Share your pfSense stories!
-
Quick story here, just to confirm a point about ProxMox adapter performance.
I set up pfSense 2.4.5-RELEASE-p1 (amd64) on ProxMox on Friday, and when I was creating the VM it was crashing if I used the Virtio Parallel driver for the NICs so I changed to E1000.
After install eveything worked but bandwidth throughput was slowed by half.
I shut down pfSense and changed the NIC drivers to Virtio and started pfSense back up.
On boot pfSense ran through interface assignments, but I was pleased to find that once I was back up and running, none of my configurations had been lost and everything was working as it should.
I did have to reconfigure the Snort interface in order to get Snort running again but once I did that everything was running well.
I ran speed test again and got full bandwidth and pfSense is running great.
Moral of the story is anyone having throughput problems on ProxMox deployments, needs to make sure they are using the Virtio Driver (where supported) because it does make a huge difference (at least from my experience with Intel NICs)
My set up is:
2.4.5-RELEASE-p1 (amd64) with Snort in VM on ProxMox 6.2-4
On HP T730 thin client 64GB M.2 SSD, and 16GB Memory
Intel EXPI9404PTLBLK PRO/1000 PT 4-Port PCIE NICSean
-
Hello
I have been working in the IT business my whole career.
When I retired I was not aiming as being a "couch potato" so I search for an activity as a volunteer
and I discover Emmaüss Connect a caritative French association.Emmaüs Connect fights for the digital inclusion of the most vulnerable people in France,
where a quarter of the population is unable to use the internet on a daily basis.I joined the local team in Lyon France where I provided lectures regarding basics used of laptops, smartphones
and tablets.From an IT side I found that the small local network didn't have any protection aka the cable modem/routeur
was directly connected to the PCs.Talking to the local responsible I suggested that we implement some basic strategy to protect our local network.
The constraint was to make it at 0 Euros as you may understand.
After looking around on what was available on the software market I choose pfSense because it got an excellent
reputation, it was modular and available to be implemented on a recycled PC.So I moved that way and with the help of the pfSense user forum and the many excellent tutorials available on Youtube
I end up with a pfSense configuration that is now up and running 24 hours a day.
The Firewall protects our small network.
I also added the following packages:pfBlockerNG : to filter what is going out because we don't want people going to "bad" sites using our network.
Captive portal : so we can provide free vouchers to the people we are supporting to use our network to connect to the internet.
OpenVPN : so I can do remote monitoring/maintenance on the firewall.I like to really thank the whole pfSense community for the great product they have made and keep maintaining actively.
I will be a real advocate for it.
If anyone is in the same situation I will be happy to help/share.Thanks again
Pierre -
I'm not sure how well this fits in with the topic, since I'm not a network admin or engineer, and I've only been using pfSense for a short time for my home network.
I had been using some consumer-grade routers at home and found them unsatisfactory, often unstable, and generally unreliable.
I had tried an inexpensive brand of routers that was less consumer-oriented and that worked ok. I also tried one of the mesh systems and that worked ok too. Neither was really ideal though.
Some of my friends and co-workers had been telling me I needed to switch to pfSense. I resisted at first because I thought it would be overkill. I looked at the Netgate appliances and thought the SG-1100 might not be enough to allow for future growth and the SG-3100 seemed too expensive.
I also wanted to try Untangle, IPFire, Sophos, and another project that I won't name.
I got some hardware and tried these out and it didn't take long to decide that pfSense made the most sense to me and offered the features that I wanted. It was really easy to install and configure and has great docs.
I've since found that some of the features I originally wanted, like Suricata, really didn't add anything for me at this time. I also talked to some people and found that faster internet is going to be a long time coming to my neighborhood, so I'm not going to need to handle gigabit speeds anytime soon.
The SG-1100 would probably have been ideal for me, although I wouldn't have been able to try the other software on it, so it didn't seem as attractive until I really decided that what I wanted was pfSense. (The SG-2100 arrived a bit too late, but would have been an excellent choice too.)
pfSense is the router/firewall for me. It feels comfortable and I'm looking forward to learning even more about it and finding ways to make it even more useful and informative.
-
I just wanted to run pfSense virtualized and discovered that it is not possible. - The thread got hijacked by a whole load of senior members who seem to believe that virtualization is all about dual-booting (hardly) and ProxMox was recommended.
No problem there, but ProxMox is hell to run, will not install pfSense, and does not like anything but Debian distros. VMWare, on the other hand, can be made to run on Windows, but software pfSense will not work with it, and cannot be used for PPoE IPv4 with PPP IPv6 ...so absolutely useless; especially so bearing in mind that, even given all the right DNS information, it absolutely refuses to connect to your ISP on FTTP connections even with the ethernet cable plugged directly into the mainboard.
Thank goodness for Draytek: the experts are right when they say that pfSense (and others) cannot even come close to them and, more importantly, at least they work.
-
@2RTzC5KbQGH4aG I'm glad that you found something that works for you, but I've never heard any "experts" recommending Draytek. :-)
I've worked in IT for many years and I think this is the 2nd time I've even heard Draytek mentioned. They sort of remind me of Zyxel, and that's not really a good thing.
