Site-to-Site OpenVPN…only access from server, not client
-
I finally upgraded the client side of my Site-to-Site VPN setup to a virtual instance of pfSense (perviously DD-WRT) today. My OpenVPN server is already a dedicated pfSense box. Both server and client setups seem simple enough to configure, yet I'm only getting access to the client local network from the server local network but not from the client to the server. So I can ping/access file shares from the server side but if I'm on a host from the client side I can't ping or access anything on the server side.
I figured it was probably a firewall rule and not a routing issue since it's clearly routing in one direction. However my firewall rules are identical on both ends. You can see what I configured in the pics below.


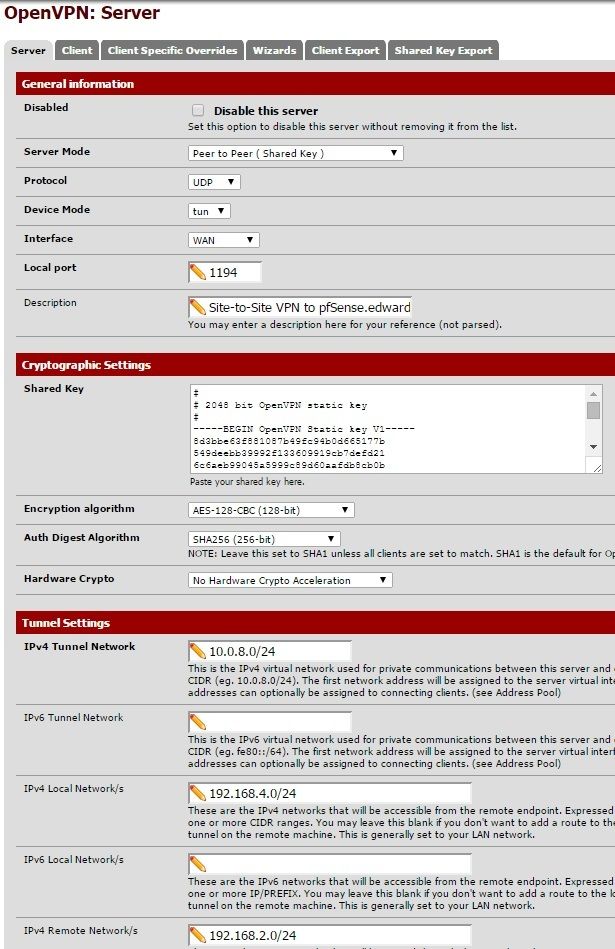
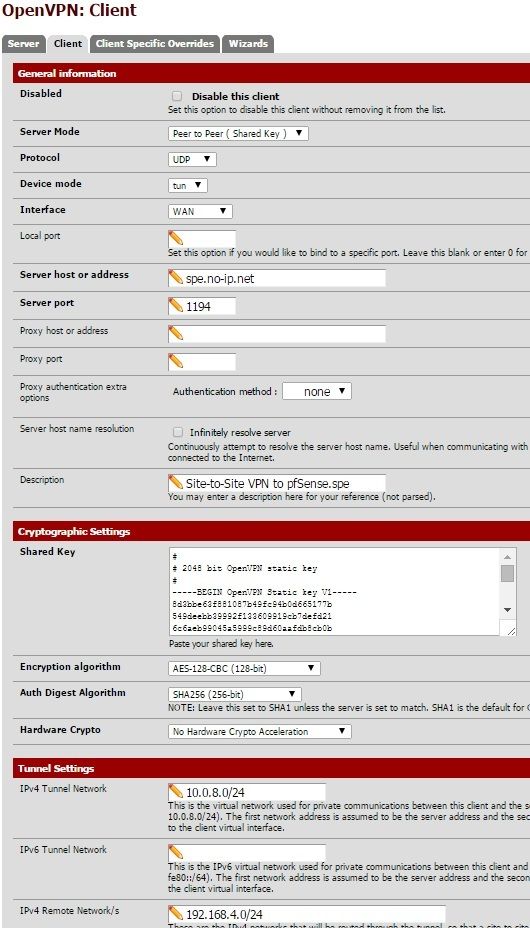
-
What networks are what? What are the firewall rules on all the interfaces in question and the OpenVPN interfaces/tabs on both sides?
-
What networks are what? What are the firewall rules on all the interfaces in question and the OpenVPN interfaces/tabs on both sides?
OpenVPN Server local network is 192.168.4.0/24.
OpenVPN Client local network is 192.168.2.0/24.The firewall rules shown in the pics above (which are configured on both the client and server) are the only ones configured other than 2 NAT rules I have for allowing access to my Plex Server and for RDP (which will go away once I fix this VPN issue).
I've even tried putting ANY/ANY rules on both the LAN and WAN interfaces (I already have one on the OpenVPN side right now) on both the server and client to eliminate the firewall as the issue. That didn't fix it.
-
Man that is weird. It's like the ANY/ANY rule I had in my OpenVPN tab of the Firewall rules wasn't applying. As soon as I added an easy passing rule through the firewall log for ICMP traffic that started to pass. Removed that rule, and now everything is passing. I don't get it but at least it's working for the time being.
-
Your rule on OpenVPN was TCP only. Ping is not TCP, it's ICMP. Many protocols are not TCP.
-
Your rule on OpenVPN was TCP only. Ping is not TCP, it's ICMP. Many protocols are not TCP.
Wow. I must have looked at that rule and compared like 10 times and still missed that. Yesterday was not my day. I guess 12 hours of upgrading everything on my entire home network took a toll on me.
Thanks for that catch.