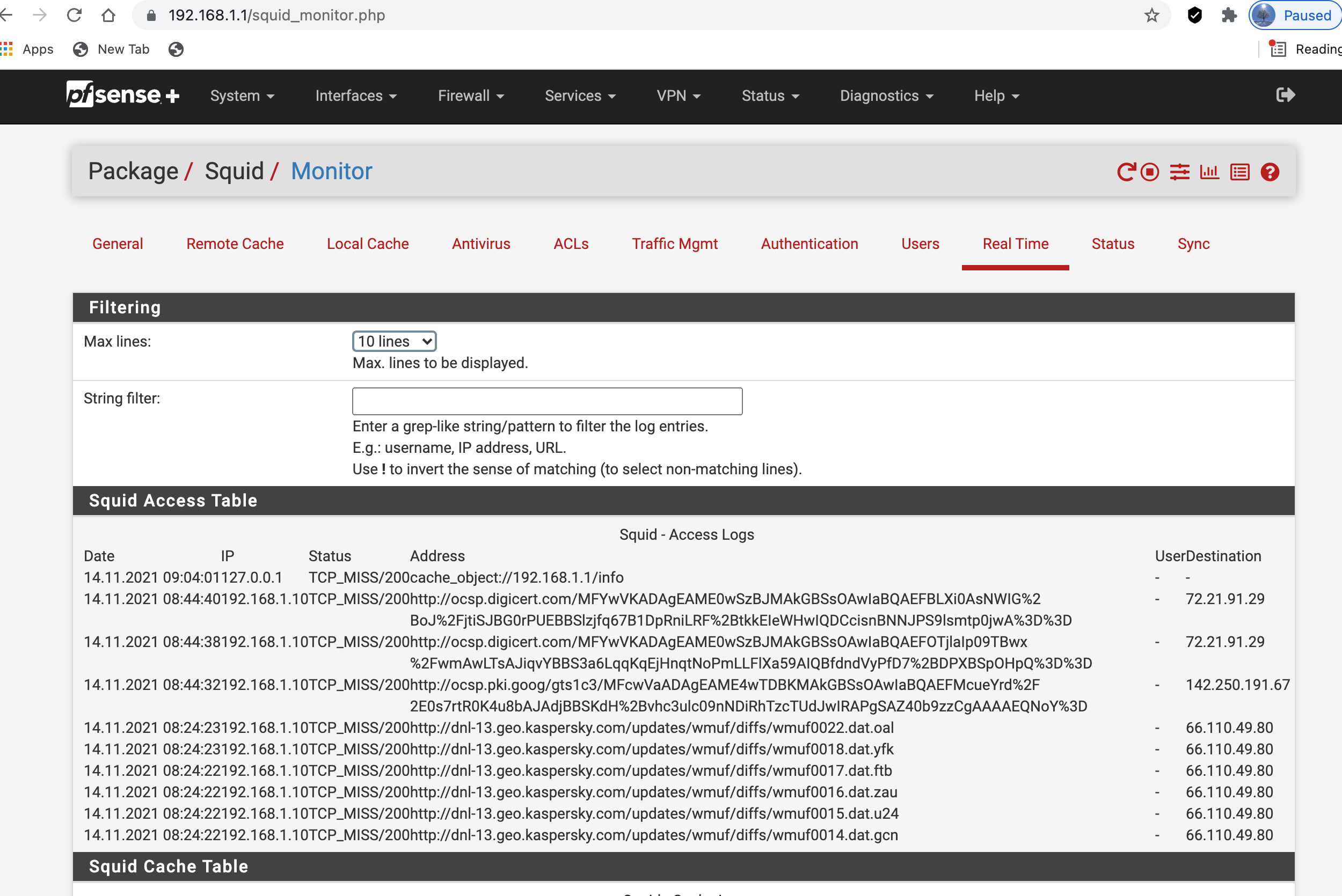
Netgate 2100 and any any rules questions
-
@steveits so if I was a business I could not load something like Gmail approved email server ID or Yahoo etc? PaloAlto has app-Id and content-id but nothing for email approved server Id. It would have to be done by hand.
-
You can add an alias there with a list of destinations if you wish. But you would need to find a list of IPs used by gmail and that's going to be difficult. That actual list is large and not static.
