Home Network Design
-
Hi,
I just took a custom box that I'll use to run PfSense.
I'm not a network engineer, so you need to expect basics in the language here :DI need to design my home network at its best, this is my plan overall:
-
ISP modem/router (necessary for IPTV, or almost)
-
PfSense Box (at this point, it will become an L3 switch, can I call it in this way?)
-
Some L3 switch afterwards, or also L2 should suffice as long as it can connect to the specific VLAN configured on the PfSense port (which is configured on the PfSense box, so I don't see any issue)
-
APs (I'll mount 2 in 2 different VLANs). For my knowledge, also a consumer grade router makes the job after the PfSense box, I just want to recycle some consumer grade router before to buy business APs like Ubiquiti. Less I spend on it, better it is, but since WIFI 6 and the new protocols + 5GHZ antennas, I think it will cost me a bit anyway.
Looking at this, it seems that WIFI 6 is useless at home: https://en.wikipedia.org/wiki/Wi-Fi_6
My usage will be:
-
IPTV
-
Gaming (I need low latency, so DPI may play a bad game here, but I got performance :D )
I chose Qotom, not many other choices available this period, below there are the reasons. -
Chance of fallback on X86 architecture in case I face some problem with PfSense (I doubt), I may use this box for something else
-
I've chosen the Intel i5 8250U CPU, really the best considering the TDP of 15W and 4 core - 8 threads (major shift after the Intel series 7), otherwise it would have been 35W TDP.
-
16GB of Ram, I know it's a lot but the fallback needs may be 16GB of Ram... Plus I don't know how much the plugins can take with many VLANs etc, looking online, it's very difficult to exceed 4GB with 1Gbit download... Not sure with many devices though, but it shouldn't make much difference.
-
SSD is not important, I don't need much space, in the worst case, I'll dump the network traffic on another HDD, but the USB bandwidht may not be enough. So I've chosen 256GB SSD.
-
Network card is fundamental. The box I've chosen has 2 network cards
 , both supported.
, both supported.
I have 8 Gbit (8 ports) with no uplink port though.
Based on my knowledge, I have 1 Gbit on the LAN port that I'll configure as a WAN port towards the modem/router.
Other common needs such as banking, personal stuff etc, certainly more important than gaming :D .
In future I may need videocameras on the LAN, but it's not for the near future.What do you think?
-
-
@jt40 said in Home Network Design:
- PfSense Box (at this point, it will become an L3 switch, can I call it in this way?)
Please don't call pfSense a switch , it's a L3 Firewall
- Network card is fundamental. The box I've chosen has 2 network cards
 , both supported.
, both supported.
I'll clarify that "2 network cards" for others.
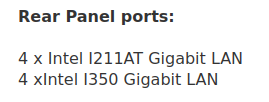
I have 8 Gbit (8 ports) with no uplink port though.
Any of the Lan ports can be Uplink .... You just don't have a dedicated uplink port
Based on my knowledge, I have 1 Gbit on the LAN port that I'll configure as a WAN port towards the modem/router.
I'd just use the lowest marked port (prob Port1) , or whatever is seen as igb0 on the pfSense.
Nice Box , but what was the total end price ?
/Bingo
-
@bingo600 said in Home Network Design:
@jt40 said in Home Network Design:
- PfSense Box (at this point, it will become an L3 switch, can I call it in this way?)
Please don't call pfSense a switch , it's a L3 Firewall
- Network card is fundamental. The box I've chosen has 2 network cards
 , both supported.
, both supported.
I'll clarify that "2 network cards" for others.

I have 8 Gbit (8 ports) with no uplink port though.
Any of the Lan ports can be Uplink .... You just don't have a dedicated uplink port
Based on my knowledge, I have 1 Gbit on the LAN port that I'll configure as a WAN port towards the modem/router.
I'd just use the lowest marked port (prob Port1) , or whatever is seen as igb0 on the pfSense.
