Connecting Cisco 3560 to Netgate 2100
-
So on my cisco switch:
switch#s arp
internet xxx.xxx.20.1 90.ec.770d.8e0b.8e0bFrom pFsense
Diagnostics/ ARP Table:Vlan20 xxx.xxx.20.1 90.ec.770d.8e0b.8e0b
I also gave the vlan on the switch an IP of .5 which is showing in the ARP table of both the switch and pFsense box with the poper MAC.
Losing my mind here can figure out why they are not communicating
xxx.xxx.20.5
-
And you can not ping the pfsense IP from the switch? Then that screams firewall rule dude!
-
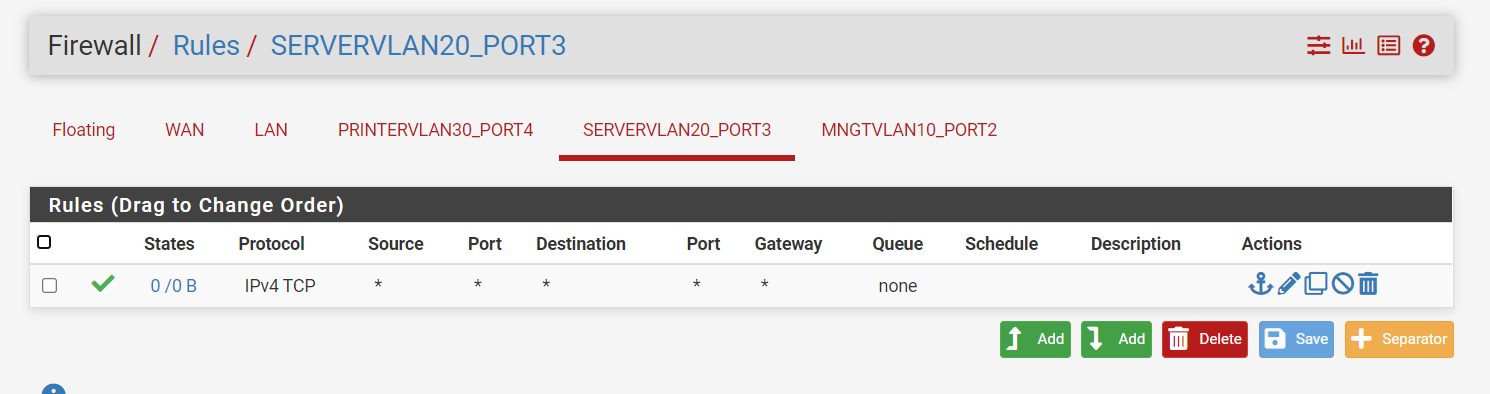
So that rule wont allow traffic to PING the interface? Can you confirm so I'm not losing it.
-
No - its TCP only! That doesn't allow ICMP.
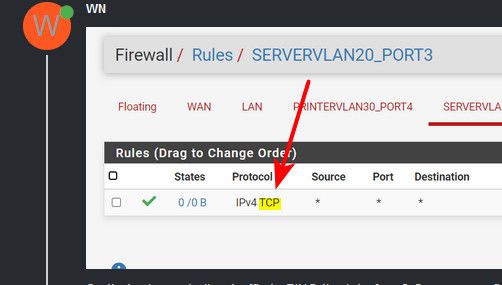
Or UDP for dns either. If you want a ANY rule - icmp, tcp, udp, etc.. Then you have to set that in the rule and would show little *
-
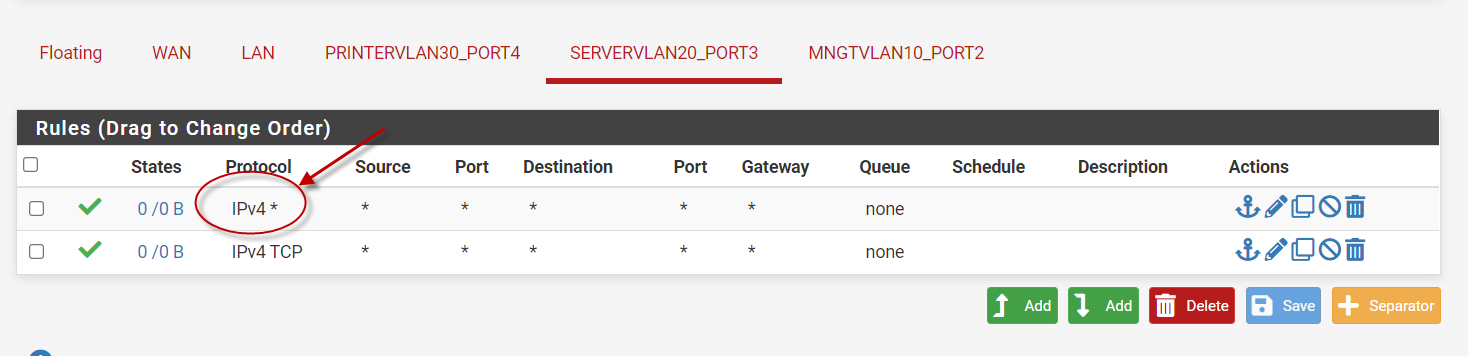
The top one should be correct then? I just want to get connectivity going and then I'll start peeling it back. Also, most of my experience is with ASA's. Do I need a bi-directional rule within the same interface?
