Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work
-
Hello I have been working at this for days and still nothing, I have a netgate 4100 with an Aruba 1930 24 port switch. The goal is to be able to talk from VLAN1 to VLAN10 or VLAN20 so I can upload & download updates & sequences to/from my pc to the Raspberry pi on VLAN20, separate VLAN20 from the rest of the network as when I run a light show I dont flood the rest of the network.
On the 4100 I created the VLANs 10 & 20 thru Interface-Assignments-VLANS, then added them thru Interface Assignments and they show up as VLAN10 on icg0-lan(MGMT) & VLAN20 on icg0-lan(XLights). Then I go to Interfaces XLights check box enable, change description, static IPv4, enter address 192.168.20.1 /24, Save. (Same for MGMT 10 except .10.1) but not focusing on that one right now. Then go to Firewall - Rules - XLights, I have 2 rules, top is Allow LAN address access - Pass - XLights - IPv4 - Any - Source = Any Destination = LAN address. Lower rule Allow All - Pass - XLights - IPv4 - Any - Source Any, Destination Any. Thats it for the 4100.
The Aruba came with VLAN1, I added VAN 10 MGMT & VLAN 20 XLights, untagged on the 2 ports that the XLights devices plug into. On the port that my pc plugs into I tagged VLAN1, and added untagged VLAN10 & VLAN20. I am thinking I have everything setup correctly (of course...) but its not working? Can someone take a look and HELP? If you got this far THANK YOU and Thank you for your Help! -
@dbeaver2471 hey there,
@dbeaver2471 said in Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work:
On the 4100 I created the VLANs 10 & 20 thru Interface-Assignments-VLANS
What about VLAN1? Created that there as well?
BTW it is not a good practice to use vlan1 as data transporting productive vlan...better: either put pc in mngmt vlan as well or create a new one (and make sure to set proper firewall rules).If you use vlan 1 as trunk / uplink VLAN, then vlan 1 (often the native vlan) goes untagged while all others go tagged...
-
@dbeaver2471 said in Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work:
The Aruba came with VLAN1, I added VAN 10 MGMT & VLAN 20 XLights, untagged on the 2 ports that the XLights devices plug into. On the port that my pc plugs into I tagged VLAN1, and added untagged VLAN10 & VLAN20.
I don't know the Aruba switches, but generally:
- a port can only have one untagged VLAN on it, never two or more.
https://arubanetworking.hpe.com/techdocs/AOS-S/16.10/ATMG/WB/content/common%20files/exa-tag-untag-vla-por-ass.htm - how have you configured the port that connects the switch and pfSense (trunk port)?
- What traffic from which VLAN do you want to see on the PC?
- the two XLights firewall rules: if you use the second rule (any-any), you don't need the first since the.
- I would leave the Source=Any - Destination=Any until you configured the VLANs correctly
- a port can only have one untagged VLAN on it, never two or more.
-
@dbeaver2471 said in Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work:
n the port that my pc plugs into I tagged VLAN1
That is almost always going to be wrong.. If your tagging vlan 1, I can pretty much assure you doing it wrong. Especially if your plugging a pc into that port.
pfsense - 1 U, 10T, 20T - switch - ports you want devices in either 1, 10 or 20 - all would be untagged.
Untagged is also just another way to say native, if you have your lan on icg0 then that is a native and untagged.. If you want to carry other vlans over that same icg0 interface they would be tagged.
Your switch would have its default (vlan 1) as native on the port that plugs into icg0 of pfsense - and would have tagged vlans 10 and 20.
Devices you plug into this switch that you want on a specific network, be it 1, 10 or 20 would be just untagged in that vlan on your switch.
Only if you are uplinking to another switch, or AP or like a vm host interface or something would you tag 10 and 20.. When that thing your uplinking to would need to be able to put traffic on any of those networks.
If you would tag a vlan to your PC, then you would have to setup your pc to understand the tag, and also any traffic it put on the wire would need to be tagged.
-
Thank you all for the replies, some things I dont understand but I will research and try to figure out, I am new to Pfsense and have some understanding of VLANs, just not setting them up apparently.
My pc is connected to port 2, port 2 via the switch has tagged VLANs 10,20 and untagged 1 (I was backwards in my original post, sorry).
