How to disable ipv6 logging.
-
Greetings.
Is there any chanse to turn off ipv6 logs in firewall? They're flooding logs. Ipv6 is turned off at all in pfsense and blocked by firewall rule, but the logs keep going and going. Help!
-
Whooops. Suddenly founded answer.
Logs won't wrote in one and only one situation — if ipv6 is turned ON and blocked without logs.
Any other combinations of options will begin log flooding.It's illogical, but it works. O_o
-
Nothing illogical about this. There's no "disabling" of IPv6. The only thing done by the checkbox is blocking all IPv6.
-
Port 5355 is Link-Local Multicast Name Resolution (LLMNR).. You could turn it off at what is sending it, would assume your not using it. I don't think pfsense supports it??
To remove the noise from the logs, you could either create a specific rule to ff02::1:3 and block, allow and not log or just turn it off at the source so traffic is not sent in the first place. I would suggest turn it off at the source unless you have specific need/use of it. I don't find that protocol of much use IMHO.
That 547 to :2 is dhcp ipv6.. I would suggest if not using ipv6 to disable it at the clients so they don't send out ipv6 noise. It can be log cluttering ;) If windows boxes its simple reg key to disable all of ipv6..
reg add hklm\system\currentcontrolset\services\tcpip6\parameters /v DisabledComponents /t REG_DWORD /d 255
Simple remove the key if you want to put it back to how out of the box.. I find MS choice of turning on every single ipv4 to ipv6 conversion service teredo, isatap, 6to4 PITA and noisy.. If your wanting to use/play with ipv6 then take the time to correctly set it up for you network.. You will find less noise in your logs that way :) of or not yet ready to get your feet wet its better to disable the noise at the source than just not log it at pfsense.
-
Port 5355 is Link-Local Multicast Name Resolution (LLMNR).. You could turn it off at what is sending it, would assume your not using it. I don't think pfsense supports it??
The problem is that it's, hmm… multicast. It's not that pfSense is using it or not, this LAN traffic simply hits the firewall by design. (Any Windows box will produce tons of these.) Even enabling IPv6 does not get rid of the useless noise, you need to allow it instead. I filed a bug about this pointless blocking and got an answer that it's by design, so I gave up and did this instead:
Aliases:


FW rules (LAN):

-
Agreed it will hit pfsense by design.. Be it pfsense should allow it or block it out of the box is valid question.
I just by habit turn off protocols not in use at the source of the problem - in this case client that has it on by default.. Which most likely the user has no real need of.. Or devices that even support answer it other than other windows machines.
-
Nothing illogical about this. There's no "disabling" of IPv6. The only thing done by the checkbox is blocking all IPv6.
I didn't want to block it. I wanted not to write IPv6 blocks in firewall log.
-
I didn't want to block it. I wanted not to write IPv6 blocks in firewall log.
Considering the checkbox descriptions says it ONLY blocks all IPv6…. not really sure what to add here.

-
I have firewall rule, blocking IPv6 with option «Log packets that are handled by this rule» turned off. If IPv6 enabled — it works. If not — it doesn't.
If that IPv6 checkbox really blocks all IPv6, that's not the problem. The problem is: if the global blocking option exists, it shouldn't log all operations without any possibility to change that.
-
@doktornotor I have similar rule/aliases for the same thing. Only difference since I more then 1 LAN interface; I applied them to floating rule and select all the lan interfaces I want it enabled on.
-
searched "pf sense turn off ipv6 logging" and was brought here. Does not look like anyone had a good answer.
(I just ran into the same issue)
I fixed it by going into the logging settings and unchecking "Log packets matched from the default block rules in the ruleset". And this worked. Be sure to add logging for any other defaults you did want.
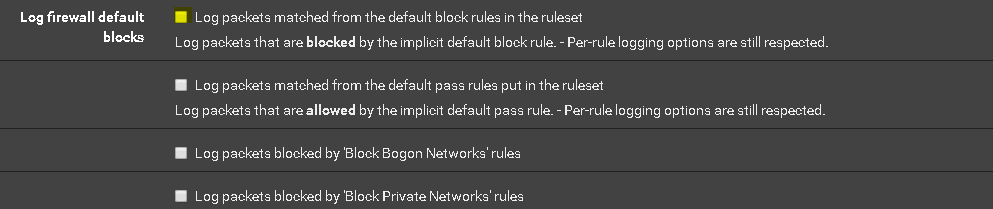
-
This is very easy to do, and its the same way I do it on our routers ACLs.
- Disable logging of default rules
- Create a new IPv4 deny all rule (keep it disabled) with logging enabled.
- Move it to the bottom and enable it.
Now only IPv4 blocks get logged,.
Ive also disable all the pfblocker logging etc, so I only log denied IPv4 of my devices. Makes troubleshooting easier
Also to "filter"out spesific noise, create new spesific deny rules above this bottom rule with logging disable. I do this with for example tcp 137 (netbios) andf other noise i dont care to log.
-
This post is deleted!