-
Yeah that rule would be true any any rule.
edit: no you wouldn't need bidirectional rule, any return traffic would be allowed by the state created when inbound traffic to the interface is allowed.
-
Yeah... Still didn't work.
-
Well sniff on pfsense - pfsense can not answer ping if it never sees it.
Its not rocket science here - the traffic is tagged or its not, etc Post up your switch port config on pfsense and your switch..
If your seeing the mac - that says your L2 is connected.. If your rule allows for answer then it would work.
edit: You don't have any floating rules do you?
-
No floating just the any/any on each interface. Below are the uplinks for each vlan 10,20 and 30. I removed the vlan interfaes off the switch and te defalt gateway. there should be no more layer 3 on the switch
interface GigabitEthernet0/16
description Uplink to pFsense Vlan 10
switchport access vlan 10
switchport mode access
spanning-tree portfastinterface GigabitEthernet0/32
description Uplink to pFsense Vlan 20
switchport access vlan 20
switchport mode access
spanning-tree portfastinterface GigabitEthernet0/48
description Uplink to pFsense Vlan 30
switchport access vlan 30
switchport mode access
spanning-tree portfast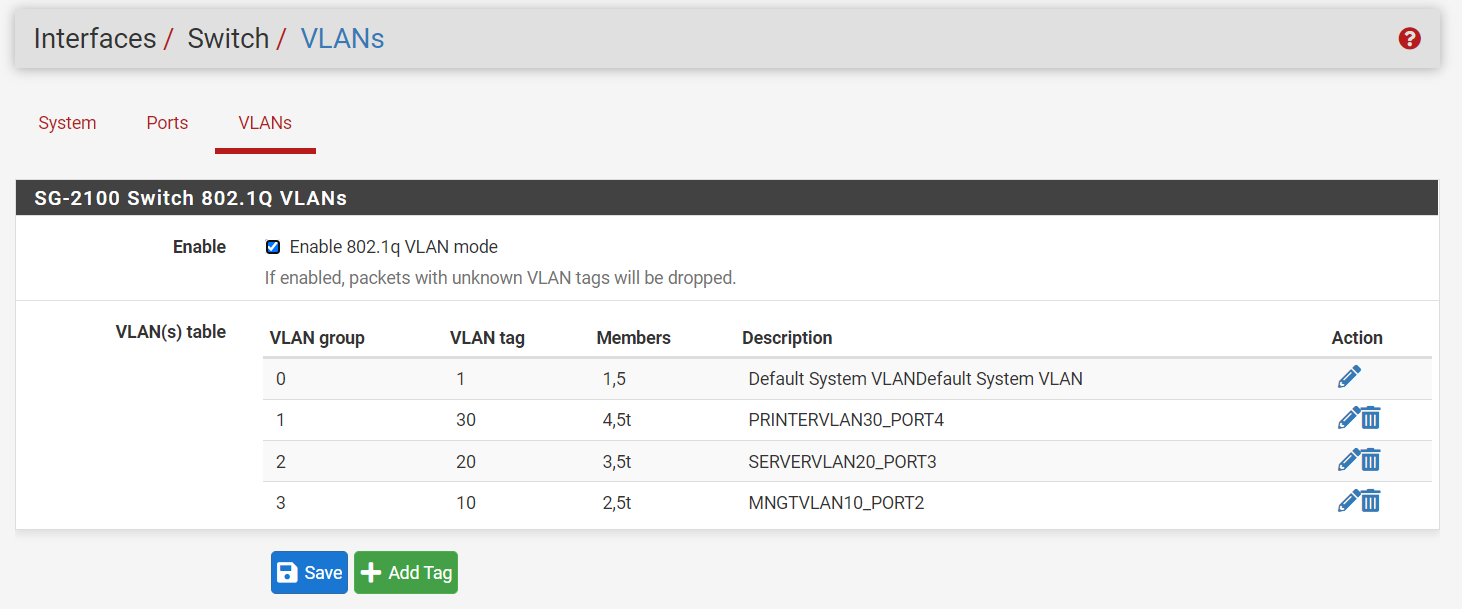 Arp on
Arp on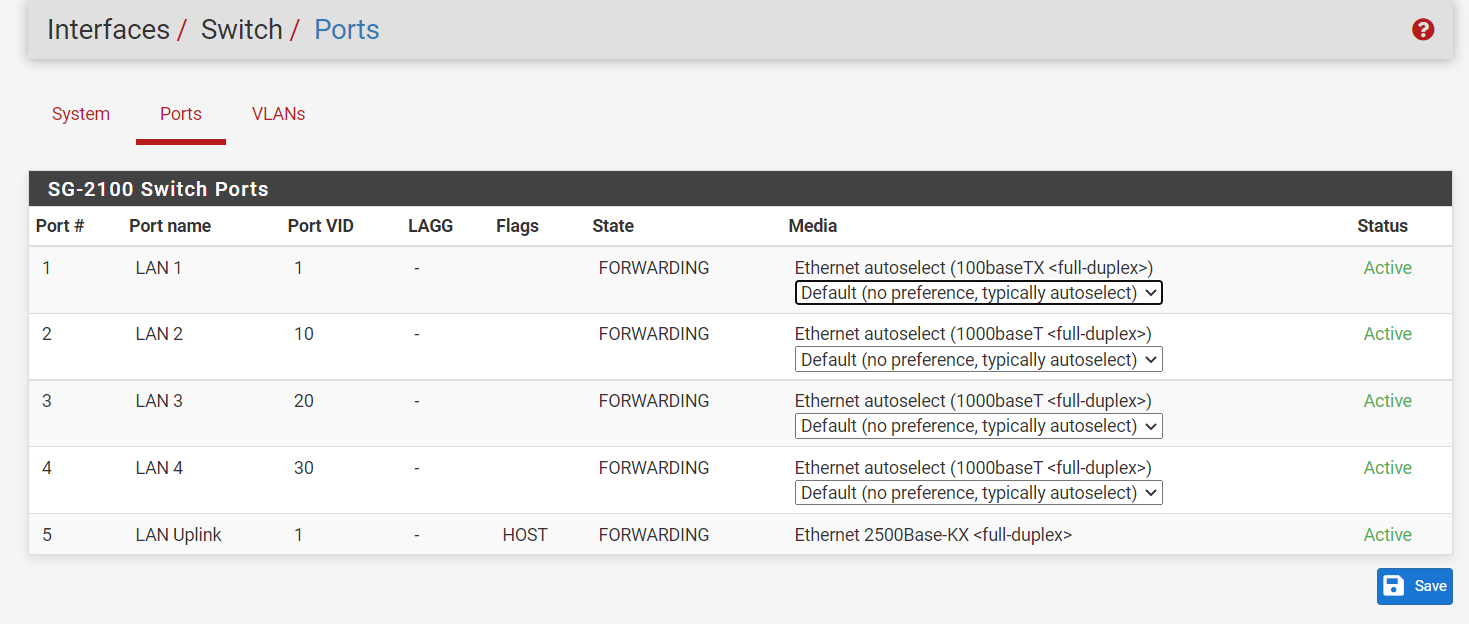
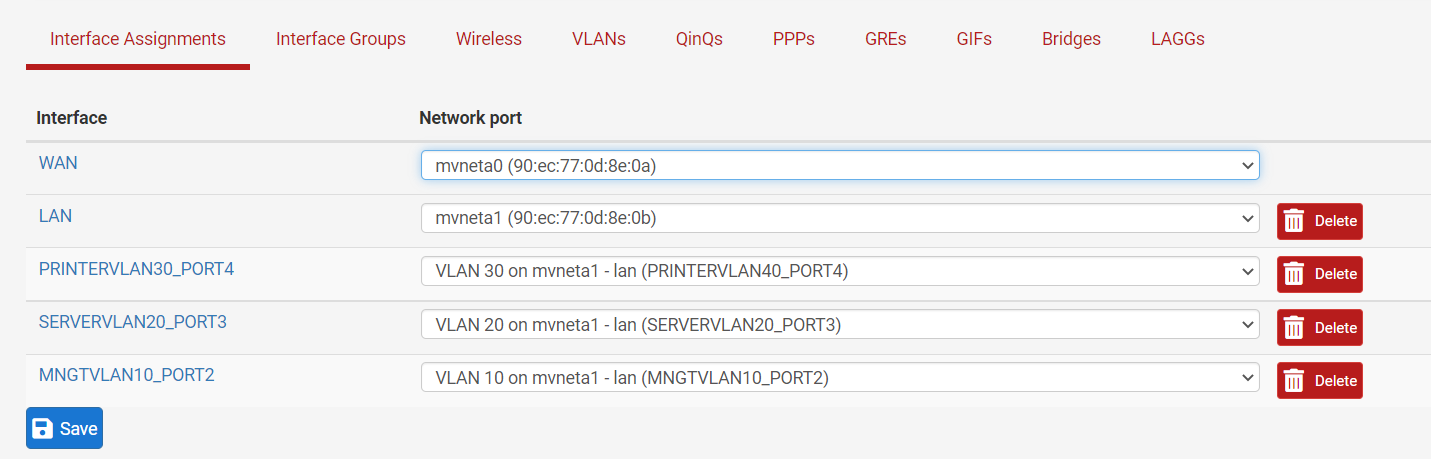
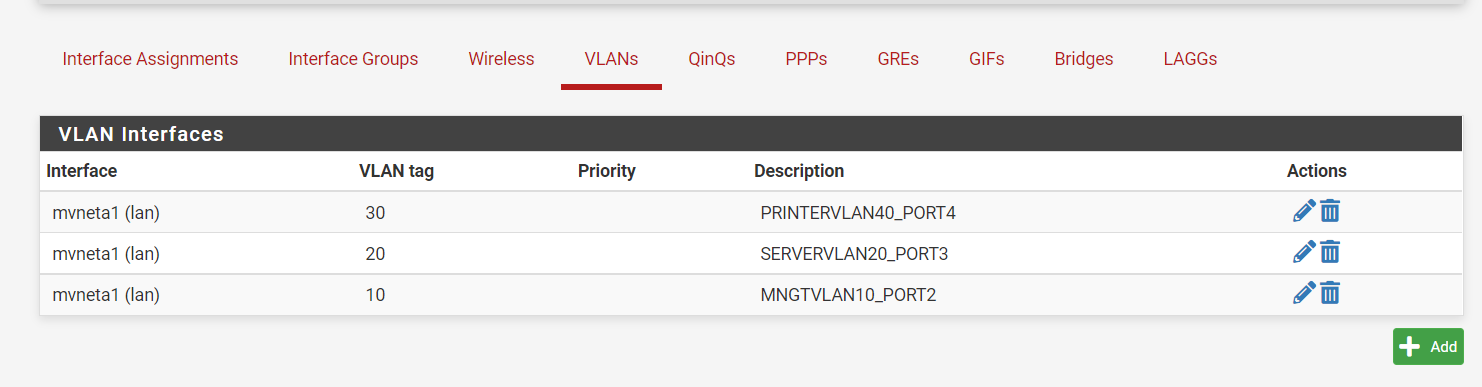
-
@wn Nothing jumping out at me that is wrong there.. Have very sim setup on a 3100 with switch ports being untagged vlans.
If your firewall rules are any any.. and you showing the mac in your device your trying to ping from.. Then you should get an answer..
