Need to allow access to specific corporate network IP from guest network
-
Ah, actually are you using pfSense for DNS on the guest network?
@JKnott's ruleset does not allow that so if you are you would need an extra rule for that.
If you're not then there would be no DNS override for the guests accessing the wiki so you would need something else, like NAT reflection.
Steve
-
@stephenw10 We're not exactly using pFsense for DNS. I'm using a Pihole that gets DNS from OpenDNS. The DNS resolution can be resolved to either external IP or internal IP depending on whether I leave the DNS server in Pihole alone, or I add an entry for our internal IP addresses and names.
Our main corporate LAN gets DNS from our domain controller. It was like that when I got here and works correctly.
So in PiHole I have local DNS entries like this:
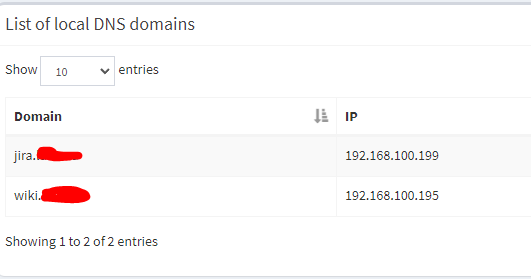
And they resolve properly as NSLOOKUP throws me the correct IP address from a DOS prompt on a laptop connected to guest.These are the rules in pFsense:
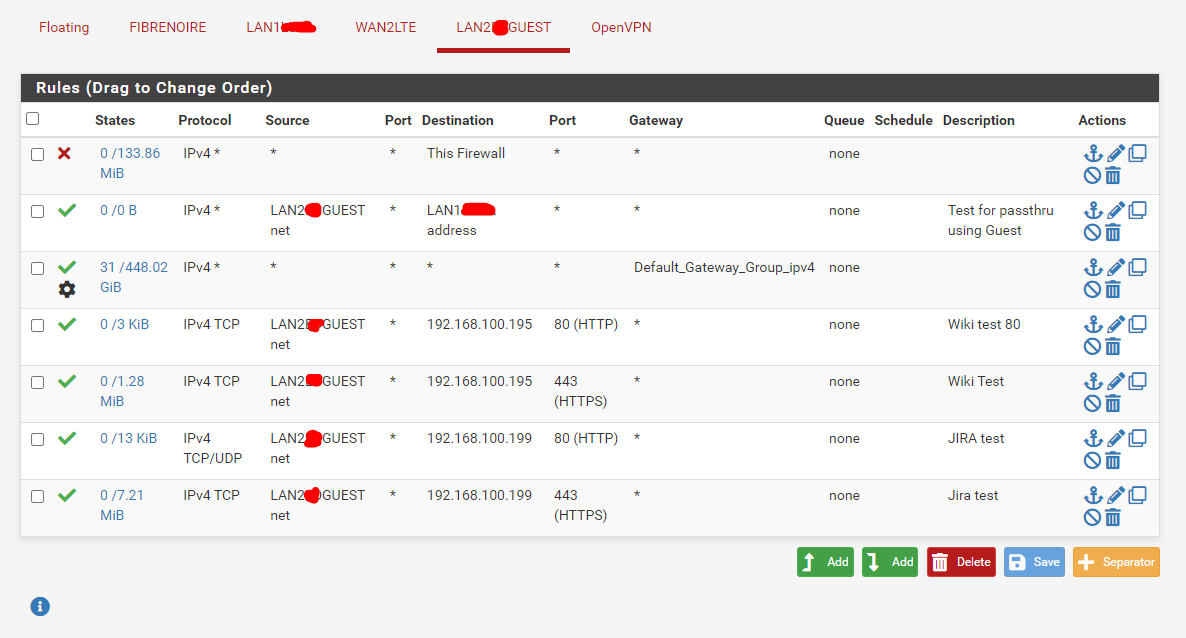
That first pass rule is supposed to open everything to the guest network. I know it worked a while back but as aforementioned I disabled it because we don't want anyone with our guest password to access our devices.
I tried enabling it now, but it's not working anymore, not sure why... I moved it up/down above/below the default gateway group to see if it made any difference but it didn't.
