ATT Uverse RG Bypass (0.2 BTC)
-
It's possible the authentication always takes a while but you wouldn't normally see that because the AT&T router does it before pfSense even connects in the double NAT setup. In the bypass mode the auth can only start once pfSense bridges to the router when it sets up the WAN. It seems unlikely it should take anything like 75s though.....
I don't have an AT&T connection to test. -
Since you can't really eliminate the newer AT&T gateways completely (thanks to AT&T's certificate-based authentication and integrated ONT module), then I don't even see the point of doing this. I just put mine in IP passthrough mode with my public IP going over to pfSense along with my /29 block and I haven't had any issues with latency or dropped packets. AT&T reboot time is still only about 20-30 seconds.
-
Mmm, interesting. Yeah I wouldn't expect the auth to take more than a fraction of a second really. Let's see if anyone else is seeing a delay there.
-
@stephenw10 Just to clear up any confusion, when I said 20-30 total reboot time, that is basically from powered off to a solid green light on the gateway. IP Passthrough mode (essentially bridging) does not add any additional time to the reboot cycle because it's still doing the auth.
-
@DefenderLLC I understand your sentiment, considering you're still stuck with the gateway using this bypass method. I liked the idea of putting the gateway behind my firewall, but it also made it easier to co-locate my network hardware with an UPS...the ONT is in a weird spot in my house. As a secondary benefit, I've noticed a slight to moderate increase in overall performance.
I've yet to see a speedtest actually reach full gigabit speed, but before the bypass I'd hit around 800Mbit with latency of 15 to 20 ms. After the bypass I'm hitting roughly 920Mbit with 8-10 ms latency. It's minor and surely not noticeable to my dulled senses, but it's measurable.
I haven't accessed the gateway itself since the bypass...Setting it up on a 'modem' interface keeps me from getting at it via the ol' 192.168.1.254, but I may see if I have time to mess around and look into the RG logs if they're easily accessible.
-
@darkphox said in ATT Uverse RG Bypass (0.2 BTC):
@DefenderLLC I understand your sentiment, considering you're still stuck with the gateway using this bypass method. I liked the idea of putting the gateway behind my firewall, but it also made it easier to co-locate my network hardware with an UPS...the ONT is in a weird spot in my house. As a secondary benefit, I've noticed a slight to moderate increase in overall performance.
I've yet to see a speedtest actually reach full gigabit speed, but before the bypass I'd hit around 800Mbit with latency of 15 to 20 ms. After the bypass I'm hitting roughly 920Mbit with 8-10 ms latency. It's minor and surely not noticeable to my dulled senses, but it's measurable.
I haven't accessed the gateway itself since the bypass...Setting it up on a 'modem' interface keeps me from getting at it via the ol' 192.168.1.254, but I may see if I have time to mess around and look into the RG logs if they're easily accessible.
AT&T generally oversubscribes the service, but if you’re using a 1 gig port from the gateway to your LAN of course you’re not going to get any speeds faster than that. Port number 1 (the blue one) is a 5 Gb port on the newer models and will step down to 2.5Gb or 1Gb. Now the ONT modules are built into the modem itself. You have no choice but to use it.
I went back to the one gig service and this is what I get from my UDM-SE which sits behind my Netgate 6100 MAX with IPS enabled on both firewalls (dual NAT).