I also note you have added default block rules which is not necessary in pfSense as everything is blocked by default. Adding them your self can appear logical but you can end up blocking things that would normally be passed automatically. Also without logging enabled on those you will not see any blocked traffic in the firewall log.
Steve
-
@stephenw10
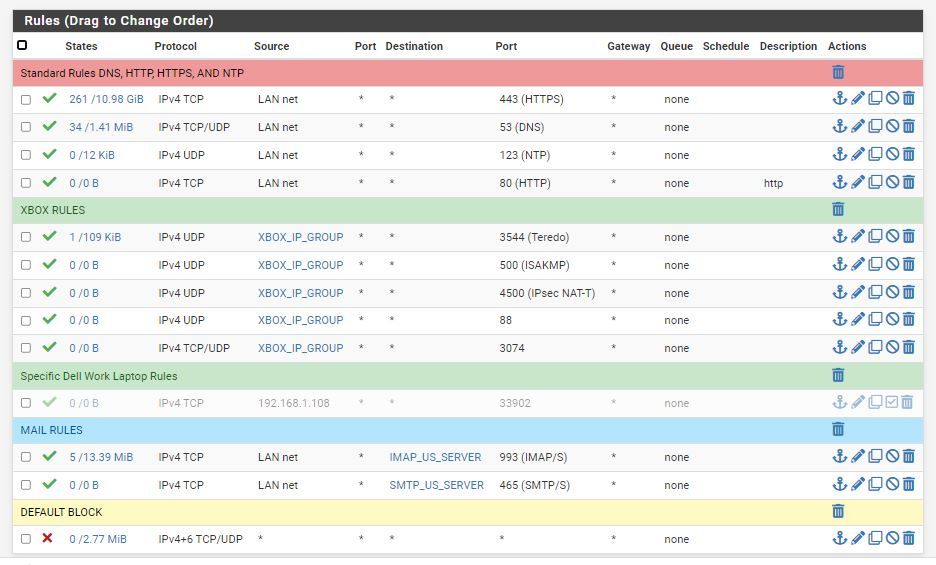
