L2TP Site to Site between PFsense and Mikrotik
-
No errors on the pfSense side? Does it try to establish both ways?
That error looks like a pretty basic mismatch though. Can you show us the setting used at each end that generated it?
Steve
-
@stephenw10
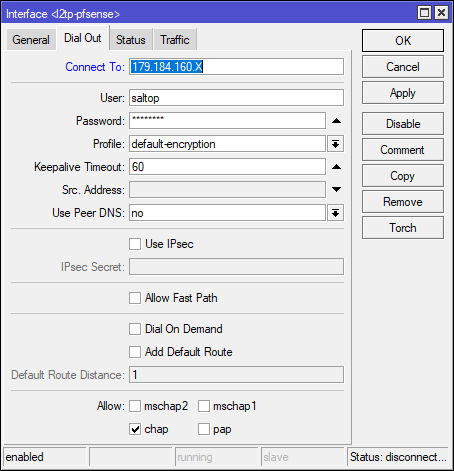
PFsense Config:
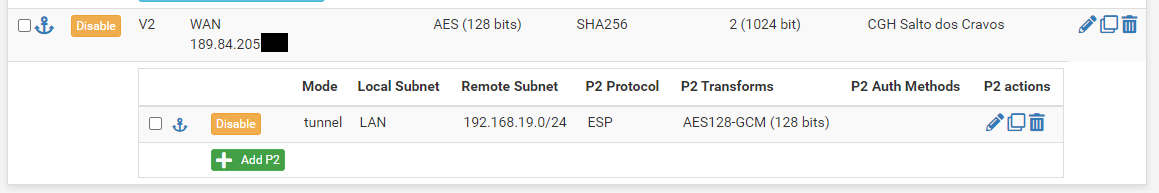
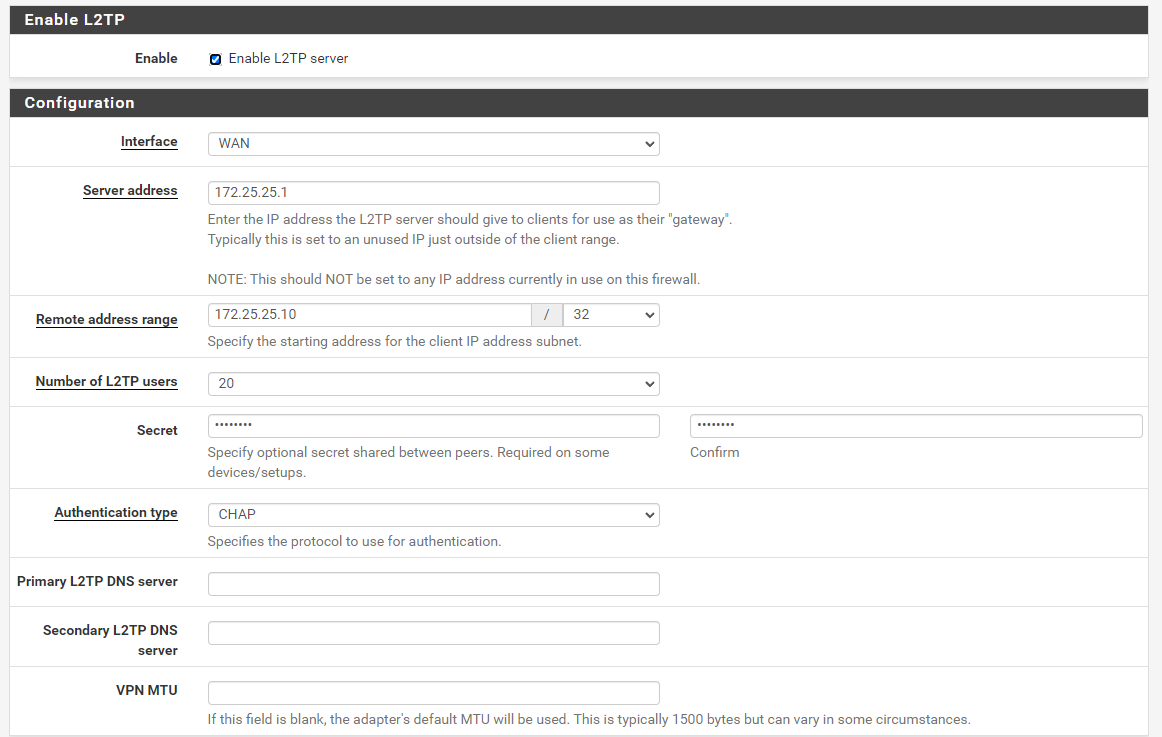
Mikrotik config:
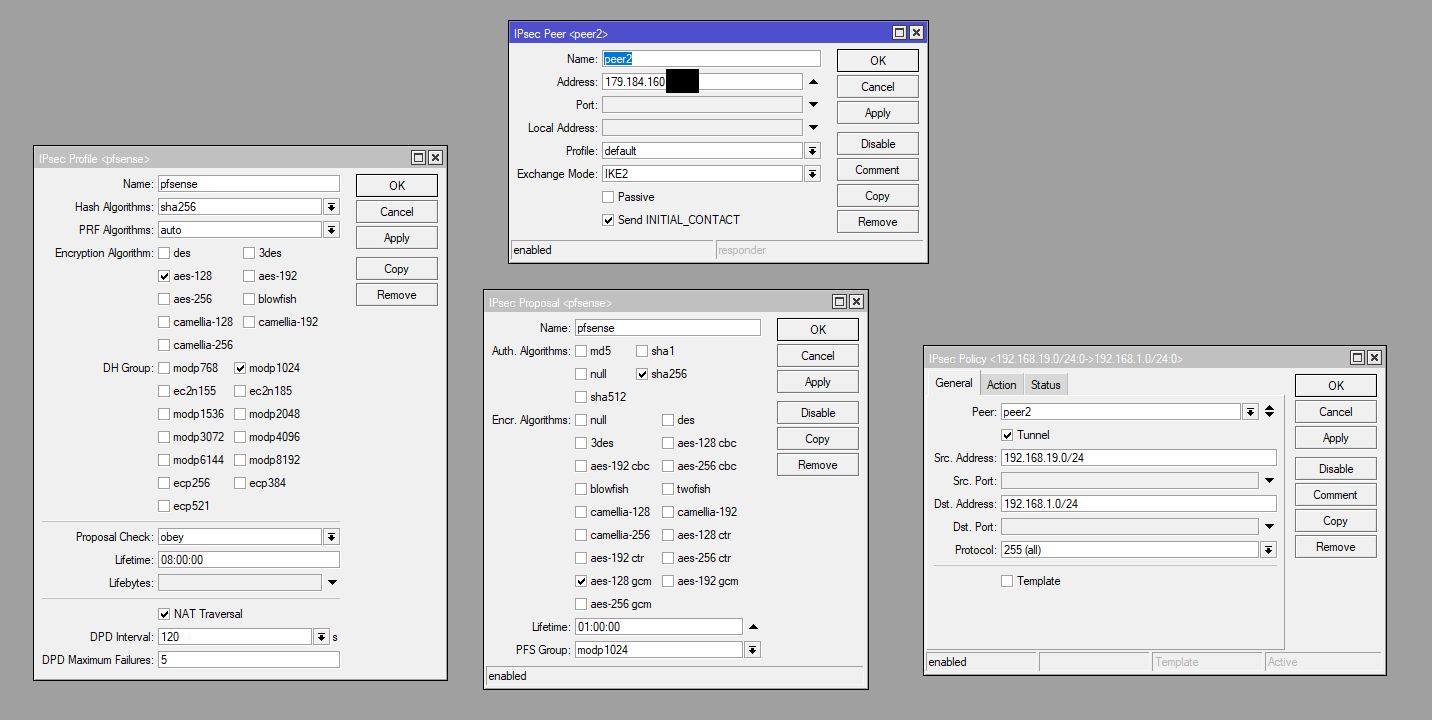