My goal is to be able to upload sequences or programming to the raspberry pi on VLAN 20 from VLAN1 (my pc) when needed. Allow the pi (VLAN20) access to the xlights main board (also in VLAN20) to receive data and send data to each other in VLAN20 but not over to VLAN 1 or VLAN10 while allowing all of them Internet access (for updates).
I understand it might not be best practice to have everything in VLAN1 but until I can figure this out its only thing I can do :-). Then I hope to move stuff around and get out of VLAN1.
Thank you again for your help and suggestions!
I very much appreciate it! -
@dbeaver2471 said in Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work:
My pc is connected to port 2, port 2 via the switch has tagged VLANs 10,20 and untagged 1
That is wrong.. Is your pc acting as a vm host that you will put vm on different networks?
Nothing on vlan 1 is an enterprise thing.. Its not a serious problem running it on a home network or smb. It is just the default untagged network. And to be honest you will see it in the enterprise as well.
We have a site in the enterprise I work for, actually a couple where they have a vlan 1, that lots and lots of users sit - just not been on the top of list to fix yet ;) Its been years and years - just a company that was acquired and wasn't worth the hassle to fix when their network was connected to the global company network.
All smart/managed switches come with vlan 1 as the default vlan. Comes down to more of a hey don't use the default setting sort of thing. I have some switches in the network where you can not change the default vlan, and that is their management network (untagged) and you can not change that - so to manage them you use an untagged network, and to that switch it is vlan 1. Doesn't matter if switch its connected to thinks it vlan X, if its untagged makes really no difference other than for the internals of the switch to keep track.
Untagged traffic coming into port 3 might be actually be vlan 30 to switch A, and port 6 might be vlan 1. etc. Any untagged traffic coming into that switch on 6 would be vlan 1, untagged traffic coming into port 3 would be on vlan 30.. The "management" IP of that switch has to be on vlan 1, so your traffic coming in on port 3 wouldn't be able to talk to the management IP of that switch even if on the same L3 network of like 192.168.0.0/24
If all you have is entry level switches, I doubt they will be able to actually work correctly if you don't use vlan 1 on them, or be able to access their management IP. I would serious suggest you forget about the negative connotations around vlan 1. If your lan is an untagged network on pfsense. Then just use vlan 1 on your switch and more than likely where its management IP sits. Doesn't mean you can't have other vlans on that switch that are untagged on other ports, etc. You could for sure put your pi on a different vlan that is tagged coming into the switch from pfsense, but the port that is connected to the pi on that switch would be untagged in that other vlan.
