Big issues related to Firewall logging.
-
Two perhaps related serious issues
- Today I had to dig into a problem needing the firewall logging for that. I noticed that there was no firewall logging. It had stopped !!! (all ready for a couple of days)
After clearing the alarm log the logging did work again. Note that I have a lot of ram and disk space in my system.
- Perhaps related and very very annoying (complained already a couple of times) , is that pass rules without logging do behave like block rules with logging. Which is I keep saying that is really ridiculous.
And that issue is causing many thousands of alarms and perhaps it is reason of the problem mentioned above.
below an very often occurring example of the mentioned problem.
Note that I am running the latest plus version.
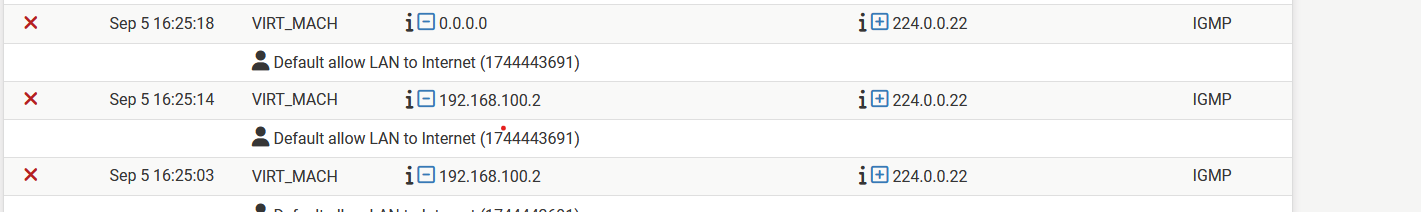
-
@louis2 #2 is not a problem per se…IGMP/options drops are logged now.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html#packets-with-ip-options
You can create a rule to match and not-log them.
-