Nice Box , but what was the total end price ?
/Bingo
Thanks for the answer.
Ok, L3 Firewall, sound better :D .
Can I install another PfSense box in replacement of a switch? Basically right after the main PfSense box.
If I'm not wrong, the majority of switches have only cli, no user interface, so with PfSense I should find myself more comfortable. It's going to be a bit more expensive but I think it's the best solution.The uplink port is usually faster, but in my case, it's not a problem, I won't go over 1Gbit in this decade minimum :D , not even 500 Mbps...
Price? Do you really wanna know? :D Almost 500 pounds, I don't even remember the precise amount, I don't wanna see the bill (including import tax) again :D :D :D
So, am I good with the performance required in latency if I also use DPI and other features like Surricata?
I don't even bother with bandwidht, it's overkill. -
@jt40 said in Home Network Design:
If I'm not wrong, the majority of switches have only cli,
Your wrong - most all switches from the cheap entry level smart switches that don't do much other than vlan support, to higher priced smb/enterprise switches support gui..
While it is "possible" to use some interfaces and cpu as a "switch" via bridging interfaces its never going to be an optimal sort of solution.
If what you want is a switch, be it L2 only or L3 capable - get a switch.. Using a box that is suited for your pfsense firewall/router as a just a "switch like device" while sure ok technically possible is not good use of such hardware.
There are many a entry level 8 port gig smart switch for like $40 price point that would be way better suited and way less power hungry than some boxed spec'd to be your firewall/router..
I have a cisco sg300-28 port switch with sfp support on combo ports that can do both L2 and L3, and got for less than $200 new.. Both gui and ssh and console access, etc. Uses a few watts, no fans, etc. And way more "switch" features than you would ever get from using some multi port nics with bridging enabled between interfaces..
There are some really home budget friendly switches that support sfp or even sfp+, etc.. Take a look at the mikrotik switches for example..
My suggestion would be if you want a switch - get a switch.. There is sure to be something that fits your needs and fits in your budget.. 2nd hand enterprise is always a possible option as well off ebay for some really heavy feature rich stuff.. But normally comes at price of noise and power use that can be a hinder to the overall experience and ROI even though they might have an attractive price to feature ratio..
-
@johnpoz Thanks for the answer.
At least the PFSense box is not useless :D .Regarding the switch, I have a crucial question, suppose that after the port n.1 I attach a switch, and the VLAN name is VLAN 1, then I can't create additional VLANs after the PfSense box...
I consider this because each device should be isolated unless specific cases, as you can imagine, I have more than 8 devices... A switch afterwards is mandatory for me, but I wonder how I can properly make the most of it...
Can I separate the connection of the devices under the same VLAN?
Essentially, fea of them will be in the same VLAN, or even all of them if this is possible.
At least the VLANs are separated from PfSense.The major VLAN divisions would be due to my devices and work related devices.
-
@jt40 huh?
You can run as many vlans as you want within reason, there is a specific limit of vlan Ids that can be used 2-4093, etc.. Not understanding what your asking?
Can I separate the connection of the devices under the same VLAN?
Yes if your switch supports what is commonly called private vlan, or some switches might call it port isolation. In the wireless world is called client or AP isolation, etc. This isolates devices from each other that are on the same vlan.
If your switch supports L3, you could for sure have it route other vlans/networks you might be using downstream of pfsense that pfsense would have no clue to what vlan ID you are using on them, etc.
I have more than 8 devices
I have some 30+ devices on my network at any given time. Broken up into currently 8 different networks/vlans, etc. Some tagged and pfsense knows the vlan IDs for these, and others are native (untagged) where pfsense has no idea what the switches vlan ID for those networks are, etc.
