Adding a Subnet to an Interface
-
@johnpoz Well these are the OPT1 rules ...and I would have expected them to be similar, only with no need for WAN rule additions (although I have tried adding LAN rules to the WAN interface in addition to LAN) and it made no difference (even after resetting the States):
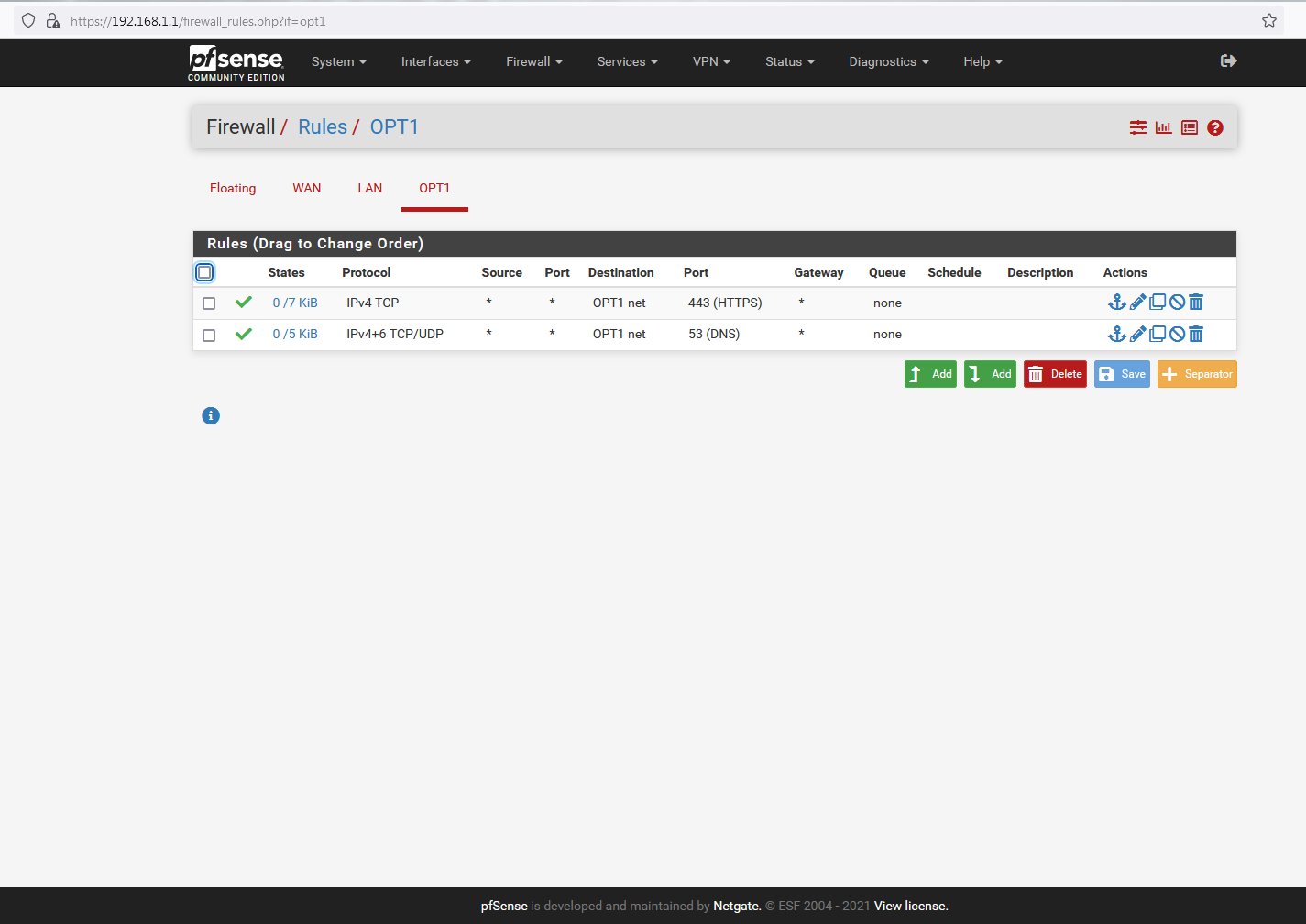
...and these are the LAN rules based on the above (following the addition of a DNS rule, as per your advice):
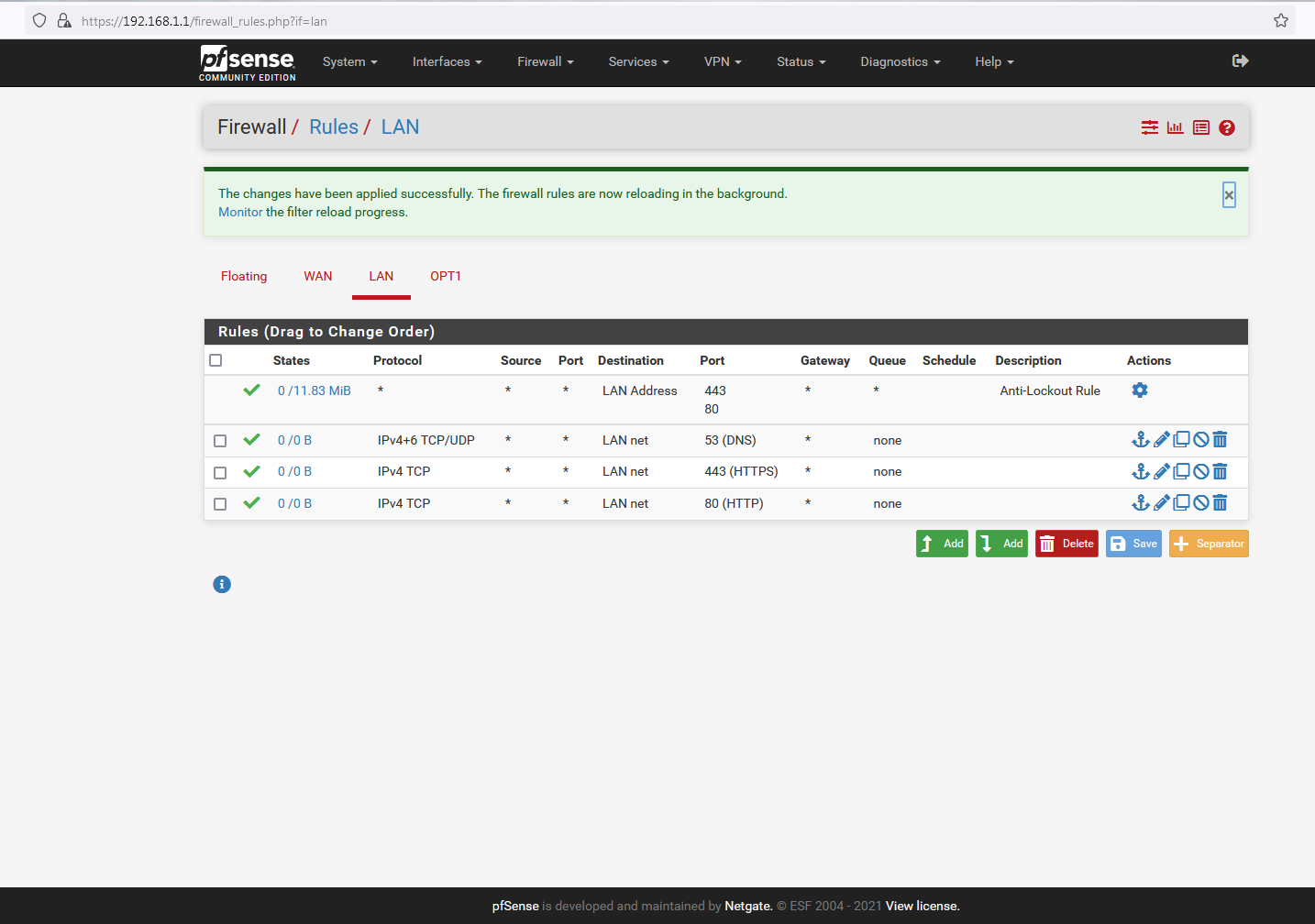
Unfortunately, the only thing that actually works (regardless of whether States reset or not) is the following:
