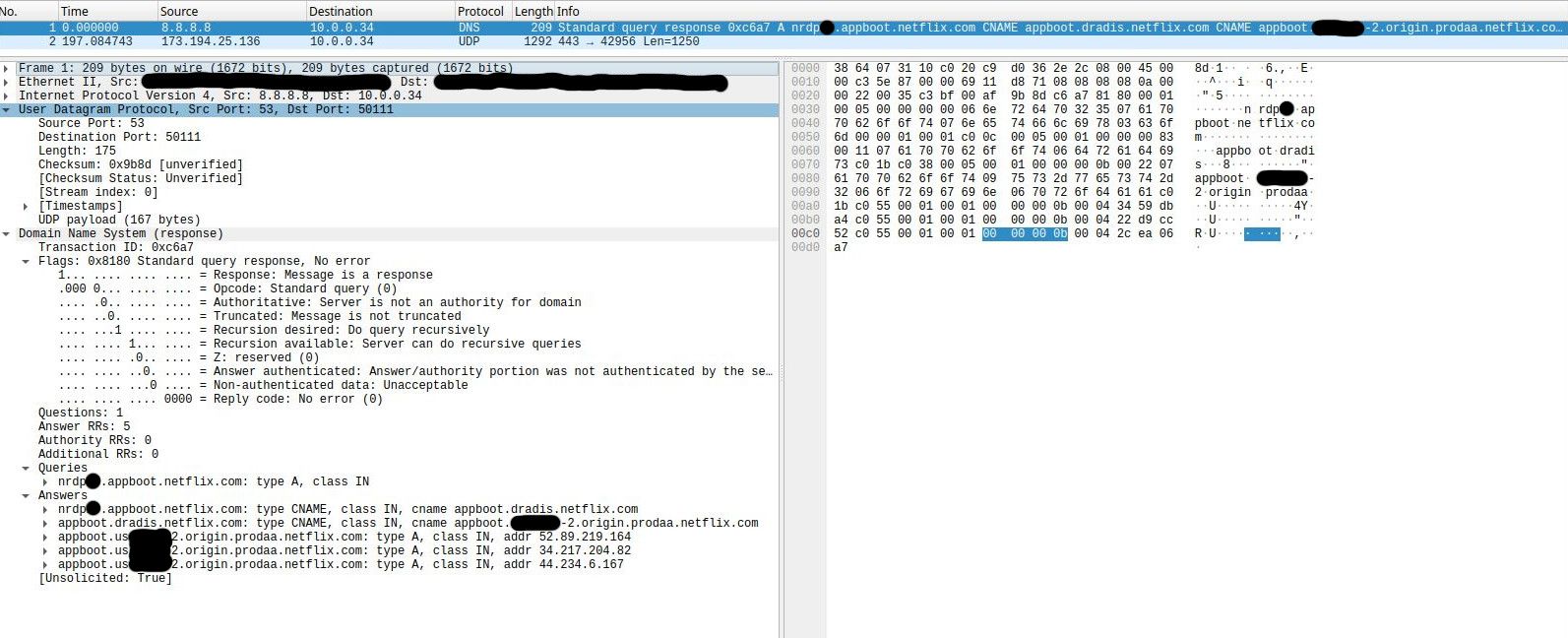
So why is Netflix hitting me with Dradis?
-
@ssullivan556 said in So why is Netflix hitting me with Dradis?:
DNS is NOT google
And apps and devices like "tvs" love to use their own dns..
Quite possible that was a dns query to check for an update or something, or telemetry - so no it wouldn't "break" your internet or anything. Or stop netflix from working.
I block lots of dns queries - stuff still works.
Why do they rate something at a 1? Is that what your asking - well if it wasn't a false positive, then yeah it would be bad ;)
Snort or any sort of ids/ips is going to have lots and lots of false positives - which is why users shouldn't be using it unless they understand that, and how to deal with it, and how to address them, etc.
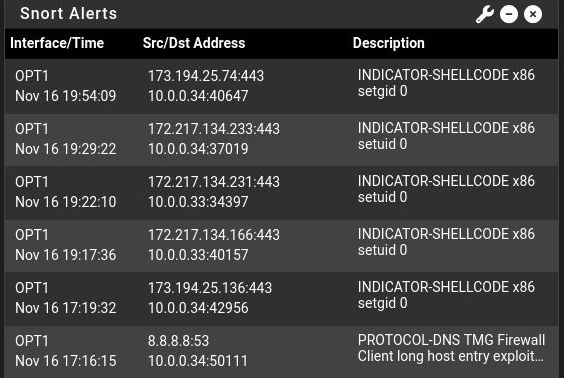
Was it actually blocked? Snort normally would default to monitor only mode.
edit: here as example - did a quick sniff on the segment my rokus and tvs are on..
