Get public ip for pcs
-
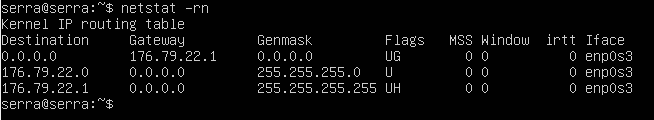
sure looks like the 22.1 address I said.. do -rn the n disables name resolution. So just see the IP.
You would keep it running until someone pings you.. I just did so you should see ping requests. I can pm you the address would of come from
-
-
@s_serra yup like I said 22.1 would be that devices gateway, which is last hop I see in my traceroute.. So I am getting there.. Now your sniff should of shown you my ping attempt.
-
15:44:28.869724 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 88
15:44:28.869734 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 89
15:44:28.869857 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 94
15:44:28.869942 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 74
15:44:28.870335 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 88
15:44:28.870392 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.870397 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 89
15:44:28.870416 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.870494 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 94
15:44:28.870512 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.870567 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 74
15:44:28.870585 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.871055 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.871072 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.871179 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.871193 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 0
15:44:28.872534 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872549 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872559 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872567 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872576 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872584 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.872593 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.873508 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.873629 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.873754 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.873851 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.873877 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874004 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874044 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.874138 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874243 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.874253 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874531 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.874557 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874568 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874578 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874587 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874805 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.874828 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874838 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874847 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874857 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 318
15:44:28.874910 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874941 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.874966 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874977 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874986 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.874995 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1254
15:44:28.875624 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.875741 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.875771 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.875963 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876047 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876137 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.876254 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876339 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.876373 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876502 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876514 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 318