edit: maybe an example drawing would help
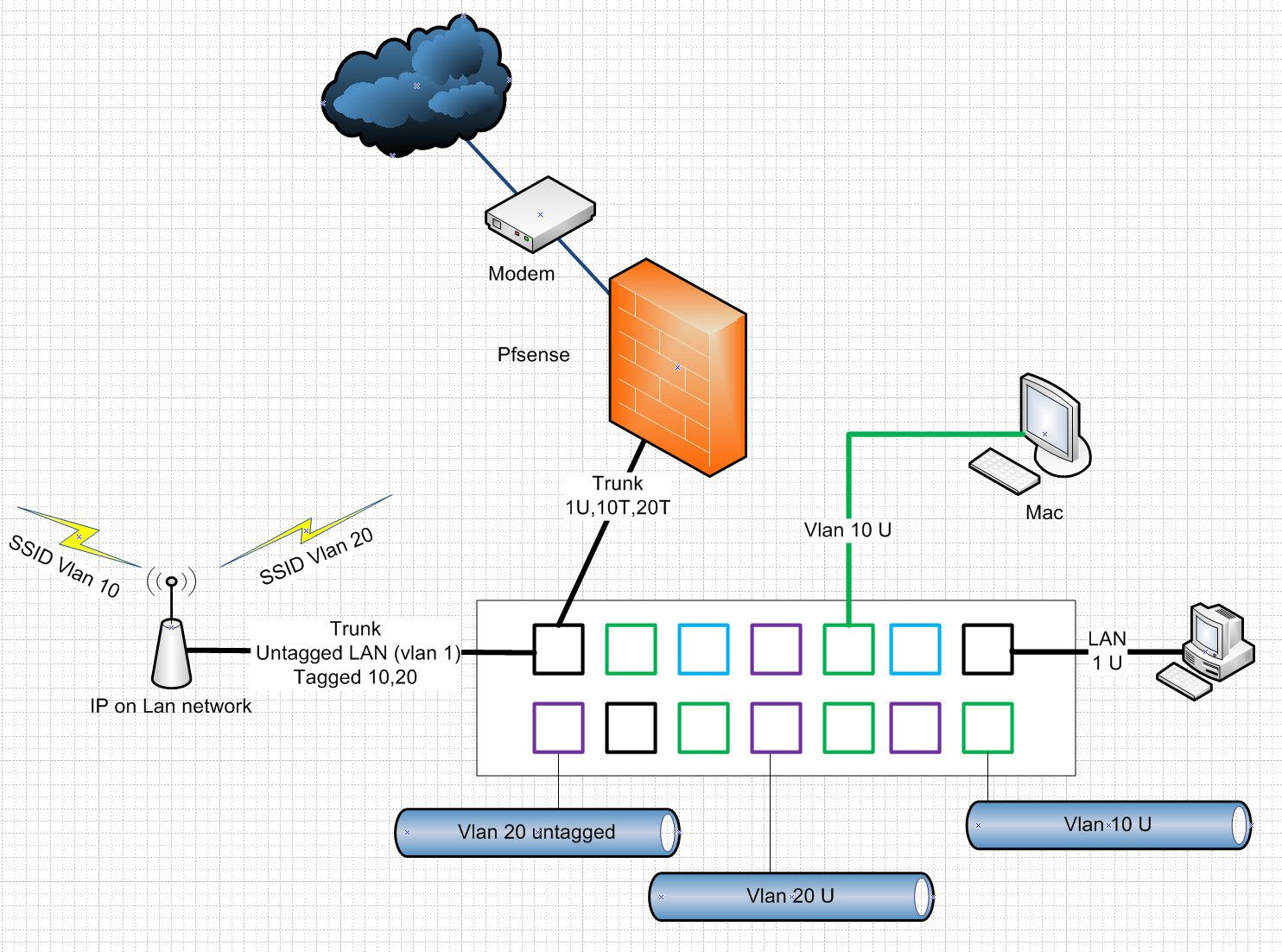
-
@johnpoz Thank you for the explanation and example!
I felt that way about VLAN1 but was very much like well its default so I should probably change that... I deleted VLAN10 MGMT for now (to simplify). Aruba 1930 switches are sorta smart? Kinda layer 2.33, not quite layer 2 and not layer 3, guess you could say pro-sumer? not professional... heavy duty consumer, or small business?
Port 1 on my switch is my netgate 4100 connection, port 2 is my pc tagged to VLAN20, untagged to VLAN1, ports 5 & 7 are untagged VLAN20 are the raspberry pi and the xlights control board set. I dont have any trunks on any ports is this where I might be going wrong? What was weird was when I set the pi to DHCP and plugged it into port 5 or 7 it picked up an address that was statically set to something else (and currently in use) and not in the defined VLAN20 range (192.168.20.xxx instead it came up with regular 192.168.1.xxx address) that really didnt make sense to me? Will try a few things and see what happens?
Thank you Again!
-
@dbeaver2471 well, if you want to use tagged vlans you better have an uplink / trunk port... ;) otherwise it won't work.
That "trunk" carries all your vlans, each has a nice little tag with it (tagged > VLAN ID to identify where from/to)...no trunk, no carrier...Your mentioned problem is just one of the funny things happening when using ill configured VLANs...
Between switch / router / AP > native VLAN untagged, rest tagged.
Between switch and client (non vlan aware) > VLAN i.E. 20 untagged
Just as @johnpoz "painted" so beautifully... :D -
@the-other
I dont know what I am doing, other than losing my hair?Netgate 4100:
Interfaces, Assignments, XLights
checkbox enabled
Interface = XLights
IPV4 Static
IPv4 address = 192.168.20.1 /24 (save) I have 1 rule on vlan20 any any.Firewall
Rules
XLights
Action = Pass
Interface = XLights
Address family = IPv4
Description = Allow All (save)Services
DHCP Server
XLights
Enable check box checked
Allow all clients
subnet 192.168.20.0/24
subnet range 192.168.20.1-192.168.20.254
address pool range 192.168.20.10-192.168.20.250
DNS 192.168.20.1 8.8.8.8 1.1.1.1Aruba 1930 24port switch:
Switching
Trunk Configuration
TRK1 = port membership 1 (port 1)VLAN
Interface 1 = Trunk (netgate 4100 to router)
Interface 2 = Tagged VLAN20 untagged 1 (my pc)
Interface 5 & 7 = Untagged (XLights)I can ping both 192.168.1.1 & 192.168.20.1 from my pc, however I cant access the pi that is on 192.168.20.3? or through name resolution fppmain.local
Basically its a very detailed description of exactly what I have?