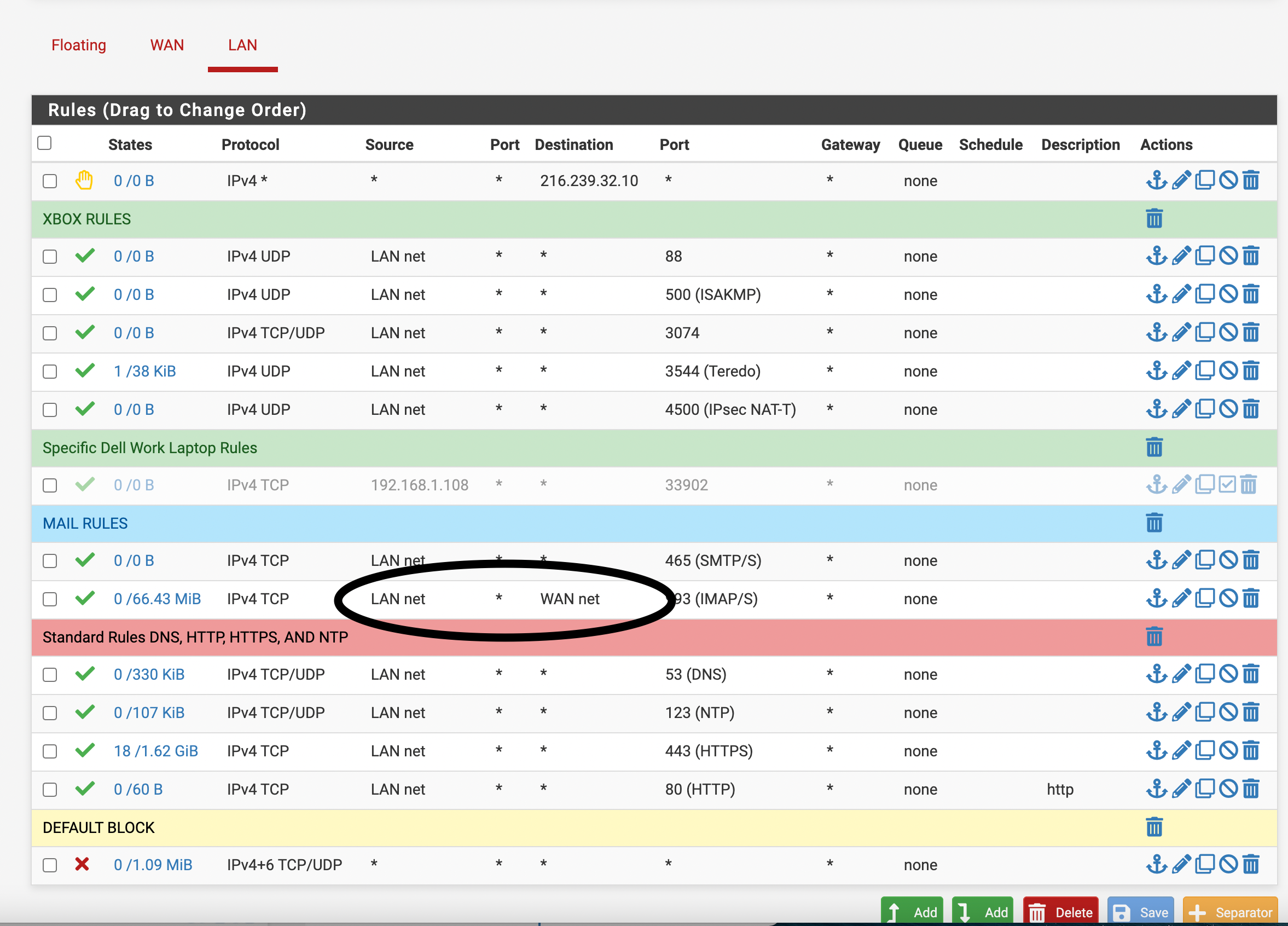
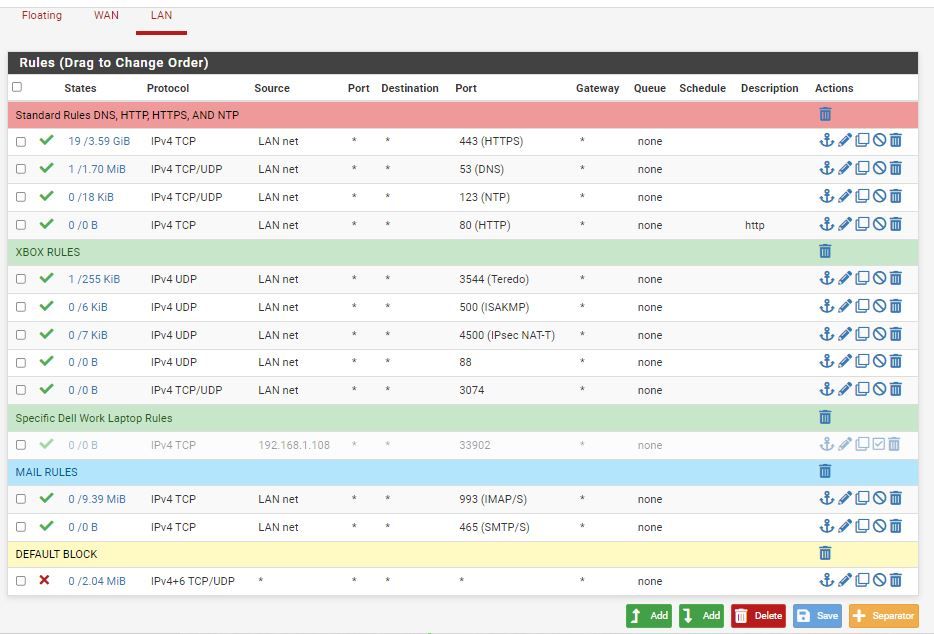
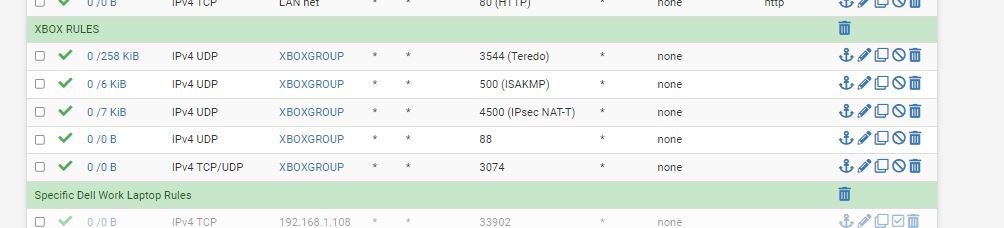
Thanks for the information,Our College Class taught to make a default block anything rule on the interfaces as it runs sequentially down and if you do not have a default block it will allow that traffic. My network I only want Xbox, internet, and email, nothing else that is why I have the default block rule.
