Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate
-
So about to deploy and OpenVPN Setup on PFSense 2.8.0. Everything is working great in my tests and the configuration I have seems to be correct. I have set my users up by sending out the OpenVPN client profile using the OpenVPN Client Export utility and they are in the process of installing this now.
I have this set up using a Certificate signed by a Certificate broker and third-Party CA. I have imported the CA, the Intermediate CA, and the user certificate files into PFSense. I have the OpenVPN server setting enabled "Use a TLS Key" and had PFSense generate a client key. The Open VPN client export utility exports a profile file that includes two CA certificates (assuming the CA and Intermediate CA I imported into PFSense) embedded in the profile file. All this works fine.
I'd like some clarity on what this "Use TLS" Setting is doing. I think its essentially generating a client certificate and key from the third-party CA certificates I imported into PFSense, and then including these CA certs and key into the clien profile. When a client connects it then uses this "pre-shared key" to validate both the client and that the server the client is connecting to is the actual server it thinks its connecting to. I additionally am using 2FA with FreeRADIUS to further secure users logging into the service.
So do I have this correct with regards to what the "Use TLS" setting is doing?
Additionally, When I change the client certificate I am using, as long as I don't change the CA certificate (and ensuring the CA certs are valid and match up with the new user certificate so the cert chain is intact), I should NOT have to change anything in the OpenVPN client profiles (i.e. change the certificates and key in the file) to have these clients continue working. The key is generated from the CA cert and as long as that does not change, I shouldn't have to do anything with the client profiles when I install a renewed certificate and use it for the OpenVPN server configuration in Open VPN other than import the new certificate and change the OpenVPN server configuration to begin using it. Setting I am talking about:
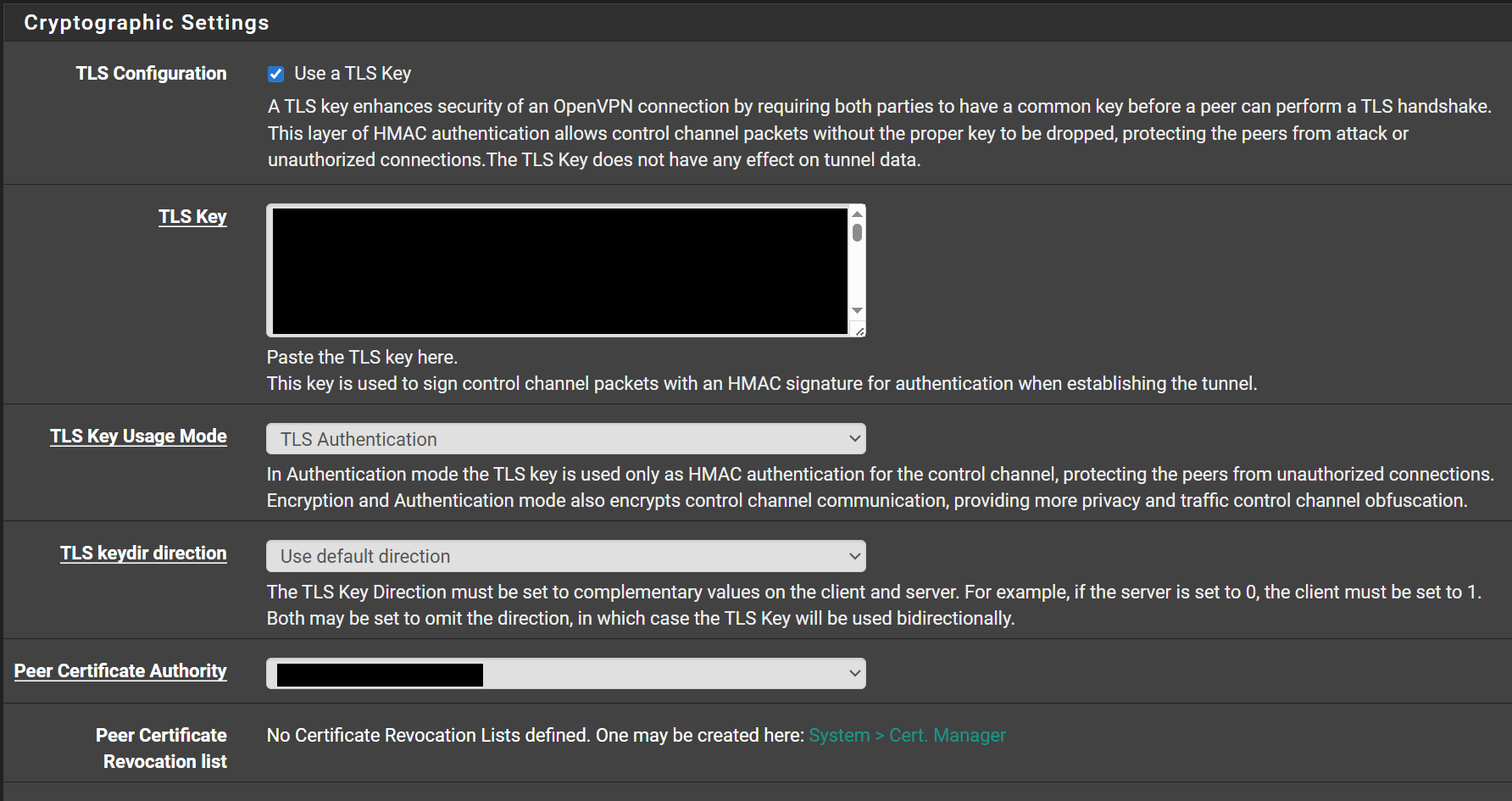
Thanks in advance for setting me straight here.
-
@rfranzke said in Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate:
I have this set up using a Certificate signed by a Certificate broker and third-Party CA.
Normally, you don't need a certificate broker to create a certificate use by one or more OpenVPN clients.
Certificates created by, for example Letsencrypt, are valid for 90 days max.
Other CA brokers : 1 year ? That's to tedious to handle.Create your own "10 years lasting" CA in pfSense.
When done, create your OpenVPN Sever certificate based upon this CA in pfSense, and set up your OpenVPN server what this cert.
