No blocks on IP
-
Hi all,
I am new to pfsense and pfblockerng.
I installed and configured the package with some default IP blocking and OISD add blocking.Before switching to pfsense I used OPNsense and configured the spamhaus drop rules.
In OPNsense I could see matches on the IP’s from the aliases that were blocked.
With pfsense and pfblocerng I didn’t had any blocks on IPs yet, thus iam wondering if everything is working fine. Is this normal behavior?
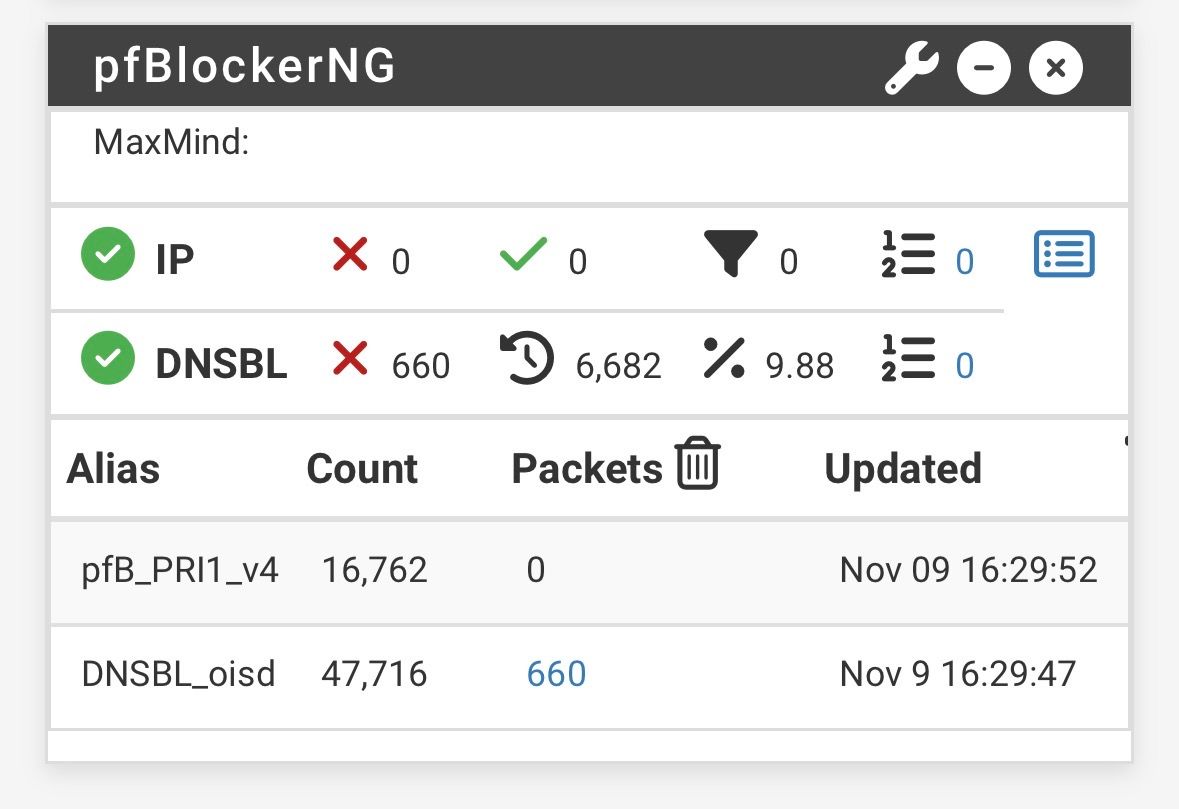
-
Ah, I changed the action to deny both and now I also have a wan firewall rule, which I also had on OPNsense.
With this wan rule I can see the blocks already coming now!
Is it a bad idea to have the action set to deny both instead of inbound only?
-
@vicking said in No blocks on IP:
Is it a bad idea to have the action set to deny both instead of inbound only?
Question is squarely for admin. Per the infoblock which explains, in part, the "Deny Inbound", "Deny Outbound", and "Deny Both" actions:
'Deny' Rules: 'Deny' rules create high priority 'block' or 'reject' rules on the stated interfaces. They don't change the 'pass' rules on other interfaces. Typical uses of 'Deny' rules are: Deny Both - blocks all traffic in both directions, if the source or destination IP is in the block list Deny Inbound/Deny Outbound - blocks all traffic in one direction unless it is part of a session started by traffic sent in the other direction. Does not affect traffic in the other direction. One way 'Deny' rules can be used to selectively block unsolicited incoming (new session) packets in one direction, while still allowing deliberate outgoing sessions to be created in the other direction.In other words:
When set to "Deny Inbound", incoming connection requests from WAN hosts are blocked and therefore no state will be created. However a LAN host can still establish state to an otherwise listed IP.
If set to "Deny Outbound", outgoing connection requests from LAN hosts are blocked and therefore no state will be created. However an incoming connection request from an otherwise listed IP to an 'open' WAN port can still establish state.
If set to "Deny Both", both incoming connection requests and outbound connections requests are blocked and therefore no state will be created regardless of connection direction.