The default gateway group is so that both LAN and Guest can access Internet using the same gateway and switch over to the backup Internet service on WAN2LTE which is now an LTE access point. (used to be cable)
That part works properly, if I pull the plug on the Ethernet cable from FIBRENOIRE (our ISP) it automatically switches over after a few seconds. At that point, naturally the internal servers and VPN aren't accessible from outside but we can live with that temporarily while the primary ISP is restored. It gives us basic internet access so we can send/receive emails, basic stuff.
What's interesting is that my old pFsense had no problems doing the guest to local servers ONLY rules. When I switched it to new hardware, I backed up the config and restored on the new server with the new version of pFsense on it and everything else just worked. The four bottom PASS rules are the ones imported from the old instance and they don't work. They're enabled for testing now but I usually leave them disabled for security mostly because I don't know what they actually do - if anything.
I'm still scratching my head on this one...
-
The test rule needs to use destination LAN1net not address if it's intended to open it up completely.
The wiki and jira rules need to be above the default rule that is policy routing everything via a gateway group. That will get forced out of the WAN(s).
Steve
-
@stephenw10 Yes. That worked. I disabled the test rule after realizing the rookie mistake...
Wow. I didn't realize that placing the gateway group above the rules would route everything through the gateway group.
Thank you very much. That was awesome help.
-
No problem. It's very easy to overlook that.

-
@stephenw10 said in Need to allow access to specific corporate network IP from guest network:
@JKnott's ruleset does not allow that so if you are you would need an extra rule for that.
Yep, I point guests to Google DNS servers.
-
@colonnesel said in Need to allow access to specific corporate network IP from guest network:
I didn't realize that placing the gateway group above the rules would route everything through the gateway group.
What did you think would happen - rules are processed top down, first rule to trigger wins - no other rules are evaluated. So if rule triggers that forces traffic out a specific gateway, that is what will happen..
Here is docs on bypassing policy routing.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing -
Mmm, technically the negate rules are supposed to prevent that. But haven't done since.... 2.0.X something I think.

-
@stephenw10 said in Need to allow access to specific corporate network IP from guest network:
the negate rules are supposed to prevent that.
Is there some redmine about this? I don't recall ever reading anything in the docs where somehow pfsense would know not to route traffic out a gateway, if it had another route to that network.. as long as I can remember - but I don't recall doing any policy routing pre 2.x ;)
And if I did, I would of had a rule that allowed the traffic before forcing traffic out a gateway anyway.
-
I don't think there is because in fact I think the intention was to only negate policy routing for VPN connected networks after this:
https://redmine.pfsense.org/projects/pfsense/repository/1/revisions/b4227df690fb7a989ead9b3928ebaaaa34b495eb/diff/etc/inc/filter.incBut the description of it is still the original function:
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html#config-disablenegaterulesI'll open a bug....
https://redmine.pfsense.org/issues/12535
-
@johnpoz Yep. Rookie mistake. When I switched over the old cable backup Internet connection to the new LTE one I created a new gateway set and naïvely placed it above the other rules thinking that the PiHole DNS would override it.
I honestly have no idea why I would've thought that to be honest because it makes no sense.
Thank you.
-
@colonnesel said in Need to allow access to specific corporate network IP from guest network:
Rookie mistake
Not sure I would say that - it does come up quite a bit around here to be honest.. Quite often users policy routing and wondering why they can not get to some other vlan, etc.
I honestly have no idea why I would've thought that to be honest because it makes no sense.
Huh - if you understand how the rules are evaluated, and how policy routing works then its quite clear that if you forced traffic out a gateway that can not get to where you want to go.. you wouldn't be able to get there..
To be honest I would be disappointed if I had a rule that said use this gateway, and this was first in my rules, and it didn't send traffic down that gateway even if there was another route.. If that is how it "should" work per what @stephenw10 has mentioned. That really should be CLEARLY stated that it will work that way.. Which in 10 some years using pfsense, do not recall it ever doing that with any sort of negate rules, etc.
That is what can happen if the gateway your forcing traffic out is DOWN, and you have setting to not use that rule if gateway goes down, etc. But if the gateway is UP, and rule is before another rule - then it should force the traffic out the gateway.