Thank You for your help! -
@dbeaver2471 said in Cant get VLAN configuration between Netgate 4100 & Aruba 1930 to work:
name resolution fppmain.local
local is mdns - that would not resolve across vlans/networks - its local only multicast. You didn't use .local in dns did you?
If you can not ping your pi at 20.3 from your pc in vlan 1 but you can ping 20.1 (pfsense IP) this points to a problem on the pi, either firewall or it didn't get an IP in your 20 network. Maybe your switch port your pi is connected to is wrong? If you manually set the iP on the pi, did you set a correct mask, did you give it a gateway. Can the pi ping pfsense IP on the 20.1 ?
-
@johnpoz
I did not use .local in dns.took pi out of equation, plugged an old laptop (DHCP) into port 5 (VLAN20) on the switch and it did not connect nor give me a working ip... 169.254.179.208 with a subnet of 255.255.0.0 which means it didnt recognize nor connect. Tried to ping 192.168.20.1 and 192.168.1.1 neither pinged.
Swapped to a VLAN1 port and both pinged? I know am doing something wrong its just what?
-
I have been trying different things on the Aruba since it seems like what I have done to the netgate and pfsense should work, it pings? The Aruba is proving to be... glitchy? sometimes it saves the changes, sometimes it doesnt? Sometimes it shows the changes that I just did then sometimes it doesnt? I am beginning to think I might have an issue with the switch holding the VLAN / Trunk configuration? Thank you for everyones help with this, I greatly appreciate it and would not have gotten near this far without your help. THANK YOU!
-
@dbeaver2471 lets see the config of the switch.. Trunk - does that it means it allows all the vlans?