15:44:28.876741 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.876747 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876876 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.876938 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877005 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.877018 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1460
15:44:28.877127 IP 176.79.20.129.443 > 176.79.25.49.64027: tcp 1254
15:44:28.877136 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877139 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877158 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877176 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877337 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877412 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877663 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.877908 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.878028 IP 176.79.25.49.64027 > 176.79.20.129.443: tcp 0
15:44:28.962323 IP 79.124.62.98.8080 > 176.79.25.49.40092: tcp 0
15:44:29.194744 IP 176.79.20.129 > 176.79.20.1: ICMP echo request, id 19262, seq 17511, length 9
15:44:29.195923 IP 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 19262, seq 17511, length 9
15:44:29.593095 IP 176.79.25.49.52398 > 213.163.94.74.50002: UDP, length 60
15:44:29.724047 IP 162.159.136.234.443 > 176.79.25.49.57233: tcp 357
15:44:29.724081 IP 176.79.20.129 > 176.79.20.1: ICMP echo request, id 19262, seq 17512, length 9
15:44:29.765398 IP 176.79.25.49.57233 > 162.159.136.234.443: tcp 0
15:44:29.796537 IP 213.163.94.74.50002 > 176.79.25.49.52398: UDP, length 52
15:44:29.824189 IP 155.133.246.51.27028 > 176.79.25.49.51776: tcp 189
15:44:29.864554 IP 176.79.25.49.51776 > 155.133.246.51.27028: tcp 0
15:44:30.133648 IP 176.79.25.49.63231 > 185.12.116.108.2083: tcp 1
15:44:30.145388 IP 185.12.116.108.2083 > 176.79.25.49.63231: tcp 0
15:44:30.256330 IP 176.79.20.129 > 176.79.20.1: ICMP echo request, id 19262, seq 17513, length 9
15:44:30.257203 IP 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 19262, seq 17513, length 9
15:44:30.284863 IP 162.159.136.234.443 > 176.79.25.49.57233: tcp 56
15:44:30.325569 IP 176.79.25.49.57233 > 162.159.136.234.443: tcp 0
15:44:30.602764 IP 79.124.62.98.8080 > 176.79.20.129.52007: tcp 0
15:44:30.788574 IP 176.79.20.129 > 176.79.20.1: ICMP echo request, id 19262, seq 17514, length 9
15:44:30.789372 IP 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 19262, seq 17514, length 9
15:44:30.796609 IP 213.163.94.74.50002 > 176.79.25.49.52398: UDP, length 52
15:44:31.298497 IP 176.79.20.129 > 176.79.20.1: ICMP echo request, id 19262, seq 17515, length 9
15:44:31.299483 IP 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 19262, seq 17515, length 9
15:44:31.390581 IP 176.79.25.49.63203 > 185.12.116.108.2083: tcp 1
15:44:31.401939 IP 185.12.116.108.2083 > 176.79.25.49.63203: tcp 0 -
@s_serra you filled up the 100 packet count before I pinged you... In the capture set it to the IP I sent you in PM.. And I will ping you again... I have a continuous ping running now
-
I sent it in pm which returned the packet capture
-
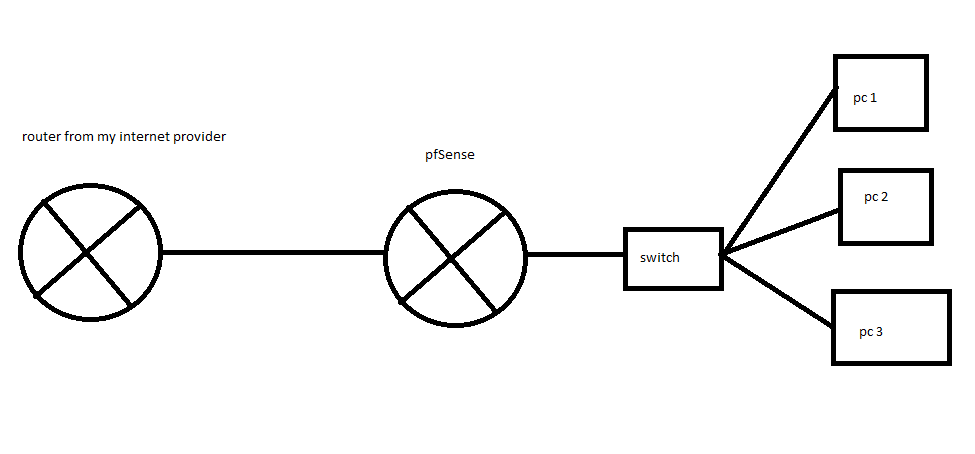
@s_serra Ok - well so getting to pfsense.
Now do the same thing on the lan side interface.. If we don't see it there, then something wrong with the bridge..
My ping is still running. If you do see it there - then something on the client blocking it.
-
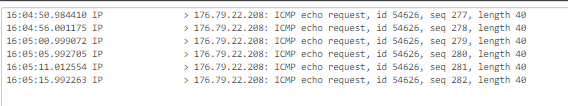
15:56:55.997368 IP x.x.x.x > 176.79.22.208: ICMP echo request, id 54626, seq 182, length 40
15:57:00.994130 IP x.x.x.x > 176.79.22.208: ICMP echo request, id 54626, seq 183, length 40on the lan side it also worked, I tested it on the bridge interface and it also receives a response
-
So you see replies from the server on LAN and Bridge but not WAN?
Did you check the MAC addresses in the pcap yet? You need to confirm those are correct.
-
@s_serra You say you see a response? Or you see my ping going to your 22.208 address?
-
I saw ping icmp on all interfaces
-
@s_serra the reply, not just the request?
-
-
how I use pcap is it in pfsense or is it another tool?