@SteveITS said in Big issues related to Firewall logging.:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html#packets-with-ip-options
Steve,
I tried a lot but the behavoir is definitively not ok and in my opinion disgusting.
I tried to stop this logging adding extra rules in front of the rule generating the logging. Nothing stops it!
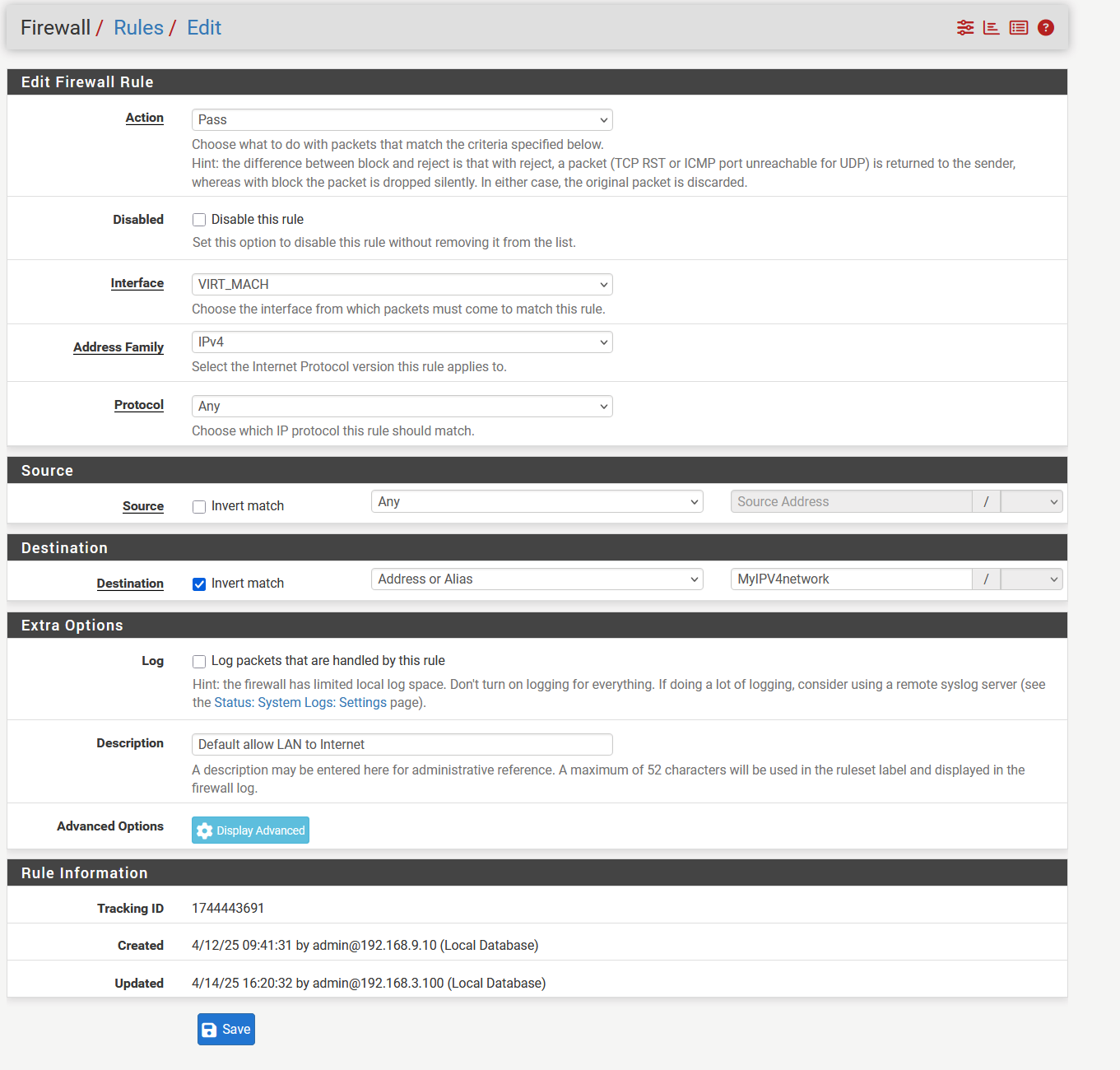
As you can see three rules:
- a rule to block IGMP with options set
- the same rule without options set
- the >>pass rule without Logging<< generating the logs .....
IMHO nothing justifies this behavoir !!
-
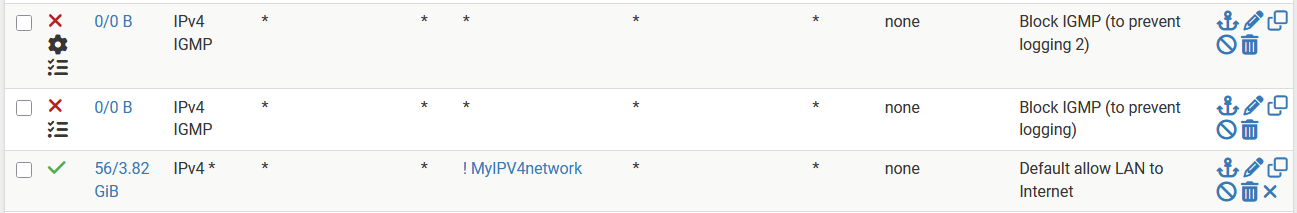
@louis2 in your screenshot both IGMP rules have “ Log packets that are handled by this rule” checked.
It should be protocol IPv4 IGMP, interface LAN, log unchecked, and that’s it.
-
Steve ... you overlooked something ....
It are not those rules which are causing the logging, it is the rule at the bottom which is causing the logging !!!
I now even add four rows above that rule trying to stop the logging. All those rules have logging on because I want to see it those rules are triggered.
