PFsense 2.0 and 1.2.3 mixed OpenVPN
-
Site 1 (PFSense 1.2.3-RELEASE)
Dual WAN (Fixed IP's)
OpenVPN Server
LAN 192.168.1.1Site 2 (PFSense 2.0-BETA1)
Dual WAN (Dyn IP's)
OpenVPN Client
LAN 192.168.0.250When I had a PFSense 1.2.3 on site 2 my OpenVPN (Site2Site) worked without any problems.
Now that I have upgraded to PFSense 2.0 (2x Dyn PPPoE) I'm having troubles with my OpenVPN
My 2XWAN on Site2 are balanced TIER1 and thats working.
OpenVPN connects and is working. Ping on the PFsense interfaces work to all ip's (Site1 & Site2)Connecting from site 1 -> site 2 is working. (OpenVPN Server)
Connecting from site 2 -> site 1 is NOT working. (OpenVPN Client)I need a OpenVPN Bridge <-> from all networks.
I have a Firewall rule * * * * * * none OpenVPN for the OpenVPN Traffic on Site2
I have something wrong on my new PFSense 2.0 (Site2) config. Or I don't understand the new OpenVPN in 2.0
Please help.
-
This should work fine, make sure you specify both local and remote subnets at the 2.0 configuration. 1.2.3 seems only require the remote subnet, it isn't even possible to provide the localnet, so that's fine. I have a working OVPN tunnel between 1.2.3 and 2.0.
-
This should work fine, make sure you specify both local and remote subnets at the 2.0 configuration. 1.2.3 seems only require the remote subnet, it isn't even possible to provide the localnet, so that's fine. I have a working OVPN tunnel between 1.2.3 and 2.0.
In the 1.2.3 its not possible to provide the localnet like you said. (1)
But where do you enter the localnet subnet it in the 2.0 config ? (2)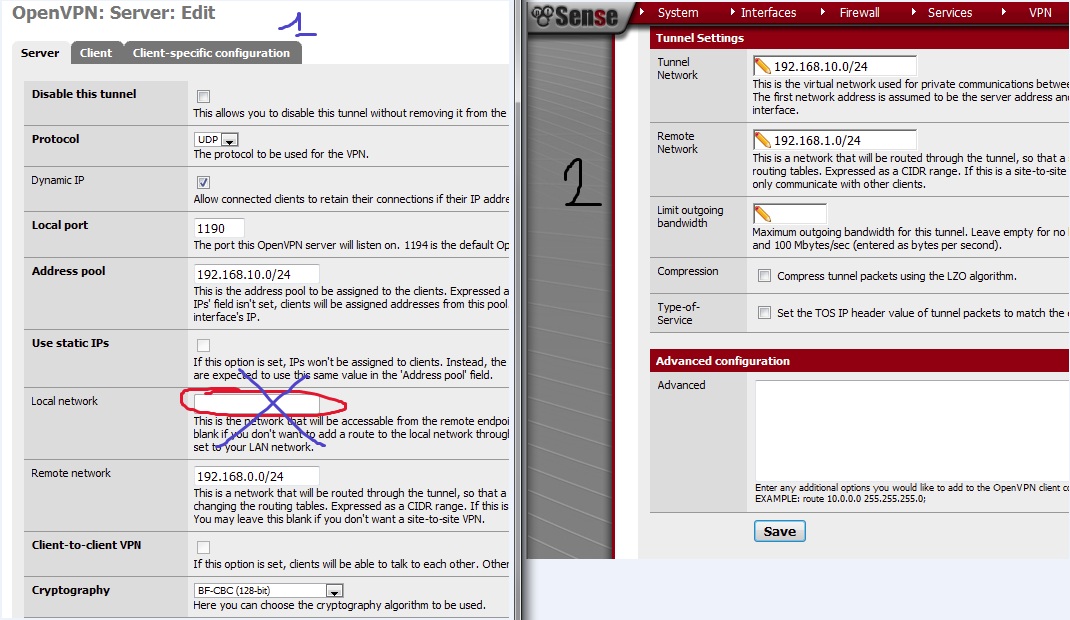
-
I'm sorry, checked it but there doesn't seem to be a localnet value. Don't know why I thought that, prolly mixed up ipsec and openvpn. My bad!
Not sure what's wrong with your configuration, as pinging from one site to the other is possible, both should have the correct routes put in. You could try adding an allow all from/to all rule for the LAN interface and make sure it's on top of the other rules, but I would suspect you'd have the same problem with 1.2.3 <-> 1.2.3. Always worth trying, making sure no firewall interferes.Good luck.
-
Found the solution:
Due to the Dual WAN solution. all my LAN traffic wanted to go true the MULTIWAN Gateway. this means also OpenVPN traffic.
Now that I made 1 rule on my LAN that only traffic for port 80 needs to be balanced and go true the MULTIWAY Gateway
then 1 rule lower pri that lets all other traffic true the * default gateway.NOW my OpenVPN works in both directions
Site 1 (PFSense 1.2.3-RELEASE)
Dual WAN (Fixed IP's)
OpenVPN Server
LAN 192.168.1.1Site 2 (PFSense 2.0-BETA1)
Dual WAN (Dyn IP's)
OpenVPN Client
LAN 192.168.0.250When I had a PFSense 1.2.3 on site 2 my OpenVPN (Site2Site) worked without any problems.
Now that I have upgraded to PFSense 2.0 (2x Dyn PPPoE) I'm having troubles with my OpenVPN
My 2XWAN on Site2 are balanced TIER1 and thats working.
OpenVPN connects and is working. Ping on the PFsense interfaces work to all ip's (Site1 & Site2)Connecting from site 1 -> site 2 is working. (OpenVPN Server)
Connecting from site 2 -> site 1 is NOT working. (OpenVPN Client)I need a OpenVPN Bridge <-> from all networks.
I have a Firewall rule * * * * * * none OpenVPN for the OpenVPN Traffic on Site2
I have something wrong on my new PFSense 2.0 (Site2) config. Or I don't understand the new OpenVPN in 2.0
Please help.