OpenVPN partialy working… Please help
-
I have searched the forum for a Tutorial that is specific to 2.1.4 and have not been able to find anything. So if someone could point me the the correct direction that would be great. the following is a list of goals I'm looking to achieve.
1.) I need to be able to access some of the computers at the HOST site. I don't mind being able to have complete access but I do need to have access to at least 2 of the machines on that side.
2.)I need my internet activity routed to the HOSTs Connection. I have to be able to access a more secure connection when in the field as I transmit possible sensitive information about my clients to and from the home office.
What I do have going for me is an OpenVPN that does allow me to ping and connect to the PFSense box. I do not have access to any of the rest of the network or the internet. I have read much of the information out there and it seems to be sending me in circles.
The Client Machine is a Laptop with Windows 7 and the current OpenVPN software.
I have followed the only tutorial I could find that sounded like what I wanted to do, and was for PFSense 2.0 I have read about the roadwarrior setup but could not find anything on a version greater than 1.2.3
I really appreciate anyone taking the time to read this and assist me with the rest of the setup.
Thanks so much in advance.
Dr. Claw
-
Post your server1.conf.
-
I hate to be to noobish but I don't know how to do that. I know how find some reports and have been playing around looking in to more all the time but I have no idea how to get my server1.conf.
Thanks
-
If you're familiar with the shell, the openvpn config files are located in "/var/etc/openvpn".
Otherwise, you can also get it from the GUI:
-
Diagnostics -> Edit File
-
Click Browse
-
Navigate to the "/var/etc/openvpn" directory
-
Click on "server1.conf"
This will display the contents of your openvpn server config.
-
-
Thanks for the quick guide for that here is the info.
dev ovpns1
dev-type tun
tun-ipv6
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto tcp-server
cipher AES-128-CBC
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
local 24.118.97.87
tls-server
server 192.168.2.0 255.255.255.0
client-config-dir /var/etc/openvpn-csc
username-as-common-name
auth-user-pass-verify /var/etc/openvpn/server1.php via-env
tls-verify /var/etc/openvpn/server1.tls-verify.php
lport 443
management /var/etc/openvpn/server1.sock unix
max-clients 2
push "route 192.168.1.0 255.255.255.0"
push "dhcp-option DOMAIN 192.168.1.1"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 75.75.76.76"
push "dhcp-option DNS 8.8.4.4"
push "dhcp-option DNS 75.75.75.75"
client-to-client
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /etc/dh-parameters.1024
tls-auth /var/etc/openvpn/server1.tls-auth 0
persist-remote-ip
float -
Just so I don't make assumptions, can you tell me:
-
What is the LAN subnet on the remote end (Behind Pfsense)?
-
What is the LAN subnet where you're connecting from?
-
What are the IP's of the machines you trying to connect to?
-
How are you trying to access these machines? (e.g. RDP, HTTP/HTTPS, FTP, file shares, etc)
-
Are you trying to access these machines by IP or by name?
-
-
1. 192.168.1.0/24
2. If I understand you question it will vary on where I'm connected from. Many of the Starbucks and other coffee shops seem to use 10.0.0.0/24. many friends use the 192.168.1.0/24. I'm guessing as I travel it will be all over the place. if you mean the VIP of the VPN thats 192.168.2.0/243. 192.168.1.20 192.168.1.254 192.168.1.253
4. RDP Samba and I would like my information routed through my home internet so the packets can't be captured without encryption.5. I could use either the names or ips. Names would be nice for future options but not necessary now if its hard to do
Thank you so much for your replys.
Dr Claw
-
A few things:
-
You are using a routed solution, but you've chosen two of the most common SOHO subnets for both your tunnel network and LAN. This will break your routing if the coffee shop or wherever you're connecting from is on the same subnet as your LAN. Change your tunnel and LAN subnets to something that is not widely used.
-
You've stated you want all your traffic routed down the tunnel, but I'm not seeing that in your config, which means "Redirect Gateway" is not enabled. Go to your OpenVPN config, scroll down to the "Tunnel Settings" section and enable the following option:
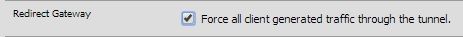
-
In the domain field, you have an IP where a domain name should be. If you have a DC, enter your domain name in the "DNS Default Domain" field. If you don't have a domain, you shouldn't be using this option… disable it.
-
Pushing 4 DNS servers seems like overkill. Also, from what I've been reading, 75.75.75.75 and 75.75.76.76 are comcast dns servers which are not that great. I would pull them out and stick with google dns
-
In a routed solution, broadcasts do not traverse the tunnell, so you can only connect to internal resources via IP unless you:
-
Have a local DNS server configured to push to your clients
-
Configure a WINS server to push to your clients
-
Manually edit the hosts file on every client
-
-
Last but not least, on Win 7 or 8, make sure you are running the openvpn client as administrator or the client will not have permissions to make changes to the routing table
-
-
Again Thanks so much for all your help!!!