They are not as you can also see from the counters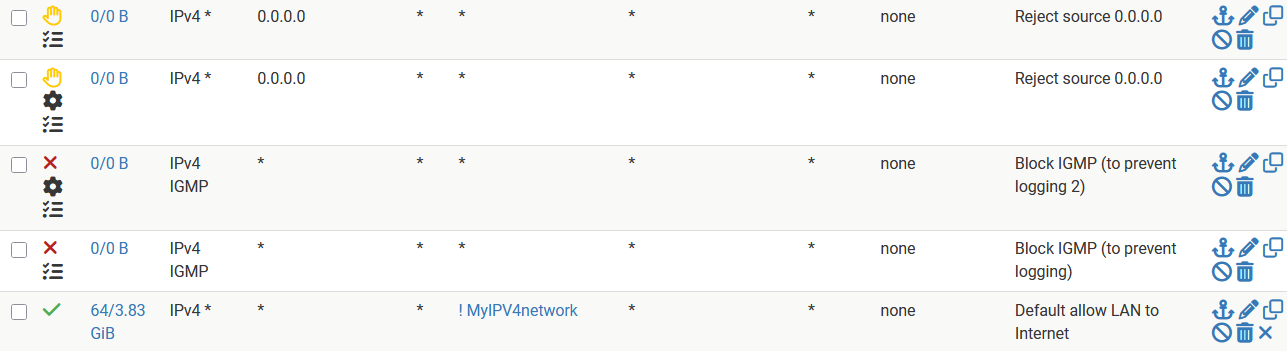
-
@louis2 please show a screen cap of the rule.
We created a not-log rule on all routers we manage. The behavior change was new in 24.03 or thereabouts.
-
-
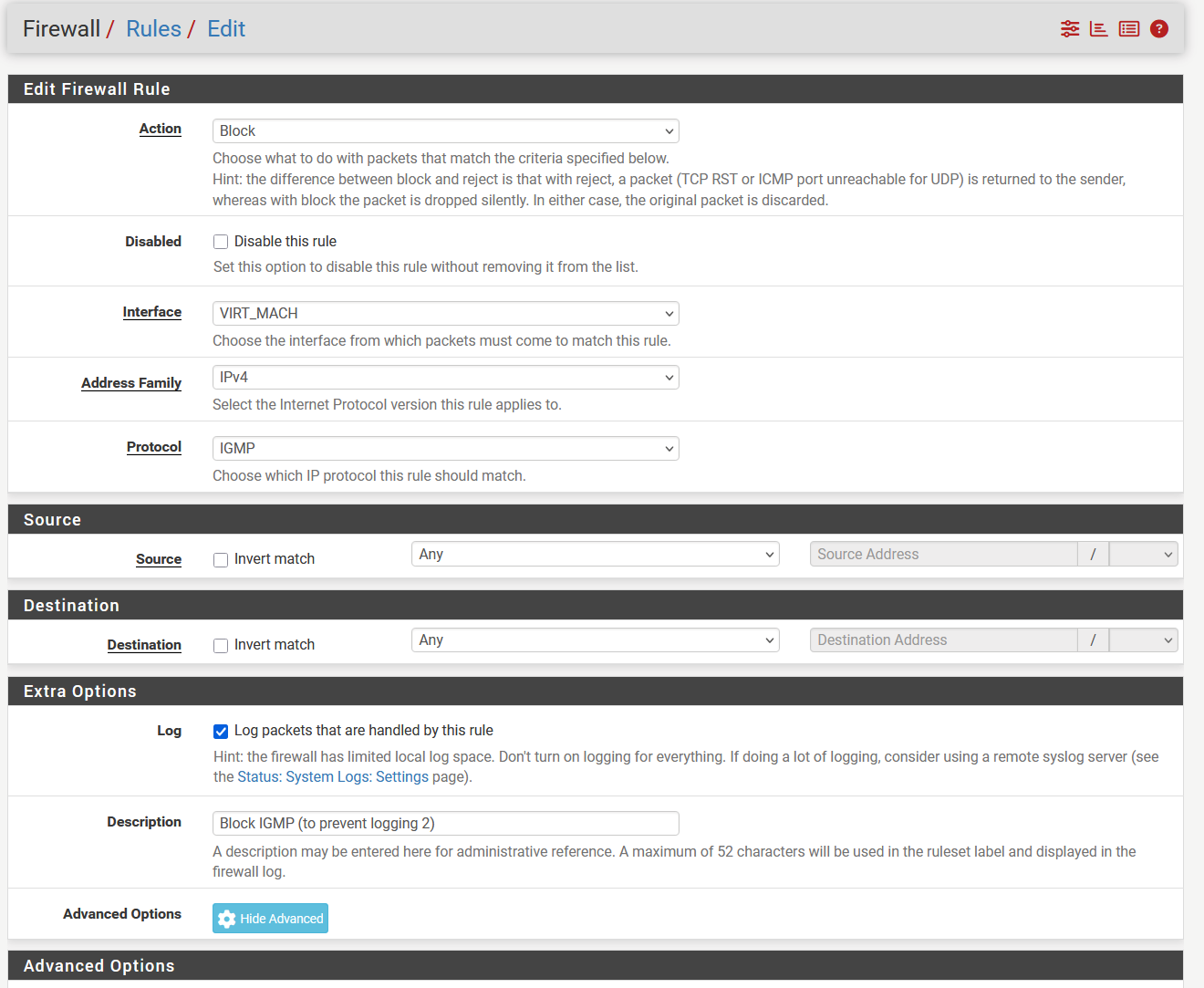