Pfsense log:
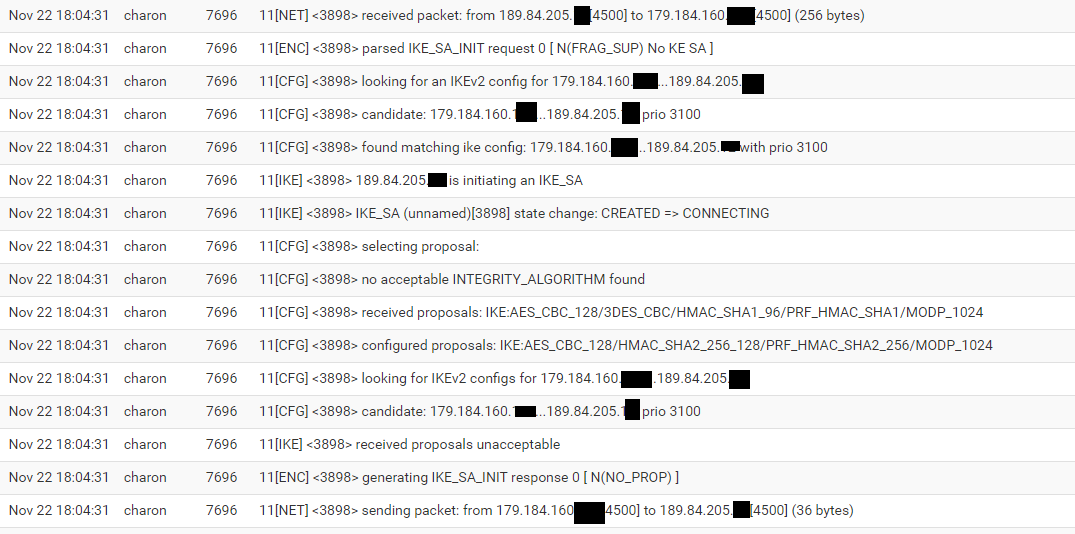
Mikrotik log:
The autentication method is Mutual PSK and I've already checked all the settings and apparently everything is correct.
-
Ok, the pSense log shows the Mikrotik is using the wrong hash value at P1 when it's initiating for some reason. The settings look correct on it though so maybe something is not applied?
You can see it's proposing SHA1. pfSense rejects it because it's set to SHA256.
The other thing that could be an issue is the identifier. You said you had the ISP forward ports to you? Does that mean you are behind NAT? If the identifier in pfSense would have to be set to match the external IP. We can't see that in the above screenshot.
Steve
-
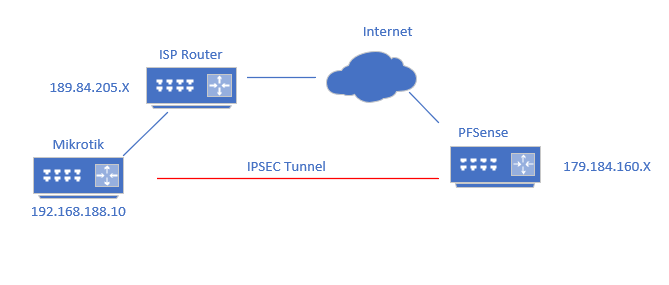
@stephenw10 yes the mikrotik is behind nat (in the first post there is an image with the network topology rsrs).
