DNS entries not updated
-
@mik-1 said in DNS entries not updated:
For the home wifi interface dhcp server, I defined first dns as my domain controller (so home clients can know the domain workstations) and a second dns as a nexdns.io dns entry (profile1).
Doesn't work like that - you have no idea which NS will be asked at any given moment.
If you want your clients to resolve your AD stuff, then the ONLY ns clients should point to is your AD dns. Then your AD can forward to where you want to resolve other stuff, be that pfsense or some outside dns..
-
@johnpoz Hello, can you explain in detail "you have no idea which NS will be asked at any given moment" ?
I believed when a client asking a resolution, it uses the DNS servers entries he has in the order of their definition. So I believed I should put the AD first and then other DNS.I defined 2 networks for the wifi to be able to set up different dns entries on each. I use 2 network groups from my ESXi, each with a VLAN, pointed to one vswitch with a dedicated port. This port is linked to a Dlink AP with multiple SSID. So I can set up a SSID per VLAN.
I use Nextdns.io as my prefered DNS server to avoid ad and trackers and to protect my network from malicious websites. With this service I can also quickly define profiles with scheduled services and parental control.
So that's why I define a profile per wifi network (profile home and profile guest).
The home wifi clients can access to the domain and internet via the nextdns.io home profile ; the guest wifi clients can only access internet via nextdns.io guest profile.
On my networks, I have some windows and linux OS, some on the domain, and some not.If I understand what you advised, is to let the AD as the DNS for the domain clients and set up a forward dns that points to pfsense ?
So I must define AD IP as DNS server in the settings of the home interfaces of my pfsense and the nextdns.io home profile on the pfsense general settings ?
And for the guest wifi I defined only nextdns.io (profile guest) as my DNS servers for this interface ?Thanks for your help and have a merry Christmas :)
-
@tzvia Hello, thanks for your answer, I already tried the ipconfig /release, /renew, /flushdns but the DNS servers listed in the ipconfig /all still the same and I never see the AD IP as my first DNS.
I tried this from a windows 10 outside of the domain.And if I try to switch my wifi from my android phone, I can see (in status details) the exactly DNS entries I defined on the wifi pfsense interface.
I will try what @johnpoz advises me.
Have a merry Christmas :) -
@mik-1 said in DNS entries not updated:
it uses the DNS servers entries he has in the order of their definition
Nope not how it works at all.
forward dns that points to pfsense ?
Why forward directly to this nextdns.io, your not using pfsense dns now, so why would you think you need to ad it into the mix?
-
yes I can use my AD as DNS server, but I have several networks, one for the workstations, one for the servers for example.
My AD does not know all of these networks, but pfsense does. -
Hello again,
I was stupid ! It did not worked because I forgot to clean my client wifi settings on nic !! I defined specific dns on my nic configuration, that's why my windows client wasn't able to use the dns provided by the DHCP f each wifi network :(
sorry for many questions for nothing.
So now, to resume :- for my home wifi interface I define the AD as first DNS entry and nextdns.io (profile home) as 2nd et 3rd entries
- for my guest wifi interface I define nextdns.io (profile guest) as DNS first and second entries
- I defined no DNS in the general config.
All works fine as I expected, may be it is not the right method but it works for now, I will try other settings later :)
thanks a lot again for your help
Have a nice end of year 2021 !
Mike -
@mik-1 said in DNS entries not updated:
I define the AD as first DNS entry and nextdns.io (profile home) as 2nd et 3rd entries
This might work for a while, but the first time your client asks for something in your AD from nextdns.io and gets a NX, its just done its not going to ask your AD dns.
While the dns might be listed 1st, 2nd, or primary / secondary.. Your client will ask either of those at any given time. And when you ask something that doesn't know what your asking and sends back a NX, the client says ok - and doesn't ask any of its other listed NS.
You need to point your clients that can resolve all of your local dns. If you want you could have them all ask pfsense, and pfsense could have a domain override for your AD domain.
