Wireless with VLAN not allowing traffic
-
@johnpoz yeah, i mightve done something to mess up that particular vlan...
after i nuked pfsense im planning on recreating one VLAN and test it and go from there.
ideal layout would be to have a vlan for IoT devices, one for 2.4g and one for 5g wifi
-
@dridhas if something isn't working on vlan X or network Y.. Then troubleshoot that thing - not that its tagged or not tagged.
If there was something wrong with the tagging - then nothing would work.. There is no possible way the tag could effect some websites not working while others do - just not possible.
If you had your tagging messed up - then you wouldn't be on that network..
You flipping your client to network Y and works, but move it to network X and something doesn't work - then troubleshoot that something. Firewall rule, dns - something, zero to do with X being a tagged vlan or untagged network/vlan.
-
@johnpoz based on that comment:
ive seen these 2 options:
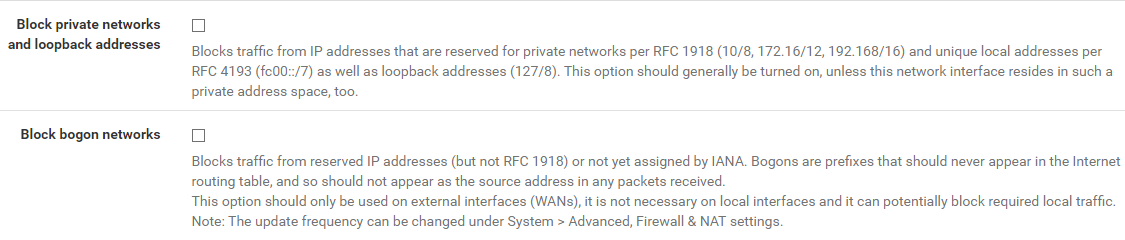
i have those enabled on the WAN interface, would they also need to be on the LAN + additional VLANs?
im unsure if i had them there before. -
@dridhas said in Wireless with VLAN not allowing traffic:
would they also need to be on the LAN + additional VLANs?
What does it say right there on them ;)
Are you using public space on your lan and vlans? I have to assume your using rfc1918 space.. Which you feel you need to hide with your x.x.50.x ? Or did you pull public space out of thin air and and think you could use it on your local networks? That could cause you not to get to some websites, if the network overlaps with what their public IP.
Bogon would never be used internally..
-
@dridhas said in Wireless with VLAN not allowing traffic:
like duckduckgo, if i untag the ports, duckduckgo works normally
VLANs wouldn't do that. Your problem is elsewhere. The VLAN tags don't make it beyond pfsense, so the other end wouldn't know you're using them.
-
There's no mystery here. It works when you untag VLAN 50 at the switch because that just puts it in the LAN subnet.
When it's correctly tagged all clients using it are in the VLAN 50 subnet and use the DHCP you have have configured for that with whatever settings that has. That includes whatever DNS you are passing there.Previously you said clients in VLAN 50 are not able to resolve those sites, which is clearly a DNS issue, but did you mean just unable to connect?
I agree, if you used a public subnet for VLAN 50 that could conflict with the real public IPs and cause this.
Steve
-
@johnpoz no, im not using a public ip, i got lazy to type the whole ip, but it is 192.168.50.x for VLAN 50
-
@jknott im starting to believe that there is a DNS configuration error or a DNS conflict.
on the VLAN in pfsense i used 208.67.222.222 and 1.1.1.1 which are the same for the DNS Server settings under System > General Setup:
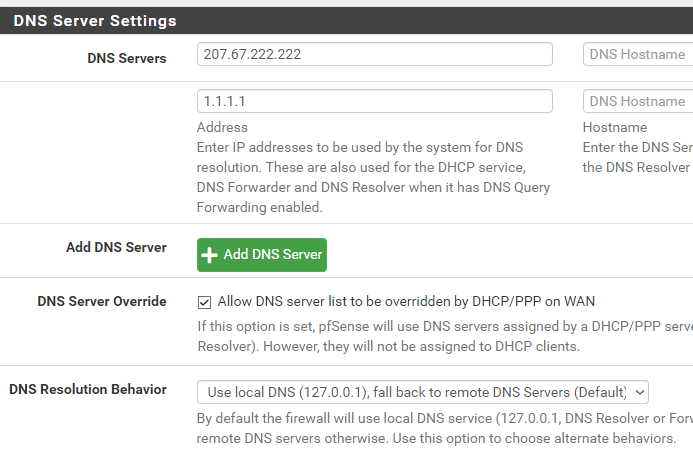
not sure if that could possible conflict.
-
@dridhas said in Wireless with VLAN not allowing traffic:
not sure if that could possible conflict.
Bad idea to use 2 different dns that can respond differently - 222.222 does filtering, while 1.1.1.1 does not..
If your going to have clients or forward to dns, you need to make sure they will always answer in the same way. One that filters and one that doesn't is not good idea - unless you are 100% sure they filter the exact same stuff. Since you can never be sure when more than 1 NS is provided to use, you have no idea which 1 will actually be used for any specific query.