Basically this is the origin of everything (the existence of NAT). I need to be able to implement this VPN with this NAT enabled, the provider cannot give me a fixed IP
-
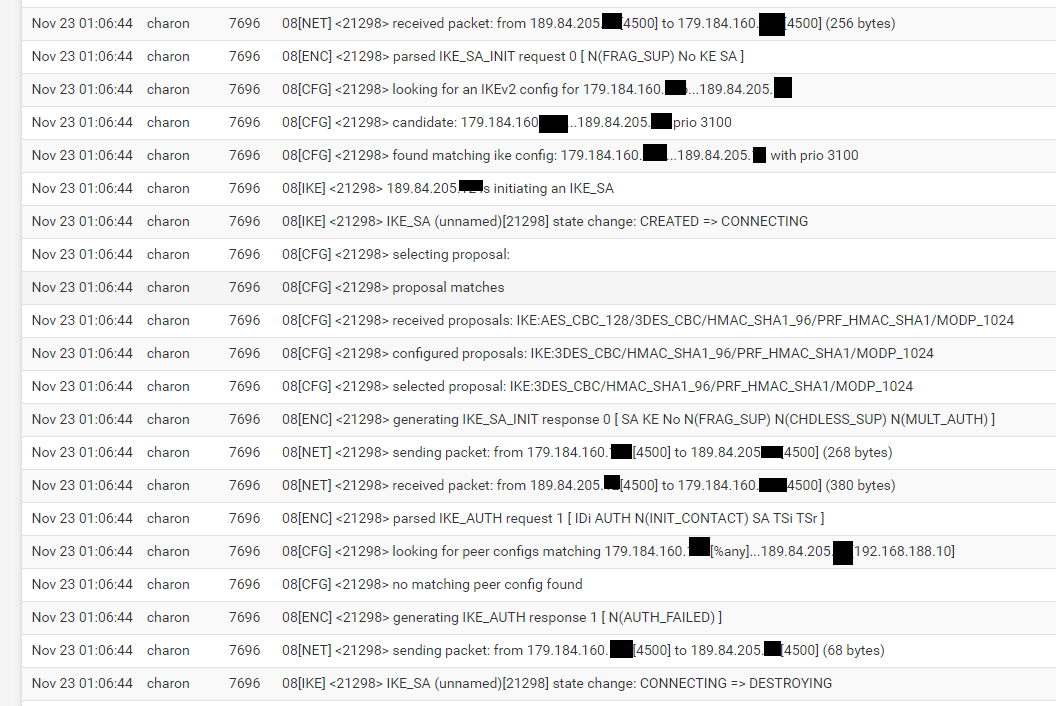
@felipefonsecabh i try to change the encryption and hash algorithms in pfsense to sha1 and 3des (to test the functioning), and the error changes:
-
Aha, OK now the proposal matches but the identifier is mismatched. The Mikcrotik is sending it's internal private IP as the identifier [192.168.188.10] and pfSense is expecting the external public IP.
You can change that so it matches at either end but I've no idea how to do it in RouterOS. So edit the Phase 1 config in pfSense and change the 'Peer Identifier' from 'Peer IP Address' to 'IP Address' then set it to 192.168.188.10.It will then match when the Mikrotik tries to establish. There may be other errors after that

Steve
-
@stephenw10 after change "Peer Identifier" as you suggested, works!
In mikrotik, i have to disable passive: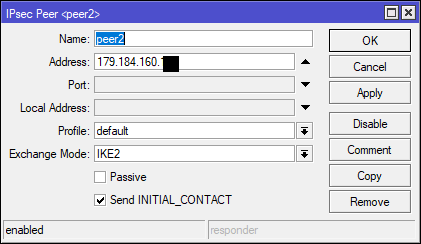
The strange thing is that the mikrotik does not send the proposal as configured, but works! Thanks a lot!
-
@felipefonsecabh the connection was estabilished but devices between sites doesn't ping. I created all firewall rules necessary.
-
@felipefonsecabh I restared my pfsense and all works. Thanks a lot!
-
Nice! Good result. Pure IPSec is waay better than trying to use L2TP over it.
Steve