Difficulty access the internet using my VLAN as an Guest Access Point
-
@jknott said in Difficulty access the internet using my VLAN as an Guest Access Point:
Some TP-Link gear has problems with VLANs. The TP-Link AP I used to use did. What model is yours.
Hi
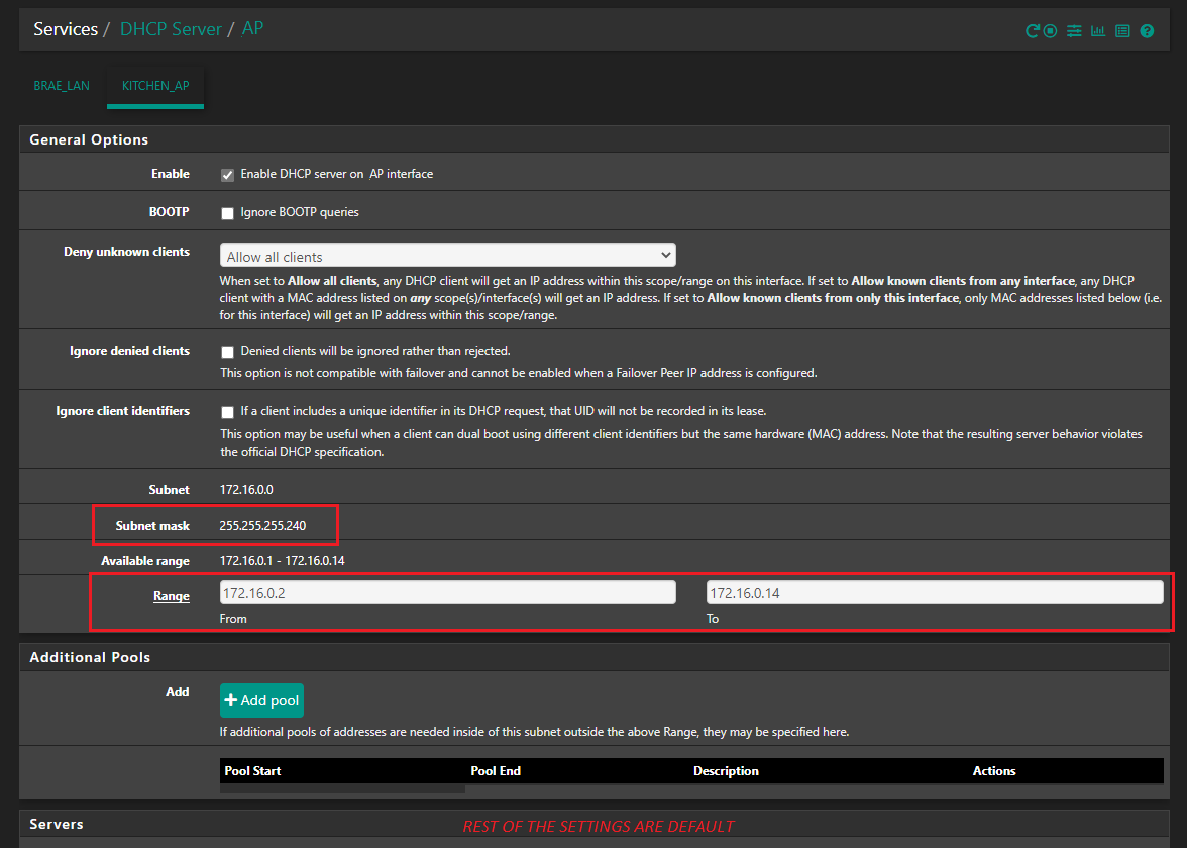
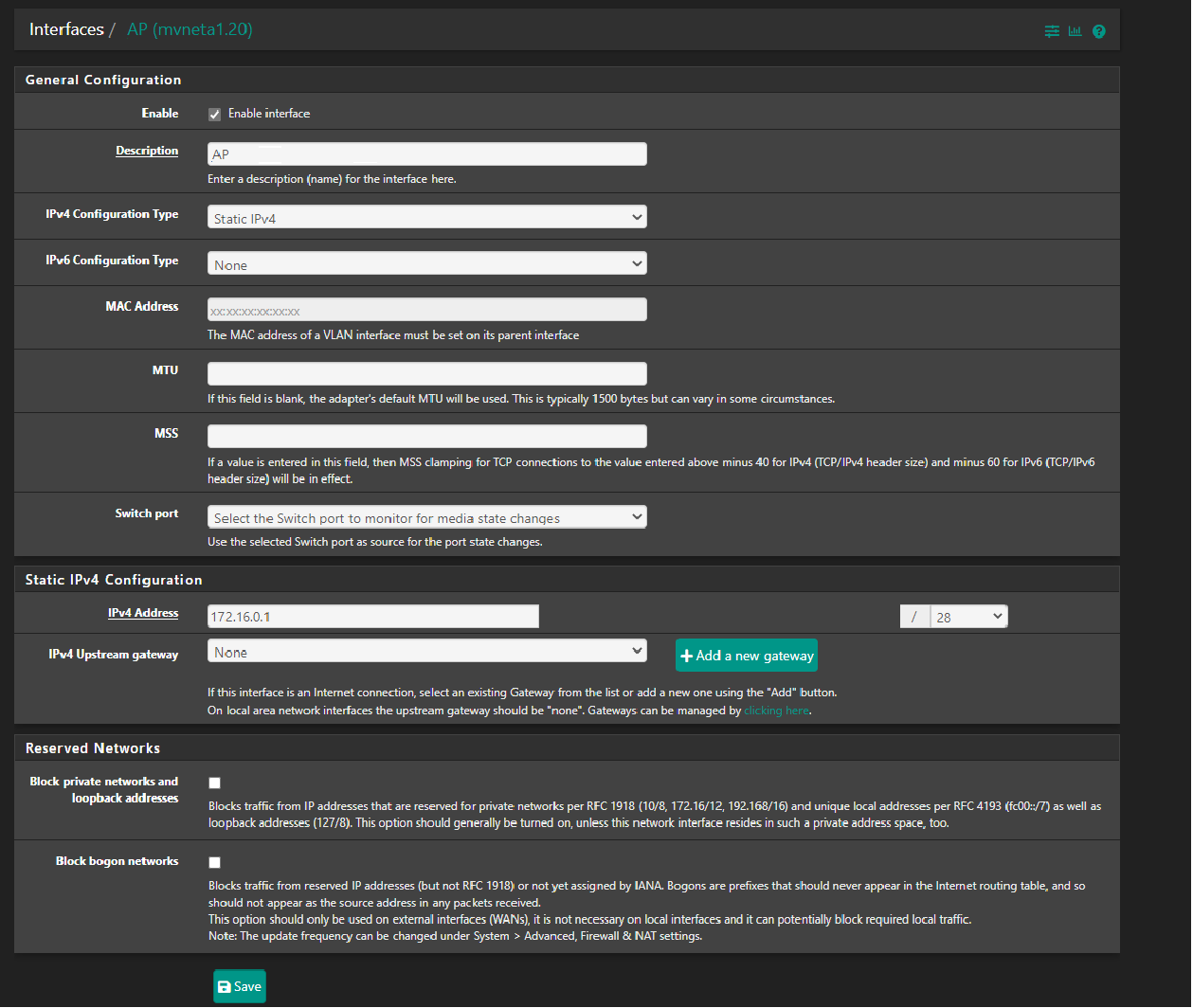
The model is "TP Link Omada EAP245 radio access point", there is a VLAN setting the default is or was NOT enabled. My logic or thinking is the physical connection to the switch port would dictate it should work but saying that it did allow me to specify a VLAN ID, so I set this to 20 which is the VLAN I am trying to work.
