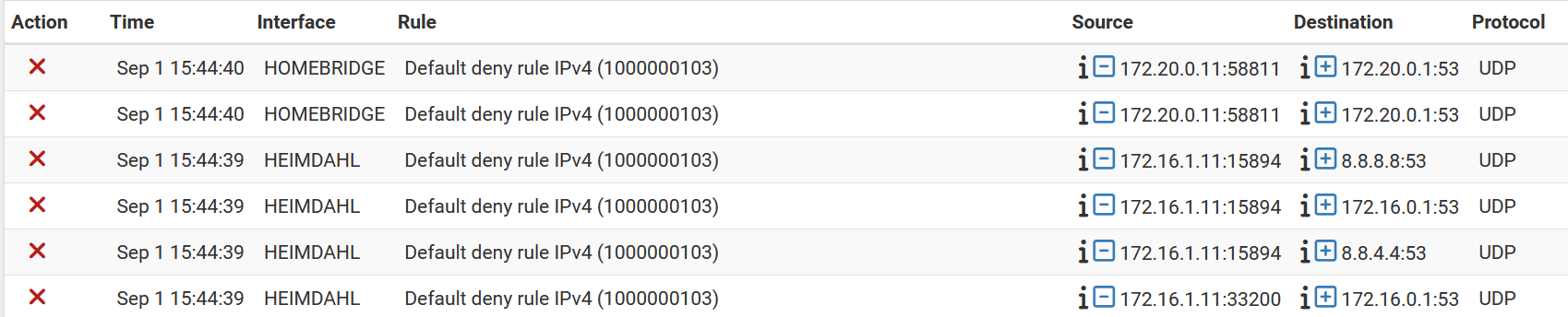
pfSense blocking all DNS
-
NSlookup on the server succeeds instantly.
It fails at clients. -
I found a problem experimenting with rules on the bridged interface.
It seems the HOMEBRIDGE_subnets network alias does not work when creating rules. Applying rules to this appears to have no effect.Use any/* does work.
I'm new to pfSense, but this looks like a bug. -
Something else.
The logs are showing an entry from the LAN interface which is a member of the HomeBridge bridged interface. Is this normal? Shouldn't the log show the traffic coming from the Bridge not the LAN interface?Firewall Log showing entries for both LAN & HomeBridge interfaces.
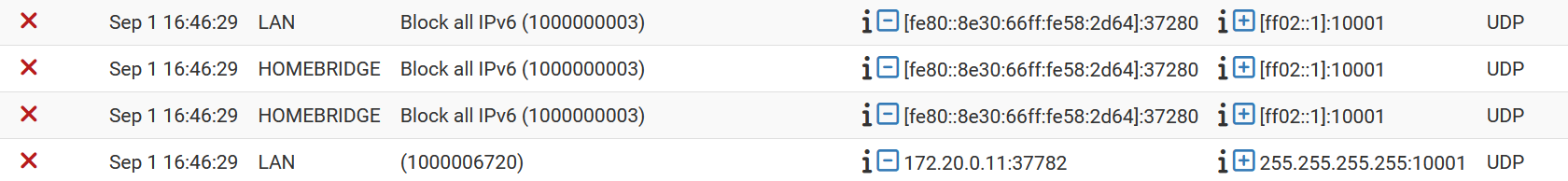
Bridge Definition
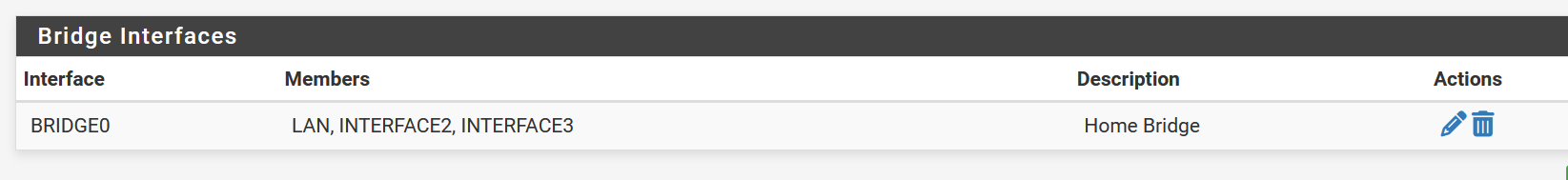
The IP address is assigned on the Bridge Config page.
Also, I have IPv6 turned off. Why are these logs showing this traffic?
-
The firewall is simply unstable.
Integrated network aliases don't function.
The firewall simply doesn't work.
Rules to allow all on specific ports appear to be the only type of rule that work consistently. Attempting to narrow the 'allow' to specific ip addresses or networks fail. User defined and system defined interface-related aliases don't function.This forum is not a good use of my time.
I assume the silence is simply bait to get people to switch to paid support. -
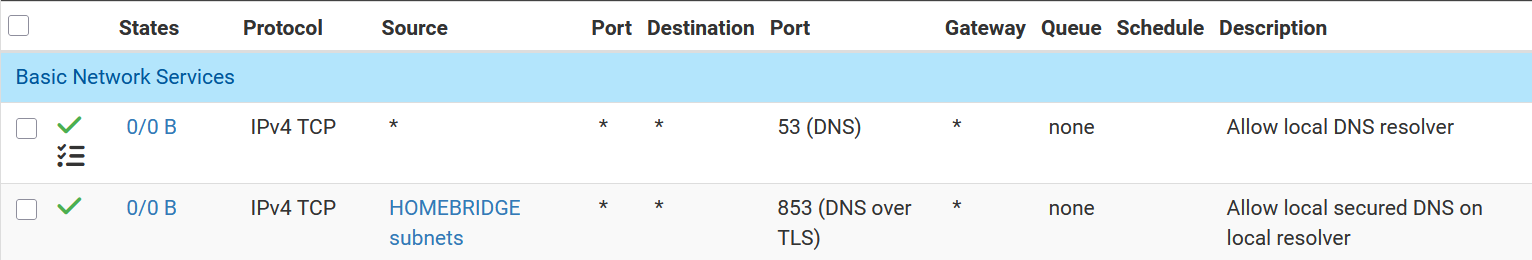
@DouggaDit allow UDP in addition to TCP
-
Nice catch.
Thanks! -
A new rule in pfSense defaults to TCP protocol, it catches everyone. It's just safer than "any" I assume.
-
@DouggaDit said in pfSense blocking all DNS:
This forum is not a good use of my time.
I assume the silence is simply bait to get people to switch to paid support.In all fairness this was a long holiday weekend in the US.
Phizix
-
@Phizix Ahhh I don't have the reputation point required to upvote this comment. Someone lurking is an asshat.
-
@DouggaDit said in pfSense blocking all DNS:
The firewall is simply unstable.
Integrated network aliases don't function.
The firewall simply doesn't work.
Rules to allow all on specific ports appear to be the only type of rule that work consistently. Attempting to narrow the 'allow' to specific ip addresses or networks fail. User defined and system defined interface-related aliases don't function.This forum is not a good use of my time.
I assume the silence is simply bait to get people to switch to paid support.Safe to file this one under did-a-derp-and-kept-digging.