I have tried to change the IP address as best I can. Both Manually and by using the setup wizard. However When I do I can no longer connect to the internet. I've tried 192.168.2.0/24 through 192.168.26.0/24 and have not been able to access the internet on anything except 192.168.1.1. In every instance I did reboot the router to make sure that the new config took. I have setup every thing except the numbered points. but just can't make the switch to a new IP. I was going to start with the numbered lists as soon as I get this issue solved.
I really appreciate your help.
Dr. Claw
-
Clarify what you mean by tried to change the IP… Which IP and where? The tunnel network or the local network? Were you making changes in OpenVPN or on your LAN interface?
Lets go back to how you had it, get it working and then adjust:
LAN - 192.168.1.0/24
Tunnel Network - 192.168.2.0/24Did you make the config change to force the traffic down the tunnel?
After reading more about "Redirect Gateway" on openvpn.net, it sounds like you either have to push an internal DNS server or push the server's IP for the tunnel for DNS, so i.e.:
Since your tunnel network is 192.168.2.0/24, remove the 4 DNS settings you have and only enter 192.168.2.1, click save and test (the openvpn service gets restarted after every save, so no need to reboot)
Make sure your testing from a separate network that is not using 192.168.1.0/24.
-
I changed the IP in the OpenVPN to 192.168.26.0/24 this should be rarely use I though.
I tried to change the IP in LAN to many differnet options none of which worked.
I did make the Config change to force traffic down the tunnel.
Erased all DNS server in OpenVPN and made it so there's just one entry at 192.168.26.1 (thought since I change to 26 that it was appropriate to adjust that here.
I have no way of testing this today and will give it a go at work tomorrow.
If you can think of a way to make the main IP change and keep working let me know as I think it would greatly increase the places where I would be able to use the VPN.
As always thanks so much for all your assistance.
Dr Claw
-
I have the same issue here so I considered not to open another topic. I have been running pfSense for about 2 years and it's very stable.
I try to make OpenVPN work in 2.1.5-RELEASE (i386) , as in 2.0.3 i386 was working ok.pfsense Box local interfaces
- LAN 192.168.111.0/24 ; 192.168.111.1 pfsense box and gateway
- DMZ 10.128.128.0/24; 10.128.128.1; pfsense box and gateway
- VPN Tunneled network 192.168.11.0/24
WINS Server : 192.168.111.100
Remote LAN (at home behind wifi router 192.168.2.0/24)
Firewall rules : OpenVPN tab : allow any to any *
Server Setup info: Pfsense is the gateway, DHCP, DNS and also OpenVPN server for road warrior remote access (SSL/TLS)|UDP|TUN . Outbound:automatic outbound NAT; push default gateway
Client : Win7 64 bit with OpenVPN 2.3.4 I603.. latest release.mention : PPTP works perfectly ! I can access any IP on LAN/DMZ.
Problem : After connecting successfully the remote LAN , I can ping the pfsense box and browse the Internet using remote public IP, but I can't access any remote device.
I have done the same setup on pfsense 2.0.3 and it work without a problem!
What has changed in routing in pfsense 2.1? What changes I have to do to pfsense config ?When i traceroute from the win7 machine first hop is the default gateway of the pfsense box (? not pfsense box), supplied by the ISP, then another 2 routers of the ISP and then Destination unreachable.
If I using packet capture are ping LAN subnet from the remote client, the ICMP packets arrive on OpenVPN interface, but only pfsense box responds ( ex ping 192.168.111.1-10 but only 192.168.111.1 responds to ICMP request)server1.conf
dev ovpns1
dev-type tun
tun-ipv6
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp
cipher AES-256-CBC
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local PUBLIC_IP_censored
tls-server
server 192.168.11.0 255.255.255.0
client-config-dir /var/etc/openvpn-csc
tls-verify /var/etc/openvpn/server1.tls-verify.php
lport 1194
management /var/etc/openvpn/server1.sock unix
max-clients 10
push "route 192.168.111.0 255.255.255.0"
push "route 10.128.128.0 255.255.255.0"
push "dhcp-option DOMAIN not-available.com"
push "dhcp-option DNS 192.168.111.1"
push "dhcp-option WINS 192.168.111.100"
push "redirect-gateway def1"
client-to-client
duplicate-cn
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server1.tls-auth 0
comp-lzo
persist-remote-ip
float
mode server
client-config-dir /var/etc/openvpn-cscroute 192.168.2.0 255.255.255.0
Client Specific overrides in CCD
push "redirect-gateway def1"
ifconfig-push 192.168.11.1 192.168.11.2
Thank you in advance for any advice!

 -
I have found the problem. In the Firewall - OpenVPN tab I had the same rule: from any to any 2 times , because I use DUAL WAN setup.
The first rule was the one with DUAL WAN gateway instead of default gateway. See picture attached.Regards,
Adrian
