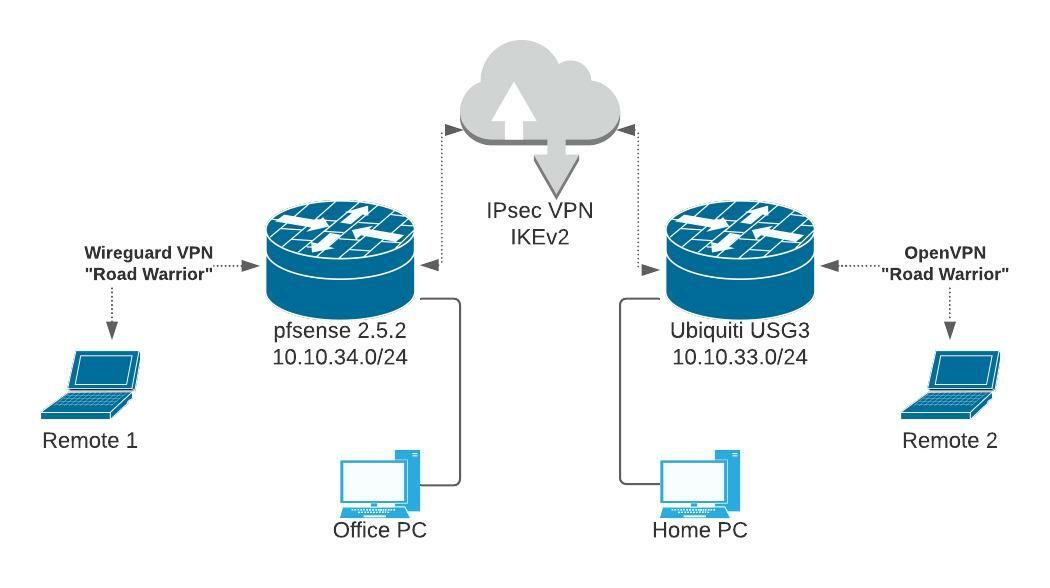
Muliple VPN configuration help
-
@jnewman33 I gave up trying to get IPsec working with USG3. The tunnel came up but would not route properly. I tried static routes and lots of other work arounds without success. I ended up replacing the USG3 with a Netgate 1100.
-
@jake Thanks for the reply. I had assumed that since the PCs were seeing both networks that the IPsec was working properly. Are you saying that minus the USG weirdness my laptops should be able to access all resources already given this configuration?
-
@jnewman33 Just so I understand. If a "road warrior" connects to the USG firewall they cannot access the pfSense network?
-
@jake That is correct. Also have the problem the other way around as well. I would be happy if I could just get the "road warrior" wireguard VPN to see the Ubiquiti side.
-
@jnewman33 I'm more familiar with OpenVPN but I'd assume you'd need to push the routes for the remote network to the wireguard client or if it's routed then setup the routes to be accessible to wireguard.
-
@jake Thanks for your continued help here. I may abandon the wireguard for now and switch to OpenVPN into pfsense for now. I was excited to the get the wireguard working but its unique interface is beyond what I can manage without someone like Christian's help.
-
@jake I have now created an OpenVPN connection for remote access to pfsense. I believe that now I need to push routes and maybe create rules in order to see the other side of my IPsec tunnel? Would you have any guidence here ?
-
I assume you are using policy based IPSec between the two sites?
If so you need to have policies in place to cover the traffic from the road warrior tunnel subnets in addition to the two local LANs.
Steve
-
Thanks for replying. I have simplified my diagram a bit:
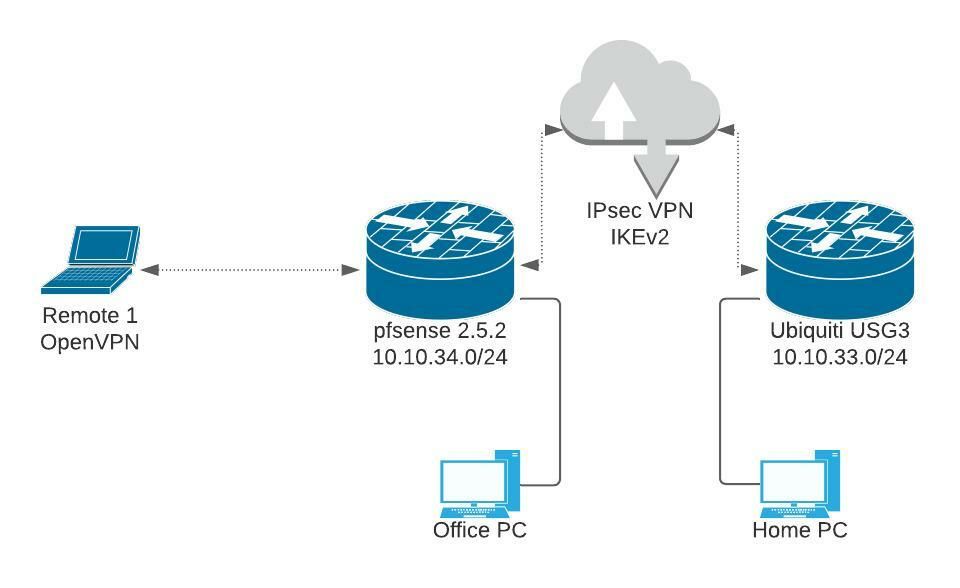
To simplify matters I am no just using OpenVPN into pfsense. That VPN works and is providing access to pfsense resources as expected.
I am assuming the site-to-site is policy based but I am confused as how to configure the addition of the OpenVPN subnet (10.10.50.0/24).
Appreciate any help you can provide.
-
OK so in order for OpenVPN users to access resources in the 10.10.33.0/24 subnet the IPSec tunnel needs to have a Phase2 policy configured for 10.10.20.0/24 to 10.10.33.0/24.
You probably only have one P2 policy defined and it will be for 10.10.34.0/24 to 10.10.33.0/24 so traffic from the OpenVPN is not carried.
What is you current IPSec config?
Steve
-
Thanks for your help here. I actually had created a second P2 but had created it backwards. Fixed that up and now all works.
Thanks again,
James