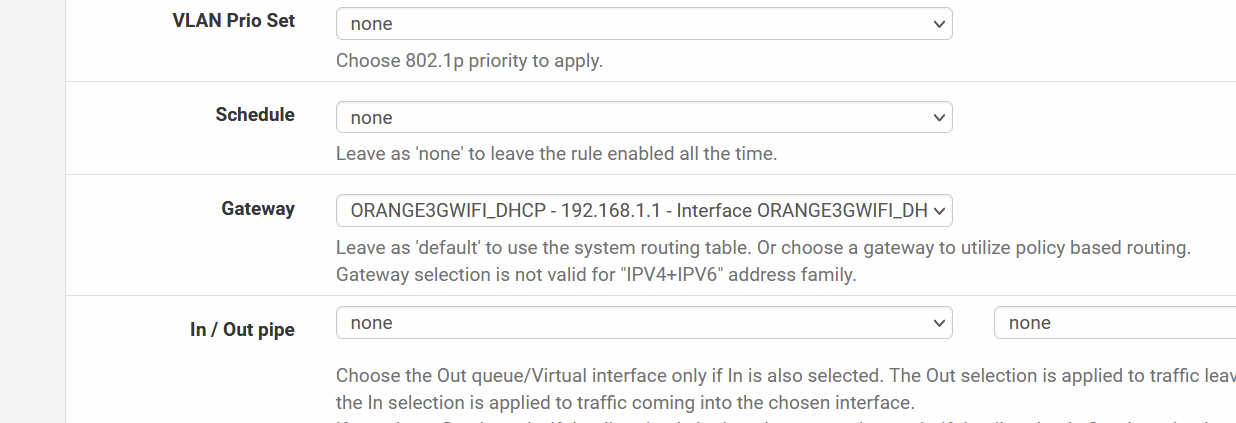
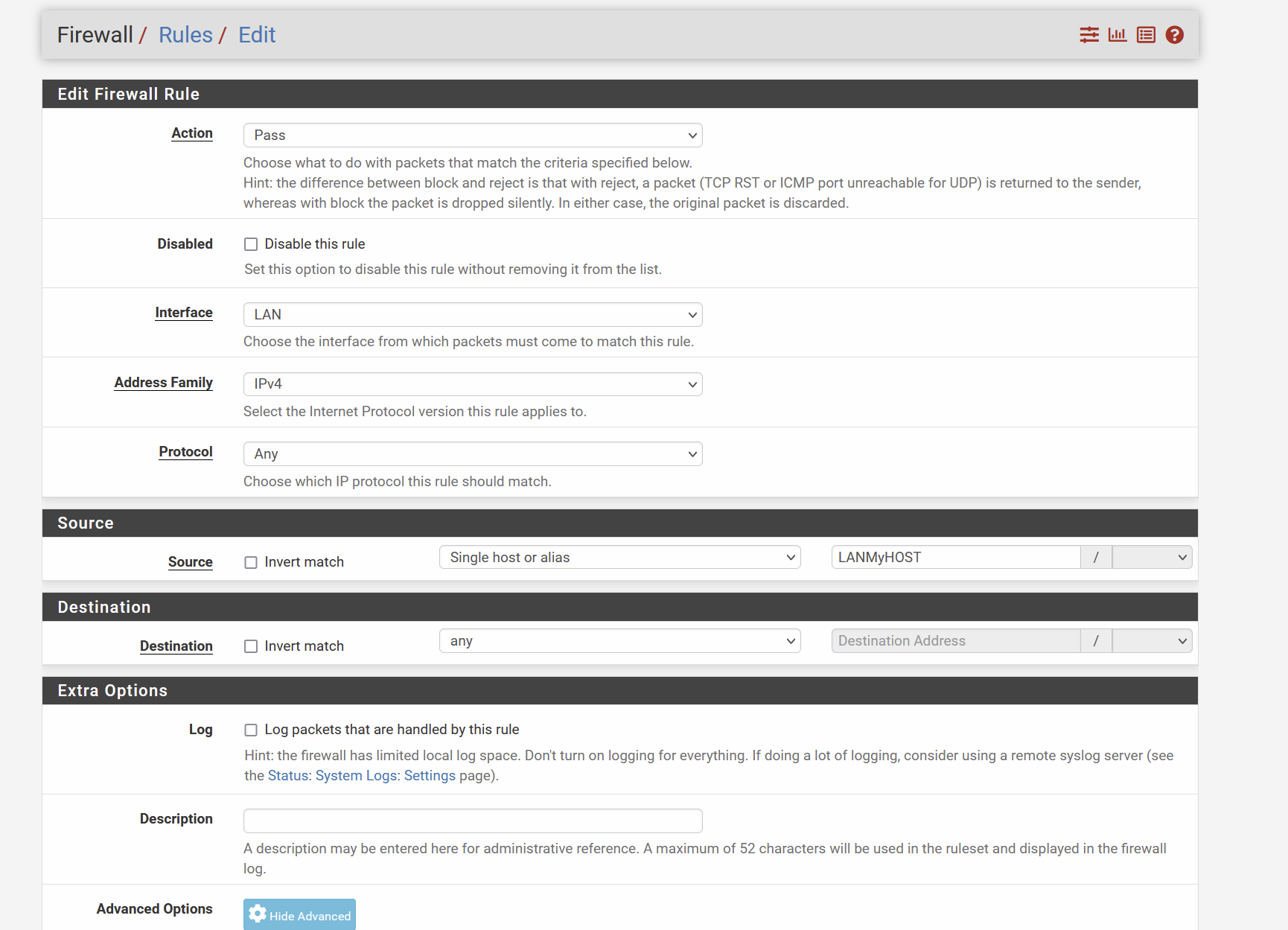
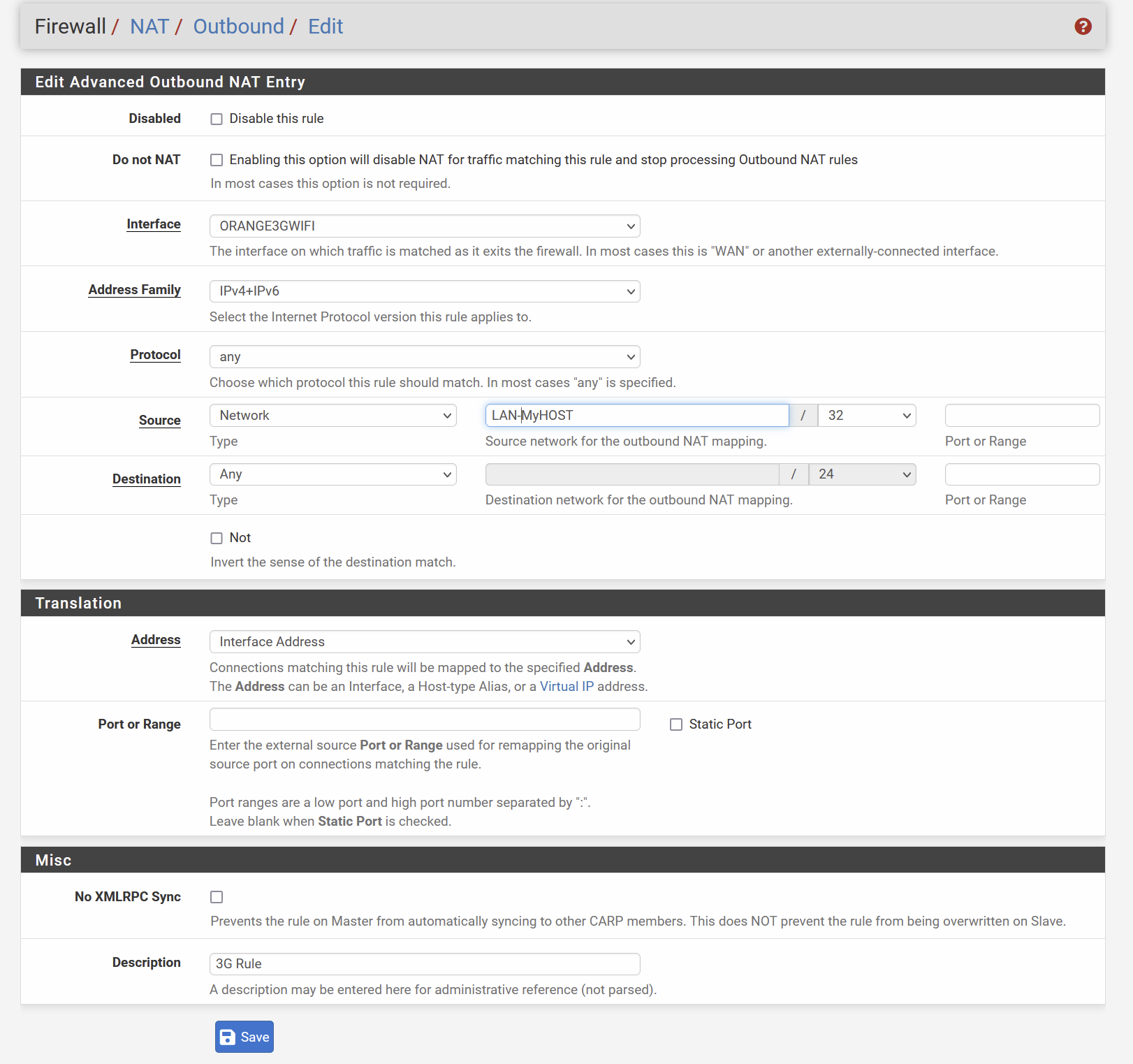
Send Traffic from 1 host to a specific GW
-
@johnpoz
Cleaned all Outbound rules. I did not created anything, it was automatically generated.
I simplified my architecture , it now fully reflect the schema I posted before ( LAN is and only is 172.16.25.0/24 )
So, here is my outbound rules set now :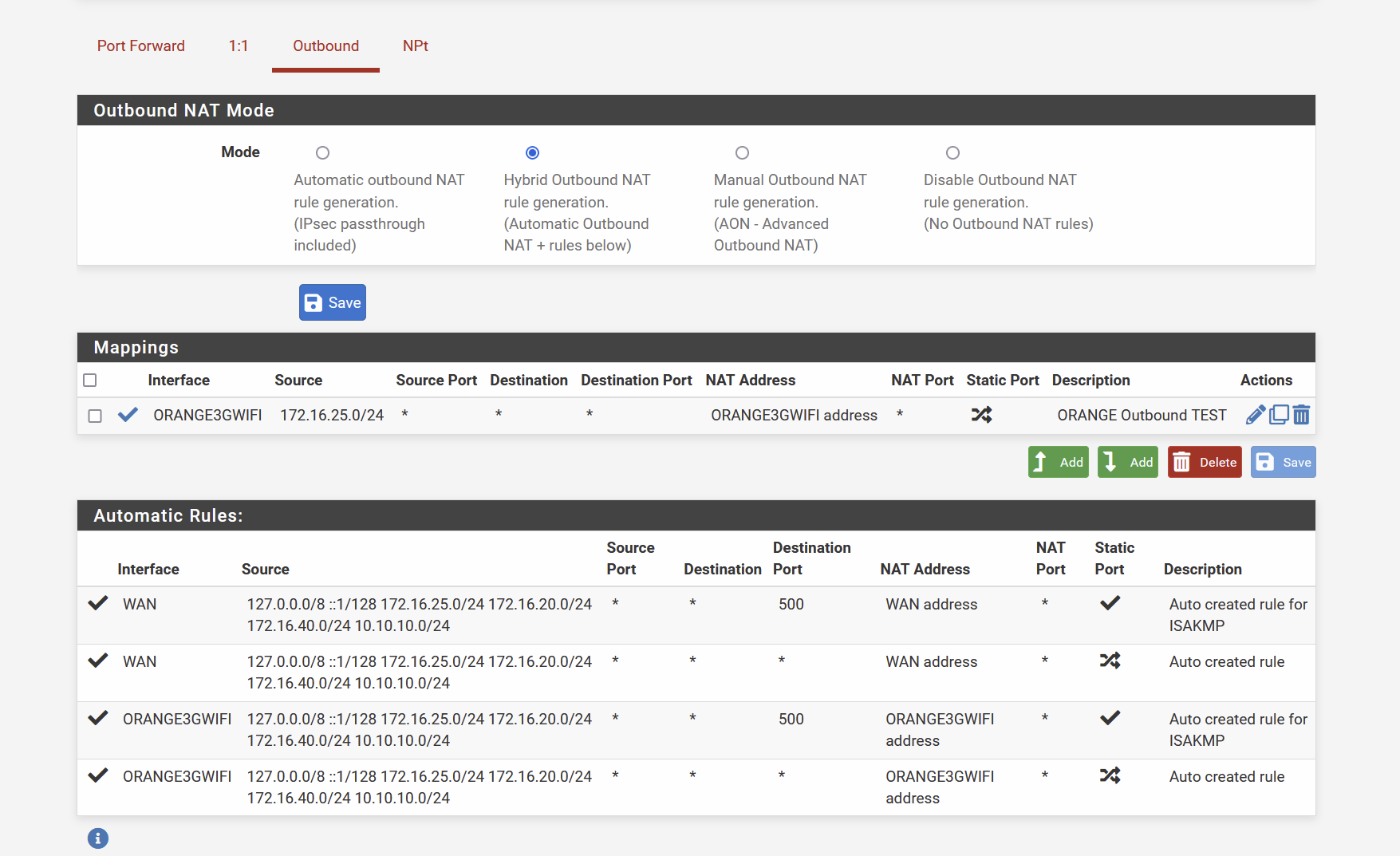
Lan Rules:
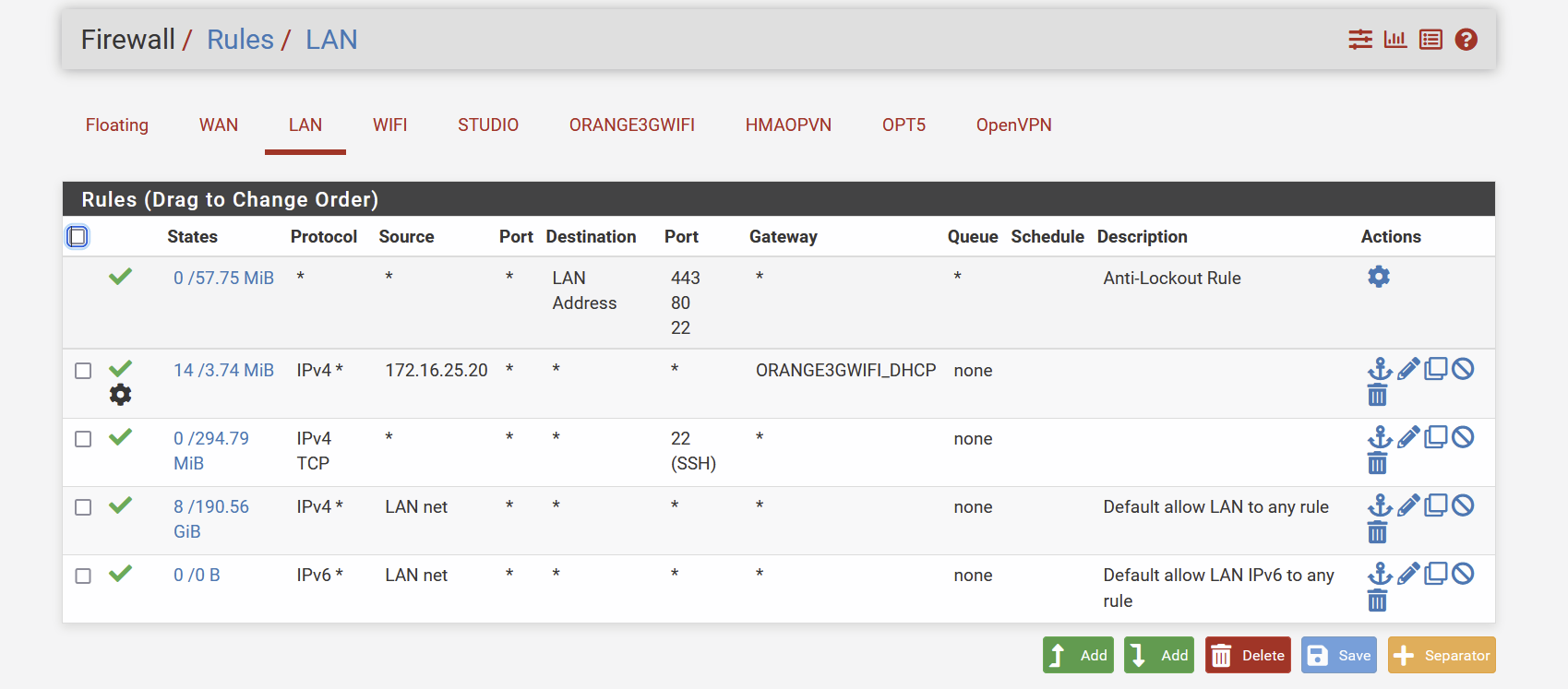
-
@smalldragoon well clearly there is listed at 14 different states being sent out that policy rule.. So pfsense is routing traffic like you told it too.