-
Yeah, try just not specifying any DNS servers in the DHCP config for VLAN 50. Clients will use the interface IP and hence Unbound in pfSense by default.
What do you have set for DNS in the LAN DHCP settings?
The servers you have defined in General Setup are probably not being used unless you have set the resolver to forwarding mode.
But if you have you also have 'DNS Server Overide' set so your ISPs DNS servers might be in use.Steve
-
@stephenw10 this is what i have on the DNS Server for VLAN 90 (i created a new one) and on LAN
and this is what i just did on the WAP:
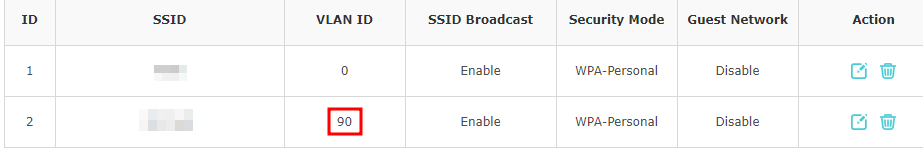
and on the switch:
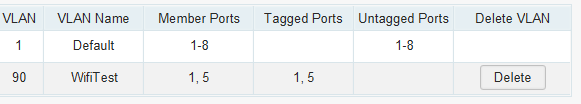
This way, the device can connect to VLAN 90 and it gets the correct ip address as i can see it on the DHCP Leases with the correct IP:
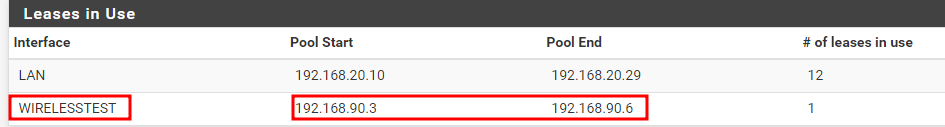
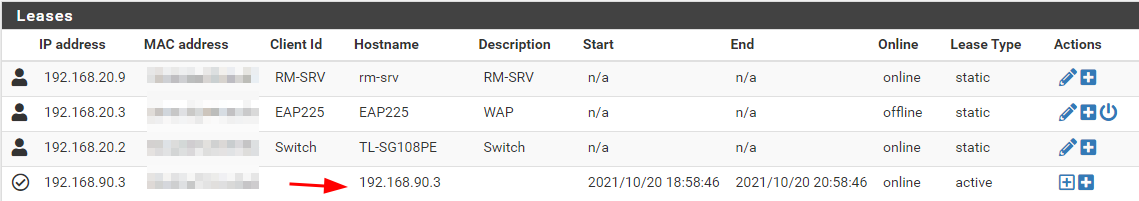
now, i cant get out to the internet on that VLAN... hehehe
-
@dridhas And what firewall rules did you put on this interface? is Unbound listening on that interface? When you create a new interface/vlan unlike lan, there will be no rules. So no until you create rule(s) to allow stuff nobody on that network is going anywhere.
Are you using automatic outbound nat, etc. Seen many a user following some "guide" on the internet for some vpn service switch their outbound rules to manual.. Which then no adding a new network/vlan is not going to work until outbound nat has been created for this new network, etc.
-
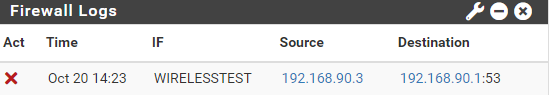
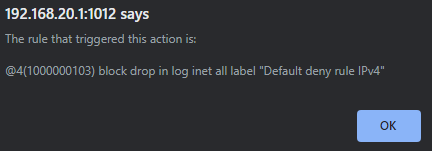
@johnpoz this is what im seeing on the firewall logs:
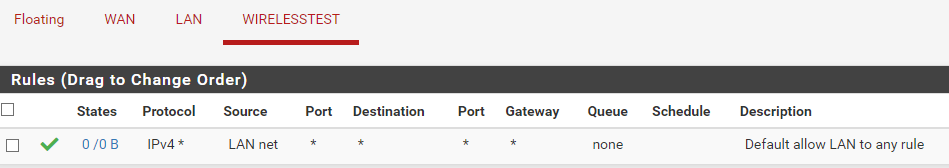
this is the Firewall rule for that particular VLAN:
im trying to find that rule somewhere.
-
@dridhas and how would Lan Net be source of your wirelesstest net?? The source would be wirelesstest net
The default deny is on every interface (hidden) - if traffic is not allowed by a rule, then it would always be denied by the default rule.
192.168.90 is not Lan Net, so that rule would not match, and traffic would be blocked by the default deny.
Looks like you copied the default rule over - but did not change the source to the appropriate network for this interface.
-
@johnpoz yes, you are correct, i copied the rule over to the new VLAN.
after the change the traffic is flowing, but then again some sites are unreachable like duckduckgo among others.
-
@dridhas said in Wireless with VLAN not allowing traffic:
unreachable like duckduckgo among others.
Well does it resolve? Use your fav dns tool from the client.. Where its not loading.