@louis2 The IGMP one.
-
Below the rule with advance options set. The other one is identical without the advance options
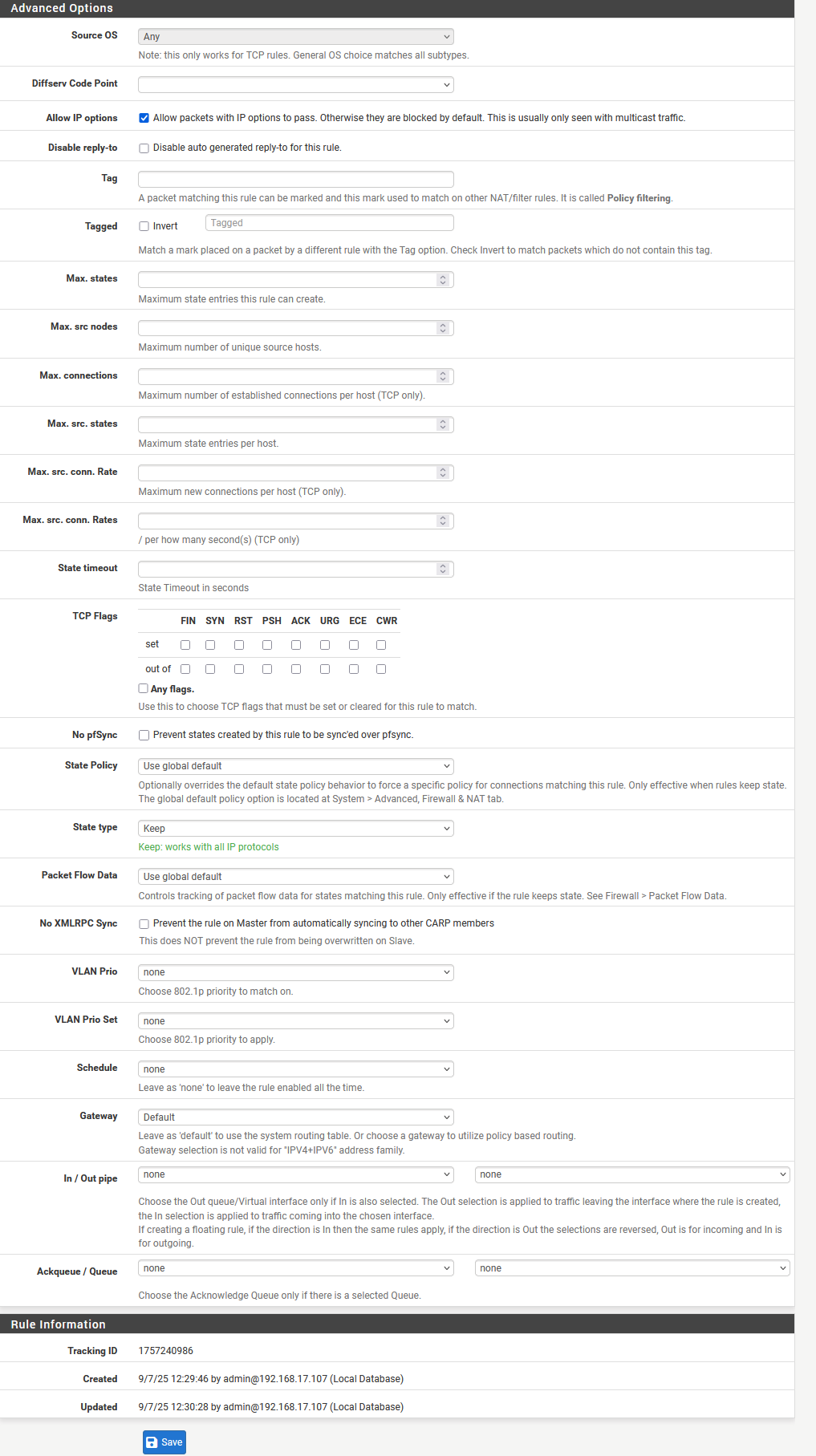
-
I leave home for a couple of hours, will respond afterwords if required
-
