pfSense HA LAN Interfaces Only
-
@viragomann Correct; i am using 8.8.8.8 and 8.8.4.4 as DNS Res via system > gateway.
I have now changed my GW monitoring IP to 1.1.1.1 on the secondary pf. Also on the secondary pf i have placed a CHECK under System > Advanced > Miscellaneous > State Killing on Gateway Failure.
When i try to ping 8.8.8.8 from the secondary; i get this timeout
PING 8.8.8.8 (8.8.8.8): 56 data bytes 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 263f 0 0000 01 01 0000 127.0.0.1 8.8.8.8 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 b74f 0 0000 01 01 0000 127.0.0.1 8.8.8.8 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 66ba 0 0000 01 01 0000 127.0.0.1 8.8.8.8 --- 8.8.8.8 ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet lossI have marked my PPPOE WAN as down on the 2nd pf as well.
This is so bizarre..
I also have just an open rule for LAN
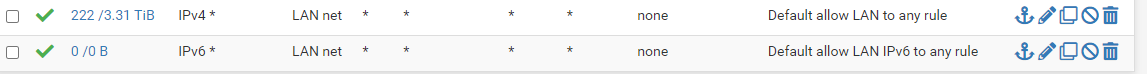
-
@iptvcld said in pfSense HA LAN Interfaces Only:
When i try to ping 8.8.8.8 from the secondary; i get this timeout
You cannot use 8.8.8.8 for troubleshooting, since you direct it to WAN gateway.
However, for getting the DNS resolution work on the secondary when the WAN cable is connected to the primary, you should set the gateway to "none" for all DNS servers in System > General Setup.I have now changed my GW monitoring IP to 1.1.1.1 on the secondary pf.
So try to ping 1.1.1.1 while taking a capture on the LAN interface.
-
@viragomann My master pf DNS settings like like this
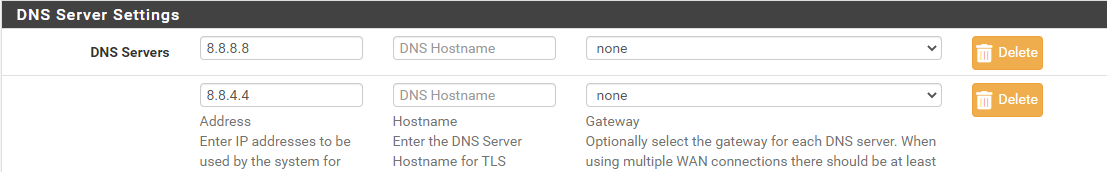
and secondary pf is the same
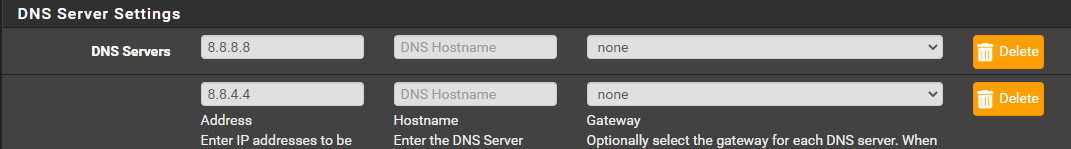
When i ping 1.1.1.1 in seconday the packet capture just gave this
12:57:15.477198 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 18433, seq 797, length 9 -
@iptvcld said in pfSense HA LAN Interfaces Only:
When i ping 1.1.1.1 in seconday the packet capture just gave this
12:57:15.477198 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 18433, seq 797, length 9You should see the same on the masters LAN. Check that out, please.
-
@viragomann thats correct; i just ran a packet cap on master LAN and then sent a 1.1.1.1 ping from the secondary pf
13:05:44.735976 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 18433, seq 1785, length 9 -
@iptvcld
Well, so 1.1.1.1 is routed to the masters LAN address.
Now, if you take a capture on the masters WAN you should also see the ICMP packets to 1.1.1.1, but coming from the WAN IP.If that's not the case, either the firewall rule or the outbound NAT on the master might failing anyhow.