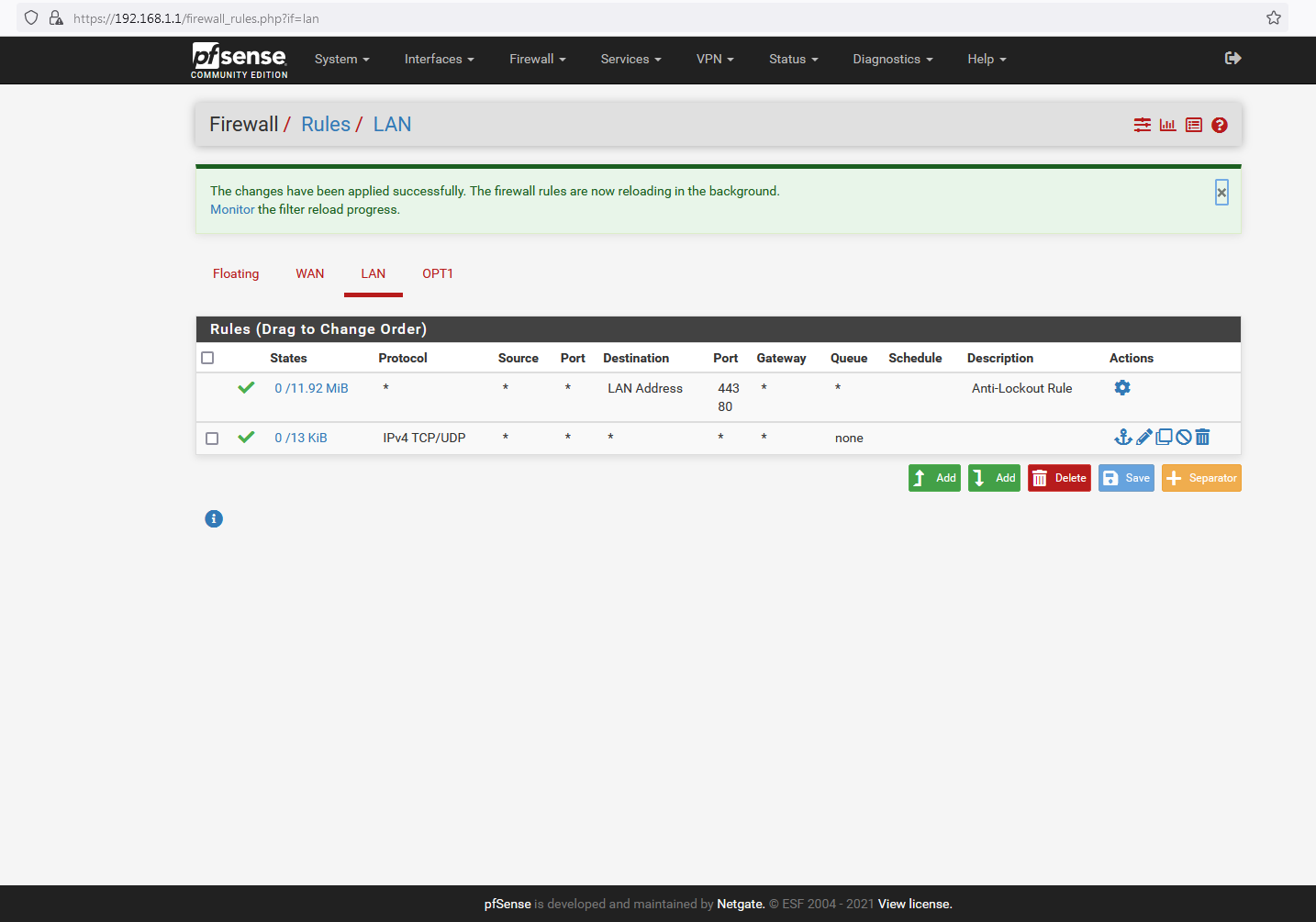
Yes, I know: not at all what I want to be doing...
Thanks, too, for the following:
"@nogosubnet BTW - as I mentioned I wouldn't use /29 in your wan rules.. Since this allows access to the web gui on pfsense opt1 interface from the internet..
I am able to hit your webgui via public internet on the .25 address. Your wan rules should be set to only allow access to the ports and IPs you want to allow access too. I doubt you want people to be able to hit the pfsense web gui from the internet."
I will remove those rules shortly and see what happens (preferably after I have managed to get some more of the rules actually working, that is.
-
Everything is now absolutely perfect, save for a stuttery SSh connection (for some reason the connection is inconsistent and it frequently takes several attempts to connect) which often freezes. This has probably got a lot to do with the hardware configuration, though, and the additional processing overheads as a result of the pfSense arrangement; but I remain hopeful that the returns from such an arrangement will outweigh that in time.