-
@jonathanlee said in Netgate 2100 and any any rules questions:
do not have a default block it will allow that traffic.
There is a default block - just not shown in the gui.. Not sure what college class your taking, but I have worked on all the major players firewalls, palo, checkpoint, cisco, etc etc.. And I don't recall ever being default allow.. That would be a horrible default stance for a firewall.
https://docs.netgate.com/pfsense/en/latest/firewall/rule-methodology.html#default-deny-rule
https://docs.netgate.com/pfsense/en/latest/firewall/best-practices.html#firewall-bp-default-deny -
@jonathanlee said in Netgate 2100 and any any rules questions:
Our College Class taught to make a default block anything rule
Yup, that's not required in pfSense. I don't know what firewall you were using for that class.
pf itself, the filter used by pfSense, is pass by default but the default ruleset adds block all rules already.
Quite a few users add a block rule just to make the ruleset easier to read. You just need to be aware that doing so can break the default rules that you don't see altering the expected behaviour.
Steve
-
@stephenw10
Hello thanks again for the reply.I am taking a specific higher education advanced firewall college credited class. I will continue to leave that specific rule in place. When logging is enabled on this rule it does block traffic I do not want running on my network.
-
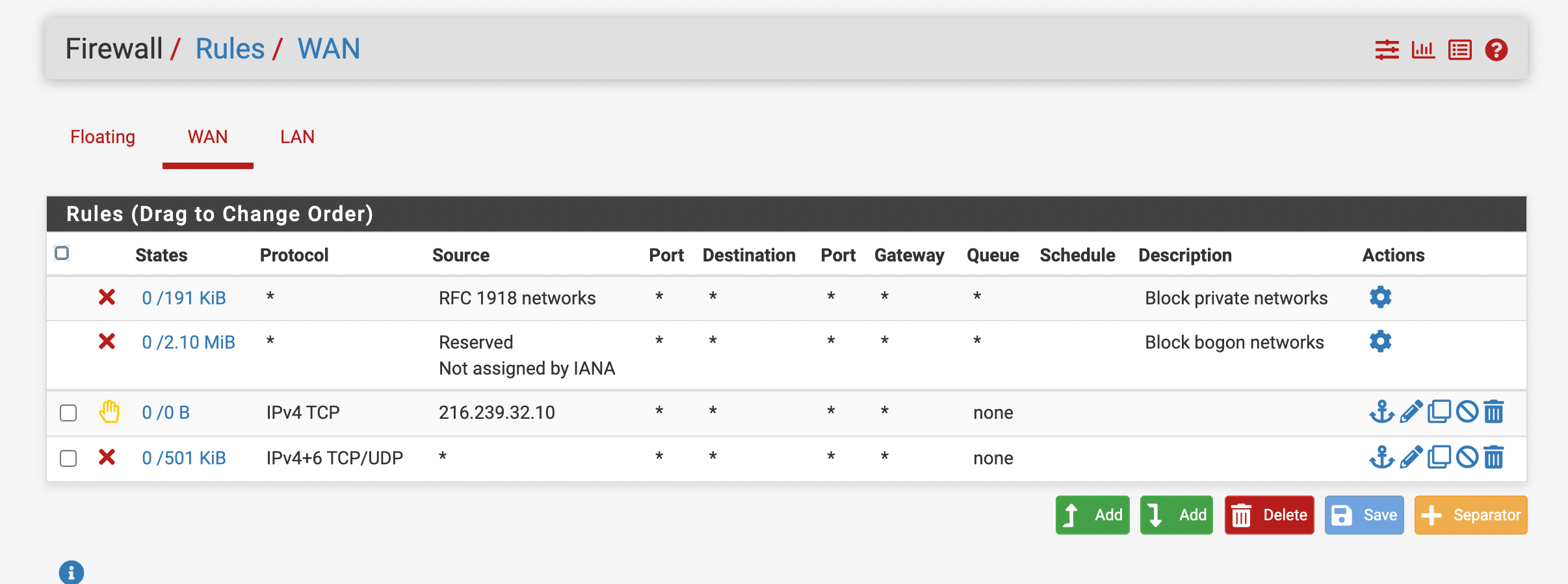
@stephenw10 Thanks for the reply, How can you just set the outside rule to WAN, doing so blocks all mail, however when it is set to allow anything out it works. I just want it to say anything is allowed for a specific port out the WAN or Gateway, and try not to just not state rule needed, source, and destination only "*" I want it set to WAN interface, or WAN network, or only allow out to WAN.