I must say I removed the VLAN 20 configuration from the Switch, left this as the default VLAN 1, it works or I can access the AP with no issues and use the Internet, is the issue that I am not communicating clearly with pfsense and my Switch maybe.
Many thanks
Chris -
I went through your repose once more, I think I have twigged what you are meaning plus I came across this previous article - https://forum.netgate.com/topic/143635/pfsense-and-vlan-help-hp-switch/3
In a nutshell it is now working, I assigned the PVID or the VLAN ID to the interface or port I use for my LAN. I tried a ipconfig command(Windows machine) and I got the IP address I allocated plus its corresponding 'Subnet Mask'. Plus, I could not see any other device on my LAN, these where hidden, which is what I was trying to achieve also. Still plan make changes, see what happens, but I now have a better understanding how it works.
Thanks, and thanks to everyone, for your replies.
Chris
-
I don't see any mention here of configuring the switch in the 2100 to pass the tagged VLAN 20 traffic to the HP switch. In it's default mode (port based VLANs) it will pass all traffic to all port so should work even if not an ideal setup. If you have changed the switch mode though it wonlt pass at all until it;s configured there.
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/switch-overview.htmlSteve
-
@stephenw10 That's a good point. It means that probably the OP's VLAN 20 packets are getting passed around to everything on her LAN, but that only looks like it's not occurring because the hosts aren't responding to them.
-
@cxcmax I think your setup is slightly over complicating things.
I don't have pfSense in front of me but the basic gist of what you need to do (and you should undo your settings):-
If you have access to a cheap dumb L2 switch swap out your managed HP switch for the time being. The cheap dumb L2 switch will simpy pass through the VLAN tags unfettered which is what you want at this point and you can focus entirely on the pfsense and the AP. Assume the netid you are using for your VLAN2 is 10.0.2.0/24 and your pfsense is 10.0.2.1/24 and AP 10.0.2.2/24.
-
Create a virtual AP on your EAP 225. Call your virtual AP guest or internet_only or whatever. Set its IP to 10.0.2.2/24 and gateway and DNS to 10.0.2.1. Set its VLAN tag to 2 ( you might find the VLAN settings on your EAP 225 in a different menu option than the IP settings option ). Leave the management interface on LAN netid no VLAN. Save your settings. The AP config is now done.
-
Go to pfSense and create a new VLAN2 on the network adapter you are connecting to the switch. Set its IP to 10.0.2.1/24.
-
Go to DHCP server and and add a new DHCP pool for VLAN2 e.g. 10.0.2.100 - 10.0.2.200. Set the gateway to 10.0.2.1 and dns to 10.0.2.1.
-
Go to DNS (best use the forwarder as its easier) and make sure it is listening on all interfaces or highlight those interfaces you need including VLAN2.
!!! At this point connect to the AP using Wifi you should be able to access the internet !!!
