Chrony, PTP, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd)
-
@sergei_shablovsky
IMHO pfSense should continue using the "Industri standard" NTP, that is installed on thousands of servers around the world.If you need ntpsec, do as @johnpoz
Make a dedicated NTP server facing public, with ntpsec , and point your internal servers to the ntpsec box.If i was to change from NTP, to something "Brand new". I would prob. consider Chrony instead.
Or maybe even look at Ntimed (which i suppose have excellent FreeBSD support , since PHK has been digging deep into it) , it just seems a bit immature.
https://news.ycombinator.com/item?id=8781435/Bingo
-
@bingo600
All good suggestions. It's always different thinking "serving NTP" or "I'm a NTP client". Different mindsets, especially if you are making the server available to the general public.ntimed: here's the pkg-descr from the port:
This is a preview/early-acces/alpha/buzzword-of-the-times release of a
new FOSS project written to gradually take over the world of networked
timekeeping.No secret on their goal, is there? :)
-
@johnpoz said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
For us NTP is not fun ;) Just a part of serious work and obligations.
In a work setup - we always ran commercial NTP servers.. I use to manage those back in the day, before I moved to a different department..
Those are not all that cheap ;) But when you have global network and 1000's of devices and clients - no you don't fire up a pi with a gps hat ;) heheh
Totally agree with a You. Sorry, not mention to confuse You. ;)
If I recall some of them were from https://www.meinbergglobal.com
We had a few different ones around the globe.
Really great hardware, I know this brand: VERY robust and reputable. But as any big brand, sometime a little bit sticky to old NTP implementation and not so fast providing fresh firmware updates...
Thanks You again one time for suggestions. I hope this would be helpful for big amount of professionals here.
-
@q54e3w said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
I'd rather have PTP personally.
**Whenever PTP positioned as “instead of millisecond-level synchronization, PTP networks aim to achieve nanosecond- or even picosecond-level synchronization”, I am not agree that “hardware timestamping“ in PTP on non-special server are much better than NTP/NTS, because “hardware timestamping” in this case based on CPU master clocking. But this is not accurate because BIOS/UEFI CPU/RAM settings, I mean threads, buffers, etc...
Generally saying, You are right and I agree with You in case of using separate HARDWARE time-clocking-specialed device (like we see several replies above, 1U rack solution or standalone device with a bunch connectors for GPS/GSM/radio antennas, to receive synchro signals from different sources).
If Your server have no directly attached time-source device, any time sync thru ordinary fiber or Eth would have the same disadvantages.
(If I loose something, just correct me, please)But in this topic I’l try to discuss on scheme “pfSense on server + GPS receiver (or any other time-source device) + Time Protocol”. No matter, for inside networks behind pfSense, or serving NTP for outside users.
-
@bingo600 said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Thank You for opinion!
@sergei_shablovsky
IMHO pfSense should continue using the "Industri standard" NTP, that is installed on thousands of servers around the world.But this is really old, outdated, and vulnerable solution. Agree?
If you need ntpsec, do as @johnpoz
Make a dedicated NTP server facing public, with ntpsec , and point your internal servers to the ntpsec box.As I wrote before, in case using non-specialized time-source device, like a just another one server, we receive some disadvantages:
- power consuming;
- several additional rules for pfSense for internal networks;
- several additional rules for pfSense for NTP users outside;
- another one (+1) point of failure; (for example if You have two(2) pfSense+GPS on COM port in HA-scheme, Your NTP service also protected, otherwise a You need two(2) dedicated NTP servers and synchronization between them...)
If i was to change from NTP, to something "Brand new". I would prob. consider Chrony instead.
Or maybe even look at Ntimed (which i suppose have excellent FreeBSD support , since PHK has been digging deep into it) , it just seems a bit immature.
https://news.ycombinator.com/item?id=8781435/Bingo
Generally say, in IT I am “conservative”” in mind, so rarely try to using “all newest”. ;) This topic I start about really outdated and vulnerable NTP need to be replaced. And mine proposition are NTPsec.
Please, describe in short about advantages Chrony & Ntimed against NTP and NTPsec. Thank You for Your time!
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
**really outdated and vulnerable NTP”” need to be replaced.
What specific vulnerability are you talking about.. Just because NTP has been around long time - does not mean its not been kept up to date for security issues.
While current version is a year so old 4.2.8p15, I wouldn't call it outdated..
-
@johnpoz My understanding of current NTPD is there is a lot of security stuff that can be used/implmented but "it's not the default".
if defaults were changed to be tighter, then new deployments (maybe upgrades) would be tighter but existing ones would need manual changes.
That argument I think applies to ntpsec: new deployments are affected but existing ones aren't.
-
@mer said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
"it's not the default".
Well that is on the runner of the software.. Are you saying there should be something changed in default settings of ntp server on pfsense?
I wouldn't in a million years provide such a service off my firewall to the public internet, ntp on pfsense is meant for ntp server for your local network.
And if I was going to provide it as public service - I would make sure I go through its config, etc. To make sure nothing stupid is in there ;)
edit: There was a thread around here somewhere someone asking about NTPv3 auth - rfc 1305, which you can do with pfsense ntp.. I don't think it was that long ago.. I personally don't get the need to be honest. While sure I could see wanting to make sure your talking to a specific ntp server externally.. Just run your own internal ntp - and not have to worry about any of that.. Not really seeing the need for any sort of ntp security on my own local secure network. If you ask me - just something else that could break ;) For very little security benefit..
-
@johnpoz I agree 100% with you. A lot of discussions around services like this seem to devolve to "the defaults aren't good/secure enough and should change".
50% take that stance the other 50% say "If you are standing something up you need to go through the defaults first".Kind of like "what editor should be the default, vi or ee"
-
@mer agree.. If your not a fan of the defaults - change them.. Defaults are almost always what they are to minimize chance of it not working.. What is the most basic config I can put in - that pretty much a given it will "work". That is the default..
Nobody says that default working config = secure ;)
While I agree as something like pfsense matures and stuff its using evolves - defaults change, and old non secure stuff can drop off. I do recall not that long ago some issues people were having because the changed and dropped off some ssh ciphers from the default config - which broke some users access via their ssh clients, because their clients were out dated, etc.
Default broke shit ;) heheh atleast from the users point of view.. I don't see pretty much anything be it ntp, ssh, web being locked down to tightest mos secure best practice from a security point of view for defaults.. Because its less likely to just work out of the box - which when it doesn't work out of the box, users not happy ;)
-
@johnpoz said in [Network Time Security (NTS, NTPsec) to replace
I wouldn't in a million years provide such a service off my firewall to the public internet, ntp on pfsense is meant for ntp server for your local network.
I totally agree here.
When i worked w. PIX/ASA , there was a sntp client , no NTP service.In fact NTP service prob. doesn't belong on a firewall , just a sync client. pointing to an inside NTP server.
And if I was going to provide it as public service - I would make sure I go through its config, etc. To make sure nothing stupid is in there ;)
The last OOPZ i know about in NTPD was the amplification attack,
and that is easily avoided in the setup today.And i agree with : What security issues needs to be fixed in NTP right now ?
/Bingo
-
I think the security question must be narrowed to have relevance.
NTP sends the time in clear text. (Time is not a secret)
NTP does not validate who it is talking to. (In theory you could use this to be mean to someone, NTP has a sanity check on time changes, check those defaults!)
NTP service has no known vulnerabilities at this time. (Software is secure)
It is simple to use and hard to mess up, does that help security? -
@andyrh nice way to look at it.. I concur!
-
an evasive post but important: (for all :))
I recommend it to all who to use GPSD based stratum1 NTP - follow and update guidelines!!! (on your network NTP source)
https://www.theregister.com/2021/10/19/gpsd_bug_reset/
we run it and it affects our settings:
https://www.ntpsec.org/white-papers/stratum-1-microserver-howto/#RASPBIANthe biggest thanks to Gary Miller and others

