New to pfsense and issues already
-
I have managed to fumble my way through the install and logged into the web interface but I'm struggling to route traffic correctly from my incoming connection to its destination
My router has allocated a dhcp address of 192.168.1.10 to the pfsense WAN I have the pfsense LAN set to 192.168.1.3 which is plugged into the a pc that has an address of 192.168.1.2 I have disabled what I believe to be the blocking rules but according to my system log all traffic is being blocked by default deny rule IPv4.
Im sure there is some routing rules that I'm missing in order to get the traffic from Wan to 192.168.1.2 but im not sure what should be going where all I want to use it for is to block certain inbound IP address maybe im over complicating things?
-
in any normal setup it is impossible to have the same subnet/iprange on WAN & LAN. routing is impossible between identical/conflicting subnets.
so basically, you either have to change your WAN subnet or if that is impossible ==> change your LAN subnet to something else
-
Ok so I have set the LAN to 10.1.1.10 on the pfsense and 10.1.1.11 on the pc but I am still unable to route traffic correctly
-
Have you disabled the Block private networks option under Interfaces - WAN?
-
Yes
-
Another option is to eliminate your other router and use pfSense instead.
If your router is a combination unit and you need to keep the switch ports and/or wireless functions, that's easy to do: Just disable the DHCP server on your old router and plug one of its LAN ports into the LAN nic on your pfSense machine. Set up pfSense with your WAN and you're good to go.
-
I don't quite understand surely I should have router –----> pfsense WAN --------> pfsense LAN ------> Server ?
But do I need some forwarding or rules to be added im in the dark here?
-
Two questions here: can you ping the internal ip of the firewall from your internal network? Let's establish first whether the issue is internal or within the firewall rules. Assuming this works and you can access the web gui, move onto the next step:
Can you post a screen shot of two particular pages? The first one is found under the Firewall/NAT menu. Select the 'Outbound' tab and post a screenshot of this page. Next, select the Firewall/Rules menu item, click on the 'LAN' tab and post a second screenshot of this page. Finally, click on the 'WAN' tab on the same section (Firewall/Rules) and take a screenshot of this page.
-
I am able to ping the firewall from the server and access the web UI from it to I have added the requested images I have checked my system log which shows activity from the router its the rules/bridging in between
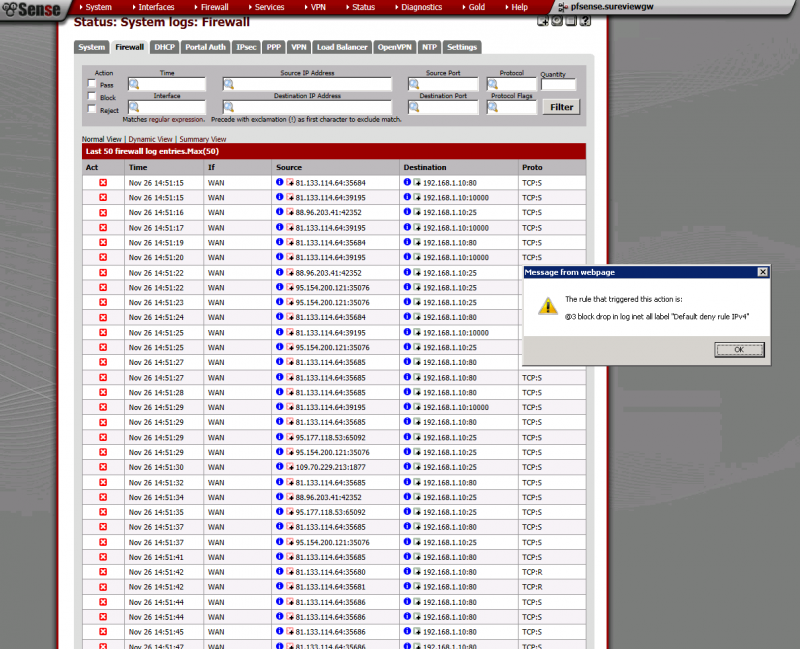
-
The default deny rule is working correctly - the last screenshot you posted shows external addresses trying to hit your external IP, which is correctly blocking the traffic.
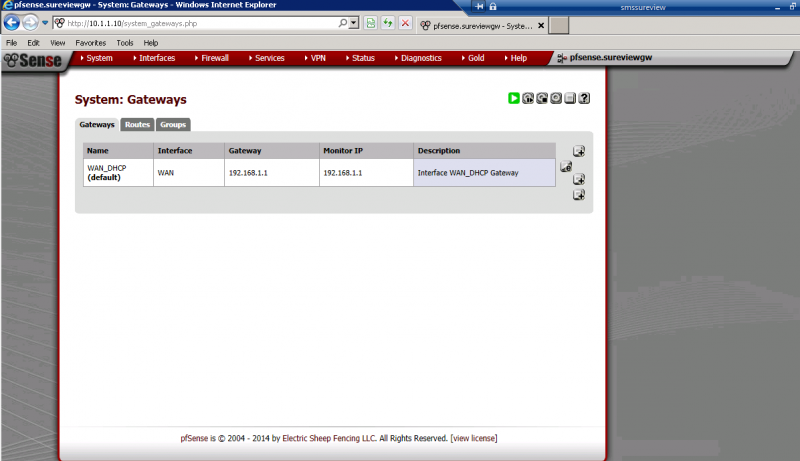
Another test: Try pinging an external address from your LAN PC, such as 8.8.8.8. Do you get a response? Check your default route out on the WAN side (menu item: System/Routing and select the 'gateways' tab. Can you send a screenshot of this page also?