States are being created.. And from your sniff traffic is being sent out..
And again with your outbound nat being created auto, there is no need for hybrid.. Hybrid are used when doing say vpn.. And no gateway setup in the actual interface that tells pfsense is a "wan" connection and therefore create the outbound nats.
-
@johnpoz said in Send Traffic from 1 host to a specific GW:
And again with your outbound nat being created auto, there is no need for hybrid.. Hybrid are used when doing say vpn.. And no gateway setup in the actual interface that tells pfsense is a "wan" connection and therefore create the outbound nats.
sorry, my bad english . you mean then I can stick back to auto and remove the 1st mapping I did , like this ?
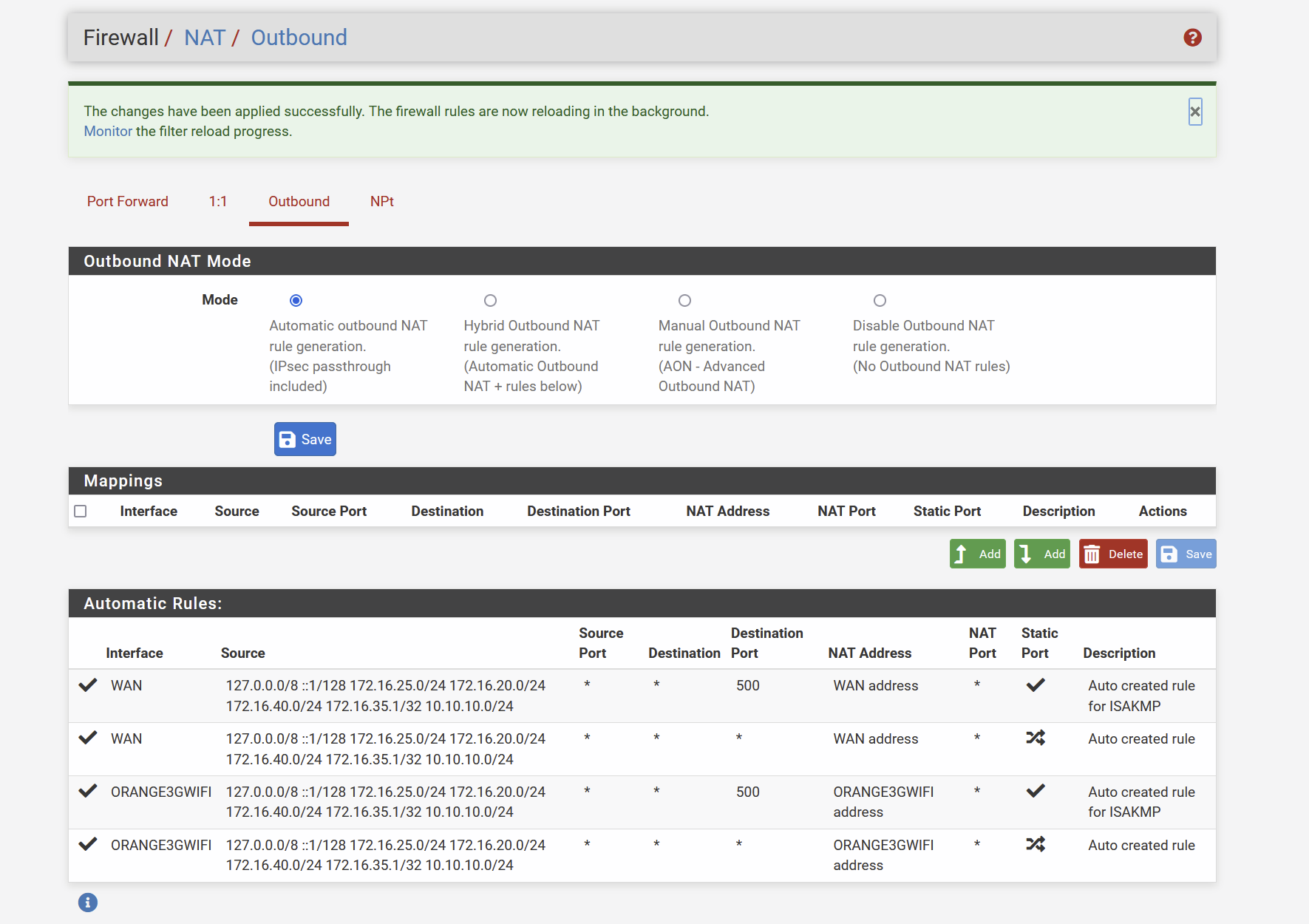
?
-
@smalldragoon Yeah see in your auto, where it lists your 3g interface.. So there is no need for hybrid mappings.
So what does your state table show for that interface.. From your latest rules posting - it showed 14 states and and almost 4MB of traffic..
From your sniff - clearly traffic was being sent out that gateway from the .21 address.. And there were some responses.. But maybe they were RST, seems like maybe some retrans because of no answers going on, etc.
