TP-Link AC1750 - What's wrong with LAN/AP?
-
When I started looking for a version that runs on this old wifi router, I came across many posts saying always use an internal AP, never use this kind of device as your Internet connected one.
I'm wondering why? I mean, I totally understand that wifi is more reachable than wired but if you properly set things up, what is the problem really? How is it any different than putting an AP inside your LAN? Now you have someone that could in theory already be inside your LAN if they were able to get into your AP from remote.
To me, it seems as simple as setting up a dual LAN, one for wired and one for the wifi stuff then the WAN is connected to the provider.
Both LAN's would be separated, rules used for any communications between them, the usual.
What am I not seeing?
-
Around here, the advice has been to use an external AP, as support for WiFi NICs is poor in FreeBSD. I use a Unifi AP. Many people use a router as an AP by connecting the LAN side to the LAN and ignoring the WAN side.
My AP is connected to my main LAN and also, with a 2nd SSID, to a VLAN for my guest WiFi.
-
Oh, I must have missed that in the posts I found. I didn't notice they suggested putting the AP outside of the LAN.
That makes sense however, because it's a wifi device, easy to access, always possible to exploit.
To be sure I understand...
One setup I have looks like this.
Wired LAN to LAN side of pfsense. pfsense LAN side to provider.
wifi router WAN goes to the LAN side of the above pfsense.Suggested;
Wired LAN to LAN side of pfsense. pfsense LAN side to provider.
wifi router WAN goes to the LAN side of the provider.This effectively prevents a wifi hack from already being on the LAN.
Then, if I want any wifi traffic allowed back to the wired LAN, I can set up rules that allow the LAN IP from the provider side to be allowed to specific things on the wired LAN side.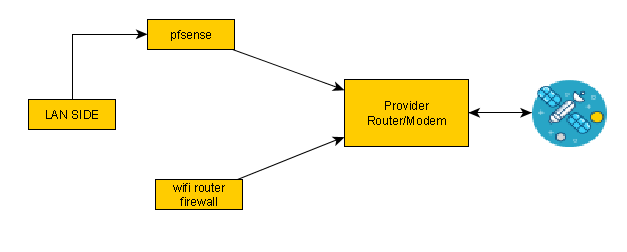
Not sure I'm explaining this well. Have I got this? -
WiFi is normally on the LAN, as it makes accessing various devices easier. I haven't had my WiFi on a different subnet since the days of 802.11b WiFi, with the crappy WEP encryption. With WPA2 or 3, that's not much of a worry. So my access point is on the same subnet as my main LAN, with only the guest WiFi on a different subnet.
-
I would put wifi on a different interface on pfSense if you can. That way you can filter between the wifi and wired subnets. If you need them to be on the same subnet you can always bridge the interfaces and still filter traffic if required.
https://docs.netgate.com/pfsense/en/latest/wireless/bridges.htmlSteve
-
Great input, thanks.
What about my thinking above? That could work well too and I would not need an additional interface and still keep it all separate.
-
Yes, that would work. But if would be much harder to allow connections between WIFI and LAN if you ever needed to.
Steve
-
Hmm, yes, I see that now.
-
@stephenw10 said in TP-Link AC1750 - What's wrong with LAN/AP?:
I would put wifi on a different interface on pfSense if you can. That way you can filter between the wifi and wired subnets. If you need them to be on the same subnet you can always bridge the interfaces and still filter traffic if required.
https://docs.netgate.com/pfsense/en/latest/wireless/bridges.htmlSteve
I think I'll go this route. Thanks for all the input.
-
@stephenw10 said in TP-Link AC1750 - What's wrong with LAN/AP?:
I would put wifi on a different interface on pfSense if you can. That way you can filter between the wifi and wired subnets. If you need them to be on the same subnet you can always bridge the interfaces and still filter traffic if required.
Why would you even do that if you're just a regular LAN user? If you're worried about guests, put them on their own SSID/subnet and allow only access to the Internet, as I have done.
Many people might use a computer on WiFi sometimes and directly connected others. Why should there be a difference for them?
-
Well it depends how you have your devices setup I guess. For me I have a bunch of things on wifi that have no good reason to be able to access everything on LAN but need to be on the same subnet as general wifi clients to be 'discoverable'.
But however you have it setup using a separate interface (if you have one) gives you the most flexibility.Steve
-
I always used separate interfaces in the past, I'm not sure why I didn't think of doing that with pfsense and that's what I'll be doing. Then I can allow only the ports I want and if someone ever gets in via wifi, they won't get access to much.