Is there a better way?
-
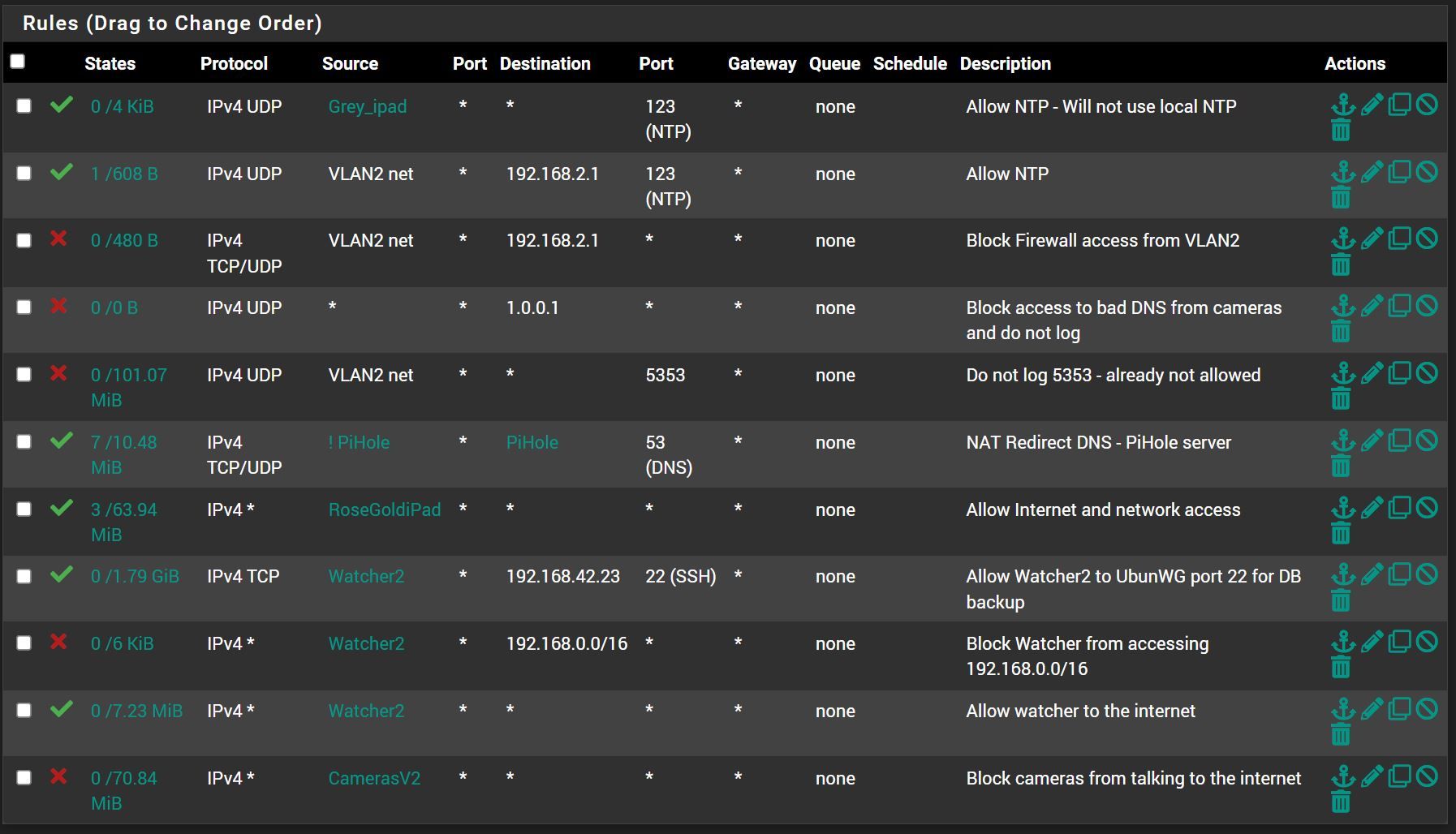
I altered my network and have isolated my security system. Allowing full access from the LAN to VLAN2 (security VLAN), but not the other way. In doing so I caused the iPads we use to look at the cameras to traverse the FW. To resolve this I moved the iPads to the same VLAN. I also needed to keep the security system from talking to the LAN, but it needs to backup to one of the LAN PCs.
When I was done I have a working system, but 11 rules to get it done. Is there a better way to structure the rules or collapse some rules. I am reasonably certain the last rule can be removed.
I am asking so I can maybe learn a little something and make it better.
The rule descriptions are reasonably good as to why the rule is there.Thank you,
-
@andyrh
A fairly granular rule set.Is there a specific reason for the Grey_ipad group to use public NTP servers?
If not you could redirect the traffic to your local server by a port forwarding rule.For blocking or allowing access to pfSense itself the preset alias "This firewall" is a good choice.
In a block rule it rarely makes sense to state the network assigned to the respective interface as source. It almost could be "any".
