pfSense setup recomendation - yet another one
-
Hi genuine noob here in need for hardware recomendations,
I'm thinking of deploying pfSense in my home network. I'm currently watching 3 available options for me:
- Dell Wyse 5070 - Intel J5005 (lowest power consumption)
- HP Thin Client T730 - AMD RX-427BB (cheapest)
- Lenovo ThinkCentre m720q - Intel i5 8500T or G5420T (maybe best future proof)
My current setup:
- Huawei E5186 - 4G-LTE router (used as DHCP server, port forwarding, firewall, WIFI AP), WAN connection up to 100 Mbps
- HP 1820-8G managed switch - connected to Huawei E5186
- Netgear GS108Tv2 - connected to HP 1820 (trunk 2 ports, LACP dynamic)
Wired devices (all connected to HP 1820):
- Synology DS918+ - trunk 2 ports (used as backup storage, Emby server, Docker, DDNS client, GitServer, accessible from WAN via port forwarding on Huawei router)
- Two desktop PCs
- Nvidia Shield TV pro - main media center, Netflix, Emby client, Hbo go, light gaming
Wired devices (connected to GS108T)
- TV, AV receiver - only for firmware updates (not so much important)
- Network media player (DAC) - Tidal client, BlueOS (doesn't need much speed for music)
Wifi devices (currently all connected to Huawei)
- 4-5 mobile phones
- 3 laptops
Main problem in my current setup is Huawei, almost every time 4G connection is dropped router needs to be rebooted and all devices lose their connection.
I bought new WIFI AP (Unifi WIFI 6) so I'll shut down WIFI on Huawei. New AP will be connected to HP switch. I was thinking to put Huawei router in bridge mode and not to be used for anything except as 4G modem. On new router I would do everything else like port forwarding, DDNS, NordVPN for PCs and phones, basic security, I really don't know much about pfSense so I can't say what else I will use. Only devices needed to be accessible from WAN are Synology NAS and my PC.
I need for LAN to be up even if WAN connection is down. Cause I don't have Gbps WAN, my main concern is getting steady 1 Gbps LAN connections and reasonable power consumption. I don't know if I'll ever have better WAN connection, maybe in few years if someone bring optic fiber to place I live.
So which of those 3 devices would you recommend for my case?
Should I disconnect 2 switches from each other and connect them both to pfSense router or it is ok to leave them connected?Thanks in advance :)
-
@lawri
Everything here is my opinion.What's the WAN connection? Cable modem, fiber, or the 4G/LTE path?
If the WAN is over the 4G/LTE, then it becomes interesting.
SG3100, SG5100, SG6100 are probably all suitable (not sure how they compare to your 1-3 options).
But:
If the Huawei is your WAN, I would disable everything else on it and simply use it for broadband to pfSense. The pfSense device can/should handle everything else like DHCP, firewalling. WiFi AP would simply be something plugged into pfSense device.
Simple switch (managed/unmanaged whatever you need) for all the wired devices (WiFi AP can plug into this). -
@mer said in pfSense setup recomendation - yet another one:
@lawri
Everything here is my opinion.What's the WAN connection? Cable modem, fiber, or the 4G/LTE path?
Huawei is 4G/LTE connected to ISP.
@lawri
If the WAN is over the 4G/LTE, then it becomes interesting.
SG3100, SG5100, SG6100 are probably all suitable (not sure how they compare to your 1-3 options).Those 3 are much more expensive appliances, don't know if I need them at all for home use.
Thanks
-
@lawri said in pfSense setup recomendation - yet another one:
Those 3 are much more expensive appliances, don't know if I need them at all for home use.
Understood. I was using them as examples "processing power" as I don't know how your 3 options compare (yes, I'm feeling lazy and didn't look them up).
Basically anything with 2 interfaces running at 100M or 1G should be fine for the pfSense device. You'd be putting the 2.5CE (or whatever is latest Community Edition) on them. My point about "a pfSense device with adequate resources should be able to run everything you need, just make the Huawei device be the WAN and only the WAN for the pfSense device".Hopefully that make sense.
-
@lawri said in pfSense setup recomendation - yet another one:
I need for LAN to be up even if WAN connection is down. Cause I don't have Gbps WAN, my main concern is getting steady 1 Gbps LAN connections
There's no reason the LAN would go down if the WAN does.
You only need 1G LAN connections if you are going to be using multiple internal interfaces and routing between them. VLANs perhaps? Otherwise you will only ever see the WAN-LAN traffic there at the available WAN bandwidth.
Steve
-
@stephenw10 said in pfSense setup recomendation - yet another one:
@lawri said in pfSense setup recomendation - yet another one:
I need for LAN to be up even if WAN connection is down. Cause I don't have Gbps WAN, my main concern is getting steady 1 Gbps LAN connections
There's no reason the LAN would go down if the WAN does.
That is happening on my current router, I need to reboot it every time it disconnects from WAN and in that time my LAN is also down.
That is what I noticed. Maybe problem is something else in router, too weak to be router and AP and DHCP so it shuts down every day once. :)You only need 1G LAN connections if you are going to be using multiple internal interfaces and routing between them. VLANs perhaps? Otherwise you will only ever see the WAN-LAN traffic there at the available WAN bandwidth.
Steve
I was referring on gigabit traffic between devices in local network. Does router have anything to do with that, I mean CPU power of router? I'm maybe asking stupid questions, but my knowledge of networking is limited. Also English is not my native language.