Something like private vlans or port isolation might not be supported by your $40 entry level smart switch.. You will have to look into the specifics of the switch and what features are supported.. There are lots and lots of different protocols that you may or may not want/need to take advantage of at layer 2, etc. That might be difficult doing bridging on interfaces to simulate a switch.. Port spanning one that comes to mind, difficult to do something like igmp snooping etc most likely as well with just bridging. LACP or port or etherchannel sort of stuff.. The feature set of different switches can be vary different.. All comes down to what you actually want to do - if you need a switch that supports more than basic vlans, etc.
Something your entry level switches might not do is say multicast ACLs where you can block multicast traffic at the port level, etc. I do this on more than a few ports because have some chatty devices that spew multicast that I do not like on my network just from hey not using it point of view no reason for the noise sort of thing..
The stuff you can accomplish at layer 2 with a actual real switch that is feature rich is going to be far superior to what you could do with bridging some interfaces in software - let a lone the overall performance comparison.. There are few instances where bridging can be useful - but its not a replacement for actual switch by any stretch of the imagination that is for sure.
Look at this way can I use the back end of screwdriver as a hammer - sure its possible.. But its not the proper tool for the job..

-
@johnpoz said in Home Network Design:
The stuff you can accomplish at l
Thank you.
You recommended an L2 switch in the end, did you mean L3?
Without L3 I won't have routing capability, L2 VLANs are quite limited, despite the concept of VLAN can be applied also at L2.I have other questions:
-
What switch (L2 or L3) do you recommend that doesn't create any kind of conflict with a PfSense Firewall?
-
I would tag my VLANs, but you said that what happens in PfSense won't have anything to do with a VLAN in the L3/L2 switch...
Did I understand correctly? Is there no way to pair the VLANs IDs?
I'm not sure if I'll need such thing, but initially it seemded to be the right thing to do.
The reason why I'd add an L3 switch is to have more ports, that's it.
The fact that I can block multicast etc, ok, but I thought that also PfSense can do it... Maybe yes but it happens on another layer, and surely on a different device.Certainly, the fundamental thing seems to be the functionality of private VLAN, without it, it would just be a simple HUB, right?
-
-
@jt40 your pfsense can route.. But sure if you really want to route at your switch, there are reasonable L3 switches.. My sg300 does L3, I don't really use it for that, other then if want to lab something for something. My sg4860 handles all my routing needs, and adds the ability of simple firewall rules between vlans - which while you can do acls and such at a L3 switch - the firewall capabilities are normally quite limited.. And difficult to maintain and configure vs just point and click in pfsense.
-
@johnpoz So you are suggesting to keep my PfSense box as an L3 firewall, then add up an L2 switch, it seems reasonable to choose 24 ports for the future.
For me, the form factor has to be fanless, what brand do you recommend? Unfortunately, Netgate doesn't make L2 switches.
With 500 pounds budget I could have purchased the Netgate 2100 and an L2 switch with 24 ports :*(
Coming back to the businees:
-
I had a quick look online, TP-Link seems to be the cheapets, are they good?
-
What about an AP?
Ubiquiti? These are quite expensive :D , also there I need client isolation!
-
-
I still have few doubts:
- I had a quick look online, TP-Link seems to be the cheapest, are they good?
I don't ask only for the price, but also for the availability and the fact that they are quite recent, instead, brands like HP (became Aruba for network appliances) and Cisco are basically all old, for example, your sg300-28 is going to be out of support in 2023... I don't even mention HP...
It's also important to notice that the new TP-Links are available in UK, the others need to be imported, unless I buy something used without warranty in UK...
The idea is one of these 2, most probably the one with 24 ports
https://www.tp-link.com/us/business-networking/managed-switch/t2600g-28ts/#overview
https://www.tp-link.com/us/business-networking/managed-switch/tl-sg3452/#overview (they still release updates for this)The probelm with TP-Link seems to be the support, after 3 years good bye... When I look at Cisco and HP though, it seems that they both reduced the support, better than TP-Link but this is not the moment to enter first in the timeframe... As an example there is your sg300.