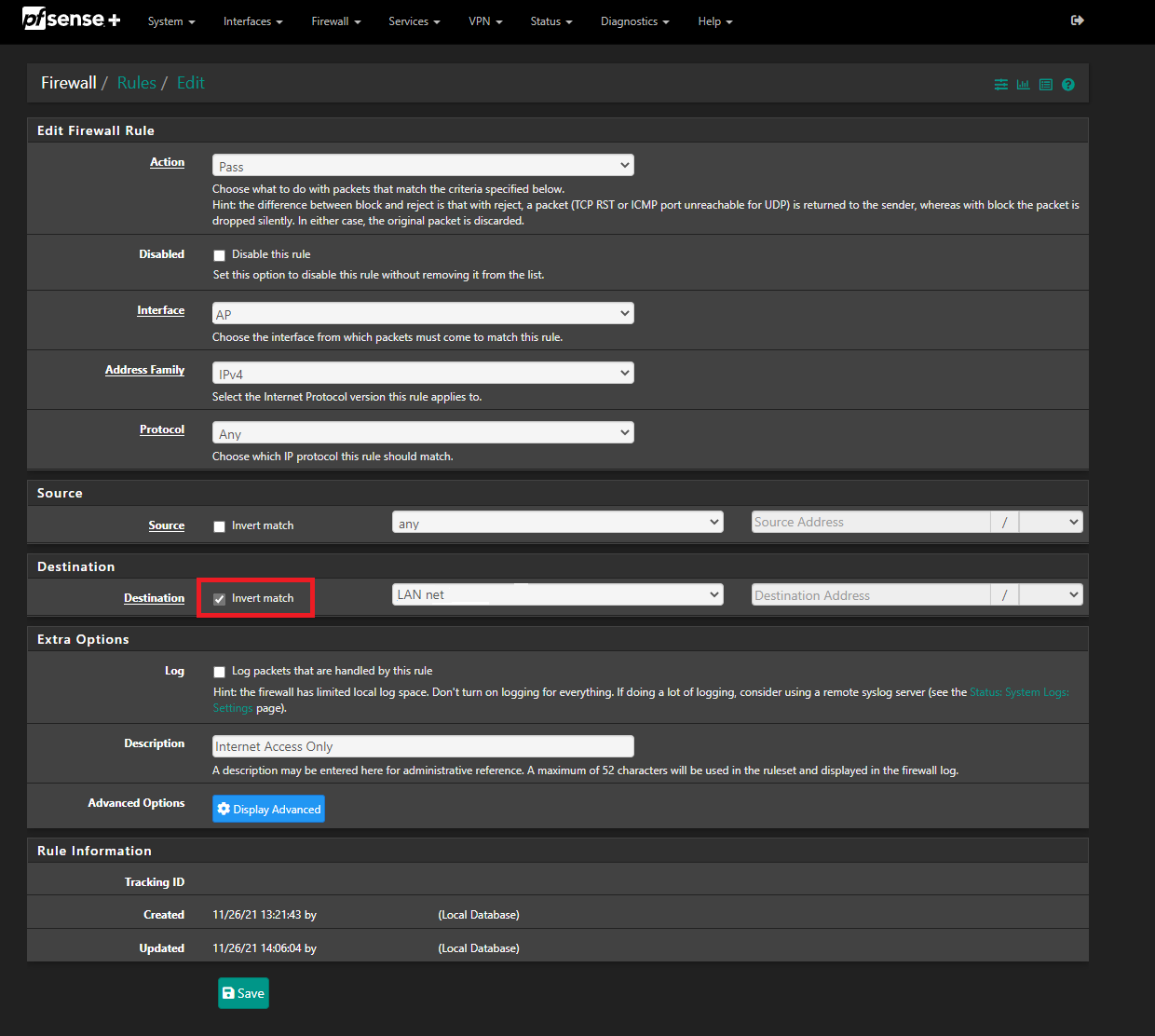
- Go to firewall and click on LAN add a new rule for IN drop VLAN2 NET. This will prevent users on VLAN2 from accessing hosts on LAN.
!!! At this point connecting a notebook to Wifi AP you can try to scan hosts on your LAN network which should be blocked !!!
- Remove the dumb switch and reintroduce the HP managed switch. If the HP managed switch is using comware OS then the two access ports you are connecting both the AP and pFsense into must be switched to either hybrid or trunk. Unlike Cisco IOS comware OS requires you to specify which VLANs can traverse the trunk port. Set it to VLAN 1 and 2 (1 is needed to access the management of the AP).
!!! At this point you should be able to access the internet using the HP switch !!!
-
-
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
If you have access to a cheap dumb L2 switch swap out your managed HP switch for the time being. The cheap dumb L2 switch will simpy pass through the VLAN tags unfettered which is what you want at this point and you can focus entirely on the pfsense and the AP.
I would avoid doing that if at all possible. An unmanaged switch will usually pass all tagged traffic but you cannot be sure of that until you try it. Additionally it will pass it to all ports. Any device on another port could tag it's traffic and become a member of that VLAN. It's much better to use a managed switch and control where the tagged traffic goes.