-
@johnpoz "Generally, firewalls should block all inbound and outbound traffic that has not been expressly permitted by the firewall policy—traffic that is not needed by the organization. This practice, known as deny by default, decreases the risk of attack and can also reduce the volume of traffic carried on the organization’s networks. Because of the dynamic nature of hosts, networks, protocols, and applications, deny by default is a more secure approach than permitting all traffic that is not explicitly forbidden" (NIST Special Publication 800-41r1).
For me If it is not specifically built into the firewall I am going to block it with a default block anything at the end of the Access control lists here is my reasons why and the reasons the class is taught for students to add such rules at the end of access control lists or ACLs.
"Firewall rulesets should be as specific as possible with regards to the network traffic they control. To create a ruleset involves determining what types of traffic are required, including protocols the firewall may need to use for management purposes. The details of creating rulesets vary widely by type of firewall and specific products, but many firewalls can have their performance improved by optimizing firewall rulesets. For example, some firewalls check traffic against rules in a sequential manner until a match is found; for these firewalls, rules that have the highest chance of matching traffic patterns should be placed at the top of the list wherever possible" (NIST 800-41r1).
"Organizations should only permit outbound traffic that uses the source IP addresses in use by the organization—a process that helps block traffic with spoofed addresses from leaking onto other networks. Spoofed addresses can be caused by malicious events such as malware infections or compromised hosts being used to launch attacks, or by inadvertent misconfigurations" (NIST 800-41r1).
"Create a firewall policy that specifies how firewalls should handle inbound and outbound network traffic."
-
I have reordered the rules per the document for the rules that are most often used at the top so it does not have to check the other rules before reaching the HTTPS for example.
-
@jonathanlee said in Netgate 2100 and any any rules questions:
(NIST Special Publication 800-41r1).
Dude that is funny.. I have been doing firewall, most likely before you were born ;) hehehe
Really before statefull firewalls, back in the day of just old packet filters... hehehehe But sure ok feel free to quote docs ;)
I was just pointing out that pretty much every firewall on the market is default deny, no need to put in the rule. And from your rules there all your doing is hiding blocked traffic from your log for tcp and udp.. Since your not logging that rule.. What about all the other protocols - that deny there at the end should be logging and any rule..
Also btw NTP, doesn't use TCP - so why have it allowed? ;)
And there are many sites that do can do QUIC, HTTP/3 which is over UDP.. Guess you want to block that traffic and not log it ;)
From a security point of view, allowing those tunnel protocols for your XBOX -- horrible horrible idea.. Once you allow such a tunnel or vpn out like that - all of your firewall rules and blocking go out the window.. Your allowing anything on the lan net to do that, not just some specific xbox..
-
Realistically you cannot define the destination for a lot of those rules, it has to be 'any external IP'.
But you can set that by defining an alias with your own local subnets in it and then using the inverse of that. Like:
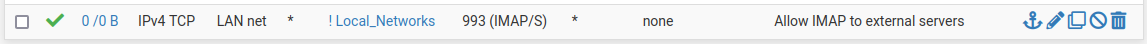
and
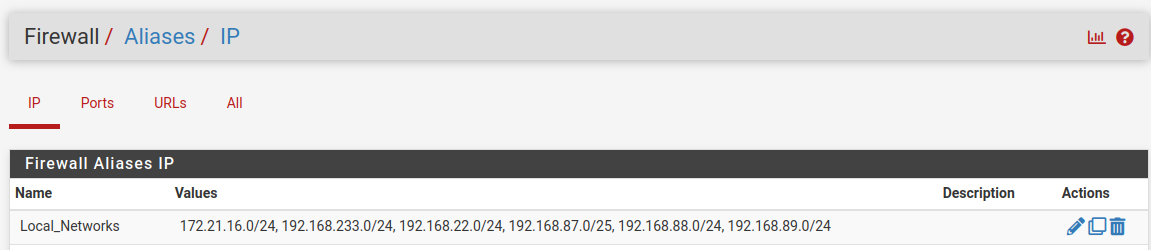
Steve
-
@johnpoz Thanks for the information on HTTPS/3 that is new to me. I was born years ago and have worked on IT equipment for over 15 combined years, all over the USA all the way up to the internet backbone level. Like you I have also worked on glorified packet filters back in the day, all Command Line Interface (CLI) based with no GUI.