...so, again, thanks to everyone who has helped me get this working, - your input was really appreciated, as was your determination to tame my pfSense.
-
@nogosubnet Well the rules you posted woudn't work because you have lan set to lan net for destination. How would that allow access to the internet..
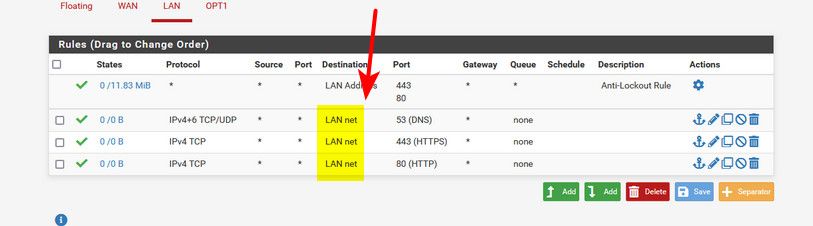
Those rules say anything (already on the lan net - so really only source could be lan net) But your saying you can go to the lan net - which they are already on.. How would that work trying to go to say 8.8.8.8 or 1.1.1.1 - ie the internet.
Source should be lan net, and destination should be ANY..
additional processing overheads
No that has zero to do with anything.. Since you have not actually given any details on how you actually have the lan side infrastructure setup - if I had to guess I would guess asymmetrical traffic flow.. You have 2 networks - how do you have them isolated? You have 2 physical switches, you have a vlan capable switch?
And the opt1 rules you posted same problem - you list your dest as opt1 net.. Again how would that would work as destination, from the opt net..
edit: BTW you say its working - but I can not query your dns from internet again, nor does the apache site come up even.
-
After one hell of a fight I finally got the rules working:
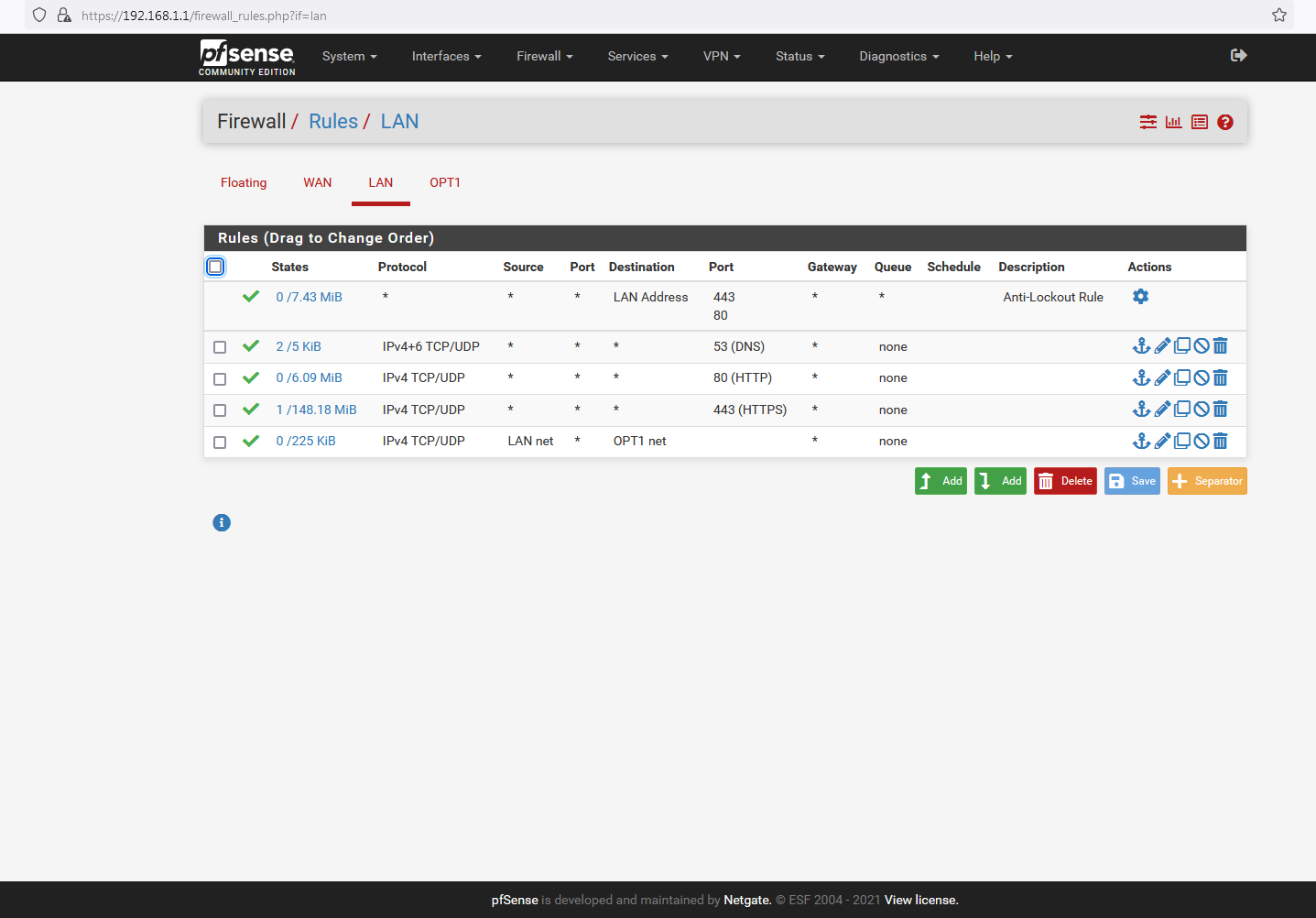
My website was down last night, - no idea what happened, - network connectivity literally just died and stopped responding, and could only be restored by restarting the machine. This is not the first time that has happened, and I have no idea what causes it or why it happens, but I do know that it sometimes coincides with heavy and sustained network attacks (although I would have thought that the networking would resume afterwards, bearing in mind that the underlying services are, in all cases, still working and showing no errors).
I am also seeing a lot of flakiness with pfSense: very slow, unstable, connections, erratic SSh connectivity, and seriously poor connectivity (especially with the webserver), but I am hoping that improvements in the cabling and hardware might mitigate some of these problems.
There is also an issue with rule ordering, which I am stuggling to find information on; specifically, do the block rules go at the top (as I suspect), and what sort of impact will they have on rules that proceed them? - One of my rules is an inverse (!LAN) rule on the OPT1 tab to prevent access to a port from everything save the LAN subnet, but should that rule be at the top, and will the blocked port apply to every rule (including pass rules) underneath it?