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
Go to firewall and click on LAN add a new rule for IN drop VLAN2 NET. This will prevent users on VLAN2 from accessing hosts on LAN.
A firewall rule on LAN will allow or prevent hosts on LAN accessing VLAN2 but it will not prevent hosts on VLAN2 accessing LAN.
You need a rule on VLAN2 to prevent that. You also need a pass rule on VLAN2 to allow any traffic from wifi clients, otherwise it will all be dropped.Steve
-
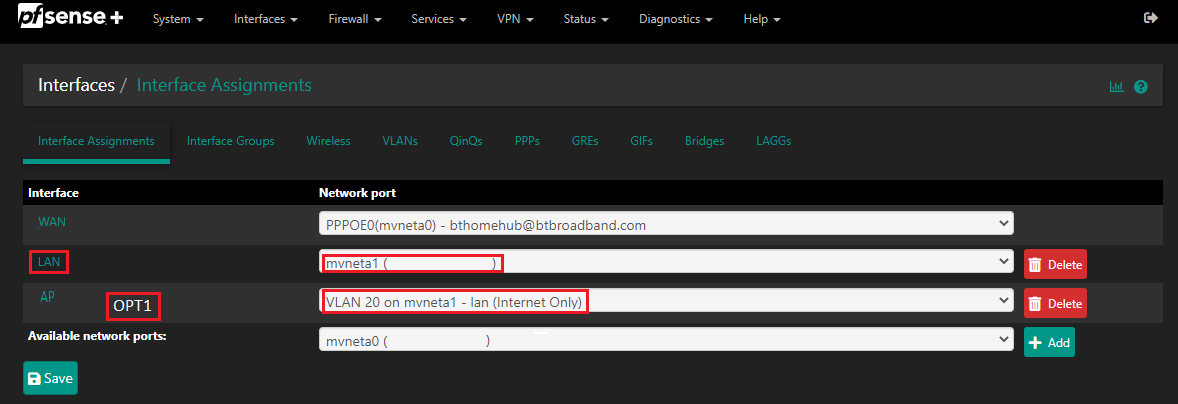
Hi and thanks to everyone also who has contributed to what must be a simply problem. I am going to look go through the steps listed in the "../Switch-Overview" give this a whirl. @stephenw10 the only thing that is confusion me a little is the LAN ports.
I am only using the one port to connect to my Switch, LAN1, I assume in the example in the documentation I am basically just substituting 'LAN4' for my 'LAN1'Chris
-
Yes, you can use any port as the trunk to the external switch.
Steve
-
@stephenw10 Relying on VLAN's for security is foolhardy. VLAN hopping through a switch is easily accomplished with a few simple commands on a linux box. VLAN's were not designed for security, they were designed for segmenting networks.
-
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
VLAN hopping through a switch is easily accomplished with a few simple commands on a linux box.
Can you demonstrate that? I'd like to test it if you have the commands.
Steve
-
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
@stephenw10 Relying on VLAN's for security is foolhardy. VLAN hopping through a switch is easily accomplished with a few simple commands on a linux box. VLAN's were not designed for security, they were designed for segmenting networks.
I think that depends on how you're using VLANs. If you depend upon hosts to tag their packets correctly [1], then yes, it's trivial to hop VLANs. If you require each host to use a specific switch port as an untagged access port that is a member of a particular VLAN, then the host should not be able to hop VLANs without a bug or misconfiguration in the switch. (Because the switch adds the VLAN tag on packets entering the access port, and removes them from packets exiting the access port). Of course "misconfiguration" could include errors involving nested VLANs and multiple switches.
[1] Don't do that!
-
Mmm indeed, I would hope nobody is having hosts tag their own traffic in anything other than a test environment. Obviously that is no sort of security.