@louis2 Try a Status/Filter Reload to ensure they're loading?
here are mine:

no advanced anything set:
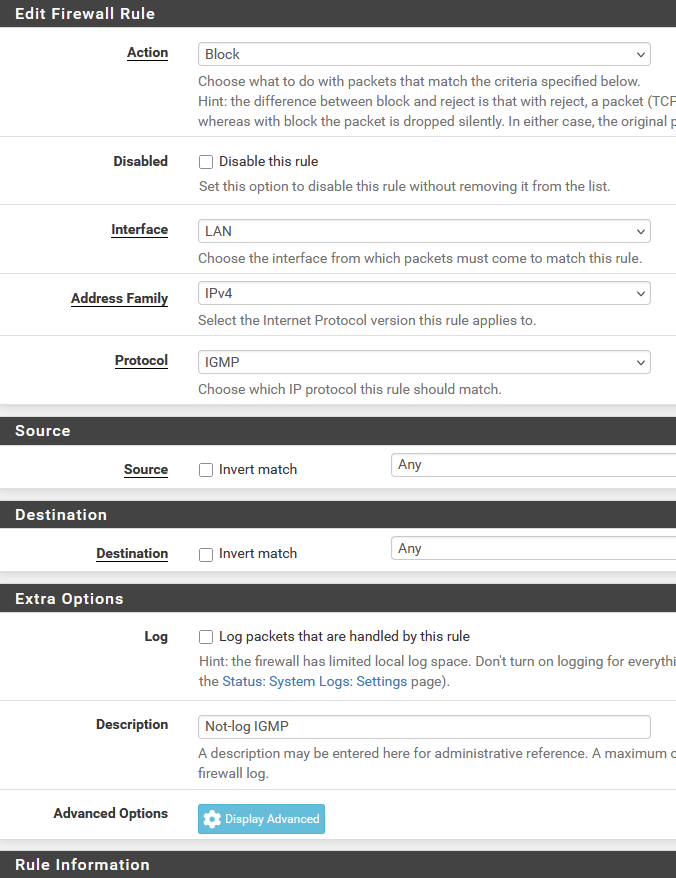
-
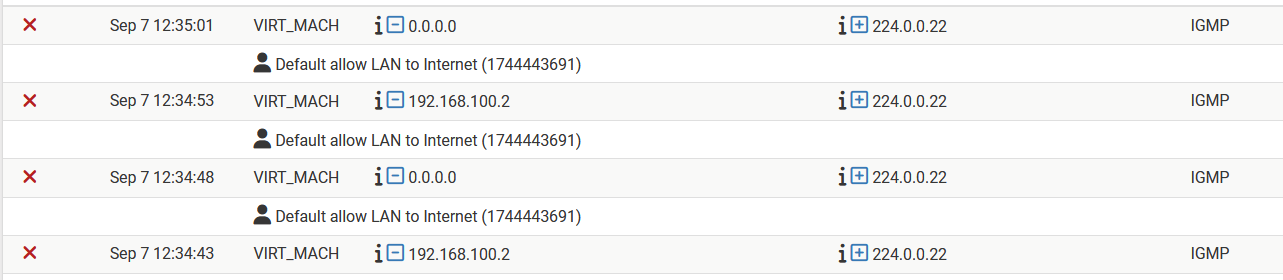
Hum ... I did reboot the FW ..... which changed the behavior .... what should not be the case ....
