Virtualize pfSense, two WAN, one switch, possible?
-
Hi everyone,
I am considering to combine my pfSense and my NAS into a rack server. The pfSense will have a 2-port Mellanox ConnectX-2 10GbE LAN Card from PCIe Passthrough. One of the port will be used for PC connection, another will be connected to CSS610-8G-2S+IN 10Gbe Switch.
The configuration is like:
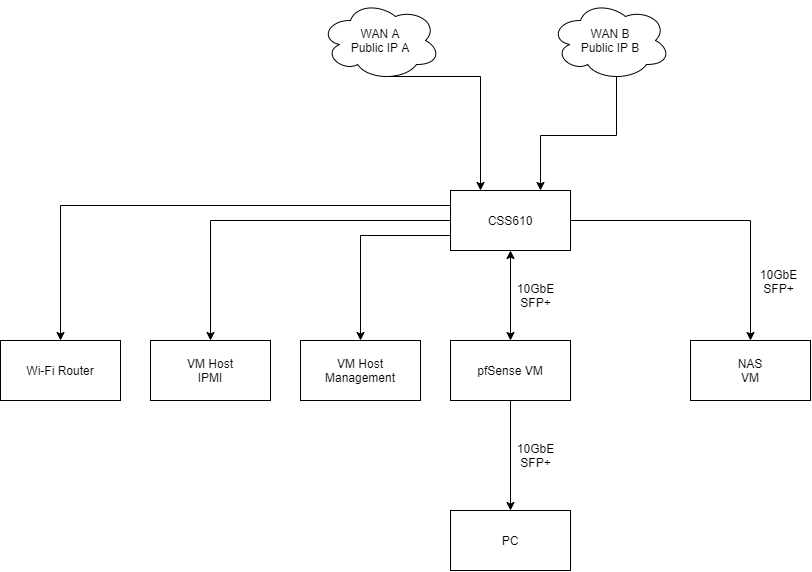
For the LAN Part, I can set the Port-based VLAN ID
xxin switch, set the Port to receive untagged VLAN and create and assign VLANmlxen1.xxas LAN interface with static IP in pfSense.However, I have no idea how to connect the two WAN to the pfSense. In my knowledge, the two WAN have no VLAN tag. Then I suppose both WAN are in VLAN ID 1, which means that I can only connect one WAN to the pfSense
mlxen1.Any suggestion are welcome. Thank you.
-
@testcb00 Put the ISP modem in bridgemode and use IP Alias as the second WAN address.
Then you can forward the traffic as usual.
One thing.... use the second port on the Mellanox as the connection to LAN. Much more secure.
Then you dont need VLANS on the internal network unless you need it for seperating the networks.
-
@cool_corona Thank for your reply, cool_corona.
For the IP Alias, do you mean the settings inFirewall -> Virtual IPs?
In normal setting, I have to set WAN interface's IPv4 Configuration Type to DHCP for getting IP, and the two WAN are from different modem, I am not sure I can use the IP Alias...Besides, the ConnectX-2 just has two ports so I have to use one Port for both LAN and WAN and another Port for PC connection. I will use Port Isolation and make sure that the WAN Port cannot access to Switch Management.
-
Why not just put the two WANs on different VLANs in the switch?
I'm not really seeing the problem here. If you are passing through the NIC to the VM you can do whatever you want.
Steve
-
@stephenw10 Thank for your reply, but I am not familiar with VLAN.
In my understanding, the WAN from modem should be
VLAN 1. Assume the Modem A to Switch Port isPort 1and the Modem B to Switch Port isPort 2. If I setPort 1's Default VLAN ID asVLAN 50andPort 2's Default VLAN ID asVLAN 51, how do I get theVLAN 1data?Or the VLAN is only work in switch? Do it mean that I could set the
Port 1andPort 2to receiveonly untaggedpacket as theuntaggedtraffic do not contain VLAN information? -
@testcb00 said in Virtualize pfSense, two WAN, one switch, possible?:
I am not familiar with VLAN
Here's your chance to get familiar!

Traffic from the modems is almost certainly untagged. Which is very much not the same thing as VLAN1 but is a surprising common misconception.
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan1Port based VLANs is probably not what you want here. That is typically used for separating switch ports into groups but not for trunking tagged traffic which is what you need to do here.
You need to use 802.1Q based VLANs to tag the traffic and trunk it to pfSense.So, yes, set the PVID / Default VLAN ID (whatever it's named on that switch) on the WAN ports to 50 and 51. Then set the port connected to pfSense to trunk those VLANs. The traffic from each will arrive tagged to the pfSense NIC.
In pfSense setup VLAN interfaces for 50 and 51 on the parent Mellanox NIC. Assign those interfaces as WAN1 and WAN2. Done!You can the same with other VLANs. You only actually need one NIC there, all the interfaces could be VLANs on it.
Steve