-
This is very interesting stuff, being the novice do I need to have rethink about what I am trying to create here if security is a risk? Not having this knowledge, I could be doing more harm than good.
Just to recap, I am just trying to setup a Wifi Access or Hot spot for visiting friends and family, they do not need to see my main LAN if you wish.
I tried the suggested link/documentation, https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/switch-overview.html, I hit a bit of a snag with part of the setup process, the step that said delete the Member(s) from the VLAN group. I need to look at it again, possible reset everything back to fresh starting point go over these instructions few times. When I deleted the member, in my example LAN1, I was having to physically swap the LAN1 to LAN2 port on my netgate to get internet access again, and when I was on LAN1 I was also getting the IP address and Subnet mask range I setup as WiFi Access Point(172.16.0.1/28). The reference to "..Ethernet ports as discrete ports", since I am using VLAN 20 along with my Native VLAN, all traffic passes via that single cable from Netgate to a Switch, is this to help LAN1 on my netgate understand what information is coming through LAN1 and where it is to be redirected, ie back to the Switch port(s) assigned to VLAN 20(which again is routed through the same LAN1 on the Netgate)? Just a thought, you said 'Trunk', in an earlier reply, so I am trying to setup some form of a junction between VLANS; a Native VLAN which is the default and in my case VLAN 20, is that right?
Apology if the extra questions, its just so I can better understanding how this all fits together.
I will be the first to say I need to do a bit more background research, I do enjoy the negate device its a good learning curve.
Many thanks
Chris -
Are you adding the guest wifi network as a second SSID to an existing AP?
Or are you adding a new AP that will only carry the guest wifi?
In the first case the AP will present the guest wifi fraffic on a VLAN directly. So would be looking to trunk the VLAN through both the switch in the 2100 and the HP switch so it;s tagged to the AP.
In the second case you only need trunk it through the 2100 switch and then it will be an access port in the HP switch to the AP.
Steve
-
-
@stephenw10 said in Difficulty access the internet using my VLAN as an Guest Access Point:
An unmanaged switch will usually pass all tagged traffic but you cannot be sure of that until you try it.
Would someone please explain why that might happen. The only significant difference between a VLAN frame and any other is the contents of the Ethertype/Length field. That's it. Given that Ethernet switches are supposed to pass all Ethertypes, why would a switch not pass a VLAN frame?
For an unmanaged switch to not pass a VLAN frame, it would have to check the Ethertype and then specifically drop VLAN frames. It seems to me that's a lot to ask of a dumb switch. And to what end?
-
-
At the cable level VLAN hopping is straightforward. There is nothing to mitigate this.
-
At the switch level there are various ways to hop a VLAN. Most switches fresh out of their packing box will allow you to hop the VLAN. You must to take the effort to harden the switch. Even though you have spent days maybe weeks hardening your switch any security bugs in the software makes your hardening completely useless. For e.g. Some Cisco switches have a security bug in the HTTP server that is suscetiple to an OB attack giving the attacker executive privileges. This attack is easy to execute using simple telnet and a python script.
-
Finally there is the human error aspect. You can spend forever hardening your switch but at some point you are going to need to take that little paperclip bend it straight and do a full blown reset on the switch. At which point you forget you have just unhardened your switch.
-
-
@jknott Oh...and I forgot...
If an attacker fails to break into your super hardened switch all they need to do is literally cut the physical cable that is the trunk cable, crimp it with a new RJ45 plug, and plug it into their own switch and feed it back. Unless you have the proper monitoring software on your trunk line you wouldn't know.
-
if all you're doing is setting up a VLAN for friends and family I don't see where your concerns are. VLAN's are fine your purpose.
VLAN's are adequate for creating private networks
VLAN's should not be relied upon for security if that's what you're looking for. -
@cxcmax To me, your setup seems awkward...why not put an guest AP device that does its own DHCP and let your pfSense do DNS? Seems simpler than to have a static IP for your AP then trying to use the vlan as DHCP server.