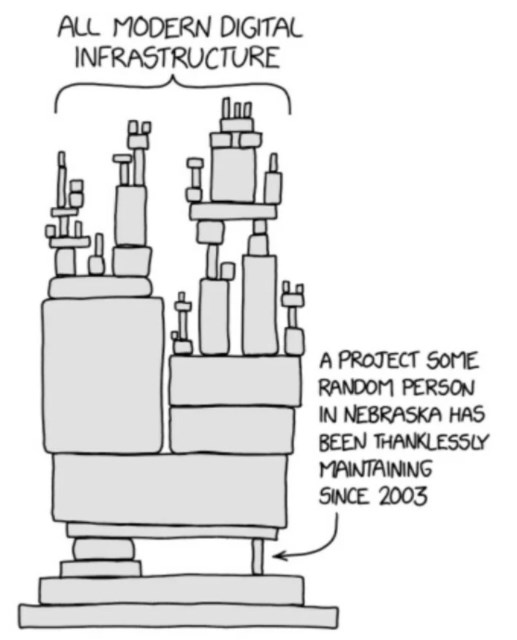
-
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
I recommend it to all who to use GPSD based stratum1 NTP - follow and update guidelines!!! (on your network NTP source)
https://www.theregister.com/2021/10/19/gpsd_bug_reset/
we run it and it affects our settings:
https://www.ntpsec.org/white-papers/stratum-1-microserver-howto/#RASPBIANLet's to remind very old but useful Network Time Protocol: Best Practices White Paper
-
@andyrh said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
NTP service has no known vulnerabilities at this time. (Software is secure)
It is simple to use and hard to mess up, does that help security?“If something in Internet was not already hacked, this is not because it’s strong, it’s because till this time no one pay serious attention on this “something”(c)myself
No one goes deeply and care about how this old things working, but only after a lot of crashes, transporting issues, and some quantity of broken peoples lifes community starting SLOWLY changing mindset about needs to keep up to date old protocols that used in billions devices from your coffee maker, heart cardio stimulator, cars to blood pumps, very big oil & gas sea tankers, citie's energy stations, etc...
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
it’s because till this time no one pay serious attention on this “something”(me)

Hmmm, that's a serious formula, but just think of all the stratum1 satellites... (there are a few of them)
The NTP is currently massive....
(but like everything else it may be vulnerable)everything would be dead without it, think of the stock exchange, credit card transactions that are dampened by prime number encryption and much more....
BTW:
use your power for good things
-
I feel like I am missing something here.
Synchronizing time across the network, even if a single server and single client, means what?
client asks a configured server "what time do you think it is" and then applies alogrithms on the reply.Security wise:
What level of trust does the client have for the server it's asking? One would think the client shouldn't be configured to as clients it doesn't trust.Granted:
NTP servers typically are open, so anyone can ask them, which could result in DOS from the server. But "so what"? Client can't talk to a server?So: I think a lot of this discussion is based on standing up a server not simply being a client.
If your pfSense box is going to have an independent time source at stratum 1, of course make it so only your desired clients (your network) use it as a definitive source of time. -
One thing to remember is you can set up NTP with multiple sources. You should have at least 3, so that if one starts providing bad data, then it will be ignored. This makes it difficult to tamper with.
I have 5 sources, 3 of which are stratum 1 and 2 stratum 2.
-
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
it’s because till this time no one pay serious attention on this “something”(me)
use your power for good things

Sorry my misstyping, I mean that’s phrase made by myself. :)