DNS Doctoring in pfsense
-
Hi All,
Is there any similar feature to Cisco DNS Doctoring in pfsense ?
here's a link to describe what DNS Doctoring is: http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/115753-dns-doctoring-asa-config.html
The story is: I have GRE over IPSec VPN from our Headquarter to another site, and we are NATing our local IP addresses when the trafic goes toward the remote site.
What I want, when someone in the remote site look up for the IP address of my local machine, I want him to get the NATTed IP address, not the real local IP addresses (Exactly like the case in the link above)
I'm using virtual pfsense FW, version 2.1.5-RELEASE. Please let me know if you need any more information !!
Thank you all in advance
Best regards,
Jameel -
No its not going to do anything like that… But to be honest a better solution would most likely just run bind and use views so queries from source network other site would get the IPs they are suppose to get.
You can install bind on pfsense, not sure if gui gives you enough control for the views to have different IPs for records.. But for sure bind can do that..
-
Thank you johnpoz,
I'm using dnsmqasq, can it do the same function ??
-
I do not believe so, nor can unbound that I am aware of.. But could look.. Since both dnsmasq and unbound are really only caching servers and not really meant to be authoritative for domains I do not believe they offer such features. But they do have some fancy stuff you can do via advanced options that might provide such a feature.. Will have to look.
edit: Ok let me do some testing, it seems dnsmasq supports a localise-queries function… Which could be used to resolve an IP that is in the same network that the query came from
-y, --localise-queries
Return answers to DNS queries from /etc/hosts which depend on the interface over which the query was received. If a name in /etc/hosts has more than one address associated with it, and at least one of those addresses is on the same subnet as the interface to which the query was sent, then return only the address(es) on that subnet. This allows for a server to have multiple addresses in /etc/hosts corresponding to each of its interfaces, and hosts will get the correct address based on which network they are attached to. Currently this facility is limited to IPv4.
So this might not work for your specific scenario where your natting... But it might, but this same sort of question came up in another thread.. Which pretty sure it will for sure work for.
edit: So in the other thread I did a simple test that shows this works for dnsmasq
https://forum.pfsense.org/index.php?topic=106872.0
Where I did queries from 2 different networks and got answers with IPs from that network.. But not sure this going to work in your nat setup if the IP you want to hand back is not in the network your query came from.
-
I know this is really old, but I am having trouble finding any more recent discussion. dnsmasq has a feature called
aliaswhich allows replacing the IP addresses for returned results. It would be cool if this could pull automatically from the 1:1 NAT settings. I don't think unbound has a similar option.-V, --alias=[<old-ip>]|[<start-ip>-<end-ip>],<new-ip>[,<mask>]
Modify IPv4 addresses returned from upstream nameservers; old-ip is replaced by new-ip. If the optional mask is given then any address which matches the masked old-ip will be re-written. So, for instance --alias=1.2.3.0,6.7.8.0,255.255.255.0 will map 1.2.3.56 to 6.7.8.56 and 1.2.3.67 to 6.7.8.67. This is what Cisco PIX routers call "DNS doctoring". If the old IP is given as range, then only addresses in the range, rather than a whole subnet, are re-written. So --alias=192.168.0.10-192.168.0.40,10.0.0.0,255.255.255.0 maps 192.168.0.10->192.168.0.40 to 10.0.0.10->10.0.0.40
-
@yakatz at the bottom of dns resolver settings is host and domain overrides :)
-
@sparkyMcpenguin That is different. Let's say my public IP address is x.y.z.10 and that has a 1:1 NAT mapping to 192.168.100.10. The alias feature would allow me to change any returned A record that contains x.y.z.10 to 192.168.100.10 without knowing about it in advance.
One example use case where this would be extremely useful: We have a cPanel server using 1:1 NAT, and our customers can add new subdomains or hosts as they please, so we can't specify them all in advance as host overrides. This feature allows split DNS to work transparently with this use case because the IP addresses are replaced on the fly.
-
This post is deleted! -
@yakatz
virtual IPs under firewall? -
@sparkyMcpenguin Any of those options assume that you are working with specific hostnames. I am talking about having it work based on the IP address returned in the record. dnsmasq has built-in support for this, so I am suggesting the config be automatically built from the NAT configuration. (It looks like unbound might be able to use a python filter, but that is probably a lot more complicated.)