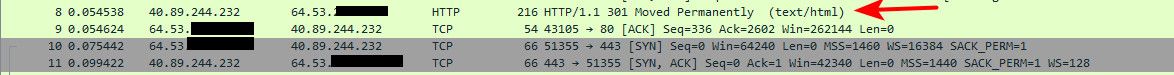
$ nslookup duckduckgo.com Server: pi.hole Address: 192.168.3.10 Non-authoritative answer: Name: duckduckgo.com Address: 40.89.244.232Maybe they are blocking you? Sniff on your wan while you try and go there, do you see the syn go out, do you see a syn,ack come back..
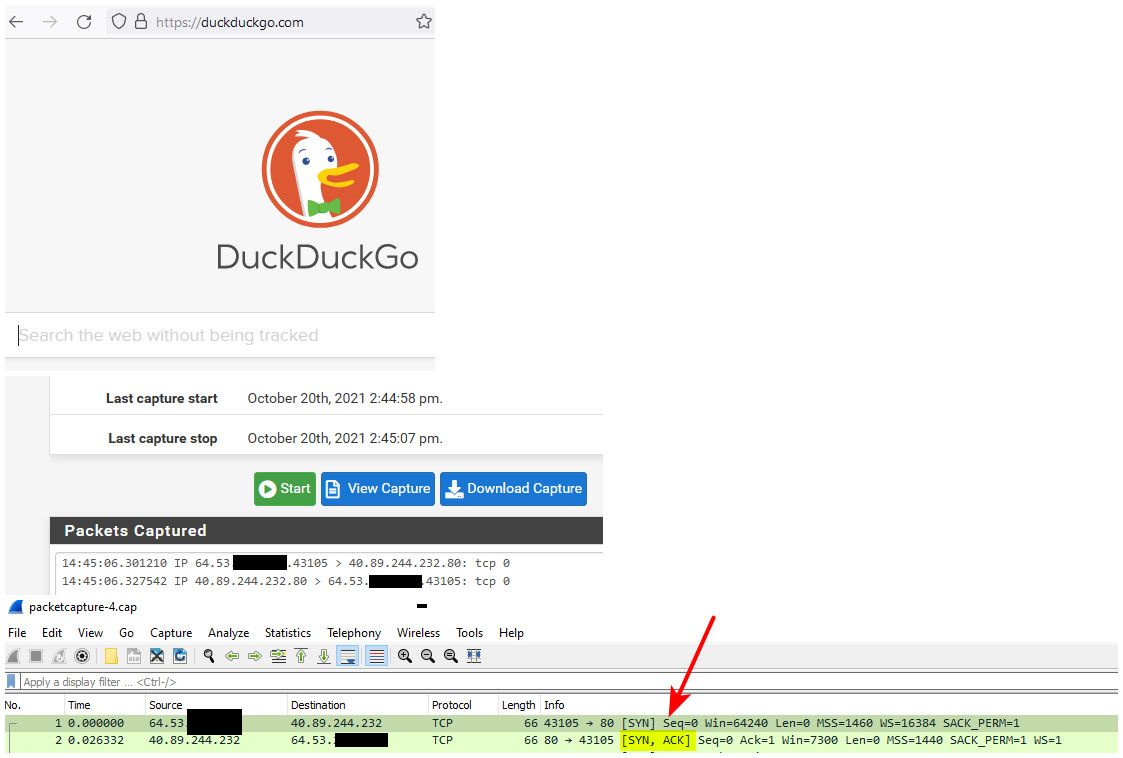
Maybe your browser is using doh for dns? There are many reasons why you might have an issue loading up websites - tags on a vlan or not tag is not one of them.
edit:
what specific sort of error are you getting in your browserCan see they send a 301 redirection, and then the browser connects via https (443)..
-
@johnpoz there is where i have some questions...
WAN outbound is the same for LAN and VLAN.
LAN works fine, but while on VLAN, several websites are unreachable. -
@dridhas first thing is do they resolve? Never getting anywhere if they do not resolve..
You need to troubleshoot the actual issue - not get hung up on this network is tagged this network is not - since that has NOTHING to do with the actual problem.
Now its possible this network is having issue, maybe your wifi connection just sucks and have zeroed in a specific websites not working? Why don't you take wifi out of the equation and plug something in on the switch and put it on vlan 90..
-
@johnpoz said in Wireless with VLAN not allowing traffic:
Bad idea to use 2 different dns that can respond differently - 222.222 does filtering, while 1.1.1.1 does not..
I have my main LAN configured to use the pfsense DNS server, but my guest WiFi points to Google's DNS. Separate subnets, no problem. However, they shouldn't be mixed on the same subnet.
-
Pointing different devices to 1 dns, and other device to a different dns is not what I was talking about at all.. That is fine.
The problem is if a client can use more than 1 NS, you have really no control over which one might be asked, be it your actual client, or the forwarder your pointing to (unbound/dnsmas) etc..
If the NS you could ask for something might resolve differently - filtered or not filtered, your going to have a bad day. Because you never know which one might get asked, it could be filtered when you don't want it to be, or or could be allowed when you want it filtered.