-
@viragomann Ran a packet cap on master and i see this request 3 times
13:10:40.370864 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 18433, seq 2360, length 9seems to be coming from the secondary pf LAN IP still and not the WAN IP
Outbound NAT on master is this:
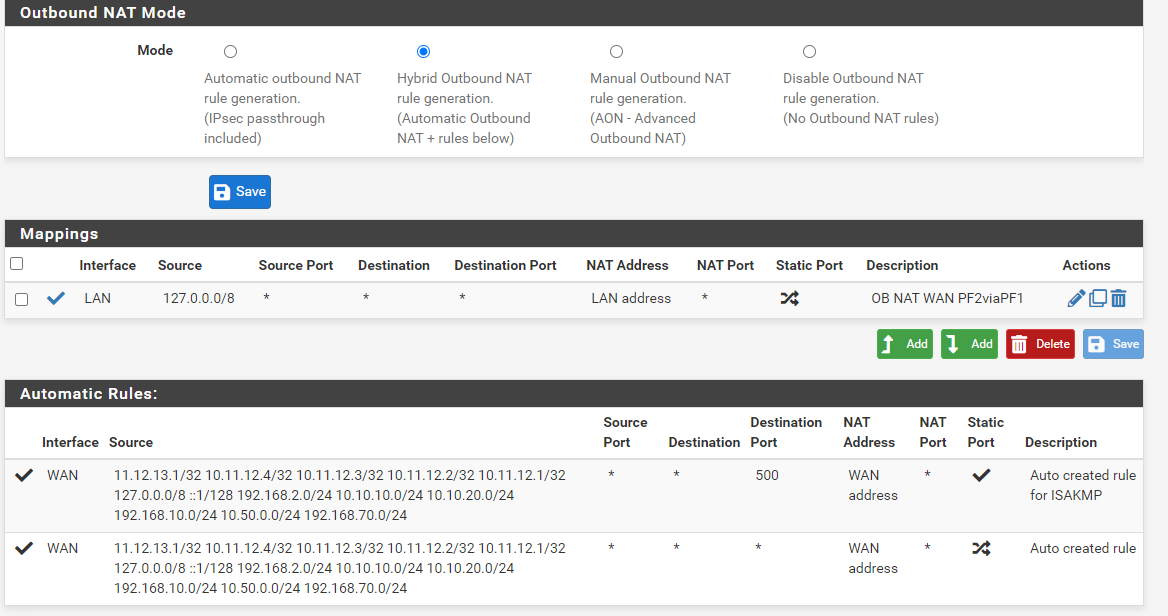
And LAN Rules

-
@viragomann Ran it again and i see this
13:17:05.527815 IP 76.64.x.x > 1.1.1.1: ICMP echo request, id 55322, seq 0, length 64 13:17:05.542715 IP 1.1.1.1 > 76.64.x.x: ICMP echo reply, id 55322, seq 0, length 64then
13:17:05.562166 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 34782, seq 78, length 9PING 1.1.1.1 (1.1.1.1): 56 data bytes
64 bytes from 1.1.1.1: icmp_seq=0 ttl=55 time=15.187 ms--- 1.1.1.1 ping statistics ---
3 packets transmitted, 1 packets received, 66.7% packet loss
round-trip min/avg/max/stddev = 15.187/15.187/15.187/0.000 ms -
@viragomann Does this need to be unchecked under my WAN interface?
Block private networks and loopback addresses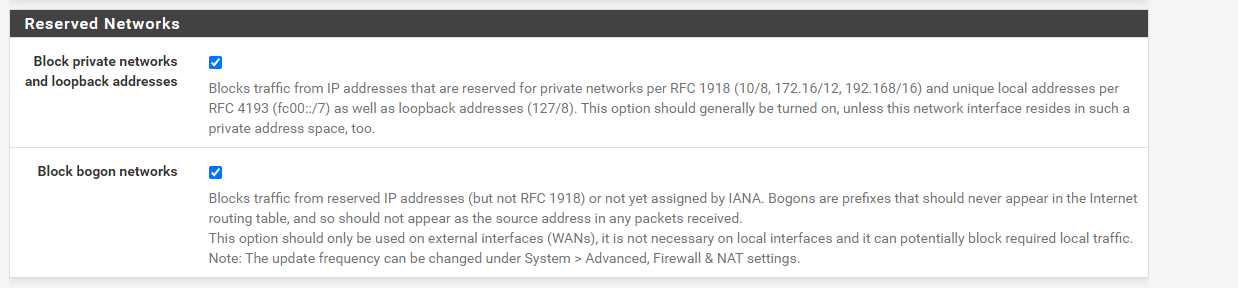
-
@iptvcld said in pfSense HA LAN Interfaces Only:
Ran it again and i see this
13:17:05.527815 IP 76.64.x.x > 1.1.1.1: ICMP echo request, id 55322, seq 0, length 64
13:17:05.542715 IP 1.1.1.1 > 76.64.x.x: ICMP echo reply, id 55322, seq 0, length 64then
13:17:05.562166 IP 192.168.2.81 > 1.1.1.1: ICMP echo request, id 34782, seq 78, length 9PING 1.1.1.1 (1.1.1.1): 56 data bytes
Strange!
Check the masters state table and filter for 1.1.1.1 after pinging from backup.
-
@iptvcld said in pfSense HA LAN Interfaces Only:
@viragomann Does this need to be unchecked under my WAN interface?
Block private networks and loopback addresses
No, this is only for incoming packets. There is no need to allow private addresses on WAN.
