Multiple Static Assigned Addresses FreeRadius For OpenVPN
-
Hello all,
Recently deployed a new PFSense setup with OpenVPN and FreeRadius to replace my Cisco FTD Anyconnect Device. The deployment went very smooth and so far PFSense has done fantastic.
I did run into an issue with OpenVPN and FreeRadius I'm not sure how to handle. I initially set this up to assign static addresses to each user using FreeRadius User config section for Each user:
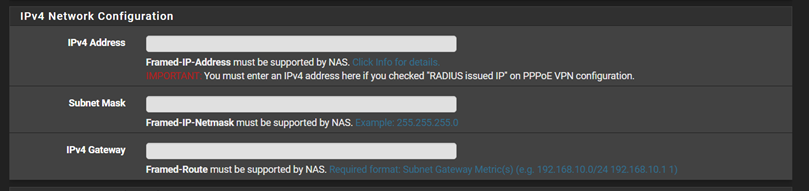
The idea here was so I can add ACLs to control what user can go where when connected to the VPN. This worked fine initially until........I noticed that if a user tries to connect to the VPN multiple times, FreeRadius tries to assign the same configured static IP address each time, which breaks the initial VPN session for the user. My fix for the deployment was to simply only allow one session for each user. But we have certain users who need to have multiple sessions going at once for dev testing code while looking at logs, etc.
So my question here is there some way to both assign a static IP address for each user session using FreeRadius Config UI? Maybe a comma sep list of static IP addresses to assign there or using some other address assignment method (client overrides or something).
End result I am after is to have user1 be able to connect to the VPN up to 3 times and get a different static assignment for each session. Then user2 can connect up to three times and get a different set of known static IP addresses for each session. Like this:
user1 session1 static IP 10.10.50.2/24
user1 session2 Static IP 10.10.50.3/24
user1 session3 Static IP 10.10.50.4/24user2 Session1 Static IP 10.10.50.5/24
user2 Session2 Sttic IP 10.10.50.6/24
etc.....Hopefully that makes sense. Thanks in advance for replies.
-
I thought about this some and I think I might do this a different way. I have a /24 allocated for my OpenVPN setup. So routing on the network is routing the entire /24. What I can do though is split the /24 into two /25's, with one allocated to normal users and one allocated to Admins. I'll assign the Admins /25 statically via FreeRADIUS (Admins need only a single connection to OpenVPN at a time because they are not ridiculous). I'll assign the normal user /25 dynamically. Then I can set up Rules to allow the proper traffic for both groups. The way I have seen the dynamic IPs get allocated is OpenVPN seems to allocate addresses lowest to highest in the range and then start back at the beginning as users disconnect/reconnect. So I don't think the two networks will ever overlap in terms of allocating them. We have some 20 users so there is no fear the dynamic range ever getting allocated into the 'static' /25 range with the way dynamic addresses seem to get allocated. Maybe this would work?
-
@rfranzke Probably it won't overlap, but you are departing from the original idea of allocating a specific ip to a specific user, which might be of use elsewhere.
(maybe not in your specific use case)Instead of splitting address space and hoping, create another openvpn instance on e.g. 1993
and just connect your admins there. -
@netblues said in Multiple Static Assigned Addresses FreeRadius For OpenVPN:
@rfranzke Probably it won't overlap, but you are departing from the original idea of allocating a specific ip to a specific user, which might be of use elsewhere.
(maybe not in your specific use case)Allocating a specific IP is better and would be of use elsewhere. I just don't see any way to do it for multiple sessions per user. Either you dynamically assign IP addresses via OpenVPN and allow multiple connections per user or you statically assign addresses and only allow one connection at a time.
A second instance was a thought and probably would be a better idea to split this without worry of allocation overlap via static versus dynamically allocated addresses, but as you mention still gets away from allocating a specific address per user. We only have 20 users at the moment so for a /25 there is a ton of space to work with. I don't see how we would ever clash between the two allocation types. I don't see a need for an Admin user to need multiple OpenVPN sessions going at a time right now, but we have a few more technical users that need to do some specific admin type things which require special access as well as things that might require multiple VPN sessions at a time. It's a unique use case so not sure it would come up. But if there was a group that would come up with a special need requiring a ton of extra IT work, this would be it.
-
@rfranzke since admins are admins, they can just hack themselves another username, like admin01, admin02 and deal with it too.
I wouldn't bother too much with this user class, unless of course they are not admins on pf too.
-
Just me as a PF Admin. These guys wouldn't know the first thing about it so would like to keep them out of even accessing PFSense UI over VPN among other things.
-
So, poking around in docs, seems like maybe the weapon of choice here is the framed-pool RADIUS attribute. Look like you can assign distinct IP pools to clients using this attribute. Anyone know if this attribute is compatible with the FreeRADIUS package that is available for PFSense? Can OpenVPN use this attribute for assigning IP addresses to clients? Anyone done this successfully?