Not sure this is normal
-
Hi Forum
I have a PFsense+ - running a VPN klient, where I route a subnet through.
This has been working fine, but for some reason my 2 Shields are not showing no NTP or DNS in that subnet, making them not run as optimal as it used to a couple of days ago. I can't remember or see anything changes that could carse this in the PFsense history.I've just testet creating a new VM in that subnet - having no issues with neither DNS or NTP
Its just my 2 Shields in that range( provided by a static lease by DHCP) they say they are missing time etc.The Shields contains a Kodi App for my movies - Which can not scan for new movies - carse the NTP - but the Shields provide an information that there's not network - allthough the devices have IP.
What can carse that suddenly my 2 shields looses this option for ntp ? Since my VM-test have no issue with ntp or DNS, as other existing machines not having these issues. My Rules have been looking like this since May:
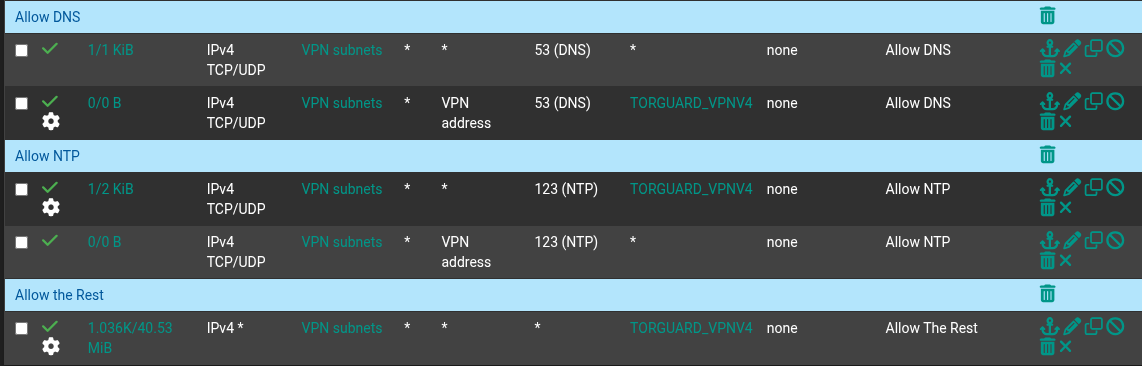
For Outbound routing - it'll look like this for the subnet
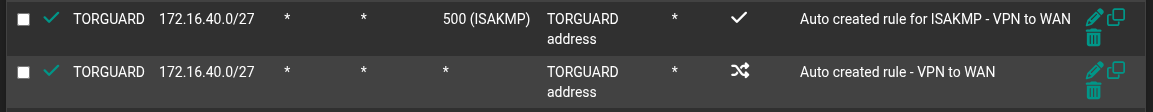
In short this means my time on my shields are not correct , all EPG etc does not match my locales and years
When I'm creating the DHCP-server - It'll have the rules as look here:
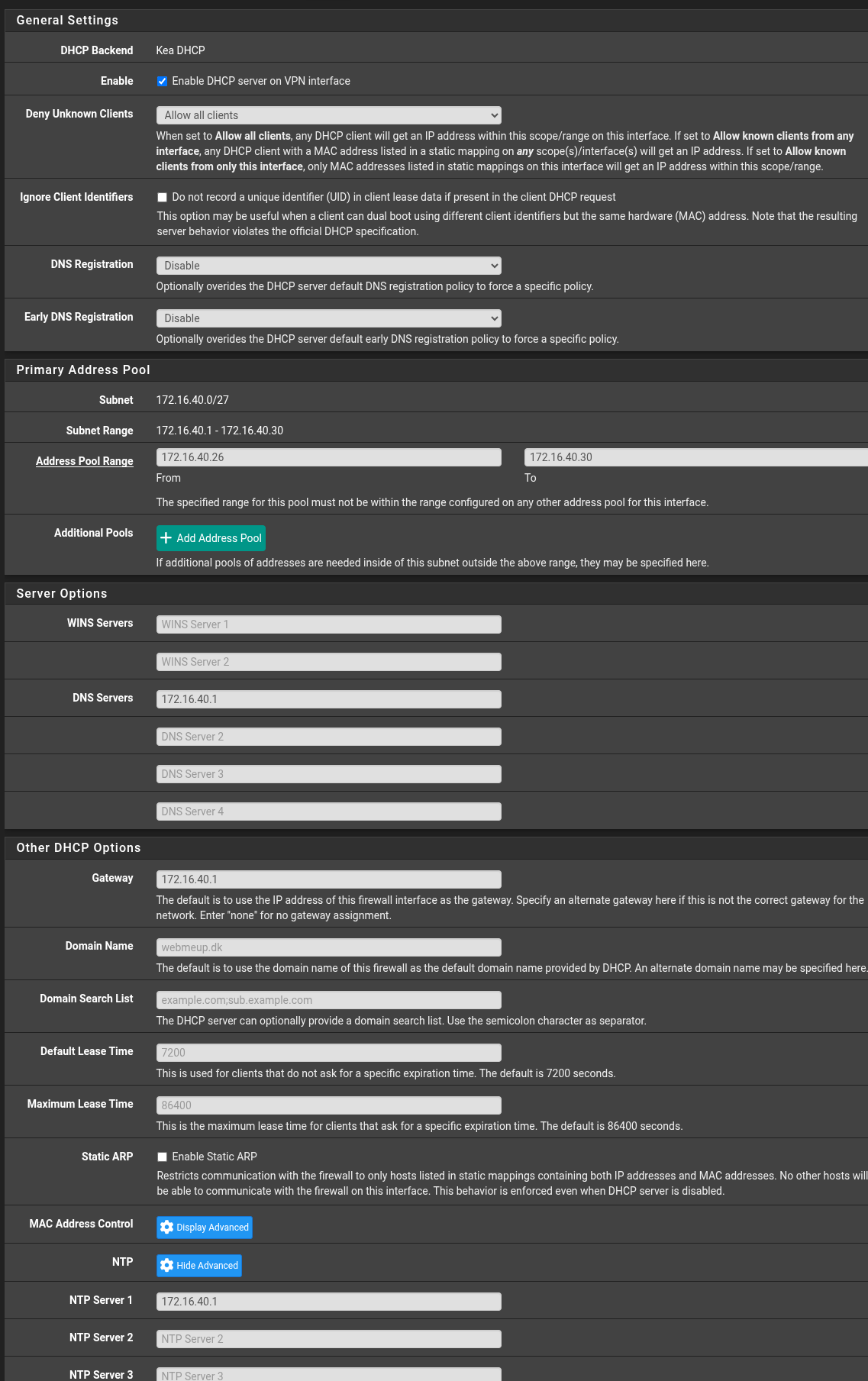
But I can not figure out why only my 2 shields are stock Not getting a NTP or DHCP server (Eventhough when I start the programs up - mostly are working but absolut not all - that are time dependent such as The weather and EPG setup)
Can anyone see any mistakes that Im missing here - since I'm missing those 2 critical services
TIA
U -
@Udbytossen said in Not sure this is normal:
my 2 Shields are not showing no NTP or DNS in that subnet
What are these subnets ? What the content of that alias ?
Did you check if the if these service are actually listening on these interfaces ? (subnets)
Example :
Question : on what interfaces is the pfSense NTP server listens ?