-
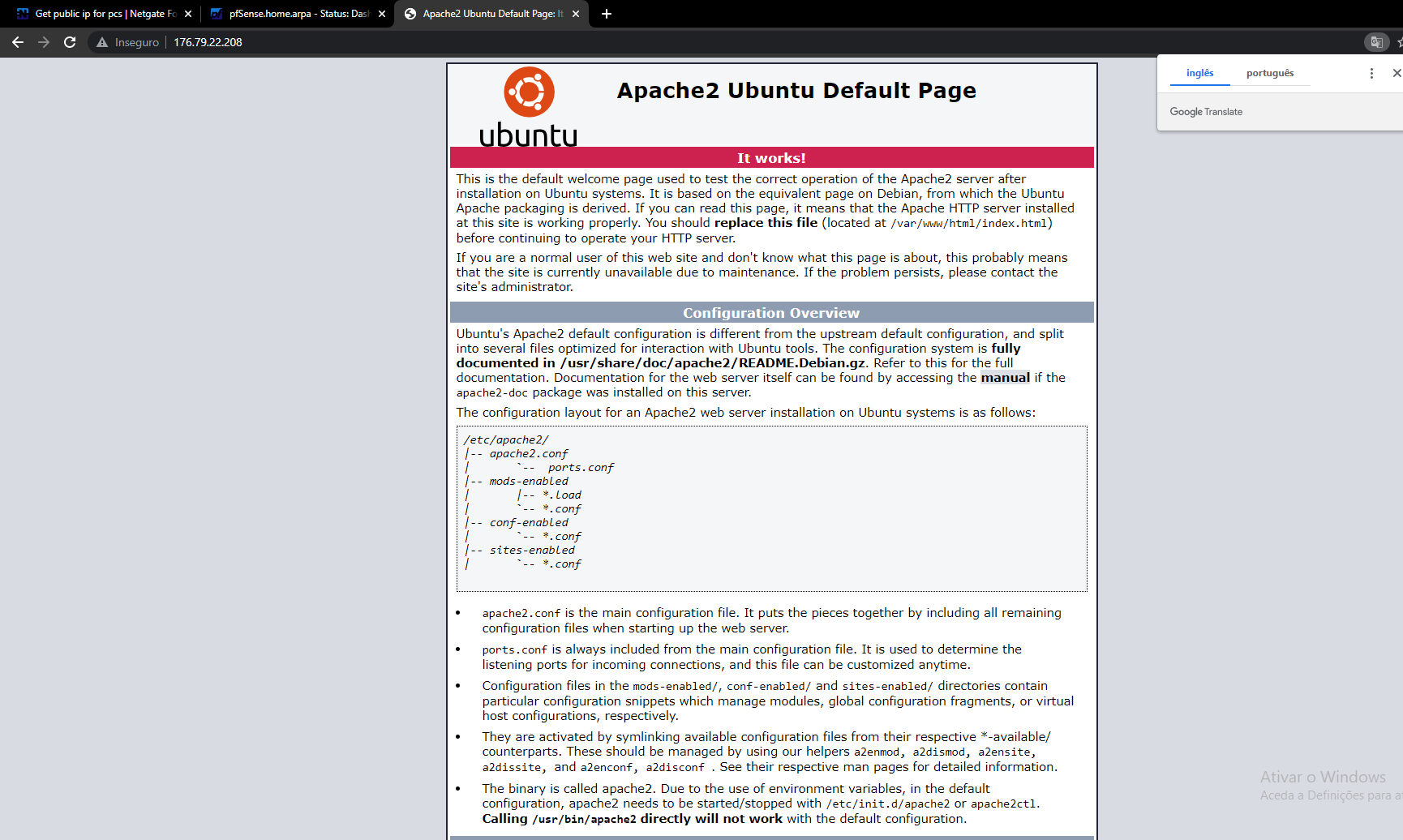
@s_serra so that is pfsense sending on my request to your 22.208 box - which is not answering..
Which would assume means its running a firewallIf you validate that the mac address pfsense sent to was the correct mac address of your 22.208 box. You can view that by downloading the packet capture and viewing with say wireshark. Or up the verbosity of the packet capture where it shows mac address.
But what I would bet a very large sum of money on is your 22.208 box is running its own firewall and just not answering the traffic.
-
@s_serra said in Get public ip for pcs:
I just get it
So to confirm you are only seeing requests and no replies when you pcap on BOTH WAN and LAN?
-
-
@s_serra your machine where? There is a HUGE difference in talking to some box on the same network as you - and some strange public IP..
-
@s_serra dude - I have to assume 22.207 is on your network as well since you said your mask is /24 - or is this assigned to someone else??
Because 22.207 answers
$ ping 176.79.22.207 Pinging 176.79.22.207 with 32 bytes of data: Reply from 176.79.22.207: bytes=32 time=120ms TTL=45 Reply from 176.79.22.207: bytes=32 time=119ms TTL=45Which is another SCREAMING indication of firewall on the 22.208 box
22.206 also answers, and 22.210-212 all answer..
-
@johnpoz
These IPS are other people's. MY ISP provides IPS via DHCP as available. The machine on which it works is also connected to a bridge with another public IP of a different range.