-
Certainly I'll need to choose an L2 switch that doesn't have PoE ports, they consume much less energy (max 20W ) and 24 ports are enough for me, against 250W+ for a PoE switch
 .............................................................
............................................................. -
I have a doubt on these 2 products, I'm not oriented with these products but I'm curious to discover why that huge difference, I'm not able to understand the reason behind the TDP difference:
https://www.arubanetworks.com/assets/ds/DS_2530SwitchSeries.pdf
-
Aruba 2530-24G Switch
(J9776A)
Maximum power rating 14.7 W
Idle power 8.4 W -
Aruba 2530-24 Switch
(J9782A)
Maximum power rating 48.0 W
Idle power 28.8 W
-
What about an AP?
Ubiquiti? These are quite expensive :D , also there I need client isolation!
Do you suggest to set 2 different APs for work and home network? Ok client isolation, but I'm not sure about the real isolation that it offers :D , moreover I don't know if I can setup the routing of the devices connected through WIFI in different VLANs. -
I have an important requirement, that is to set the VPN on the router for a specific VLAN, I think I can do it with PfSense without troubles.
The question is: can I enable the VPN for a VLAN that is defined in L3, but after that I have an L2 switch that pairs the same VLAN ID?
Probably my networking knowledge should be better :D , but I think that the switch will only switch, I won't create a VLAN at L2, but only in the PfSense box.
If my assumption is correct, then how the PfSense box will get the device ID? Is it only about the MAC?
I also assume that I'll rely on the L2 private VLAN, but it's not the VLAN at L3, right?
The intention is to create VLANs and some of them will have a VPN from the PfSense box.
At the same time, the devices should not talk each other, they should not even see each other, which I believe is the purpose of a private VLAN.
This unfortunately confuses me, until I don't have a switch in front of me I can't test it, so that's why I ask here.
The moment I set the private VLAN functionality in the L2 switch, then is it just about creating VLANs at L3???
Are these things completely indipendent? - I had a quick look online, TP-Link seems to be the cheapest, are they good?
-
@jt40 said in Home Network Design:
TP-Link seems to be the cheapest, are they good?
For a switch - I wouldn't go that route.. There are many a thread even here, and all over the net, even their own forums where they wouldn't let you remove vlan 1 from ports you wanted to put in another vlan, etc. Took them forever to fix, and then didn't port it backwards to their old models.
They said it was normal <rolleyes> on their own forums until they finally fixed it.. They don't seem to understand how vlans are suppose to work ;)
can I enable the VPN for a VLAN that is defined in L3
Yeah could policy route for a network that is downstream of pfsense..
Ubiquiti? These are quite expensive
Guess that is relative, they are very reasonable priced if you ask me - for what they do. You can pick up a lite model for under 100.. I show the uap-ac-lite over at baltic for 80$ currently. I believe they are sold out of their wifi 6 lite model, but that retails for 99$
Sure some of their higher end model are a bit pricey for a home setup, like the SHD which I would love to have to play with, but at $500 I don't want to play with it that much ;)
I have 3 of their AP currently, the UAP-AC-PRO, the lite and the LR.
-
@johnpoz Thank you.
The Ubiquiti switch you mentioned is this one?
https://store.ui.com/collections/unifi-network-switching/products/usw-lite-16-poe , 200 dollars/pounds new, not bad, even though I find it much cheaper on unofficial stores...In this link you find the AP from Ubiquiti, in the bottom of the page, do you mean the first one on the table? U6 Lite?
https://www.ui.com/wi-fi#compare
Will I be able to separate the connection between 2 different devices and put them in 2 different VLANs?
As you understood, I'll have PfSense --> Switch --> AP, so the VLANs creation would be in the switch first, or directly in the PfSense box, not sure what's best :D , but at least I want to be sure that I can do it in somehow.
Basically, my WIFI devices have to be in different VLANs. -
@jt40 not switch AP... I didn't recommend a switch.. Not really a fan of their switches..