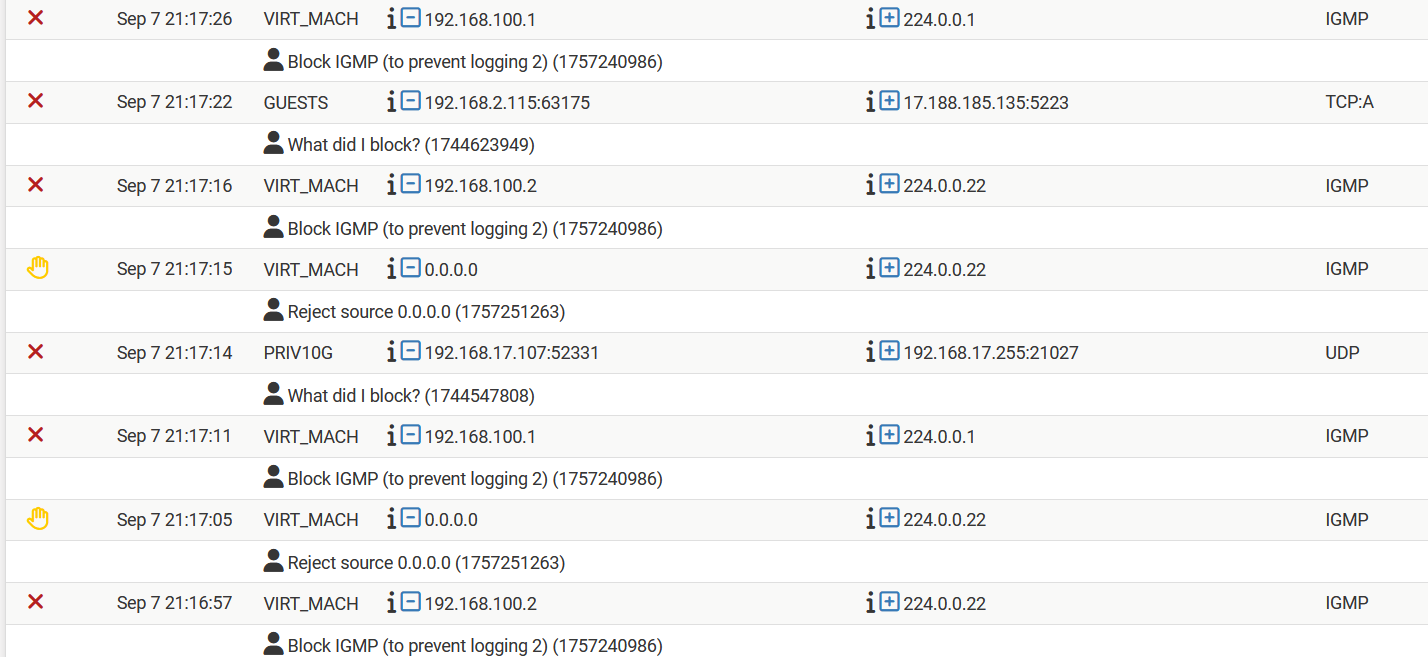
The first rule in my 'rule-group' blocks the packet now
And a unkown rule generates a 'reject source' message ..
The whole thing is bizar in multiple ways .....
note: alias MyIPV4network = '192.168.0.0/16'