Really the only thing left to validate is traffic is being seen by pfsense - as stated if pfsense never sees the ping, it for sure can not answer. Seeing the traffic would have zero to do with rules being wrong or not, etc.
edit: Just for reference and example.. Here is my very sim sort of setup
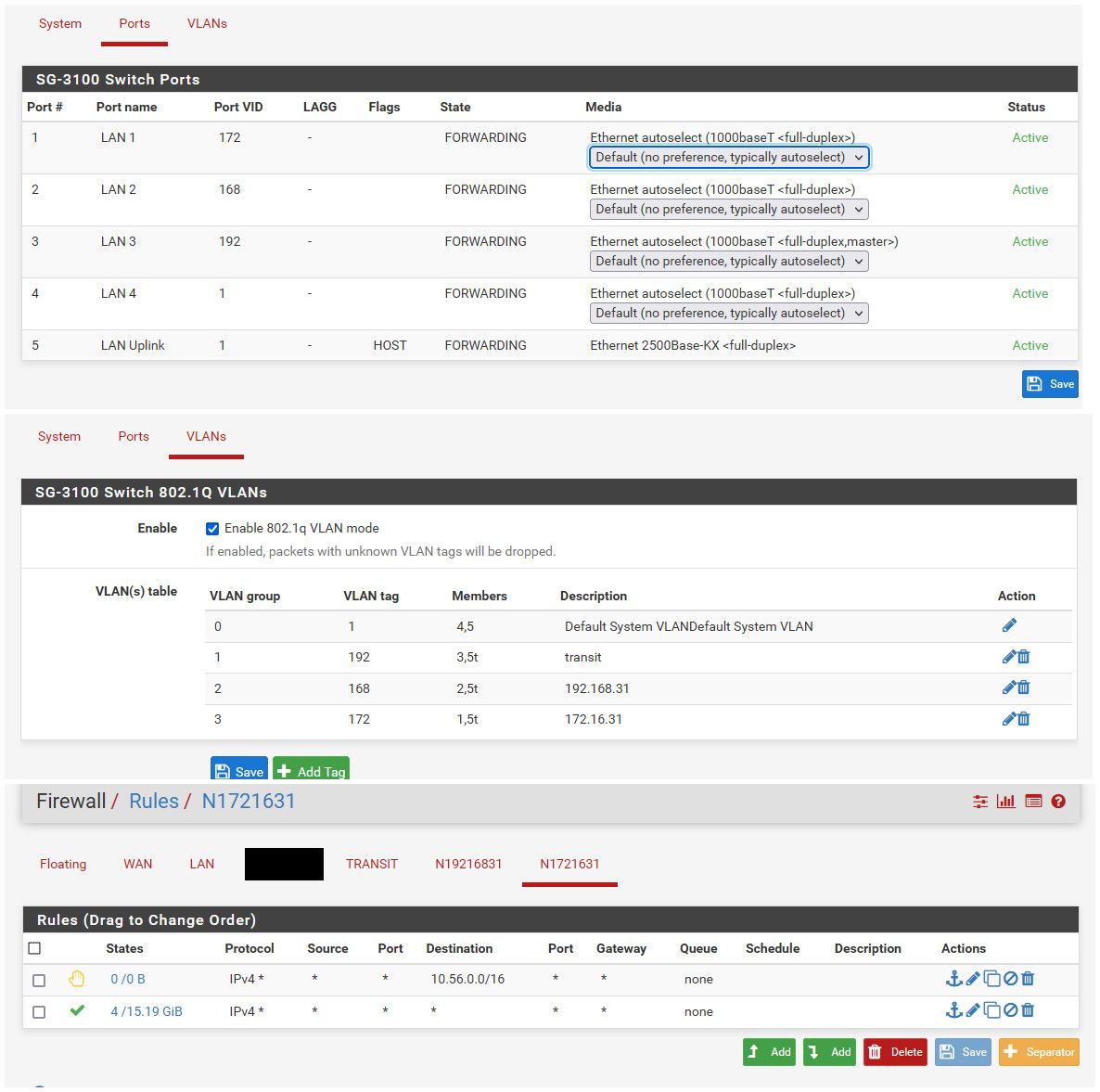
-
I I believe me removing all layer 3 interfaces from the cisco switch might have done the trick. I can ping the interfaces from the server IP's.
Thank you again for letting me bounce things off of you. Extremely important to have other eye look at your work. Thanks again!