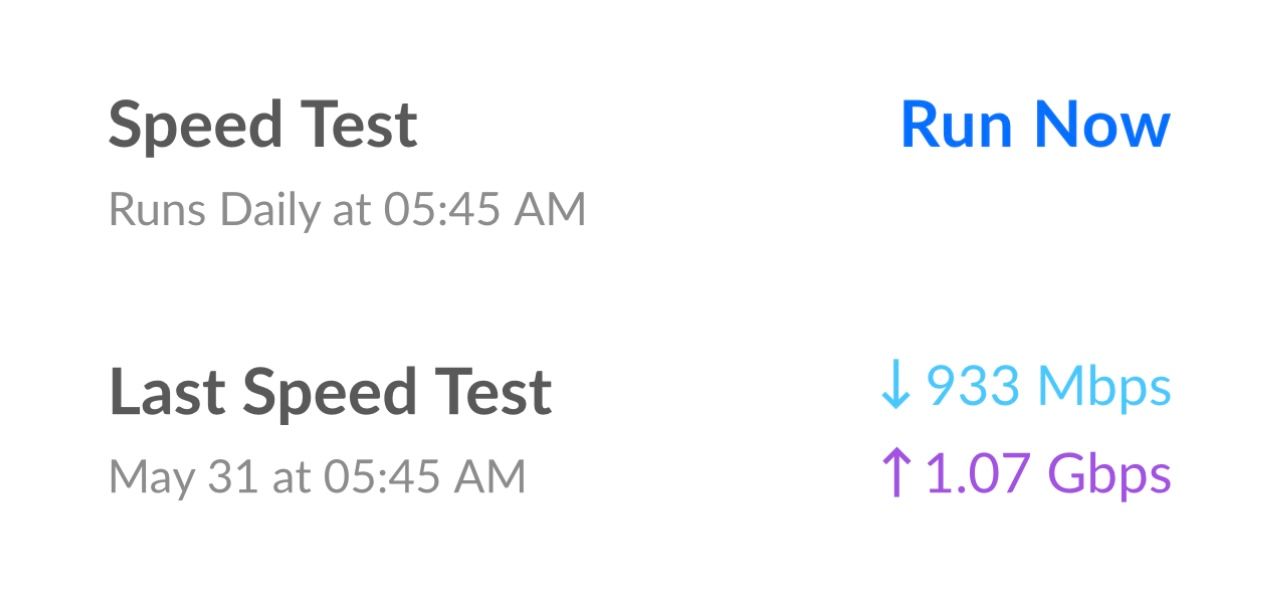
-
Hey AT&T folks! I'm new here and do want to be frowned at for double posting. I have a AT&T Pace 5268ac and got the new Bypass to work but every 24 hours for ~90 minutes the modem interface drops and reconnects every 2-3 minutes. If you might know how to help please jump over to my post.
Thanks!
-
@DefenderLLC would it theoretically be possible if you had a pfSense box that had a fiber input used as WAN? Unless there's a reason someone is using that same certificate type that's using the Ethernet rule. I don't have either but was curious if someone may have tried that option.
-
@Zaf9670 said in ATT Uverse RG Bypass (0.2 BTC):
@DefenderLLC would it theoretically be possible if you had a pfSense box that had a fiber input used as WAN? Unless there's a reason someone is using that same certificate type that's using the Ethernet rule. I don't have either but was curious if someone may have tried that option.
You cannot do this with the newer AT&T gateways like BGW320 (newer installs in the past 2 years). The ONT module is built-in to the modem itself and it must be used in conjunction with the SFP+ module that they provide to authenticate the service. There's no getting around it for new AT&T Fiber installs unless they happen to give you an older modem and separate ONT box which would be very rare unless they have no way to get the fiber to the modem directly.
-
Thanks to C McDonald (@cmcdonald ), there's a new wpa_supplicant out which now listens on vlan0. Netgraph or vlan stripping switches no longer needed.
code
https://reviews.freebsd.org/D40442You can either compile your own or get the binary in this thread on dslr
source - https://github.com/freebsd/freebsd-src/tree/main/contrib/wpa
binary (for 23.05) - https://www.dslreports.com/forum/r33686937-
Future versions of pfsense will come with the new binary.
As this is using wpa_supplicant, certs are still required. Existing wpa_supplicant.conf is still usable.
For implementing, 2 shell command lines are really all that's needed.
earlyshellcmd
/sbin/ifconfig igb0 ether "RG MAC" && /root/wpa_supplicant -B -Dwired -i igb0 -c /root/wpa_supplicant.conf -P/var/run/wpa_supplicant.pid && sleep 10 && /usr/sbin/wpa_cli logonAdjust paths and interface as needed. RG mac should be in the form of "11:22:33:44:55:66". Probably works without the double quotes, but given the sequence contains colons, quotes preferred.
shellcmd
wpa_cli logoff && sleep 10 && wpa_cli logonDon't forget to update the wan interface to reflect correct interface, not ngeth0. Also for now, mac spoofing still in effect, but we're testing if that's really needed.
