pfSense Not Routing Packets from OSPF Learned Routes
-
Hello all,
I seem to have a routing problem between my test pfSense and HP/Aruba 5406 ZL2 switch.Context: I am trying to learn OSPF, and setup a network at home with WAN and router redundancy. I only have one public IP from each ISP, so I can't do CARP. I've decided to use OSPF between two pfSense routers and my core switch to handle failover (the backup router has a higher cost set), and this works quite well so far. Below is almost what my testing environment currently looks like, the only difference being the "internet" is actually my internal LAN. (Once the setup is ready, I will simply connect the wan side of my test pfSense routers to the actual modems). I can ping the "Internet" from the switch on either gateway, and the switch routing table flips to the backup if I simulate a WAN failure.
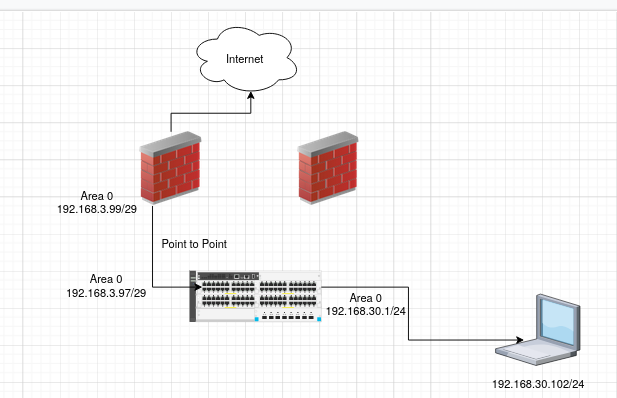
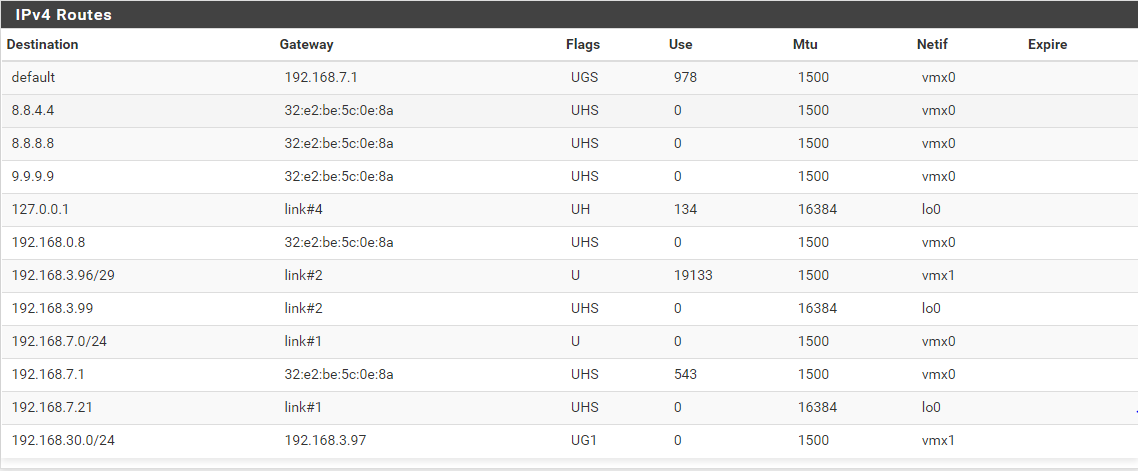
The problem: Computers on the client VLAN (192.168.30.0/24) cannot ping addresses on the "Internet". If I do a tcpdump on the LAN interface pfSense while pinging, I can see the ICMP requests, but not a single reply. This seems very odd as the routing table contains an entry to this subnet through the switch gateway IP. This route always shows 0 use, unless I try to ping 192.168.30.102 from pfSense - which does work. But when I initiate the ping from the client VLAN, the responses are never returned. Additionally, I cannot ping the LAN IP of pfSense from any host on the client VLAN. If I do a tcpdump on the target of the ping, I do not see anything at all. I saw another post on here with a similar issue and the problem being related to outbound NAT. I tried to switch pfSense to hybrid outbound NAT and create a manual rule, which matches source network 192.168.0.0/16 and a destination of any. This does not fix the problem.
Thoughts?
I appreciate any and all guidance on getting this setup working
Switch config:
coresw# show running-configRunning configuration:
; J9850A Configuration Editor; Created on release #KB.16.02.0013
; Ver #0e:01.b3.ff.7c.5f.fc.7b.ff.ff.fc.ff.ff.3f.ef:cb
hostname "coresw"
module A type j9987a
module C type j9987a
ip router-id 1.1.1.1
ip routing
snmp-server community "public"
oobm
ip address dhcp-bootp
exit
router ospf
area backbone
enable
exit
vlan 1
name "CLIENT_VLAN"
no untagged A3,A24,C1-C4,C23
untagged A1-A2,A4-A23,C5-C22,C24
ip address 192.168.30.1 255.255.255.0
ip ospf 192.168.30.1 passive
ip ospf 192.168.30.1 area backbone
dhcp-server
exit
vlan 2
name "GUEST"
untagged A24,C23
ip address 192.168.200.1 255.255.255.0
dhcp-server
exit
vlan 103
name "wan-backup"
untagged C3-C4
ip address 192.168.3.97 255.255.255.248
ip ospf 192.168.3.97 area backbone
ip ospf 192.168.3.97 network-type point-to-point
exit
vlan 111
name "wan-primary"
untagged A3,C1-C2
ip address 192.168.3.105 255.255.255.248
ip ospf 192.168.3.105 area backbone
ip ospf 192.168.3.105 network-type point-to-point
exit
dhcp-server pool "guest"
default-router "192.168.200.1"
network 192.168.200.0 255.255.255.0
range 192.168.200.50 192.168.200.100
exit
dhcp-server pool "client"
default-router "192.168.30.1"
network 192.168.30.0 255.255.255.0
range 192.168.30.100 192.168.30.200
exit
dhcp-server enable
-
Is outbound NAT (Firewall > NAT, Outbound) in place?
pfSense adds outbound NAT rules for networks it knows about, like connected and static routes, but it has no idea about routes learned dynamically. That is the responsibility of the network administrator.
-
@jmarmorato Sounds like the default gateway on the inside host isn't pfSense or the traffic is otherwise not routed properly on the inside.
-
@derelict Yes, I had outbound NAT configured.
I'm embarrassed to admit that I neglected to check the firewall rules - The default allow all rule only matched packers sourced from the LAN subnet, not any subnet behind the LAN interface.
All is working now.
Thank you for your time!