Nodes on OPVN server side cannot ping client and beyond
-
Hi guys - got a pfsense vm running very well on 2.1.5 in Esxi 5.5 U2
I've setup OpenVPN and have my remote location connecting with an Asus AC68U router running OpenVPN client so that I can have a site to site.
The client LAN is 192.168.1.0/24 and the Server LAN is 192.168.50.0/24
Client 192.168.1.26 can ping and RDP to 192.168.50.25, but not vice versa.
What option am I missing?
Thanks guys
-
Rules on the client OpenVPN end could be blocking incoming session start from the Server LAN end.
Client 192.168.1.26 might have a firewall stopping all traffic (or maybe stopping traffic from outside its own subnet).
Post some actual settings/rules screens if you are stuck. -
Rules on the client OpenVPN end could be blocking incoming session start from the Server LAN end.
Client 192.168.1.26 might have a firewall stopping all traffic (or maybe stopping traffic from outside its own subnet).
Post some actual settings/rules screens if you are stuck.Thanks for the reply - I used the wizards to simply create the server side including certs and all. Client connects fine. Here are my FW rules on the pfSense:
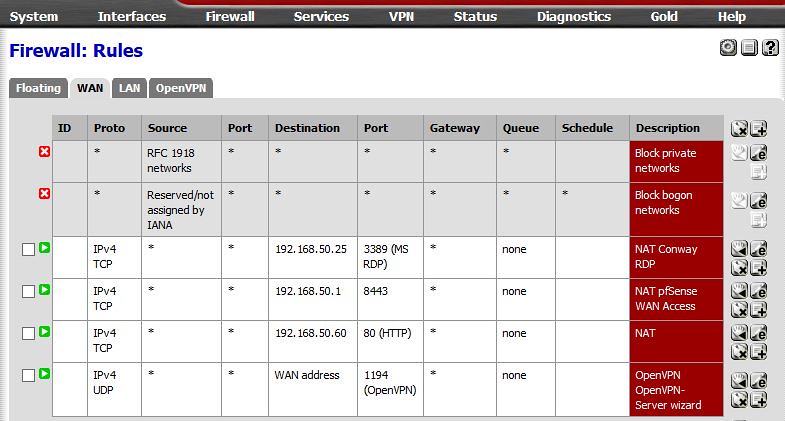 pfSense Firewall Rules by Jon Kensy, on Flickr
pfSense Firewall Rules by Jon Kensy, on Flickr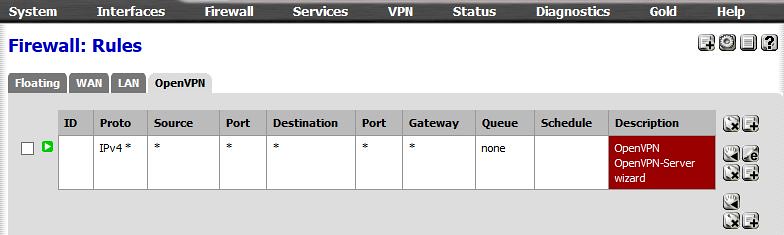 pfsense OpenVPN FW Rules by Jon Kensy, on Flickr
pfsense OpenVPN FW Rules by Jon Kensy, on FlickrHere's the ovpn file that is exported from the pfSense firewall and is what is used on the client:
dev tun
persist-tun
persist-key
cipher AES-256-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote <redacted>1194 udp
lport 0
verify-x509-name "bridgetownovpn" name
auth-user-pass
comp-lzo<ca>–---BEGIN CERTIFICATE-----
redacted
-----END CERTIFICATE-----</ca>
<cert>-----BEGIN CERTIFICATE-----
redacted
-----END CERTIFICATE-----</cert>
<key>-----BEGIN PRIVATE KEY-----
redacted
-----END PRIVATE KEY-----</key>
<tls-auth>#2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
redacted
-----END OpenVPN Static key V1-----</tls-auth>
key-direction 1So basically the other router (the client, Asus AC68) knows to route requests for 192.168.50.x through the gateway on that side (192.168.1.1), but my machines either do not know what to do with requests for 192.168.1.x or my gateway (pfSense 192.168.50.1) doesn't handle them.</redacted>
-
Also very interesting - when you go to create an OpenVPN setup through the wizard in pfSense there's no field for "remote network", however when you go to create an OpenVPN server setup without the wizard there's an option that says:
Remote networks : [ ]
These are the IPv4 networks that will be routed through the tunnel, so that a site-to-site VPN can be established without manually changing the routing tables. Expressed as a comma-separated list of one or more CIDR ranges. If this is a site-to-site VPN, enter the remote LAN/s here. You may leave this blank if you don't want a site-to-site VPN.That's sounding exactly like what I need - so it seems the wizard does not offer the same options as the non-wizard?
-
The wizard is for Remote Access (Road warrior) setups. Not site-to-site.
-
The wizard is for Remote Access (Road warrior) setups. Not site-to-site.
Yep! Figured that out now lol.
Got it going with the standard setup for site to site using just shared key.
Thanks guys - both sides ping!