pfSense replacing a Cisco Router - not acting as expected
-
@johnpoz What I was trying to do was create a single route to my LAN, rather than routes to each VLAN... but it seems like that doesn't work. Unfortunately, if I switch the /24 routes on and the /16 route off, I can no longer access pfSense from inside my network, and everything on the 192.168.0.0 vlan no longer connects to the internet. I don't really want anything on the 192.168.0.0 vlan anyway though, I just moved them there to temporarily get internet access working until I could figure out what was wrong with the routing.
on Serverthehome, it was suggested that I had an overlapping route and if I move my transit vlan to a different subnet range such as 172.16.X.X or 10.X.X.X, then my /16 route will work, just by changing the gateway on PFSense, and making the new PFSense LAN IP the default route on the Aruba, eg make the Aruba VLAN1000 10.0.0.1 and pfSense 10.0.0.2, set the default route to 10.0.0.2 on Aruba, and add a static route to 192.168.0.0/16 via 10.0.0.1 on pfSense.
I'm in a webinar right now, so I can't test just yet, but this seems plausible. I'm not entirely sure why I didn't have this issue on the Cisco router though...
Looking at the diagram you posted kinda confuses me. I don't want pfSense to deal with multiple VLANs, I want to use it as a router/firewall between my WAN connection (and eventually add failover to the LTE one once I get the first part working) and my LAN, which should be entirely routed on the Aruba.
I have some time in about an hour to try changing the transit stuff, and I will follow up afterwards.
-
@jonthewise said in pfSense replacing a Cisco Router - not acting as expected:
if I move my transit vlan to a different subnet range such as 172.16.X.X or 10.X.X.X, then my /16
I would concur with this.. If you want to use summary route like 192.168/16, then using a transit network that is not in the 192.168 range would make sure your not overlapping.
You could also use some other summary route for your downstream that doesn't include your transit network.. For example if your transit was 192.168.0/24
Use could use some summary routes to include your other 192.168.x/24 networks vs specific /24 like 192.168.2/23
All depends what those downstream networks are and how you can summary it up.. But yeah easy would be to just use different range for your transit so you could use 192.168/16
-
@johnpoz Okay. Then something else that is confusing to me;
As seen in the screenshot, I created /24 routes for each of the VLANs that I wanted to have access to the internet, but when I turn those on, and turn the /16 off, I still can't reach the internet from inside my LAN, and it breaks access for all the things I moved to VLAN1000 to limp along. If I try creating a route on my pfSense router of 192.168.0.0/24 to point to 192.168.0.1 (the interface on Aruba) it throws the error seen here:

I think if I turn off the /16 and move all the stuff that was on VLAN15 and subsequently moved to VLAN1000 back on VLAN15, this would accomplish the same thing, but that didn't seem to work for me.
In a half hour I'm going to reload pfSense from scratch and start clean, but if I can't set a route on pfSense for the transit VLAN, I don't see how changing the subnet from 192.168.0.0 to anything else is going to make a difference?
-
Okay, well that absolutely did not work
On my Aruba, I changed the default route to 10.0.0.2/24 and made it's VLAN1000 interface ip 10.0.0.1
Reloaded a fresh pfSense install. Set the LAN to 10.0.0.2/24 with 10.0.0.1 gateway and created a route of 192.168.0.0/16 -> 10.0.0.1
Still no internet on my internal LAN networks... I'm typing this from a laptop that I manually put on the 10.0.0.0 network with 10.0.0.2 for the gateway and dns.
Ideas?
-
@jonthewise said in pfSense replacing a Cisco Router - not acting as expected:
Still no internet on my internal LAN networks
And did you edit your rules on this 10.0.0.1 interface to allow for these downstream networks? Did you adjust unbound ACLs to include your downstream networks. The auto ACLs for unbound are normally only the directly attached networks.
Also if you had messed with auto outbound nat, switch to manual for example then the downstream networks would not be auto added to outbound nat.
-
@johnpoz Did I do what? Point me to some docs?
I reloaded pfSense, so I haven't messed with anything except what I literally spelled out above. I was under the impression for basic internet access this would just work... but obviously my setup is a little more complicated than just using pfSense as a router

-
@jonthewise holy shit! All I had to do was add a firewall rule?!
I wonder if this was my problem the whole time?

See, I assumed that the LAN net was just saying anything that came through that interface :/
Adding the 192.168.0.0/16 rule (copying the default lan rule and changing the address) seems to have resolved the problem!
So thank you so much for pushing me in the right direction. I really appreciate all the assistance!
-
@jonthewise said in pfSense replacing a Cisco Router - not acting as expected:
All I had to do was add a firewall rule?!
Yeah - which was clearly spelled it in the picture I posted about setting up a downstream router ;)
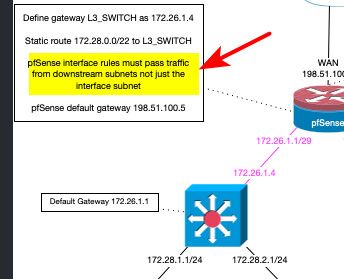
How you had it before where your route overlapped with the connected network - while could work in a device that is designed or configured for that. Its not good idea to do it that way, because it can be confusing. If a router gets traffic destined for network xyz, and its directly attached to a xyz network, why would it send it to some downstream router to get there, when its directly attached to this xyz network..
Now in theory it could arp for this host IP, on its attached xyz network, and doesn't see it send it on via some route..
-
@johnpoz I guess I can see that it says that now that it's all highlighted and has a big red arrow pointing at it... It just wasn't clear to me (I really don't specialize in networking) that what it meant was that there needed to be a firewall rule in place to allow traffic. Here I was trying to figure out why I couldn't ping the gateway from my devices, and thinking it was a routing issue, when it was just being blocked by a firewall rule

How I originally had it set up would have worked because I had created /24 routes for each of the VLANs on my Aruba and tried turning off the /16 as a part of my troubleshooting, and had I figured out the darned firewall rule was missing, everything would have worked just fine with the transit VLAN living on 192.168.0.0/24 and all my other VLANs on their respective 192.168.X.X subnets, and there wouldn't have been any overlapping routes. That being said, I'm fine with having my transit on the 10.0.0.0/24 and using a 192.168.0.0/16 route to the LAN, and it also looks a little cleaner.
But regardless, chalk this one up to operator error. It would seem most people that use pfSense either connect to a layer 1 network, or actually know something about networking (okay, I know a little bit, but mostly just enough to get myself into trouble LOL)
Thanks again. I'm sure I would have never figured this out on my own!
-
@jonthewise said in pfSense replacing a Cisco Router - not acting as expected:
It would seem most people that use pfSense either connect to a layer 1 network, or actually know something about networking (okay, I know a little bit, but mostly just enough to get myself into trouble LOL)
That should say layer2, but when I try to edit it's flagging my post as spam and won't let me save