Now, for every OpenVPN client, create a dedicated certificate based up the certs mentioned above.When you have to renew these certificates (after 10 years ^^) you have to redeploy for every OpenVPN client a new OpenVPN client config (that contains the new cert).
-
@Gertjan said in Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate:
Normally, you don't need a certificate broker to create a certificate use by one or more OpenVPN clients.
Agreed here. I already have this certificate for other things so I also used it for this VPN because I have to renew it anyway. I don't mind swapping the certificate out every year but want to make sure I understand what I need to do with the client profiles when I do. When I say 'user certificate', understand what I mean here is the certificate issued by my third party CA (of which the CA certificates are installed in PFSense). I am not creating a certificate for each user such that they have a unique certificate for just them in their profile like you can set up. I just have the TLS CA and key in the profile common to all users that to my understanding allows them to even begin making the connection to the VPN. If a client has a key, then it can negotiate the connection and authenticate with the PFSense box using the User credentials given to the clients. Thats my understanding anyway.
If I need to generate a new TLS key (and thus a new client profile including them) each time I replace/renew the certificate issued by the CA, then I would want to do what you are suggesting and set this up with a self-signed CA with a long expiration date or perhaps move to using Let's Encrypt for this setup. I am not sure how the Let's Encrypt thing works with the OpenVPN server and the clients with key embedded profiles. Assuming if the cert changes with Let's Encrypt this should not cause a need for any changes on the client side. But again I am not sure I understand how this works. Thanks for replies. -
@rfranzke said in Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate:
common to all users that to my understanding allows them to even begin making the connection to the VPN
Imho, that like creating a user (user name + password) on pfSense, and share this user among all connected clients.
Afaik, that might work, but 'nobody' should do this.
Every user should OpenVPN ovpn file with an unique certificate, created solely for that user.Even the big CA players rotate their "CA" certificates often, like every 3+ years or so.
Certificate that you get (buy) from them most often integrate a host name, not a "user name". The first is needed/usefull for domain names (https and the like). OpenVPN doesn't use/needs host names to compare against. It needs a user name.Using "Let's Encrypt" for OpenVPN access certificates : it can be done .... true. And guess what, no one does so ^^.
Look here, and locate all the OpenVPN videos. They are old, but actually still very valid. You'll find the exact reason why your own CA (and other certs) are best for OpenVPN usage.