Last thought: Does your internal PC have the correct DNS settings? Without a valid DNS server in your network settings you won't be able to resolve internet names, which could also be creating the problem you're having.
-
I don't quite understand surely I should have router –----> pfsense WAN --------> pfsense LAN ------> Server ?
Normally pfSense gets WAN directly, via cable modem, dsl modem, etc., and then you hang everything else (switches, wireless access points, PC clients, … ) off of the pfSense LAN port. pfSense is the router; if you have another router in front of pfSense, it's best to put it into 'bridge' mode.
What type of internet connection do you have? And what is your 'router' (brand & model)?
-
Its a business connection with Zen and the router is a vigor 2710
-
Ok I am able to ping 8.8.8.8 and Im able to view sites
-
I dont want to block the external traffic thats the data I want to recieve
The default deny rule is working correctly - the last screenshot you posted shows external addresses trying to hit your external IP, which is correctly blocking the traffic.
Another test: Try pinging an external address from your LAN PC, such as 8.8.8.8. Do you get a response? Check your default route out on the WAN side (menu item: System/Routing and select the 'gateways' tab. Can you send a screenshot of this page also?
Last thought: Does your internal PC have the correct DNS settings? Without a valid DNS server in your network settings you won't be able to resolve internet names, which could also be creating the problem you're having.
-
Ok, if the ping works, then your firewall/router are both working correctly and the issue is almost certainly DNS. If you're using a Windows PC open a command prompt and type "nslookup www.google.com 8.8.8.8". If you get a non-authoritative answer back then you just have to add 8.8.8.8 as a DNS server in your PC's network settings.
Alternately, you could set up DHCP on your firewall to assign addresses internally. (Services/DHCP Server + LAN tab). Create a valid internal range and include a public DNS server(s) in the settings. You can try 8.8.8.8 for a start, as it's a public DNS server anyone can use.
-
I dont want to block the external traffic thats the data I want to recieve
The external traffic being blocked is traffic which is originating from the internet, not your internal network. This is normal behaviour for any firewall - you don't want anyone externally to access your firewall from outside unless you have services that you want external audiences to see, which I don't believe you do. So long as the request originates from inside your LAN, traffic will be allowed back in. It's just the traffic coming unannounced from outside that's being stopped.
-
This server is used for receiving remote CCTV video alarms so I am expecting the majority of traffic to come externally
-
Ok, so you'll need to make sure you know the following information:
1. Does the traffic from those remote CCTV alarms originate from the remote addresses of the alarms or is the traffic initiated from the internal PC?
2. If the above answer is 'traffic originates remotely' then what are the external IP addresses of the remote CCTV alarms?
3. What is the tcp (udp?) port that your internal PC is using to allow connection from those remote alarms? (this has to be visible from the outside)
If you can pass on the above info, I should be able to tell you what to do to allow access to your PC from those remote sites.
-
Ok this could be tricky
There are over 200 remote sites each with static external ip's
tcp ports that need to be open are 25, 8005, 3389, 1025, 1237, 10000, 2000, 1024, 80
up until recently we blocked all traffic unless recieved on those ports via the router in built software and had filter rules to block ip's that were spamming us I run out of available rules hence the need for pfsense
Many thanks for your input so far
-
I guess that the front-end router has been setup to port forward all incoming traffic on its public WAN to the pfSense WAN at 192.168.1.10 - since that outside traffic has found its way to pfSense WAN and been blocked and logged.
Now you need to add port forward/s and rules to allow the traffic you want and forward it to that server on LAN.
Firewall->Aliases
- make an alias with the 200 static public IP addresses that you expect traffic from
- Make an alias with the list of destination ports you want to allow traffic to reach
Firewall->NAT Port Forward - Add a port forward, click the "Advanced" button for Source. Select type "Single host or alias". Start typing the alias name of the 200 addresses - the full name will appear.
- Leave source port range "any"
- Destination should be WANaddress
- Destination port range - use the port alias you made
- Redirect target IP - address of the server on LAN
- Redirect target port - use the port alias again
- Leave "Add associated filter rule" selected at the bottom
Save it.
That should redirect all the stuff you want into your server. The associated filter rule should allow it to pass.
All other traffic on WAN is blocked, so rubbish from unknown places will simply be blocked. You can choose whether to log it or just ignore it.