BTW, I know people who run pfSense virtualized and some of those are using ProxMox. I don't use Windows, so I can't comment on that. As for ProxMox not liking anything but Debian, that's simply not true.
Again, I'm glad that you've found something that works for you, but my experience with pfSense has been completely positive.
-
@2RTzC5KbQGH4aG said in Share your pfSense stories!:
I just wanted to run pfSense virtualized and discovered that it is not possible.
That's an absolute load of... I run many, many PFsense installations like virtual machines in both VMware and Hyper-V and it works great.
Thank goodness for Draytek: the experts are right when they say that pfSense (and others) cannot even come close to them and, more importantly, at least they work.
The one who proclaims Draytek over PFsense clearly haven't got many miles on their back. I agree it's somewhat like Zyxel, and that's saying a lot. Its just a load of manure. Probably a sales pitch that stuck. Nothing more.
PFsense can compete with the best. I would argue it's in class with Cisco, any day. I've had serious relationships that lasted shorter than the uptime in PFsense. And the possibilities are literally endless (well as long as we're talking networking of course). And to have a GUI beats Cisco every day.
Go back, analyse your notes and come back when you realised where you were wrong.
-
@2RTzC5KbQGH4aG said in Share your pfSense stories!:
The thread got hijacked by a whole load of senior members who seem to believe that virtualization is all about dual-booting (hardly)
WHAT? That thread your talking about... You stated and I quote
"Would like to setup a Dual Boot with pfsense on a Lap top."Now your saying you wanted to run it as VM? From that thread, and your statements here it is quite clear you have no clue to what your talking about.. You seem to be a troll and nothing more..
-
come on.... my isp gave me a Zyxel, it's good if you put it in bridge mode and let pfsense manage everything ....

-
@kiokoman I'd rather have my liver taken out.
-
@kiokoman Based on my experience, Zyxel has a high failure rate. We saw a lot of them DOA when you opened the box. Then they'd fail over the first year of service. We speculated that they were using very low-quality parts or didn't put heatsinks were they were needed, etc.
Worst of all was the ones that would fail, but not completely. People would be complaining of assorted problems with their internet connection, and when you went to diagnose and troubleshoot maybe you'd find something and maybe you wouldn't. Or the issue would come and go. After a couple of go-arounds, a replacement of the hardware would resolve it - for a while.
Zyxel was inexpensive to purchase, but it wasn't cost-effective.
-
@stuartkh42 said in Share your pfSense stories!:
Zyxel was inexpensive to purchase, but it wasn't cost-effective.
Precisly. Amen.
Intermittent problems are the most expensive ones, because they are time-consuming and create the most miserable users which reflects poorly on us.
-
well.. I'm using it only as a modem .. everything else(router/wifi/voip/firewall/dhcp/share) is disabled / turned off... I had it for free from my isp. no problem so far.. I will think about it when the problem arises. I already have a couple of other modems as a spare part

-
I've been using pfSense for about 5 years after my Linksys router running DD-WRT was no longer able to keep up with the speed of my internet connection.
I am so thankful for the pfSense project, the community is friendly/helpful, the documentation is good, and the software is very professional/stable. A sharp contrast from what I was using.
When our ISP rolled out IPv6, I read that anyone using the ISP provided hardware as it was configureded was exposing all their Windows file/printer shares on the LAN to the internet! Many consumer routers contain serious security flaws and corrective updates are slow or nonexistant.
pfSense allows me to easilly treat the ISP equipment as part of the untrusted internet. pfSense makes it possible to manage and secure my network using enterprise techiniques that would be impossible with consumer equipment. Secure remote access, Multiple VPNs, VLANs, IDS, IPS, IP/DNS Blocking, Proxies, Reverse Proxies and Enterprise Grade Firewall, pfSense has it all, and more.
There are some very bright and talented people in the community who really care working with this software, so security gets taken very seriously and the few CVEs that are found get patched very quickly.
For anyone willing to learn how to set it up, (or pay someone) the possibilities are endless and pfSense can't be beat.
-
I came from ddwrt and was looking for some better security, so maybe 6yrs? Just recently started actually "using" pfsense (snort/vlans).
My pfsense system has gone through multiple iterations, with the last motherboard dying. I'm "in the process" of building a new box with the new i3 1200 socket.
So in the meantime I pulled out some random board I had bought back in 2014 and loaded my config on it and it blew me away at how well it runs with +/- 40 clients and two people working from home with mucho teleconferencing.
My current setup (Don't laugh too hard)
J1800 motherboard
1x pcie 2 port intel nic
1x ssd
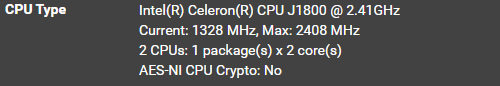
It literally sits on top of a shelf with an atx power supply next to it (It's fun trying to remember which pins to jump to boot the system).