If cpu of router doesn't have anything to do with local traffic in LAN then cheapest of those 3 is my best option :). -
Yeah, that sounds like some quirk in the Huawei router you have. pfSense would not disconnect the LAN if the WAN goes down. You may see some slowness connecting to it initially in that situation because the initial page, the dashboard, tries to check for updates etc.
Traffic between hosts on the same subnet doesn't go through the router so you should never see any throttling due to the LAN side interface or CPU. The only exception to that is if you have bridged interfaces but it's unlikely you would do that.
Almost anything will have no problem routing/filtering etc at 100Mbps.
Steve
-
@stephenw10 Thanks for answer
What is right way to connect 2 switches to pfSense router?
I have two with 8 ports, should I connect one to LAN port and other to OPT1 port on pfSense router? Then I have to set 2 VLANS? -
@lawri
My opinion:
If you are setting up LAN and OPT1 as 2 different network segments, say one on 192.168.1.0/24 the other on 192.168.5.0/24 then one switch connected to LAN, the other connected to OPT1. That gives you separation, so you could use LAN for your home/personal network, OPT1 could be for work or a guest network. Then setup firewall rules on LAN and OPT1 to block or allow traffic as needed.If you need VLANs and the switches support them, then set them.
If you don't need VLANs or the switches don't support them, don't set them.
Typically VLANs are used to give you separate network segments when you don't have enough physical interfaces to do what you want. -
Yeah it depends how many internal network segments you have and where those need to be available.
So if you have multiple VLANs and need to be able to connect hosts on either switch to any VLAN then you would probably want to connect the switches to the same interface in pfSense (or a LAGG pair).
If you have only two segments and can have hosts divided on each switch then you could connect one switch to each interface on pfSense and avoid using VLANs at all.Steve
-
This is what I want to achieve.
Can you look at it and give suggestions?
I think I have to use VLANs for this.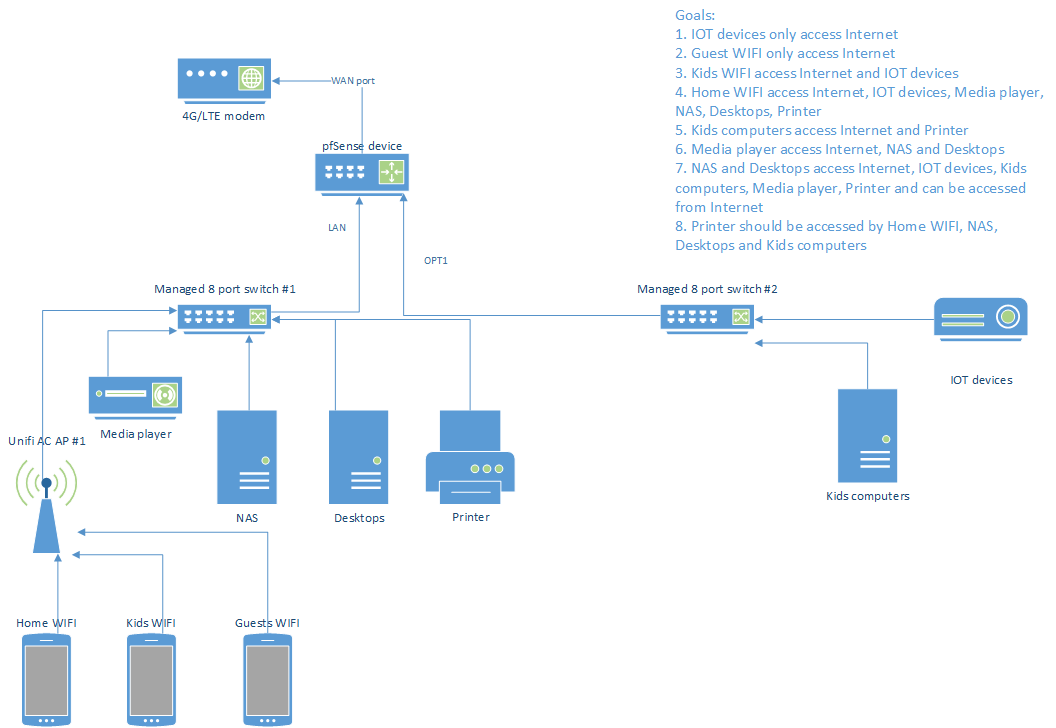
-
Yes, you would need VLANs to separate the different devices on each switch. However it doesn't look like you have hosts on any particular segment on both switches so it should be fine as shown in the diagram.
Steve
-
@stephenw10 Thanks
I need to do like this cause I don't want to buy new switch with more ports.
Maybe in future. -
In the end I went with Dell Wyse 5070 Extended.
I also put Dell 09YD6K 4-Port 1 Gbps Ethernet NIC inside.
That is Intel i350-T4 card.
I had problems with this card cause when I put it inside, dell was not posting anymore.
It signaled memory problem.
So if anyone has similar problem with i350 card, solution is to block pins B5 and B6 with electric tape.
After that it posted and everything works ok.
Solution was found here: Modding a Dell Perc 6 / Dell H310 / Dell H710 (other LSI 1078 or 9223-8i based) SAS Raidcontroller.
In comments on that blog post, someone mentioned i350 NIC.