...and, yes, there is a missing port number from the above: this detail was deliberately removed prior to posting.
-
@nogosubnet your site is down now.. I can query your dns, but not access apache.
Rules are evaluated as traffic enters the interface, top down, first rule to trigger wins, no other rules are evaluated..
Pretty much like very other single firewall on the planet..
-
@johnpoz ...so "first rule to trigger wins, no other rules are evaluated" as in the first rule concerning a given protocol, port, etc., meaning that any other similar situation (same protocol, port, etc. in a later rule) would be disregarded? - Fair enough, - thanks.
The website was back up a few minutes ago, - I have no idea why the availability of that site is being such a basket because, outside of the pfSense arrangement, there are seldom any issues ...so it could be board issue, ethernet cable issue, or possibly the network card (I do not feel that it is a configuration issue because the configuration is the absolutely minimal required to make it work and to lock it down). I have made some changes and will be replacing the ethernet cables to fully shielded 5e cables to eliminate them as a problem, and will just have to take things from there.
-
@nogosubnet If the rule matches be it block, be it allow - no other rules would be looked at.
So for example if you had a rule that blocked anything to port 456, and the other setting on the rule allowed for a match of your traffic to 456, like source and dest ip... Then no a rule below that said hey any any would not be evaluated.
Its pretty simple start from the top walk down your rules - what rule matches.. There you go - no need to look at any other rules.
edit: site still down... I don't know how your testing - but its not available from teh public internet. Dns working - but nothing answers, no apache.. nothing when go to IP or fqdn.. even those the fqdn resolve.
-
@johnpoz Fair enough, - thanks.
The problem with the webserver connections being forcibly killed is definitely a pfSense issue: I do not know what is happening, and have no way of tracing it, but there is definitely something on the pfSense side of things that is blocking (and actively killing) connectivity with the webserver.