Yes ALL of their AP support vlans.
-
@jt40 said in Home Network Design:
The idea is one of these 2, most probably the one with 24 ports
https://www.tp-link.com/us/business-networking/managed-switch/t2600g-28ts/#overview
https://www.tp-link.com/us/business-networking/managed-switch/tl-sg3452/#overview (they still release updates for this)Those switches would likely be fine. TP-Links 'business' switches are a world away from their SOHO devices, might as well be a different company. I have a T1700G-28TQ and would have no problems recommending it, though only if you need 10G.
A PoE switch is not going to use 250W unless you have a load of PoE devices drawing power from it.
Steve
-
Mixed up posts
It was my understanding that the OP already had a PoE switch , that might be "unsafe" to use with multi vlan (as L3 routing can't be disabled.But if all the Cameras that need PoE , would be put in the same Vlan. Then why not try to use that switch for the PoE part, and just run a single "untagged" port from the "core switch" to the PoE switch.Now the "core switch" could be a cheap xx-port L2 managble switch./Bingo
-
@bingo600 said in Home Network Design:
(as L3 routing can't be disabled.
huh.. What switch would be like that, even if supports L3 if you do not setup any SVIs it has no way to route.. Mine is in L3 mode, but it only has the 1 SVI used for management, so there is no way it can "route"..
-
@johnpoz
Think i have mixed up this thread with another -- OOPzzz
Forget the above./Bingo
-
@bingo600 no biggy some of these threads are close in nature.. I for sure have done that a few times ;)
-
Thanks everyone so far, but this thread will be a bit in this way, I'll keep asking questions :D until I don't saturate your patience :D
I came across Cisco Meraki, I was excited for the price, support and performance, but guess what, this is what you find in the end of this thread: https://forum.netgate.com/topic/160537/pfsense-cisco-switch-ms220-24p/18
A Meraki switch is cloud managed and needs to be able to see the internet for it to work. Here is what the lights mean: https://documentation.meraki.com/Go/Meraki_Go_-_Decoding_the_LED_Light I would reset the Meraki switch to default and then connect to pfsense box. See restore button: https://documentation.meraki.com/MS/MS_Installation_Guides/MS_End_of_Sale/MS220-24%2F%2F48_Series_(EOS)_Installation_Guide I have number Meraki switches and if they cannot see the internet they do not boot.I'm speechless, what about if my Internet goes down?? It doesn't even boot?


What about if it's already ON, does it turn OFF?

I'd like to take this switch precisely, if I don't go with TP-Link: cisco meraki ms220-24p
Not easy to find in the list of supported devices, not sure why , but you can find it here: https://meraki.cisco.com/lib/pdf/meraki_datasheet_ms_220_320_only.pdf
, but you can find it here: https://meraki.cisco.com/lib/pdf/meraki_datasheet_ms_220_320_only.pdfI think I like the possibility of having PoE ports for videocameras in the future, and why not, some other IoT device, so I'm also evaluating PoE switches.
-
@jt40 said in Home Network Design:
Thanks everyone so far, but this thread will be a bit in this way, I'll keep asking questions :D until I don't saturate your patience :D
I came across Cisco Meraki, I was excited for the price, support and performance, but guess what, this is what you find in the end of this thread: https://forum.netgate.com/topic/160537/pfsense-cisco-switch-ms220-24p/18
A Meraki switch is cloud managed and needs to be able to see the internet for it to work....Ugh indeed. Also cloud-managed devices offer manufacturers more opportunities to spy your network, and hackers more routes in. I chose a Cisco CBS350 several months ago, and have been pleased so far. It's not cheap (~$300 for the 16 port model) but it's full-featured (yes, all the VLAN stuff you're likely to need) and doesn't need any WAN connectivity (or periodic license renewals!) to work. For any switch, but especially more expensive ones, beware fake hardware or grey-market items.