I have snort and multiple vlans running and it supports my gigabit connection just (If snort is configured correctly, that's another "in process" thing).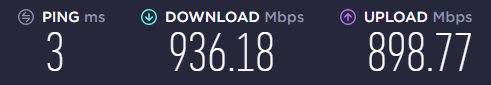
-
@nullvalue
If the PSU has colored wire's it will be the green wire and any black wire. -
Former organisation hunts companies who are practicing corruption, collusion and nepotism. Usually, these organisations do hostile takeover of other companies. The organisation's goal is one organisation to control them all.
Short story, me and a few of my colleagues resigned because of their new policies against our conscious and moral values. Remember! Just do the opposite of what this organisation tells you. If they advised you and your family to implant microchipped (WO/2020/060606) for (Covid) prevention, refuse it. When they tell you don't use an open source OS/firewall/router like pfSense, use it. That's my story on why I use pfSense.
-
Home user, but I have been using pfSense since 2014ish.
My first install was on an Intel DQ77KB, and that was fun and worked great.
Later, I moved to virtualize pfSense in ESXi for around 2 years (stable, but was a bear to properly configure).
Currently, I have my install on a Pcengines APU2. It works perfectly other than a weird issue with an upgrade to OpenVPN causing a boot hang (had to use my serial to see the error).
The weakness of pfSense is wireless, but that seems to flow from the underlying FreeBSD.
I will post an update about a new project: a "DIY Nighthawk X10," which is a wireless router/NAS/Plex box. Unlike some other people, I don't need AC-wireless and would prefer an older, but stable platform.
Cheers!
-
@garrett-0 said in Share your pfSense stories!:
Home user, but I have been using pfSense since 2014ish.
My first install was on an Intel DQ77KB, and that was fun and worked great.
Later, I moved to virtualize pfSense in ESXi for around 2 years (stable, but was a bear to properly configure).
Currently, I have my install on a Pcengines APU2. It works perfectly other than a weird issue with an upgrade to OpenVPN causing a boot hang (had to use my serial to see the error).
The weakness of pfSense is wireless, but that seems to flow from the underlying FreeBSD.
I will post an update about a new project: a "DIY Nighthawk X10," which is a wireless router/NAS/Plex box. Unlike some other people, I don't need AC-wireless and would prefer an older, but stable platform.
Cheers!
It's way easier to buy a Ubiquiti Unifi AP AC Lite for €60 and run the controller on the pfSense:
https://github.com/gozoinks/unifi-pfsenseI have roughly 100-150 of those exact installations out there running perfectly for at least 3-5 years. For larger installations just add a switch and more APs. And for high density environments just replace the Lite with Pro. You can easily handle up to a thousand users this way, probably more. The largest such installation I have is running pfSense on an APU2, five or six switches and about thirty mixed Lite and Pro APs. About 800-1000 devices divided on 4 VLANs. Works like a charm.
-
I had always wanted my own server setup for various things. I was advised by a friend to get a firewall as well. This is where I started looking into different options for my own home firewall for my network which will be getting quite extensive. I came across pfSense. I watched youtube videos about it and had read the forums for a few weeks before really delving into it myself. Started out with an old Watchguard X750E when pfSense was still supporting x86. When pfSense went fully x64 I was thrilled. I knew that 64-bit can really do a lot more and offer more. Tho I did have some issues getting it going I was able to do so with help from others in the community.
I have since upgraded my old X750E to a Watchguard XTM550 with the latest version of pfSense. Love it. Will not use another firewall for anything. Simply love the setup and ease of use. Am quite happy with the software. Does more than I could ever dream of and allows me the ability to learn more and more as I go. I can't wait for pfSense Plus to be supported across 3rd party hardware as I really want to have it installed on my XTM550. It will offer so much more for me at home and it will be able to be setup quite easily. Thanks for offering a really nice piece of software. I really don't know what else I can say. It is just that much of a nice thing to have.
-
Okay, I'll add my story now.
For years I've had issues with wifi connectivity throughout the house, and over the last couple of years my wife would complain about the wifi printers not working. At first I thought my routers were just old, so I paid more money to upgrade a D-link to a Netgear, then to another Netgear, and you know that story. Wifi would improve slightly, and seemingly quite well for the first while, but ultimately after a few months wifi got worse, and wifi printers started dropping again.
Then I started researching enterprise level routers and the name Netgate came up. The installation was sure a steep learning curve for me, and even now I would consider myself a sub-novice at it. But I got it up and working. But I was still using the old Netgear router as an wireless AP, and guess what? My wifi printers were still dropping and I still had lousy Internet at the opposite end of the house.
I have since added two Unifi Lite AP, one on the top floor, one on the main floor. I keep them on medium power and wifi is fine. Even on basic 20 Internet, we can Zoom call, watch TV on the Roku, and surf Youtube all at the same time. I haven't lost the wifi printer once in the 6 months I've had this set up.
I know I've wandered into a field I probably have no business mucking with, given my knowledge, but it works better than the consumer junk I had. I even started making my own cables so I could make specific lengths, and connect the Unifi APs.