I have also tried to implement the DNS ANY fix and can confirm that it does not work in BIND, as BIND does not recognize the records as being valid syntax and, quite honestly, even the hacker groups do not recognize the 'fix' so, yes, it may look good but, outside of that, it would unfortunately appear to be nothing but another cute piece of theory.
As an example of what is happening on the connectivity side of things, pfSense will often show OPT1 as being down when it is not and SSh connections will immediately freeze and die upon opening ...or everything will be running fine on the webserver but it will be impossible to view the website or to connect via SSh (connection to one of the web addresses), - indicating a possible issue with the HTTP or HTTPS rules even though both are fine.
-
@nogosubnet said in Adding a Subnet to an Interface:
The problem with the webserver connections being forcibly killed is definitely a pfSense issue
Says who? Do you have logs of this? Who says anything is being killed? Maybe your internet connection just blows? Why don't you open up your wan IP so can ping that at least. And can validate if can even get to pfsense. Pfsense can not allow traffic it never sees, etc.
Your dns is not working currently either.
BIND does not recognize the records as being valid syntax
Zero idea what your talking about.. Support for this was added back in bind 9.11
https://www.isc.org/blogs/bind-release-911/Minimal Response to ANY Queries
Queries for ANY records are a possible abuse mechanism because they typically extract a response much larger than the query.
The new minimal-any option reduces the size of answers to UDP queries for type ANY by implementing one of the strategies in “draft-ietf-dnsop-refuse-any”: returning a single arbitrarily-selected RRset that matches the query name rather than returning all of the matching RRsets.
minimal-responses takes two arguments: no-auth suppresses populating the authority section but not the additional section; no-auth-recursive does the same but only when answering recursive queries.
pfSense will often show OPT1 as being down
Well if pfsense says the interface is down, then its down to pfsense for some reason - if that is the case then yeah your going to have issue.. Again you have not given any insight at all to how you have any of this connected together. So nobody can help you.
-
This post is deleted! -
This post is deleted! -
@johnpoz I have now fixed this issue by reinstalling the webserver distro. DHCP Server on the pfSense side of things allows me to access the webserver, but does not work with BIND (now installed via a package on the pfSense side of things), nor is it possible to get working alongside the DHCP Server. No matter, everything has its limitations and I will just have to use an alternative solution for a webserver.
Obviously I have also looked at the DNS Forwarder and DNS Resolver options, but, as far as I can tell from the documentation, neither is of any real use and certainly would not help with my setup.
For anyone attempting this, I have the following arrangement:
webserver with domain name
DHCP Server for the webserver enabled
domain records configured under Services > BIND DNS Service
DNS Server added under System > General
DNS Forwarder in place -
@nogosubnet said in Adding a Subnet to an Interface:
nor is it possible to get working alongside the DHCP Server
Have no idea what your talking about.. You can for sure run bind and dhcp at the same time. And the bind package works just fine.
Resolver (unbound) or the forwarder (dnsmasq) are not meant to be authoritative name servers - so no those will not work if your wanting to run the authoritative NS for your domain(s).
-
@johnpoz so, just BIND DNS Server and nothing else? - Tried it, - does not work.
-
@nogosubnet Huh? The bind package works just fine - takes all of couple of minutes to get it running.
You can not run bind and unbound or dnsmasq at the same time, they would be on the same port (53).. You could run both at the same time if they are not on the same interfaces.
But if your going to run bind you really have no use for unbound or dnsmasq.
-
@johnpoz Thanks, but then I hit the problem of DHCP Server and BIND DNS Server not being able to run concurrently.
To explain a bit more clearly, I had to use DHCP Server in order for my new distro installation to pick-up on an address (which was taken from the /29 subnet) but, obviously, that does not meet my webserver DNS requirements; hence the need for installing the BIND DNS Server package.
After dropping into the shell for rndc-confgen -a I had no problem adding the required records, including PTR, but now I cannot get BIND to play nice with DHCP Server: DNS lookups are failing, even with appropriate firewall rules in place; so something is not working. This is why I looked at the option of adding a server to System > General (Allow DNS server list to be overridden by DHCP/PPP on WAN box ticked) and using unbound or dnsmaq.
-
@nogosubnet this took me what all of 2 minutes to download and install the packaqe and configure it... Boom running bind with a zone with records..
