Second WAN interface, no NAT
-
@ziceman said in Second WAN interface, no NAT:
It does show how to create a second WAN, but each of those instructions still have the NAT / Masq in place as well as the Gateway config.
I cannot think of any use of a WAN interface without a gateway.
However, If you don't want a gateway, just leave it blank. Doing so, pfSense will not add masquerading rules. -
Thanks for the reply.
The gateway of the primary WAN is still being used, but this routing is being handled by AT&T fiber on their backend.
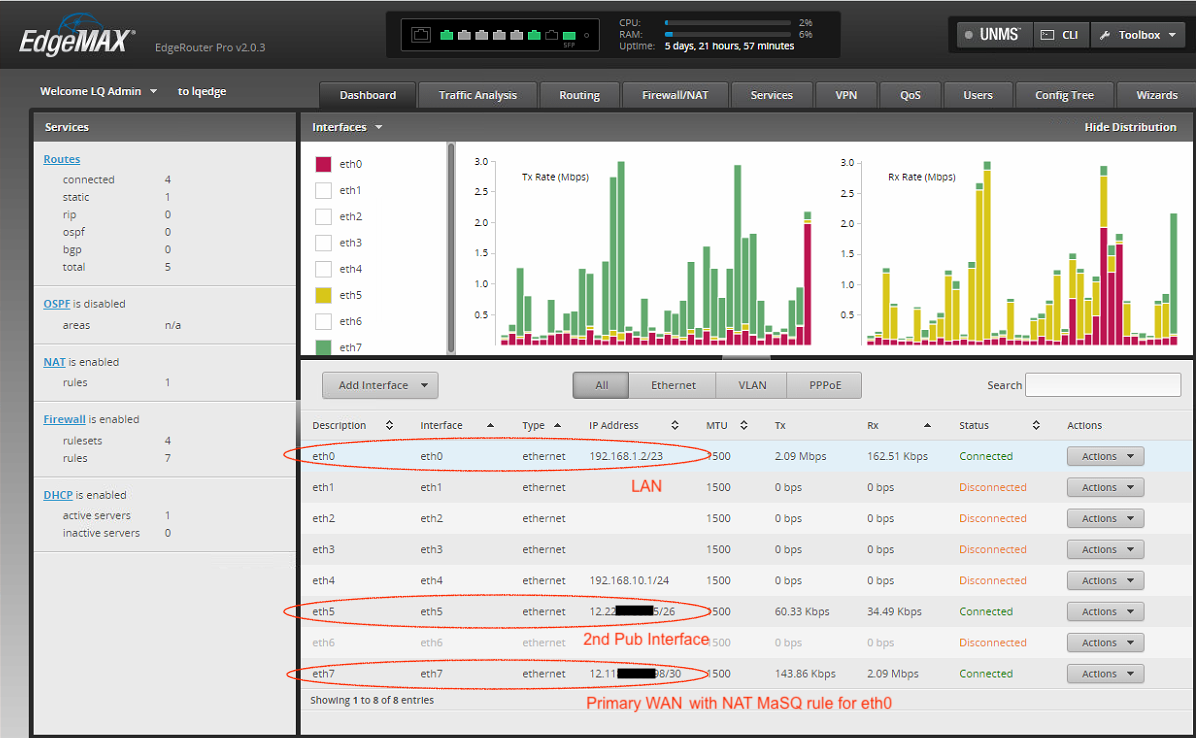
As shown in the image, they provided a 12.22X.XXX.XX/30 subnet for the primary connection. We can then use the other 12.11X.XXX.XXX/26 subnet for 62 unique public IPs. All these IPs use the interface IP of the second WAN as their default gateway (different from the main /30 gateway). That other WAN port is connected a switch that we can use for any of the other public-facing devices.
Let me know if that makes sense and the NetGate will work in this configuration.
-
@ziceman said in Second WAN interface, no NAT:
We can then use the other 12.11X.XXX.XXX/26 subnet for 62 unique public IPs. All these IPs use the interface IP of the second WAN as their default gateway (different from the main /30 gateway).
You mean, the IPs are routed to a single IP which you should add the second WAN interface.
And response packets should go out on WAN1 to the default gateway?This can also be done with a single WAN. I don't see the use of a second here.
-
This was the designated configuration by the AT&T fiber engineers. I have no idea why they did it this way.
But in order for us to have a few dozen public IPs, they specified the exact parameters for the firewall configuration. The Edgerouter was able to support their setup, and I am looking to see if a Netgate solution can supplant the appliance.
-
@ziceman
It should work in both way, with a single or two WANs. The different of two is that you have two MACs.If you do it with a second WAN leave the gateway option in the interface settings at "none", so pfSense will route out all traffic on WAN1, responses as well.
Masquerading only affects upstream traffic. So all upstream traffic will go out with WAN1 IP.
Responses to incoming traffic get the origin public IP when they go out. So the would go out on WAN1, but with an public IP of WAN2.
If your provider accepts this it will work. -
Actually, when we check the IP from a browser running on any of the machines hanging off the managed switch connected secondary WAN port, the 12.22X.XXX.XX IP is returned.
So the the other interface with the 12.11X.XXX.XXX/26 public IPs does appear to be using the WAN1 as a gateway.
The main thing is that we need to be absolutely sure that there is no MASQ / NAT rule setup for the secondary WAN.
Is there a way to confirm this?
-
Hi All - just checking back to see if anyone else had input on this?
Thanks much!
-
@ziceman said in Second WAN interface, no NAT:
The main thing is that we need to be absolutely sure that there is no MASQ / NAT rule setup for the secondary WAN.
Well look in your outbound nat - if your auto and it has a gateway then it would be set to nat outbound to that interfaces IP.
If you don't want it to nat, and it has a gateway you can go to hybrid mode and turn off the outbound nat for that interface. Or full manual mode and do the same thing. Hybrid is normally a better choice.
-
@ziceman It sounds an awful lot like the second WAN you're talking about is not a WAN but just an interface that has public IPs on it...in essence a LAN2 for lack of a better name. If the ISP routes that subnet to the WAN1 interface IP then it just works and there's no NAT needed here. pfSense will "know" to route the packets to the LAN2 interface.
Outgoing packets will go from the (let's say) web server to its gateway, the LAN2 interface IP, and pfSense sends them out to the only gateway it knows, out WAN1.
-
@steveits exactly - I think this is more just a routed public IP network?
https://docs.netgate.com/pfsense/en/latest/recipes/route-public-ip-addresses.html