Weird VPN server issue (pfSense/win2022server)
-
I am setting up a VPN server on a Win2022 server. My Win10 clients can log onto the VPN without problem from within the intranet, by addressing either the public URL or the IP address of the server. Obviously this not usefl, except that it proves that the VPN plumbing works well.
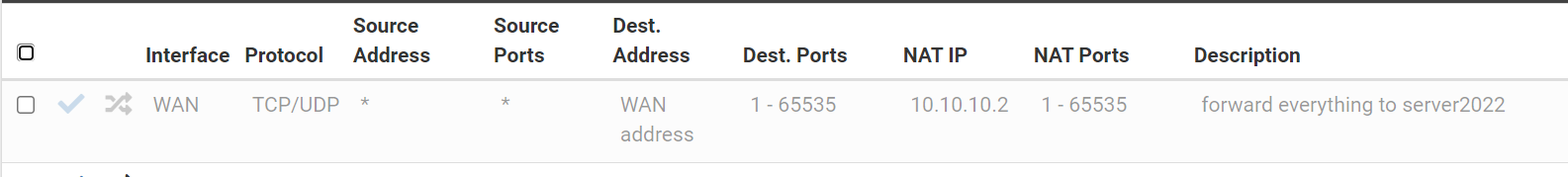
However, when trying to reach the VPN from outside, they fail. For testing purposes, I have directed all TCP/UDP traffic from WAN to the server (see rule, now inactive), but even that doesn't work. What might be the cause?
-
@aagaag said in Weird VPN server issue (pfSense/win2022server):
I am setting up a VPN server on a Win2022 server.
Which kind of VPN? Which protocols and ports does it need?
For testing purposes, I have directed all TCP/UDP traffic from WAN to the server (see rule, now inactive), but even that doesn't work. What might be the cause?
The shown NAT rule seems to be deactivated, as it's greyed out.
-
@viragomann, it's pretty standard Windows (see pic). For protocol, I like SSTP but I am not dogmatic. As for the ports, the rule I showed above should NAT everything, right? And yes, I have deactivated the rule because I didn't want to block the access to everything else for a long time. But the problem persisted also with the rule active.
-
@aagaag said in Weird VPN server issue (pfSense/win2022server):
As for the ports, the rule I showed above should NAT everything, right?
Every TCP and UDP packet. But possibly that is not enough for the VPN server.
You should better know, which kind of VPN is and what it needs.I guess, it's an IPSec. If so, you better search for "run an IPSec access server behind pfSense / firewall".
-
Yup, you might need ESP (or GRE). You would see that traffic blocked in the firewall logs from the test client IP though.
Try using a 1:1 NAT rule instead that will forward all protocols. If that works you can look at the traffic and make the required port forwards instead.Steve
-
@stephenw10 Thank you Steve, appreciated. I have never tried 1:1 NAT. Is it correct to do the following:
- set interface as WAN
- set protocol as IPv4
- set external IP as the public IP of the gateway
- set internal IP as the server that should receive all traffic
Because that's what I did, and I can still RDP all the internal servers, so obviously I am wrong...
-
The external IP should be the WAN public IP not the gateway.
If you have individual port forwards they will override a 1:1 NAT rule. So if you have forwards for RDP on individual ports those should continue to work.
Steve
-
@stephenw10 Dear Steve, you made my day! All I needed to do was to set a rule to pass GRE packets. And now everything works perfectly. I was already considering getting professional help (I am a medical doctor, not a network specialist), and your hint saved me a few hundreds bucks!!! Heartfelt thanks!
-
Good to hear!
You should be aware though that the fact you had to forward GRE implies the VPN type you're using is probably PPTP which is an outdated protocol and considered insecure.
You should check the VPN type in use to be sure.Steve