-
This post is deleted! -
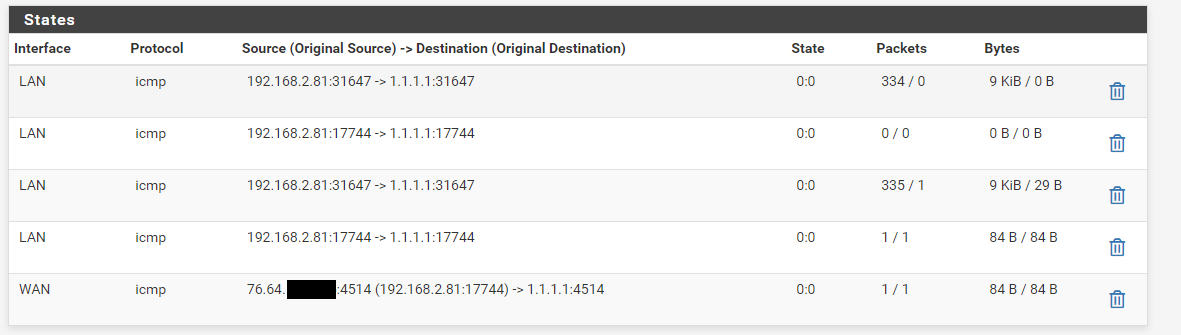
@viragomann This is the state table after pinging from 2nd
-
@viragomann When try to ping 1.0.0.1 from 2nd; i get all fails
PING 1.0.0.1 (1.0.0.1): 56 data bytes 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 ee77 0 0000 01 01 0000 127.0.0.1 1.0.0.1 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 4453 0 0000 01 01 0000 127.0.0.1 1.0.0.1 92 bytes from 127.0.0.1: Time to live exceeded Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 071e 0 0000 01 01 0000 127.0.0.1 1.0.0.1 --- 1.0.0.1 ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet lossAnd when i run this ping while doing packet cap on master LAN; i dont see the entries come over
-
@iptvcld said in pfSense HA LAN Interfaces Only:
This is the state table after pinging from 2nd
The last two lines look well for only one ping packet. One state entry for LAN and one for WAN.
But the other lines are showing faults at all. The packets column shows the packets for each direction (request, respond). So it shows many requests, but few responds.Not clear, what's going wrong here, now.
Maybe there are some hints in the system log? -
@iptvcld said in pfSense HA LAN Interfaces Only:
When try to ping 1.0.0.1 from 2nd; i get all fails
This IP might be routed out to WAN, since there is no special route for it. But WAN is not connected, hence it will fail.
-
@viragomann This makes sense..
Its just so odd that 1 get 1/3 ping request to pass when doing a ping from 2nd pf. It should almost be all or none..
-
@viragomann So just an over view of what I have done to try to get this going
-
Master Node: Disabled Static Route configuration under HA Sync setting
-
Master Node: Outbound NAT changed to Hybrid and added a mapping for source 127.0.0.0/8 to ANY and NAT Address is LAN address (this synced over to Secondary node)
-
Secondary Node: System-Advanced-Miscellaneous; enabled State Killing on Gateway Failure
-
Secondary Node: System-Routing; Created a new GW using LAN interface with the IP of LAN interface from Master node as the Gateway and 1.1.1.1 for the monitoring IP.
-
Secondary Node: Created a GW Group as PPPOE WAN Tier1, Above noted GW as Tier 2 and VPN GW as Tier 3
-
Secondary Node: The new GW group was set to default under IPv4
-
-
@iptvcld said in pfSense HA LAN Interfaces Only:
Secondary Node: Created a GW Group as PPPOE WAN Tier1, Above noted GW as Tier 2 and VPN GW as Tier 3
The VPN GW has to be set to "never", so that it is no member of this gateway group.
All other settings should be correct.
When you run a ping with 3 requests to 1.1.1.1 on the secondary the packets should go out to the masters LAN and be forwarded to the internet, since the gw monitoring has set the static route for this IP.
When you sniff the traffic filter for ICMP and 1.1.1.1, you should see 3 ICMP request packets (and 3 responds if it works) on
- both masters and secondarys LAN: 192.168.2.81 > 1.1.1.1
- on the masters WAN: WAN IP > 1.1.1.1
If you look into the masters state table you should see
- one entry for LAN: 192.168.2.81 > 1.1.1.1
- and one for WAN: WAN IP > 1.1.1.1
Both should show 3/3 in the packets column.
Not clear, why it doesn't behave this way on your setup.
-
@viragomann I removed all the settings we added, rebooted 2nd node and re-added all the settings as per above and still no go.. I am not able to see the ping req from master packet cap now even when sending a ping from 2nd node. But on the master wan, i can see the 1/1 request which shows that in the ping log on the 2nd node as well 1/3 goes