To answer the question : ask pfSense ![25.07.1-RELEASE][root@pfSense.bhf.tld]/root: sockstat -l | grep 'ntp' root ntpd 2525 20 udp6 *:123 *:* root ntpd 2525 21 udp4 *:123 *:* .... (a lot of current open connections are skipped here )This "udp4 *:123" telles you that for every interface - hence the * - on port 123, using UDP, with IPv4, the ntp server process is listening - ready to accepts time requests.
Same thing for IPv6.
Note that 'ntp' doesn't use TCP.Next : place on the interfaces a "pass all firewall" rule, like the one you found on the LAN when you installed pfSense.
Btw : I don't know what a shield is, neither who Kodi is.
DHCP is special.
When you create an interface, you have to set up a pfSense DHCP for that interface. Assign it a pool, and this pool must be part of that interface's subnet.No need to create firewall rules for DHCP, pfSense did that for you "behind your back", not showing them in the GUI.
The same command line test :
[25.07.1-RELEASE][root@pfSense.bhf.tld]/root: sockstat -l | grep 'dhcp' root kea-dhcp6 82114 13 stream /var/run/kea6-ctrl-socket root kea-dhcp6 82114 17 udp6 *:547 *:* root kea-dhcp6 82114 18 udp6 *:547 *:* root kea-dhcp4 80059 13 stream /var/run/kea4-ctrl-socket root kea-dhcp4 80059 17 udp4 192.168.1.1:67 *:* root kea-dhcp4 80059 19 udp4 192.168.2.1:67 *:* root kea-dhcp4 80059 21 udp4 192.168.100.1:67 *:* root syslogd 11947 5 dgram /var/dhcpd/var/run/log root dhcp6c 52757 3 udp6 *:546 *:*Btw :
is pretty useless.
Yeah, the DHCP server will announce a NTP IP (not a host name !!) if - and only if - the DHCP client asked for one.
Don't presume her : again, look for yourself : packet capture the DHCP traffic, and you can see the DHCP Lease request. Look carefully : did it ask for a NTP IP ?
If not, the server won't send it neither.
And guess what: most devices these days don't ask for NTP IP during their DHCP lease request.
Don't ask me why ^^
And on one side, all devices use TLS these days, so the current time/date is very important.
