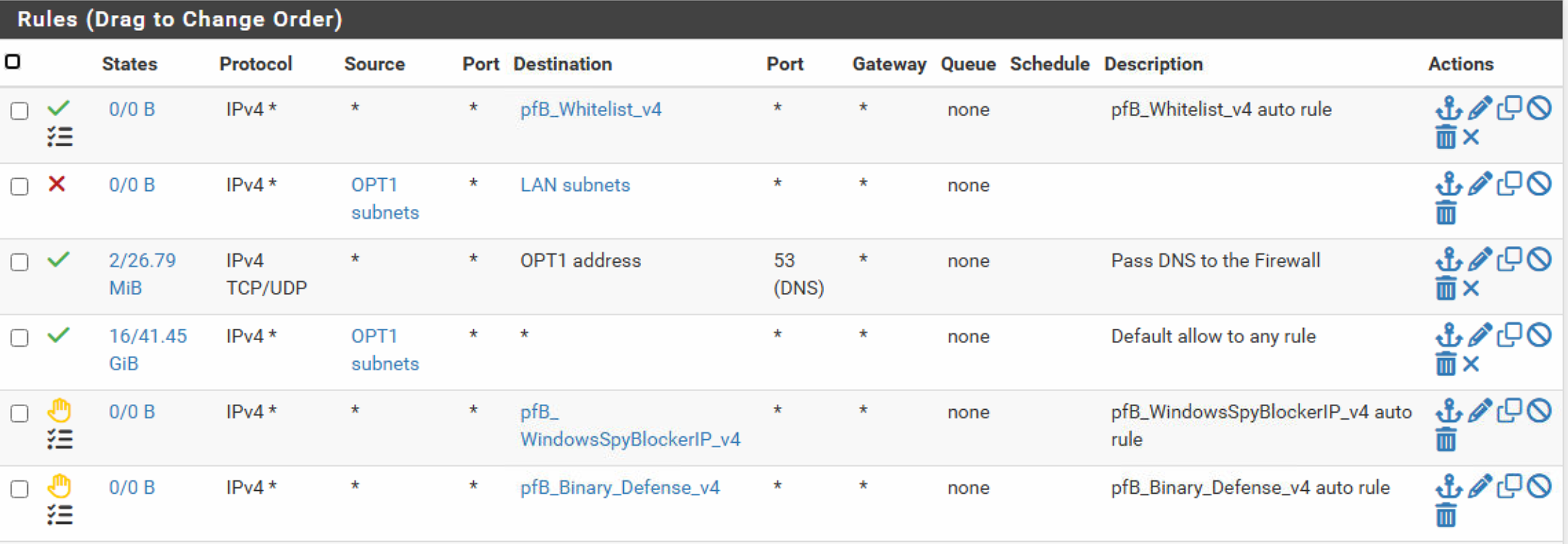
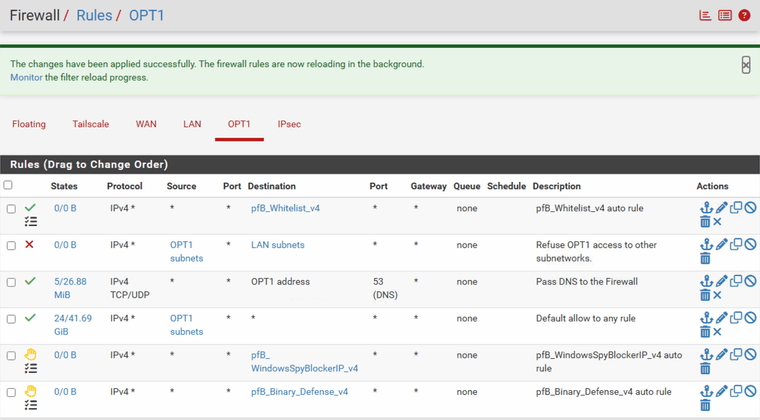
Traffic between OPT1 net and other networks e.g. LAN net
-
Hello, I made it, but it is still possible to access the other subnet (LAN net).
The other two rules were short for testing.
cheers
ron -
I'm pretty at a loss here, rules are also created;
Pre-caching Refuse OPT1 access to other subnetworks....
Creating filter rule Refuse OPT1 access to other subnetworks. ...
Creating filter rules Refuse OPT1 access to other subnetworks. ...
Setting up pass/block rules
Setting up pass/block rules Refuse OPT1 access to other subnetworks.
Creating rule Refuse OPT1 access to other subnetworks. -
@jogovogo the block rule with source OPT1 subnet to LAN subnets does not have any hits, it's 0/0 B. Have you applied the rule after having created it?
Are LAN and OPT1 on different ports or VLANs? And the rules we see are on the OPT1 tab?
