PFSense UI not detecting externally created certs as server certs
-
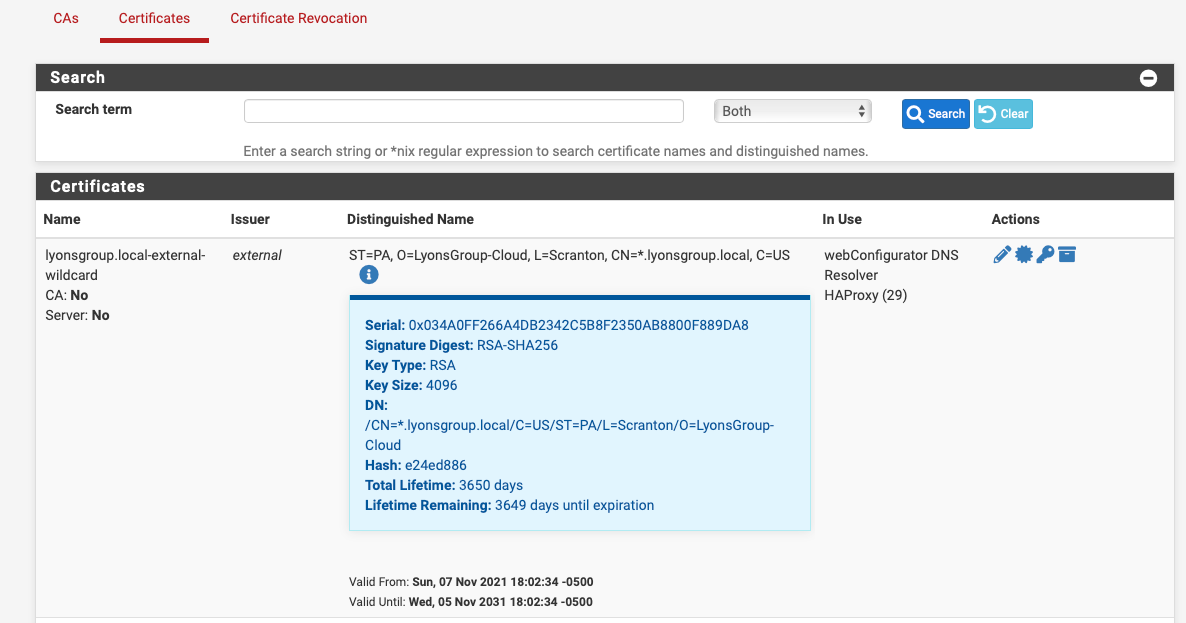
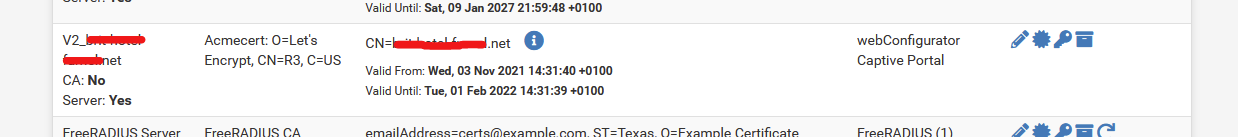
They are currently set up that way, the build process sets up the certs and ties everything thats using them up. All of this is done on initial create so all the certs are in use at start time but I see the "Server: No". I was wondering if there was some flag or something it is looking for in the cert attributes...
-
-
These are self-signed internal certs. When I create the certs in the PFSense UI, they do show as "Server: yes". Its not a big deal, everything works. I would like to have the UI show everything right and while these are only internal certs, they are used internally for a bunch of different things and if there is some setting I am missing that might cause issues elsewhere along the line so Im looking at it as PFSense giving me an early indicator that something may be up.
-
@mephmanx said in PFSense UI not detecting externally created certs as server certs:
These are self-signed internal certs
Aaaaah.
I was wonder who would sign a dot local certificate. I hadthe impression you were using 'real' (trusted) certs. -
Correct, they are created outside of PFSense using OpenSSL and then set during the install. Here is the config of the server cert:
##Required
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = v3_vpn_server
prompt = no##About the system for the request. Ensure the CN = FQDN
[ req_distinguished_name ]
commonName = $host_name.$INTERNAL_DOMAIN_NAME
countryName = $COUNTRY
stateOrProvinceName = $STATE
localityName = $LOCATION
organizationName = $ORGANIZATION##Extensions to add to a certificate request for how it will be used
[ v3_vpn_server ]
basicConstraints = critical, CA:FALSE
subjectKeyIdentifier = hash
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment, keyAgreement
extendedKeyUsage = critical, serverAuth
subjectAltName = @alt_vpn_server##The other names your server may be connected to as
[alt_vpn_server]
DNS.1 = $host_name
DNS.2 = $host_name.$INTERNAL_DOMAIN_NAME
DNS.3 = *.$INTERNAL_DOMAIN_NAME -
It's the 'purpose' flags set on the cert. For example on a cert created in pfSense:
steve@steve-MMLP7AP-00 /tmp/mozilla_steve0 $ openssl x509 -noout -purpose -in FreeRADIUS+Server+Certificate.crt Certificate purposes: SSL client : No SSL client CA : No SSL server : Yes SSL server CA : No Netscape SSL server : Yes Netscape SSL server CA : No S/MIME signing : No S/MIME signing CA : No S/MIME encryption : No S/MIME encryption CA : No CRL signing : No CRL signing CA : No Any Purpose : Yes Any Purpose CA : Yes OCSP helper : Yes OCSP helper CA : No Time Stamp signing : No Time Stamp signing CA : NoThough as I understand it most things ignore this so it's unlikely you would see an issue using that cert for the pfSense webgui.
-
@stephenw10 Dont know if you got my response to this...I think I replied via email and Im not sure if that works. I did find some things to clean up in my cert creation process but I still havent been able to get this flag to show up. I use openssl to create my certs...do you know what switch on openssl to use or if there is a value in the config or x509 settings that would kick this off? It dosent seem like its a big deal...things seem to work but would be nice to get everything to line up. Thank you for taking a look though!
-
My understanding is that the flag is largely deprecated which is why it works fine and most things ignore it.
I've never really tried but I would expect to be able to set that if you're creating it with openssl.Steve
-
@stephenw10 Thats what Im looking for is the flag for openssl...I cant seem to find it anywhere. It dosent seem like its used much..would just like to find it so the UI looks right.
-
Hmm, I guess I would start digging here:
https://github.com/pfsense/pfsense/blob/master/src/etc/inc/certs.inc#L688 -
@stephenw10 Wow, I think thats it! perfect! I was just adjusting those attributes for something else and I think I need that attribute for the VPN sever actually...was having issues with that. Great timing, thanks!
-
Ha, lucky!

-
@stephenw10 I have this working correctly now! Thank you so much for your help!
-
Ah, nice! What was the required incantation?
-
@stephenw10 I needed to add server into the nsCertType and serverAuth into extendedKeyUsage in the x509 extensions but need to add the x509 extensions as a command line arg to openssl, adding them into the config file dosent seem to work. Have to create it this way:
openssl x509 -CAcreateserial -req -days 7300
-in $cert_dir/$cert_name.csr
-CA $cert_dir/id_rsa.crt
-CAkey $cert_dir/id_rsa
-passin pass:$ca_pwd
-sha256
-extfile <(printf "$extFile")
-out $cert_dir/$cert_name.crtthe -extfile get the contests of the x509 stuff.