearly states: "All connections to the address are allowed", which confirms that there is no filtering — all ports, from 0 to 65,535, are open to that IP.
As far as I understand, IPs listed under "Allowed IP Addresses" completely bypass the rules defined in the "PORTAL" tab.
So my question remains:
How can filtering be applied before user authentication — especially for IPs listed under "Allowed IP Addresses"?Also, if I connect to your hotspot (without a Wi-Fi password, for example) and I don’t have any login credentials, technically, if I run an Nmap scan on "192.168.1.33", I would see all the open ports — and potentially exploit them.
-
This post is deleted! -
@rds25 said in Captive Portal: Restrict Ports for Allowed IP Address?:
As far as I understand, IPs listed under "Allowed IP Addresses" completely bypass the rules defined in the "PORTAL" tab.
That's what I initially also thought.
This is the portal rule that blocks all portal-to-LAN IPv4 traffic :
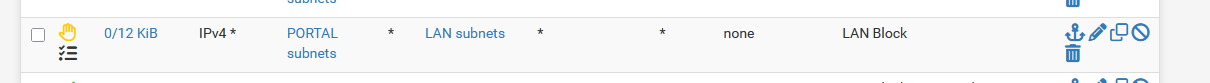
I connected my phone to the portal, it got 192.168.2.10, and then I started to send ICMP packets to 192.168.1.33.
While doing so, I was packet capturing on my portal interface for ICMP traffic, send by 192.168.2.10, my phone.
I saw the packets, ICMP requests, coming in - but no answers logged.
At the same moment, I was :[25.07.1-RELEASE][root@pfSense.bhf.tld]/root: tail -f /var/log/filter.logand I saw :
... <134>1 2025-09-02T09:15:05.661320+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,271,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,1564 <134>1 2025-09-02T09:15:06.661321+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,52479,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,1664 <134>1 2025-09-02T09:15:07.661337+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,19671,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,1764 <134>1 2025-09-02T09:15:08.661389+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,9817,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,1864 <134>1 2025-09-02T09:15:09.661321+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,17809,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,1964 <134>1 2025-09-02T09:15:10.661336+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,16478,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,2064 <134>1 2025-09-02T09:15:11.661399+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,17854,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,2164 <134>1 2025-09-02T09:15:12.661402+02:00 pfSense.bhf.tld filterlog 75062 - - 164,,,1655045805,igc1,match,block,in,4,0x0,,64,34051,0,none,1,icmp,84,192.168.2.10,192.168.1.33,request,63694,2264 ...which tells me that my firewall rule (shown above) was blocking my ICMP requests (to 1492.168.1.33).
GUI equivalent :
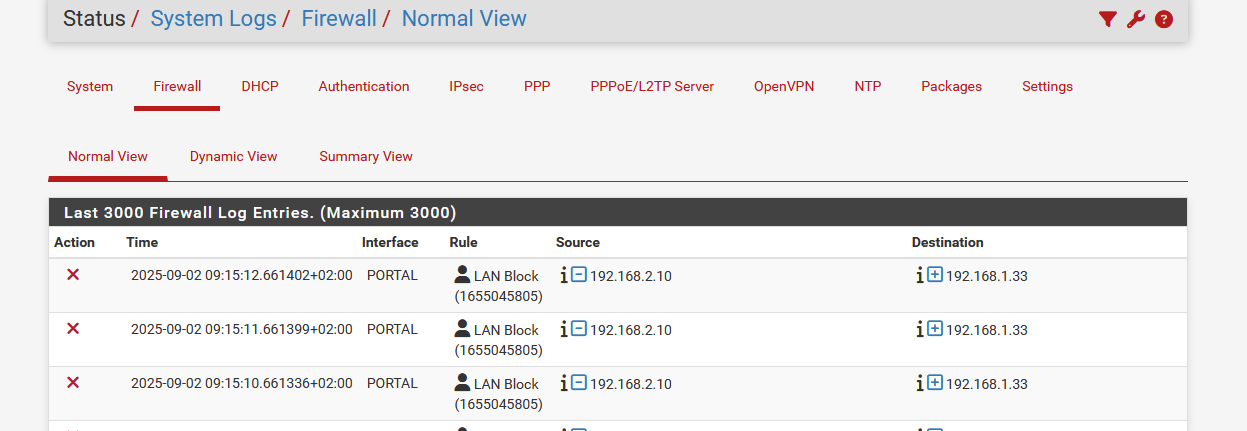
The firewall log label is "LAN Block" so I knew which firewall rule was blocking, the one I showed above.
This really makes me think that even when you Allow an IP address, the portal's GUI firewall rules still apply.
As soon as I activated this first portal's firewall line :
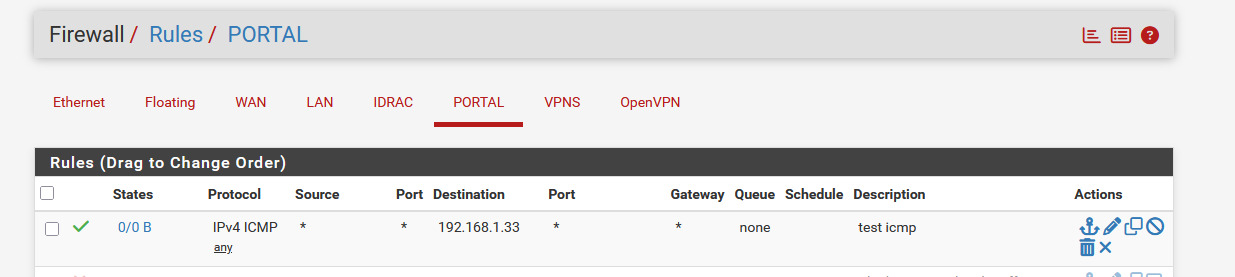
which allows ping packets from the portal interface to go to my LAN, 192.168.1.33, my NAS, ping packets came back / the NAS was replying.