Btw: your rule will (should) prevent access from OPT1 to LAN. You'll need a similar rule on LAN if you want to prevent LAN to access OPT1.
-
@patient0 said in Traffic between OPT1 net and other networks e.g. LAN net:
the block rule with source OPT1 subnet to LAN subnets does not have any hits, it's 0/0 B. Have you applied the rule after having created it?
Are LAN and OPT1 on different ports or VLANs? And the rules we see are on the OPT1 tab?
Yes, the rules are applied and are also loaded in the background.
Pre-caching Refuse OPT1 access to other subnetworks....
Creating filter rule Refuse OPT1 access to other subnetworks. ...
Creating filter rules Refuse OPT1 access to other subnetworks. ...
Setting up pass/block rules
Setting up pass/block rules Refuse OPT1 access to other subnetworks.
Creating rule Refuse OPT1 access to other subnetworks.OPT1 is vlan 22 and yes the rule is on the OPT1 interface.
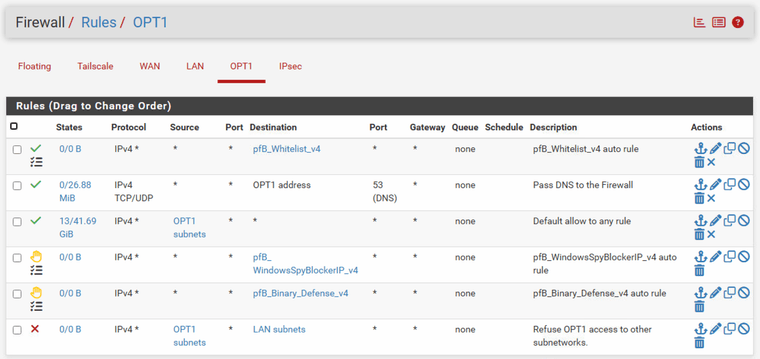
But what I noticed now is that the rule somehow slips down by itself...
-
@jogovogo said in Traffic between OPT1 net and other networks e.g. LAN net:
But what I noticed now is that the rule somehow slips down by itself...
Ah, that would explain it. The rules are first-match so that rule won't run because the third rule matches first.
Moving it above the "OPT1 subnets * *" will make work. -
-
@jogovogo said in Traffic between OPT1 net and other networks e.g. LAN net:
But what I noticed now is that the rule somehow slips down by itself...
You need to read and understand the setting at:
Firewall / pfBlockerNG / IP / 'IP Interface/Rules Configuration' / Firewall 'Auto' Rule Order. -
Okay, but that doesn't postpone the rule I created by itself, does it?
-
@jogovogo The setting affects the ordering of all rules in the ruleset.
-
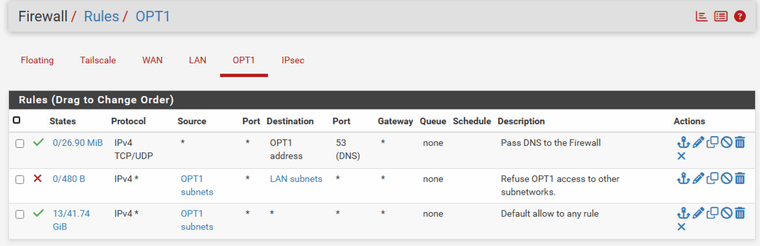
I have now switched to floating so that he leaves me my rules alone. (and kill states, one time)
-
@jogovogo I personally only use floating rules as a matter of absolute last resort. I've therefore found pfBlockerNG's default ordering format to be the setting that works best for my use case.
-
Okay, I understand, how would you approach my case without floating?
-
@jogovogo From what you've shared, it appears the default ordering format (i.e., "
| pfB_Pass/Match/Block/Reject | All other rules | (Default format)") works perfectly for you—as long as you keep the "Refuse OPT1 access to other subnetworks." deny rule above the "Default allow to any rule" pass rule of course...And unless you expect any non-"OPT1 subnets" DNS traffic to arrive on OPT1, the "Pass DNS to the Firewall" pass rule is unnecessary.EDIT: The "Pass DNS to the Firewall" pass rule may be necessary if the "OPT1 address" IP is contained within the "LAN subnets" alias. (And in such as a case, it would need to remain above the "Refuse OPT1 access to other subnetworks." deny rule.)SECOND EDIT: I maintain that unless you expect any non-"OPT1 subnets" DNS traffic to arrive on OPT1, the "Pass DNS to the Firewall" pass rule is unnecessary.
-
@jogovogo what I forgot: what pfSense version are you using? There was an issue with changing rule orders in certain situations on pfSense+ 23 and 24.
https://forum.netgate.com/topic/196601/rules-order-randomly-changes
https://redmine.pfsense.org/issues/16076