-
Live configuration from one site:
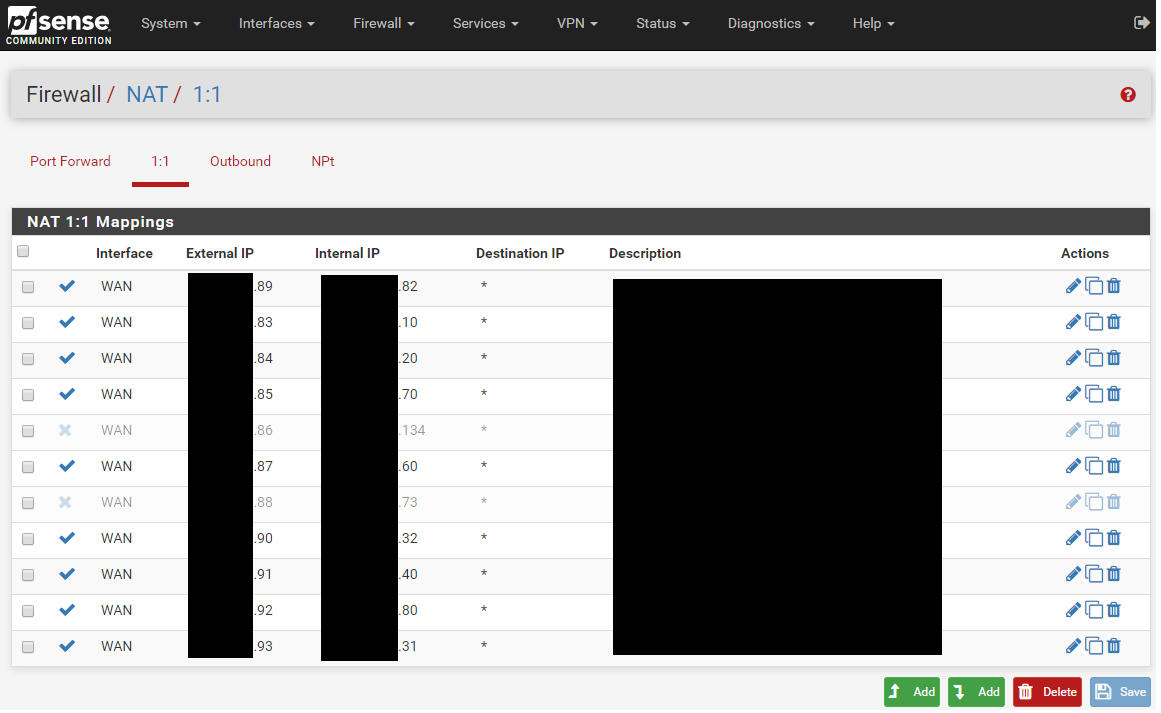
-
@yakatz
under system > advanced> network address translation -would NAT reflection options be useful for this?
-
@sparkyMcpenguin We have tried it, but we could never get it to work reliably, possibly because of our multi-WAN, multi-LAN and VPN configuration.
-
@yakatz
out of curiousity how many different DNS resolvers (for system use, not what is given to clients) are set up? also is there a dynamic dns configuration? -
@sparkyMcpenguin All static IPs. We are current;y using unbound, so no upstream DNS servers.
-
@yakatz only unbound (and assuming the Root servers)?
so in general settings there's no added dns, what about 'allow override on wan' allowing the ISP to override the dns (i personally didn't want this option - in order for me to get my cell phone carrier MMS and wifi calling to work, i had to add extra dns. i started with just unbound and cloudflare. no go on picture messages etc. added google, and those features started working. added quad9 for a third cause i like redundancy
getting to the rest of my thought, when was the last time a reboot, or states reset? pfblockerng packet counter clear (if applicable - this affected me on certain things)
-
@yakatz said in DNS Doctoring in pfsense:
@sparkyMcpenguin All static IPs. We are current;y using unbound, so no upstream DNS servers.
my logic with redundancy in my dns resolver choices is "i dont trust just one source". if that source gets corrupted or altered (lol sorta like what youre trying to do, but you're doing it for a legitimate thing) then im sure there's billions more ip addresses out there to tell everyone else that your IP result is incorrect(?)
when i added more than one DNS i also changed my ASN check settings to 1 hour (just cause i want it to update faster - i assume the default 24 hours would cause ... 24 hours wait time for the change to take effect, for verifying the cache in unbound)
-
@sparkyMcpenguin Currently 31 days uptime, was about 600 days until a recent reboot. Never had any problems with DNS using unbound in resolver mode.
-
@yakatz said in DNS Doctoring in pfsense:
@sparkyMcpenguin Currently 31 days uptime, was about 600 days until a recent reboot. Never had any problems with DNS using unbound in resolver mode.
31 days, is that when the problems started?
-
@yakatz said in DNS Doctoring in pfsense:
@sparkyMcpenguin All static IPs. We are current;y using unbound, so no upstream DNS servers.
my bad i misread this. when i said dynamic dns i meant an external dyn dns service to resolve your isp given ip address, not dhcp from pfsense