Consider that the 'RoseGoldiPad' might also have access to the pfSense web GUI, at least to other interfaces IPs, when not blocking before with "This firewall" destination as mentioned above.
For only allowing internet, but internal networks, I create an RFC 1918 alias and use it in a pass rule as destination with 'invert' checked.
Maybe this is an option for your "Watcher2" and you can save the block rule, if 192.168.0.0/16 includes all your internal network. -
Grey_ipad is super old and the time drifts unless it is allowed to public NTP. Tried redirecting it with no luck. Must be an Apple thing.
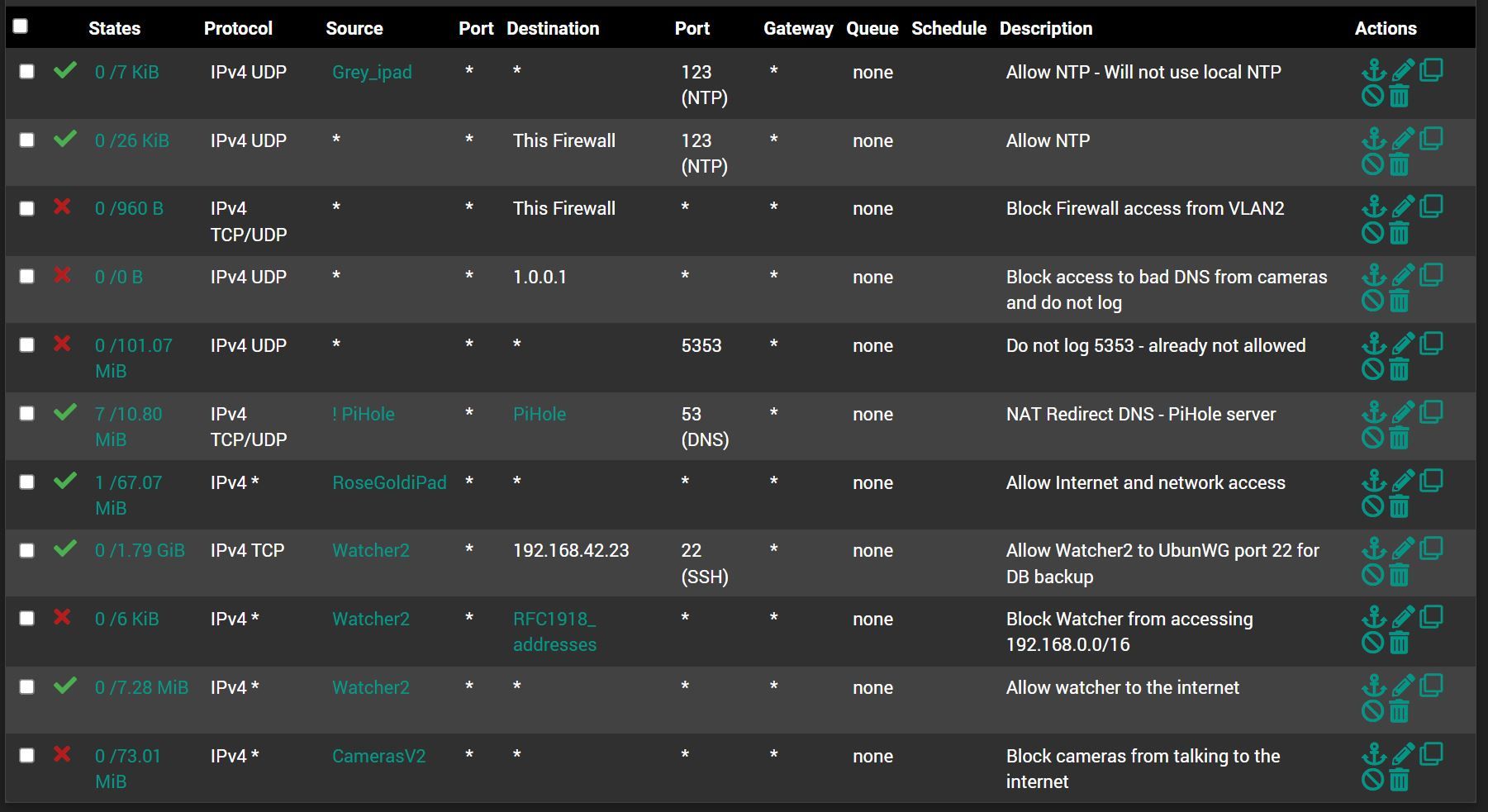
Changed to "This firewall" Thanks
RoseGoldiPad is current and I am not stressed about it having an issue, but good point.
The RFC 1918 is a good idea. There is a VPN to a friends house that is not blocked. I will make that change.
Thank you for reviewing.
-
Not really clear why you has to move the ipads to the security vlan. They would not connect to the cameras to view them from a different subnet?
-
Impressive.
-
@stephenw10 They generate 3Mb of traffic each. GreyiPad is only used to watch the cameras. The other one does that 99% of the time.
Maybe not a great reason, but that is the reason. -
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on