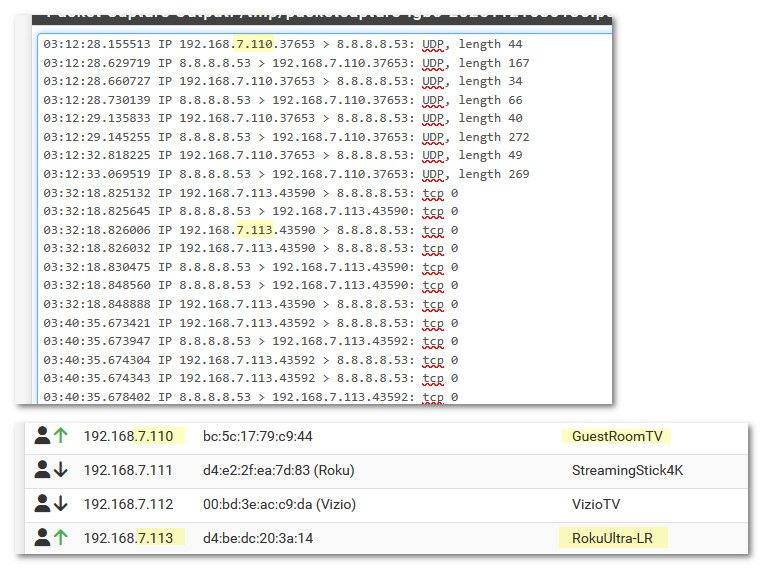
I sure don't have them set to google, If you look at their network settings in their gui, they don't list google as dns, etc.. But as you can see - they are asking google.
You could block that if you want, but when they can't talk they tend to get more chatty about it - asking more and more often, etc..
But just because they talked to google, and your ips/ids flagged something as possible bad - doesn't mean it is..
-
@johnpoz said in So why is Netflix hitting me with Dradis?:
Why do they rate something at a 1? Is that what your asking - well if it wasn't a false positive, then yeah it would be bad ;)
But just because they talked to google, and your ips/ids flagged something as possible bad - doesn't mean it is..
I am aware 8.8.8.8 is a DNS and that there are many false positives in general. If this is one, why does it appear to call a Dradis server in the pcap? Why is this unsolicited traffic (even when the TV is off) hitting my home network with a penetration testing tool?
Yes, I have the blocking box checked, it is an IPS. I cannot think of any legitimate reason to find Dradis inside my network. This is exactly why I have IPS.
-
@ssullivan556 said in So why is Netflix hitting me with Dradis?:
I cannot think of any legitimate reason to find Dradis inside my network.
Sure you can. Corporations have development and security teams that are paid to investigate unexpected client-side behaviors.
-
They'll seriously hit some random TV with a penetration test rather than just doing it in their own sandbox? When do I get the report lol? I had no unexpected behavior, have not opened Netflix since the factory reset. I have not even agreed to their privacy policy.
Is there any transparency (i.e. I could contact Netflix and try to get confirmation this was a sanctioned action)?
-
@ssullivan556 Everything you're observing is likely automated.
-
It feels like a violation that they think they can just use my devices, my bandwidth for penetration testing whenever they want (and since it is automated, that would be "all the time").
They have the source code for their software and if they are worried about other software on the TV, well they can talk to those vendors or buy their own TV (forget the phone, that is even more concerning)!
I still do not see a legitimate reason for any penetration tester to be in MY network on MY devices without MY consent. Is this actually legal? Recall I did not agree to Netflix's privacy policy.
-
@ssullivan556 Two options:
1.) Don't put untrusted devices on the LAN; or
2.) If you must put untrusted devices on the LAN, segment the LAN accordingly.I otherwise empathize with your frustration regarding the zeitgeist completey.
-
@tinfoilmatt Some good news is that these seemed to stop after a few days of blocking. Not sure how long it had been going on, Snort was down for a little while and this was literally the first alert/block when I got it going again.
Thanks all for the discussion. I am not treating this as a false-positive.
-
Do you think my devices where actually on when I did those sniffs? They were off - or like most such devices these days standby, power save - not actually "off"
most TV's never actually turn off - they go into a standby mode so that when you turn them on again it doesn't take 2 minutes to boot up.
Same goes for streamer type boxes like Roku, etc.
If you want them fully off - you would need to set that in the device - or actually remove power from them.
I would bet a very large some of money - all your seeing is typical DNS they do - possible checking for app updates or their own updates, etc. Which they also do - on a Roku you can see when it last checked for updates, more times than not its going to be when its not actively being used.
Your tinfoil hat is on a bit tight if you ask me - your snort is triggering on well known false positive rules, you have something as benign as a device talking to well known default hard coded name servers.
And you're making it to to be a global conspiracy.
If they were doing some nefarious do you not think it would be all over the place? I mean its not like you are the first person to ever turn on snort ;) And watch what traffic goes out of their network from such iot devices, etc.
You are for sure are not the first person to come screaming the sky is falling the first time they see something they do not understand and first thing they jump to is oh my gawd - they are doing something bad. While I am not a fan of hard coded DNS, or worse yet dot or doh being used without consent and acknowledgement from the user of said device.. But to think they are trying to sneak something through in a simple DNS query. And if they were - it would be caught by people way smarter than us and they would be screaming about it that is for sure.
-
@johnpoz You're responding to an LLM.