-
Thanks for the reply here. Just want to make sure I am clear what I am doing. With OpenVPN setup, you can authenticate clients using a certificate or authenticate them using a username and password, or authenticate them using both methods. I am authenticating them using a username and password via FreeRADIUS. I further am validating the connections using TLS to secure the initial connection and only allow users to connect to my VPN service if they have a profile with the proper CA certificate embedded in the profile. I don't generate a per user, user certificate as I authenticate any user trying to connect via a username and password. In this way I can have a single profile for all users. They still have to have their unique username/password pair to login and gain access to the VPN. So the certificate is somewhat secondary. If certificate auth was my only auth method here, then I would generate a unique certificate for each user. But it isn't. The way I understand this to work is the key and third-party CA cert embedded in the profile acts like a pre-shared key just to allow a client to even begin a connection. Similar to an IPSEC tunnel using pre-shared key auth. Maybe I'm wrong there. I am not really generating a username and password and then sharing it with my users like you mention. They still have to auth the session using a username and password uniquely.
I am just trying to confirm that if I change the SSL certificate being used for the OpenVPN server in PFSense from my provider if I will have to change anything in the client connection profile if the CA cert is not changed. I don't think I would but need confirmation. I am open to me doing this 'wrong' at the moment but if I need to pivot I want to do so before I deploy this solution to limit impact to users. Thanks for replies.
-
@Gertjan said in Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate:
that like creating a user (user name + password) on pfSense, and share this user among all connected clients.
Afaik, that might work, but 'nobody' should do this.So as a result of your not so subtle suggestion, I looked into and created unique certificates for each user, and tied these certificates to the FreeRADIUS server user account. The last bit was not so obvious to me but discovered to do this you add the FreeRADIUS username to the description field of the certificate when I created it. For whatever reason this ties the cert to the user. Then when you enable User Auth + TLS in the server mode, you can now export the ovpn file with their certificate for each user. Got this working today.
Now hoever the static IP I am having FreeRADIUS assign to each user works when they first log in but gives a different IP address when it reconnects from being disconnected. No idea why that would occur. Seems like the server disconnects due to inactivity and then the client reconnects automatically. Despite being 2FA enabled, it seems to auth correctly so not sure how thats happening but when it does this it gets a new IP address different from the one configured in FreeRADIUS for the user. I set the inactivity timeout for 3 days to counter that as it was set to 300 seconds. Have a few days to test this and see if its gonna work correctly. But if this works I should not have to do anything with the cert renewal as the current CA/cert doesn't expire until 2035 and some other clown will be handling this by then.
Still would appreciate an answer on if I keep the same CA will I have to generate a new TLS key for my users if I renew/replace the certificate being used for this VPN.
-
@rfranzke said in Open VPN with PFSense 2.8.0 What to Do with VPN Client Profiles When Replacing Expiring Certificate:
Still would appreciate an answer on if I keep the same CA will I have to generate a new TLS key for my users if I renew/replace the certificate being used for this VPN.
This one :
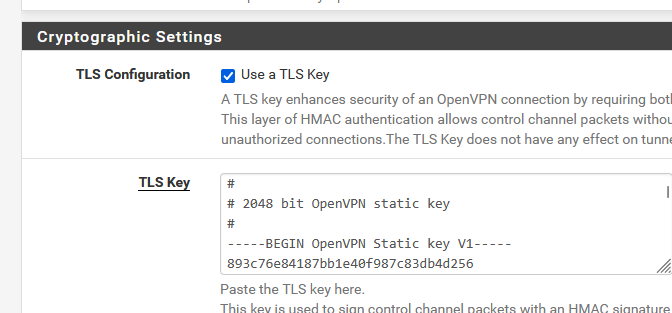
?
Afaik, that key isn't certificate related.
-
@Gertjan Thanks for the reply. Based on your input I have switched to using cert auth with passwords and now have certificates created using a self signed CA on the device I created just for this purpose. Sent all my users their individual files. Should be better than what I was doing. Thanks for the input.
-
Certificates for authentication are fine being self-signed with whatever validity you assess is good for you.
The VPN-endpoint (the public address) should have a real public certificate. The CA-chain for this ertificate is part of the profile, so there is a caveat that you must check the CA-chain for changes when you renew the public endpoint cert. This however can be considered a rare event in a sense, and usually you get heads up when roots (very rare) and/or intermediates (more likely but still rare) change. If the chain changes, you must provide new profiles to all users, which can be a PITA of not prepared.