Just because you trunk a port doesn't mean you have vlan X or Y on it.. does it say trunk all or something?
Lets see pfsense config - what specific interface did you assign the vlan too?
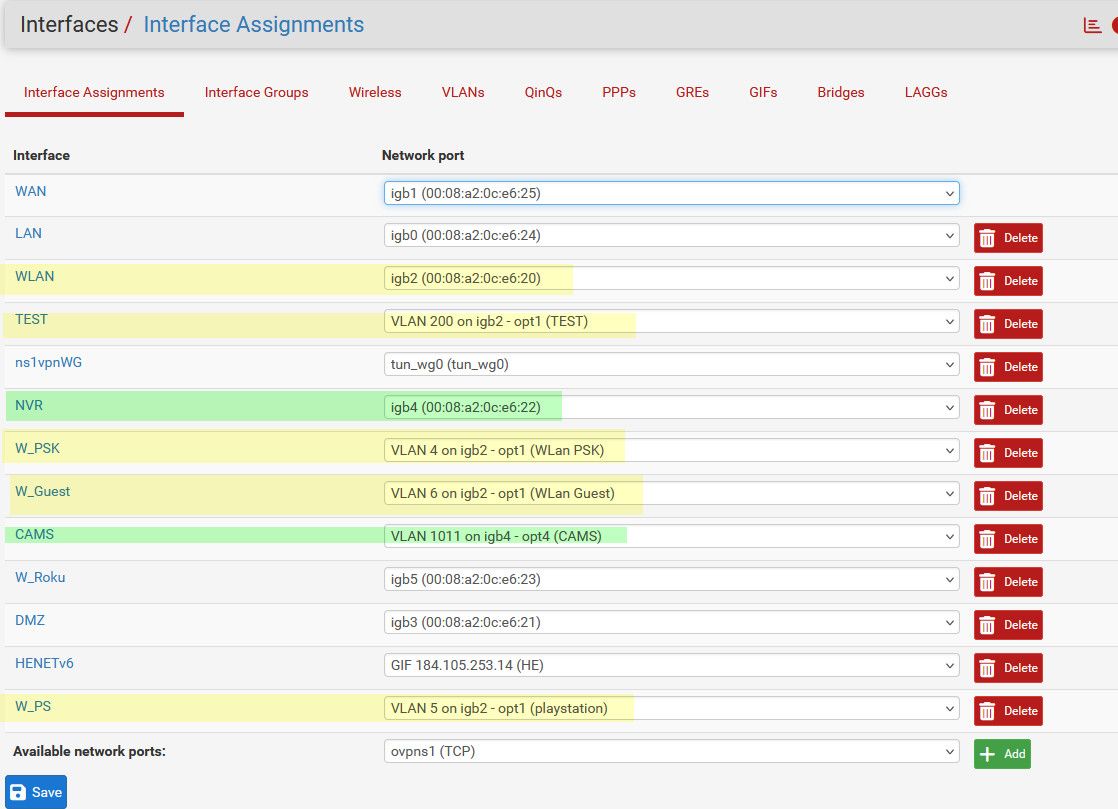
Notice I have some vlans that run on igb2 (yellow), and then I have other vlan that run on igb4 (green)
Here is config of my switch for the ports 5 and 6 on my switch that igb2 and igb4 are connected too
! interface gigabitethernet5 negotiation preferred master description "sg4860 WLan&Vlans (igb2)" no snmp trap link-status switchport trunk allowed vlan add 4-6,200 switchport trunk native vlan 2 ! interface gigabitethernet7 negotiation preferred master description "sg4860 NVR&CAM (igb4)" no snmp trap link-status switchport trunk allowed vlan add 1011 switchport trunk native vlan 110 !Here are their configs in the gui of the switch
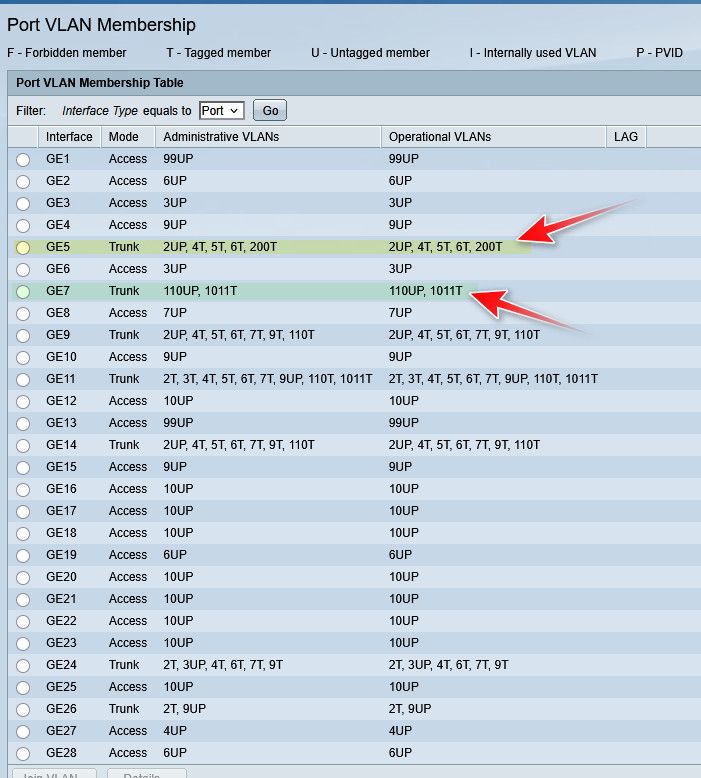
-
Thank you for the replies, I was sort of able to figure it out and get it/them working But its not how I expected? I setup the VLAN's on the switch and according to everything I could figure and you guys too it should have worked but it didnt? After going back-n-forth with this for a few days I decided to give it a rest for a couple days. When I got back to it I went to login to the switch and was unable? No matter what I tried couldnt get it so I did a hard reset (unplug) and tried to log back in, I was able to get into the switch and all the config was there so I plugged my laptop in and it pulled the .20 IP??? More testing and it did what it is supposed to do? Best I can figure is that the switch didnt like what I was telling it and decided it needed a refresh to then give what I was telling it? IDK but its working now. To all Thank You especially johnpoz , theother, and patient0! :-)