And if it doesn't know what your asking for, then it would forward to your nextdns thing.. But putting multiple NS into a client, where the NS can not all resolve the same stuff is going to be problematic..
-
@mik-1 In an environment where you have your own DNS servers for resolving the internal network and for domain joined devices to properly reach domain controllers for policy, for example, you should have all the devices pointing ONLY to the domain DNS servers. Not one internal DNS server and another being something on the internet. If you have multiple disjointed networks where some cannot reach the network where your DNS servers lie, those need to be pointed somewhere else, but if any can reach your internal DNS, that is the only DNS they should get. If your DNS server cannot resolve the request because the request is for something on the internet, you can have it forward to a specific DNS server on the internet. But I would suggest you have it forward to PFSense if you are using services like PFBlocker. PFSense can forward if you wish, or it can just resolve.
I've been running a Windows domain at home since 2003, and got my MCSE (microsoft certified systems engineer) in Server 2000 a long time ago... and I can tell you as johnpoz has, having one DNS server setting being the internal and the next being something on the internet doesn't work the way you think. The first answer your computer gets from a DNS server, even if it is "doesn't exist, can't be found" ends the request. So if a Windows desktop happens to query the internet DNS server for something internal and gets a 'not found' answer, that's it, and vice versa. You have made a crapshoot DNS. Only when a DNS server is non responsive, would the client then move to the next server in the list for DNS. Point them all at your DNS, and then let your DNS server forward as needed.
-
@tzvia hello, thank you a lot for this complete advise, I will follow your advises. If I forward the DNS from DC to pfsense, how do I have to set up the DNS addresses on pfsense ? On the general settings ?
Are the DNS settings on pfsense DHCP server supercede the DNS settings of general configuration ? -
@mik-1 said in DNS entries not updated:
Are the DNS settings on pfsense DHCP server supercede the DNS settings of general configuration ?
Yes if you point a client to a specific dns via dhcp, that is what it will use (if the client is dhcp).
Out of the box pfsense doesn't forward, and the dns you might have in general is only for pfsense own use. Out of the box, really the only thing you should have listed is 127.0.0.1, but I believe pfsense defaults to allowing for what gets hand out to it via dhcp (from your isp) to be listed. But unbound would never use those, only pfsense trying to resolve something it wants, check for update, resolving something in firewall log when you click the little resolve button.
Now if you setup unbound to forward it will use what you have listed in general. If you want unbound (pfsense) to forward to this nextdns - then you specifically need to set that up in unbound.
If your goal is to forward to something specific on unbound.. You should prob turn off get dns from dhcp for pfsense.
uncheck that option
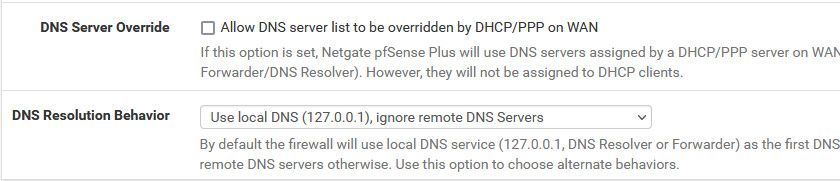
And put only what you want to forward to in the pfsense dns settings.
Personally if me, and I was running AD on my network. I would just leverage the AD for both dns and dhcp for all my clients. Even if those devices are not members of the domain. AD dns is more than capable of running multiple domains that are not its AD domain. If you want to use different domain names for these other devices.
You then could have your AD forward to unbound on pfsense if you want to say leverage pfblocker. Or just want to forward via unbound to somewhere. But you could also just forward to nextdns on your AD, or let your AD actually resolve like pfsense does out of the box.
The big take away here is that when a client has more than 1 dns listed, you really don't know which one at any given time it will ask. So if your going to point to more than 1, you need to make sure they are all capable of resolving the same stuff. Outside dns is never going to be able to resolve your internal domains.
-
@johnpoz Thank you a lot for this detailed answer. I will apply your advice, use my AD for DNS and DHCP.
Thanks again and happy new year ! :)