Still, you have to set a manual or static NTP IP address somewhere on that device to make that happen. Or it could be done over DHCP ....
Microsoft Windows often default to "time.microsoft.com".Bonus ramble : They do this, so they can 'measure' how many devices are using their product ^^ (that is, If I worked for them, I would do that).
-
@Gertjan said in Not sure this is normal:
Bonus ramble : They do this, so they can 'measure' how many devices are using their product ^^ (that is, If I worked for them, I would do that).
In theory that could give them a rough number I guess - but unless their products are sending some unique identifier in the query for time. How would they know if there is 1 device, or 100 devices behind a nat?
But it for sure is one of the possible reasons they do that. Not sure why they would host time services and point how many of millions/billions of installs of windows at it? Unless they were getting something out of it. I mean why not just point them to pool.ntp.org ;) and then not have to maintain the infrastructure to handle all the queries..
I mean don't they get a much better understanding of how many installs they have out there via their update system?
If me I would make sure my software, that can do dhcp would at least ask for ntp.. Which you would hope if handing out ntp via dhcp it would point to a local ntp server. Thus in turn reducing internet traffic, and the overall resources required to serve time from the hosting perspective. I mean sure ntp does not require much bandwidth, and can be served pretty easy.. But when you scale into the millions and or billions of clients - the resources and bandwidth add up.
I would be curious how many queries a day time.windows.com gets ;) Also curious of how many dns queries they get for it, they have a 1 hour ttl on it. Out of the box windows for sure doesn't query ntp multiple times an hour.. So why not have a longer ttl to reduce the number of dns queries, etc. I mean are the resources going to change so often that they need such a low ttl - why not set it for 24 or better yet prob a week.. I think out of the box with ntp setting in windows it defaults to 2^15 so like every 9 hours.
-
@johnpoz said in Not sure this is normal:
Unless they were getting something out of it
For me, that's the exact reason.
@johnpoz said in Not sure this is normal:
why not just point them to pool.ntp.org
They can't.
That is, not before informing them, like 'hey, do you mind if we send over a couple of billions request to your pool ?"The other side of the equitation is : accurate time is important.
Try settings your system clock a couple of years backwards and see if any TLS connection is still possible. So, somehow, they have to 'offer' some time services.Afaik, installing pfSense Plus with a device that doesn't' have have the correct time is .... impossible ? (not tested this one yet)
@johnpoz said in Not sure this is normal:
I mean don't they get a much better understanding of how many installs they have out there via their update system?
Sure, even when you manage to stop all telemetry, view will also stop updates - and as we don't know what is send over during an 'update', the entire 'oh no windows send telemetry' is just a diversion.
Anyway, as most time traffic is still 'not TLS', I've natted all UDP 123 traffic to the pfSense ntp process port on '127.0.0.1' and that works well enough for me.
@johnpoz said in Not sure this is normal:
How would they know if there is 1 device, or 100 devices behind a nat?
Lol. @arymec just answered that one

Here :@johnpoz said in Not sure this is normal:
I think out of the box with ntp setting in windows it defaults to 2^15 so like every 9 hours
The NTP resync time is probably hard coded - or stashed somewhere in an obscure registry key. Microsoft knows this value. Let's presume nobody changes these settings. 9 (your suggested) hours = 540 minutes.
So, if from some "IPv4" an NTP request originates every 54 minutes, then chances are that there are 10 Windows devices hidden behind that IPv4.
5,4 minutes ? => 100 devices.
With IPv6 => no NAT, things become more clear. -
@Gertjan
Well - I'm missing DNS and NTP - but only on 2 devices - the Nvida Shields
My 2 klients as Nvidia SHield (A little gamin console and AndroidTV)
Yes - my DHCP announces my NTP and DNS - which is also is listening on the interface on my VLAN40 - 172.16.40.0/27 which is the subnet created on my PFsenseNTP: /root: sockstat -l | grep 'ntp' root ntpd 90006 37 udp6 fe80::287d:81ff:fe16:9e9e%vtnet1.40:123 *:* root ntpd 90006 38 udp4 172.16.40.1:123 *:* DNS: /root: sockstat -l | grep '53' unbound unbound 8040 15 udp4 172.16.40.1:53 *:* unbound unbound 8040 16 tcp4 172.16.40.1:53 *:* unbound unbound 8040 17 tcp4 172.16.40.1:853 *:*But my 2 klients as Nvidia SHield (A little gamin console and AndroidTV)
But after beeing not working since last Friday w 5days - showing my Missing ethernet - eventhough its IP is 172.16.40.10 and 11 - without having changed anything - and now 5days after - it suddenly works again ?
But on my Test debian it was getting both DNS ad NTP along as the other hosts in the subnet. -
@Gertjan said in Not sure this is normal:
stashed somewhere in an obscure registry key
Not sure I would call obscure
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config