You can do your sniff, exclude the icmp stuff - set the count to more than 100... Do some testing of connections, dns etc. And then download the pcap and view with say wireshark to get a better understanding of what is going on via the sniff. But from what have shown traffic is flowing out the gateway..
-
@johnpoz
Ok, thanks, will do , and keep you posted -
@smalldragoon said in Send Traffic from 1 host to a specific GW:
I set all the rules to any any accept to avoid any blocking :
3G - OrangeOrange is an Internet connection? You probably don't want to allow all inbound traffic on it, which would allow the Internet to log in to pfSense.
-
@steveits While agree with your for sure - he is clearly behind a nat with that 192.168.1.21 address - so unless they are port forwarding to him, or he has something setup on the isp device I don't see how any inbound could come in unsolicited.
-
@johnpoz said in Send Traffic from 1 host to a specific GW:
behind a nat with that 192.168.1.21
I missed that, never mind. Unless it's set as a DMZ.
The bigger picture point is probably that an inbound rule on an interface won't affect outbound traffic. -
@steveits said in Send Traffic from 1 host to a specific GW:
The bigger picture point is probably that an inbound rule on an interface won't affect outbound traffic.
Very true and good point..
-
@johnpoz
Hi All, I made many tests as suggested and still nothing .
Today, found that the IP allocated as "wan" to the 3G router is 10. X.Y.Z.
Is there anything in PFSense preventing RFC1918 and all non routable network restrictions ?
Found some doc , doesn't seem to be relevant, but I'm doublechecking ..
Thx -
@smalldragoon said in Send Traffic from 1 host to a specific GW:
anything in PFSense preventing RFC1918
Each interface has a "Block private networks and loopback addresses" checkbox but that would normally be for inbound traffic.