I did have logging turned on for this rule, however if I am not looking at it I turned it off to have less resource use.
Over the years one can say we learned that all protocols and the rules that are in place for them need to follow some official government guidelines. Again we all can agree with that, or why have protocols at all? What is a protocols but a set of rules.
As for new HTTPS/3 "This is new to me thanks for sharing." Thank you for sharing. Why do you think this was made? Maybe because of new GDPR laws? Or something else?
Companies always have created new cutting protocols to make something work better or sometimes to just avoid detection. However, they should always train students on it before just using it or doing a blanket deployment of use.
That is why data center compliance systems can and will continue block them out when out of compliance. Rules that came out a couple years ago like GDPR and California Privacy Laws are never going away. They will continue to grow and expand for a safer internet. If protocols change to avoid detection or to avoid a system that can decrypt SSL over a enterprise network, one could say that it is no longer in "compliance" or following the official government guidelines. At that point more rules will be made and new fines put in place. "User Datagram Protocol" (UDP) does not have a three way handshake so it is harder to work with on for Nmap scans and things like that we know that and harder to detect. Thanks again for the information, I will research this more.
HTTPS/3 and use of it with UDP that is new to me. Thanks for sharing, this is why I went back to school. We have got to keep learning update our skill sets.
Years ago it was only HTTP port 80 with 56 k Modems in the 90s. I remember my 8088 Dos 3.11 PC6300 system built by AT&T all green monochrome text. Today I can download from my phone over a audio connection full files to my Apple IIc it is amazing how fast it changed.
-
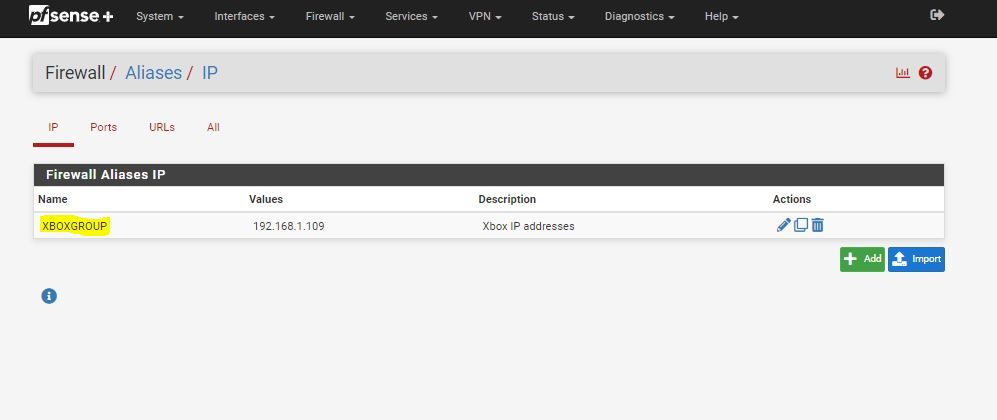
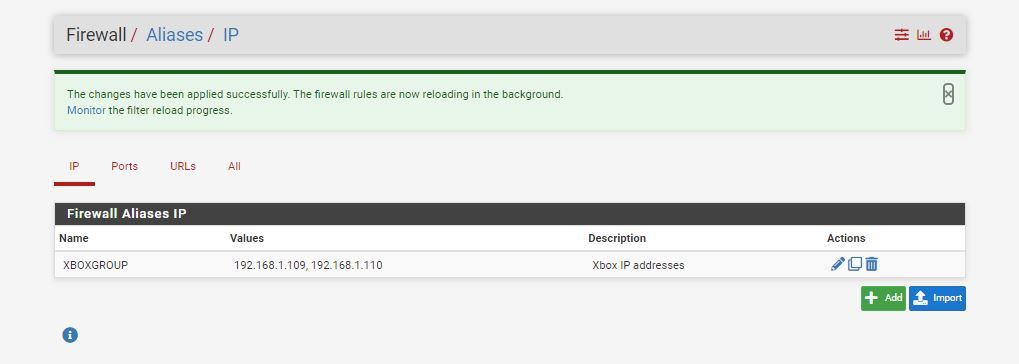
@johnpoz, I had to set to the specific IP address for the XBOX last week, I did not like the double rules, I wanted to be able to add 2 IP addresses to one rule for them The Xbox 360, and the One private Ip addresses only. Tunnels are a issue Yes.