This sequence should provide a relatively fast boot, without the 60s delay at the "configuring wan interface..." line. The logon commands are there to speed things up. Normally the upstream sends a username request to the gateway (or supplicant in this case) every 30s until a response is received. The login command expedites this.
In testing, wan ip via dhcp was generally obtained right at the end of boot or within a few seconds after.
-
@GPz1100
The wpa_supplicant.conf is the pfatt.sh correct? Or is there a specific .conf file to get?Thanks
-
@AiC0315 I use the conf that was generated when I extracted the keys
-
@AiC0315 You could use the pfatt script, but will need to modify it to remove all references to netgraph. It applies configuration a bit differently but it's the same values. Also, pf's native dhcp works, so that line too can be commented out.
The command lines I posted earlier are simple enough, don't really see a need for a script. You can add a
-sto enable logging to syslog.wpa_supplicant.conf is the one created with the devicelocksmith tool when generating the certs. You will need to a line early on for wpa_cli to work.
ctrl_interface=DIR=/var/run/wpa_supplicantunder the last comment (#) line.
-
@GPz1100 Thanks, I bought my certs so I don't have the .conf. I have the 5268. not sure if there is a way to get the certs from that without desoldering?
-
@AiC0315 If you got your certs from a seller respecting devicelocksmith's tool license, then you should have just received the mfg.dat and some CA certs. You had to run the tool to generate actual usable (by wpa_supplicant) certs.
If not, the format looks like this.
wpa_supplicant.conf
# Generated by 802.1x Credential Extraction Tool # Copyright (c) 2018-2019 devicelocksmith.com # Version: 1.04 linux amd64 # # Change file names to absolute paths ctrl_interface=DIR=/var/run/wpa_supplicant eapol_version=1 ap_scan=0 fast_reauth=1 network={ ca_cert="{PATH TO CA CERT.PEM file}" client_cert="{PATH TO CLIENT CERT.PEM file}" eap=TLS eapol_flags=0 identity="{RG MAC}" # Internet (ONT) interface MAC address must match this value ie 11:22:33:44:55:66 key_mgmt=IEEE8021X phase1="allow_canned_success=1" private_key="{PATH TO PRIVATE KEY.PEM file}" } -
@GPz1100 I found the original files and was able to get it sorted out. Thank you for your help!!
-
@GPz1100 I'm using the dfp-34x to bypass the AT&T ONT and RG, but curiously, I don't need to authenticate at all with the DFP-34X. Does anyone know why I no longer need to authenticate with wpa_supplicant when bypassing the ONT? I've read conflicting info about whether authentication should be needed or not.
Prior to bypassing the ONT with the dfp-34x, I was using AT&T ONT -> Swtich (strip VLAN0) -> Pfsense, but could not pull IP unless I authenticated with wpa_supplicant.
-
@AiC0315 said in ATT Uverse RG Bypass (0.2 BTC):
@GPz1100 I found the original files and was able to get it sorted out. Thank you for your help!!
It's because the authentication isn't really needed (there is long thread on DSLreports that proves that 802.1x authentication isn't necessary). What is needed is a compatible ont or ont sfp+ (2.5 gig sensing, which isn't in all ont or ont sticks), that is spoofed to the mac address and type of RG. That is why you can bypass the ont and RG. The only hold up was that most firewalls wouldn't recognize vlan0 on the wan. There are numerous people like myself who no longer use the RG and ONT. I do have the 5gig connection so I'm not on the older GPON, I'm on XGS-PON. But it works 100% without extracting certs. I personally have been using the Azores WAG-D20 for about a year now. The only time I have ever had my bgw320-505 powered on is when AT&T had to replace my fiber line when tree cutters dropped a tree on my fiber line and cut it. So they could run a line test.
-
@untamedgorilla Thanks, I've consistently seen that XGS-PON doesn't use authentication in the same way as GPON - but, I'm on GPON. I have seen the DSLreports thread but then again on the discord there are conflicting discussions. I guess I should be happy with it and let it go but concerned its just a temporary fluke in my setup.
-
@DefenderLLC I understand the box is combined but that doesn't necessarily mean the process is different to intercept/use. It sounds like the replies after ours show it has had some mixed success unless the all-in-ones register differently between models.