Outbound NAT?
-
@gatenet said in Outbound NAT?:
So something is messed up with the NAT on the pfsense, but I don't know where to start.
dude I showed you exactly how to start.. Sniff on your wan - it will be clear as day if pfsense is not natting outbound traffic.
-
@johnpoz dude, sorry, I meant how to start fixing this. Are this the NAT reflection settings, Outbound NAT mode, something else in the Advanced Firewall & NAT settings. What am I supposed to do here?
:(Edit: I mean, now we know, that pfsense is not actually doing NAT? It just forwards the packet with the same source address out the wan interface.
-
@gatenet well for start - lets see your outbound nat rules.. Since this is what does the nat.
Did you alter them from auto? Are you sending out a different wan? Is the source IP downstream of pfsense, and not actually attached to pfsense?
How exactly is this client even getting to this public wan IP if not natted? This public IP must be actually on your network? Because rfc1918 are not routed over the public internet.. So if you sent data with source IP of rfc1918 while it might get to something internal to your ISP network, it wouldn't get past their network to get to your smtp server, that is showing that in the logs.. So where exactly is this server? Is it just sitting on your wan net of pfsense?
-
The outbound NAT for this interface is this, no mappings, just the automatic rules:
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24 * * 500 LAN2 address * Auto created rule for ISAKMP
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24 * * * LAN2 address * Auto created ruleI did not alter from auto. The pfsense has only one WAN.
The mailserver is a linux server with one WAN interface. Both WAN IPs (pfsense and the mailserver) are on the same /28 subnet. But this should not matter, I tested with a mailserver on a completely different public IP subnet, and the same happens.
Attached a basic diagram of the setup:
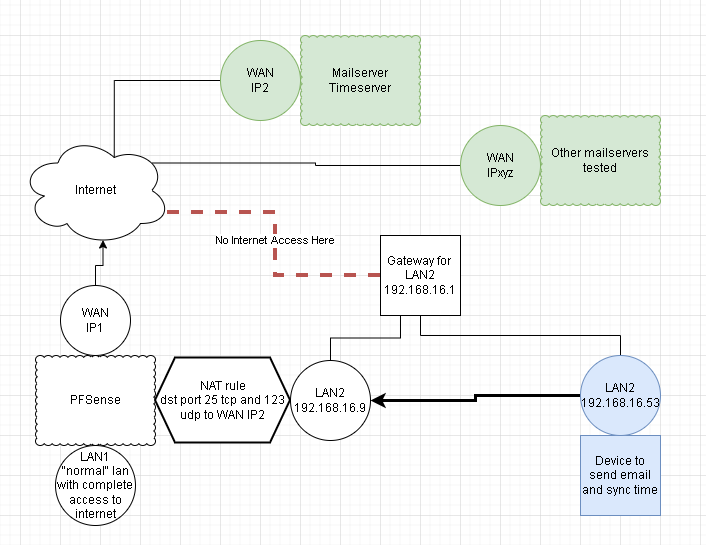
Just to clarify again here. On this client trying to send email, the server address configured for the mailserver is the LAN2 IP of the pfsense. NOT the WAN IP of the mail server. So the packets arrive from 192.168.16.53 (client) to 192.168.16.9 (pfsense) and it gets forwarded out, but pfsense should nat the packet with the source address of its WAN interface, right?
-
@gatenet said in Outbound NAT?:
LAN2 127.0.0.0/8 ::1/128 192.168.85.0/24
And where is this 192.168.16 network? If psfense sees source traffic from 192.168.16 and its allowed out, but there is no outbound nat for it, then no it wouldn't be natted.
I did not alter from auto. The pfsense has only one WAN.
If you created a gateway and route for pfsense to know how to talk to this 192.168.16 network then auto nat would of been created. But if you just altered your rules to allow for it, how would it be natted? And even if it was - how would pfsense know how to send back the return traffic without the route?
If lan 2 (192.168.16/24) is interface on pfsense then it would be listed in the auto outbound nat rules.
-
-
- LAN2 address
-
That looks like you created lan2 as a wan for pfsense? You put a gateway on it, which is wrong.
-
-
Well that did it, I just removed the gateway from the LAN2 interface, and now it works. I would never think of that.
Thank you so much for this. I already wanted to give up and just restart everything from scratch :)
-
@gatenet said in Outbound NAT?:
I just removed the gateway from the LAN2 interface
Out of curiosity - what did you have there? In your network drawing there is nothing you could of pointed to on the 192.168.16 network that would of been able to get to other networks.
-
@johnpoz Well, there is a twist.
I had the gateway there 192.168.16.1 (its a router without an internet connection, it is in the drawing).
And now I know why I put it there when I was setting this up a few years ago.
There is a monitoring server also on LAN1 that makes SNMP querys to this LAN2. And this stopped working now when I removed this gateway from the LAN2 interface.
So I have a new problem to solve now :) yaaaaay
-
@gatenet said in Outbound NAT?:
There is a monitoring server also on LAN1 that makes SNMP querys to this LAN2.
That sure and the hell has zero to do with a gateway setting on lan 2 interface.
Your problem with talking to device on lan 2 from lan 1, is if your lan 2 devices point to that 16.1 as a gateway? Gateway to what? You show it has no internet access. So what does it have access to? From your drawing this 192.168.16.1 is pointless device..
Your devices on 192.168.16 should point to the pfsense lan 2 IP as their gateway.. If you don't want these devices to have internet, then don't allow them internet access.
If this 192.168.16.1 device is router to other networks, then it should be attached to pfsense via transit network and you can correctly route all your local networks, etc. etc..
What other networks does this 16.1 have access to?
-
@johnpoz Well, one would think that. But that device is a VPN concentrator for access to many different networks, this 192.168.16.x being one of them.
Its quite a rigid setup on this 192.168.16.1 device, no internet allowed out. That is why my idea for getting emails out was using a pfsense, since messing with this main gateway could break other more important things... And this works now thanks to you.
-
@gatenet well if you lan 1 devices that need to talk to lan 2 devices that point to 192.168.16.1 as their default gateway.
Just source nat your traffic from lan 1 so it looks like it comes from pfsense lan 2 IP via outbound nat on the lan 2 interface.