-
-
-
It looks like NIST is already planning a course of action of HTTPS /3 QUIC over UDP
-
Thank you this is what I needed I have my email running with specific USA only Ip addresses for Gmail now.
sbcglobal.net that was passed to yahoo.com and after to currently from att.net through yahoo.com is another quest.
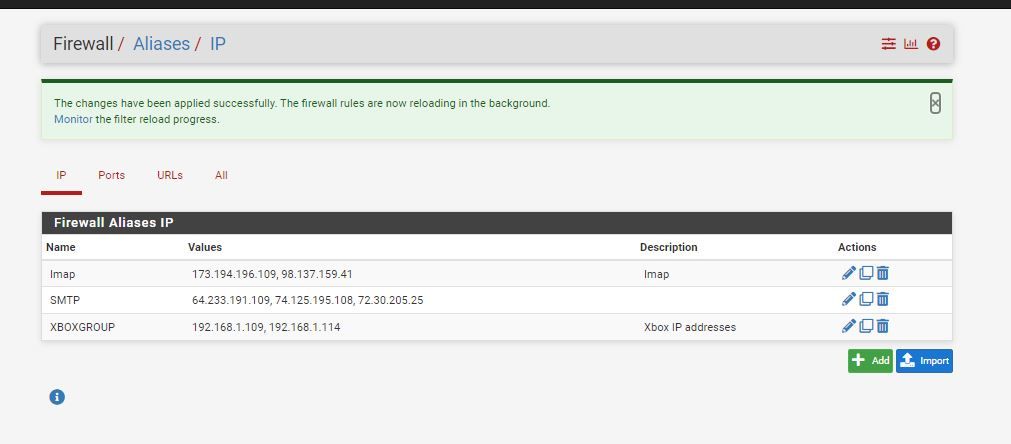
-
Thank you so much I generated a Aliases with the correct Ip addresses found with nslookup and it is now working. With all the FBI email issues in the news recently, I wanted to research a way to make a device only use a approved IP address for email on SMTP and IMAP. Your solution worked thank you again.
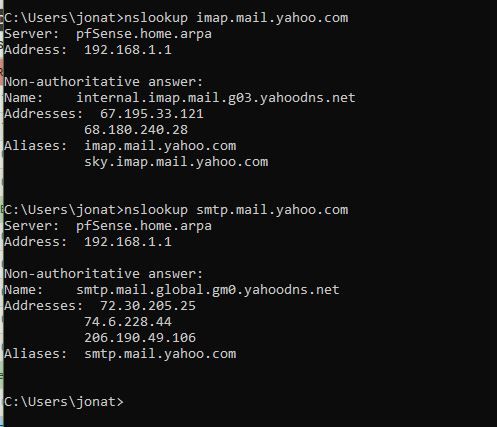
-
You can also just enter the FQFNs in the alias and pfSense will resolve them periodically for you.
Where that will fall down is for something that can resolve to a large number of IPs like mail.google.com. The alias will only ever contain the IP it resolved to at the time pfSense generated the ruleset. Anything that doesn't use pfSense for DNS, like something hardcoded for 8.8.8.8 for example, might get a different IP and then be blocked.
https://docs.netgate.com/pfsense/en/latest/firewall/aliases.html#using-hostnames-in-aliases
Steve
-
Thanks for everyone that helped me on this.
I have updated the ACLs and it is working perfectly all day. I had to add the main and backups for each email type and it worked. I just did not want tunnels on my network and to make the rules more specific. Each day I am trying to make it more secure.Thank you. This is solved.