[21.05.1-RELEASE][admin@sg4860.local.lan]/root: dig @192.168.200.1 example.com ns ; <<>> DiG 9.16.16 <<>> @192.168.200.1 example.com ns ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 17609 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 2 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 4a616f8062b04f920100000061544bc98fd0c0702ba2a376 (good) ;; QUESTION SECTION: ;example.com. IN NS ;; ANSWER SECTION: example.com. 43200 IN NS ns.example.com. ;; ADDITIONAL SECTION: ns.example.com. 43200 IN A 192.168.200.1 ;; Query time: 1 msec ;; SERVER: 192.168.200.1#53(192.168.200.1) ;; WHEN: Wed Sep 29 06:19:37 CDT 2021 ;; MSG SIZE rcvd: 101 [21.05.1-RELEASE][admin@sg4860.local.lan]/root: dig @192.168.200.1 example.com ; <<>> DiG 9.16.16 <<>> @192.168.200.1 example.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44640 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 7156bfc6f1f42d760100000061544be5a8331bf703c26ab2 (good) ;; QUESTION SECTION: ;example.com. IN A ;; ANSWER SECTION: example.com. 43200 IN A 192.168.200.1 ;; Query time: 0 msec ;; SERVER: 192.168.200.1#53(192.168.200.1) ;; WHEN: Wed Sep 29 06:20:05 CDT 2021 ;; MSG SIZE rcvd: 84 [21.05.1-RELEASE][admin@sg4860.local.lan]/root: dig @192.168.200.1 www.example.com ; <<>> DiG 9.16.16 <<>> @192.168.200.1 www.example.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21277 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: a4ed727e914027300100000061544becbda41dd2866b310c (good) ;; QUESTION SECTION: ;www.example.com. IN A ;; ANSWER SECTION: www.example.com. 43200 IN A 192.168.200.200 ;; Query time: 0 msec ;; SERVER: 192.168.200.1#53(192.168.200.1) ;; WHEN: Wed Sep 29 06:20:12 CDT 2021 ;; MSG SIZE rcvd: 88 [21.05.1-RELEASE][admin@sg4860.local.lan]/root: dig @192.168.200.1 www.example.com soa ; <<>> DiG 9.16.16 <<>> @192.168.200.1 www.example.com soa ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43097 ;; flags: qr aa rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: aac3a9f0cfce85720100000061544bef45e90e4342d1cfd8 (good) ;; QUESTION SECTION: ;www.example.com. IN SOA ;; AUTHORITY SECTION: example.com. 3600 IN SOA ns.example.com. zonemaster.example.com. 2632914345 86400 7200 2419200 3600 ;; Query time: 0 msec ;; SERVER: 192.168.200.1#53(192.168.200.1) ;; WHEN: Wed Sep 29 06:20:15 CDT 2021 ;; MSG SIZE rcvd: 122 [21.05.1-RELEASE][admin@sg4860.local.lan]/root:And still running unbound as well - just have bind on different interface that unbound is not running on.. And change the control port of bind.
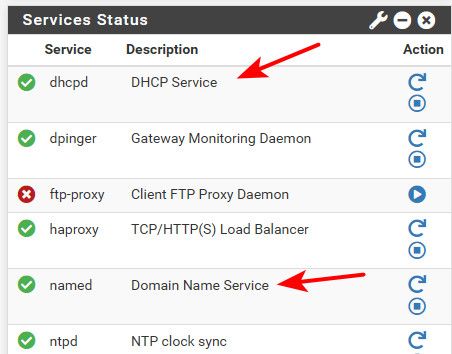
DHCP Server and BIND DNS Server not being able to run concurrently.
They have nothing to do with each other.. Look both running..
-
@johnpoz Thanks, - time for a complete reset, then, I guess, as it would appear that something has been set wrong somewhere.
Is there a way to access the shell via the webConfigurator?
-
@nogosubnet Not sure how you could mis configure either of those that would prevent the other from running since they have zero in common.. They do not use the same ports.. They are completely different protocols..
Is there a way to access the shell via the webConfigurator?
You can run commands via Diagnostics / Command Prompt
If you want a shell - enable ssh and ssh to pfsense.
-
@johnpoz No idea, - I spent hours looking for information on the subject in order to ensure that every had been added correctly, - found absolutely nothing; so I do not know what to do with this now.