Cloud pfSense+ with AP only possible - Minimal hardware setup?
-
Hello,
I would love to know if it's possible to utilize the pfSense+ cloud version, with a minimalistic on-premises hardware setup.
Like this:
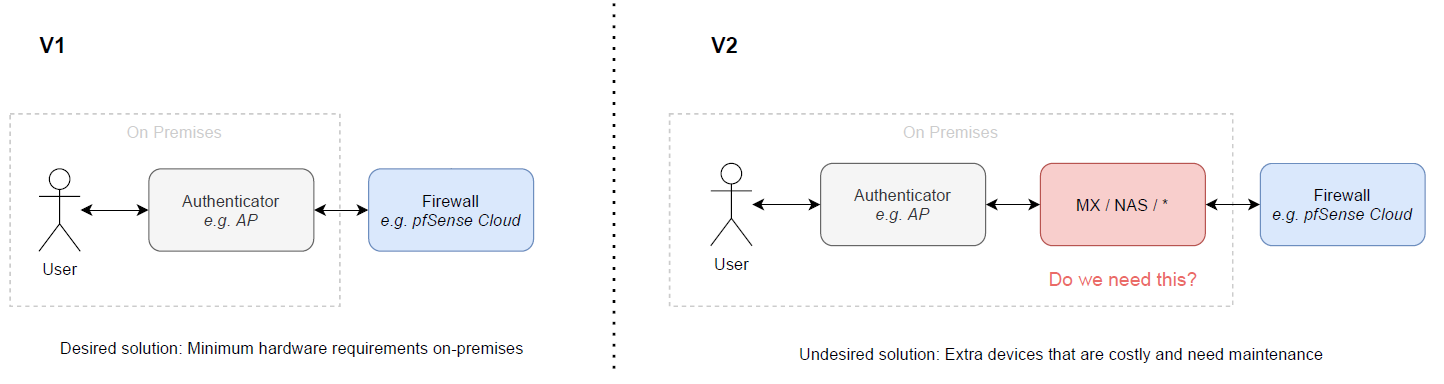
Ideally only Access Points should exist at a location, which then could directly connect/tunnel to pfSense+ (?). A pain point would be extra hardware like MX or other.
Is this possible? If not, what is the minimum requirement to connect to Cloud pfSense+ from a hardware point of view?
(For context, I am a web application developer, but not a network/hardware expert, so I found it pretty difficult to figure out how this actually could works.)
Thanks for your time!
-
@grmn-tech-co
What are you actually trying to do?-
Connect a single road warrior computer to a central server?
-
Connect branch offices to a central network?
-
Something else?
-
-
@grmn-tech-co Don't think you'll get what you want using pfSense.
I feel a bit reluctant to recommend other vendors hardware on the Hardware section of the forum, are you aware of the Aruba InstantOn AP11D:-
https://www.arubainstanton.com/products/access-points/access-point-11d/
https://www.youtube.com/watch?v=rlfEDFqACNM
See USE CASE #1: Small Clinic
https://www.arubainstanton.com/files/Aruba_Instant_On_Deployment_Guide.pdf
-
Mmm, that's not really a pfSense question. pfSense can do it's part in that diagram as long whatever you have on-site connects to it.
You could do it using an AP running OpenWRT for example. Just configure it to connect back to pfSense with OpenVPN, or WireGuard, and route all traffic over that.Steve
-
Hello, thanks for your replies so far! I've updated the diagram and added details as comments.
What we want to use pfSense+ for:
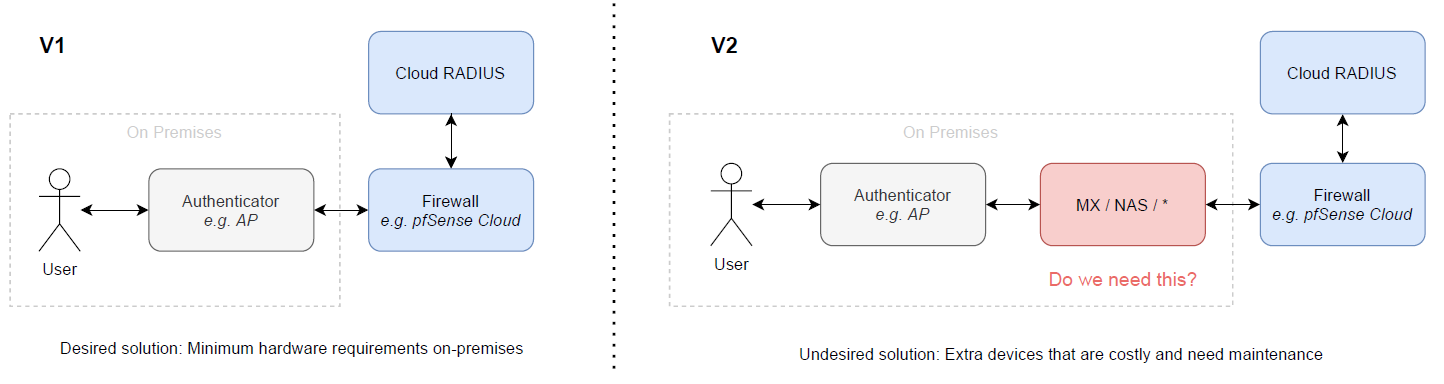
@Patch
Good you ask, missed it: We have a public user WiFi solution at various independent locations (It's not an corporate/office/branch environment). The client density can range from just a handful to thousands of users per location. Depending on needs, locations use different hardware vendor APs. Besides some staff in place, all guest users are unknown and must authenticate via a RADIUS server, which is behind pfSense+.@NogBadTheBad
Thank you for the suggestion though! The case studies are helpful and Instant On features look like an interesting addition.@stephenw10
These are some great keywords, I've look it up a bit! Seems this opens up new options.
Found out that some routers provide it, so it might not be the AP's job to do.
If you have another suggestion based on the updated comment details, I'm happy to hear it. Else I think your guys feedback have already been a great help!
-
@grmn-tech-co Why not implement an OpenVPN / IPsec road warrior solution using Radius as an authentication for the users.
-
It's not completely clear what you're trying to achieve here.
Obviously each remote location is going to require internet access so that means some sort of modem/router. That device could establish the VPN back to pfSense.
But lets assume you don't have access to that, it might be an ISP supplied router. Something else has to establish the VPN. Commercial APs don't usually have that capability but you can use, for example, an AP running OpenWRT to do that.
However that's not going to cut-it at a site with thousands of clients. You would need multiple APs and a VPN device capable of pushing significant bandwidth. More than the CPU in most APs is capable of.Steve
-
@NogBadTheBad Thanks for the suggestion, the Road Warrior concept looks interesting, I'll do some research here.
@stephenw10 The whole idea was focused around the question, "do we have to pay for a controller/MX, if an AP could do it?". Glad about your detailed answer! The DIY solution sounds not like something we want to maintain, and now I see that APs are limited here. So I think we prefer to use the suited hardware in the first place, without any custom builds.
No questions left, thank you all & Have a good new year :)