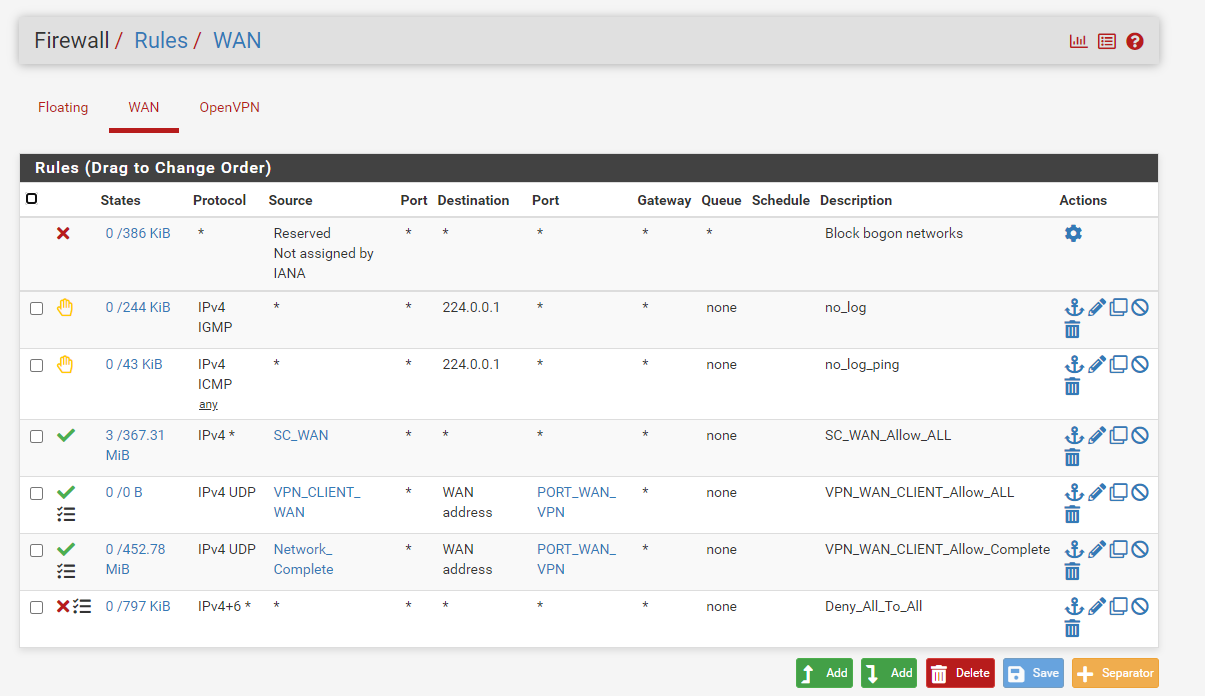
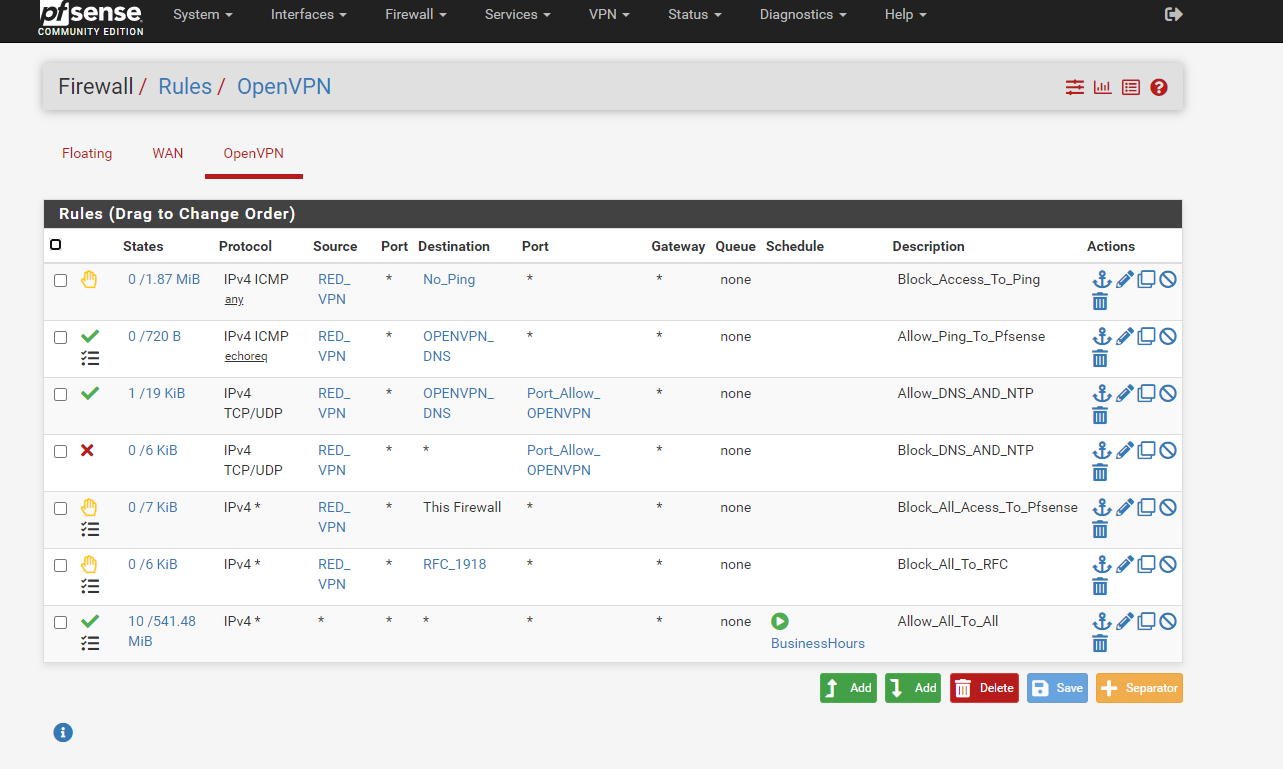
traffic in wan
-
@silence
whois 31.13.71.1 | grep 'name'Facebook wants more information from you, so they try to contact you on port 31599.
Pick up the line and see what they want ?157.240.241.60 is also facebook ....
Your WAN IP is RFC1918, so you have an upstream ISP router ?
If so, you were a bit lazy, and activated the DMZ of that router ? I mean : all entering WAN traffic is redirected to the WAN IP of pfSense, 192.168.1.254 ?
If you use the pfSense OpenVPN server on port 443 TCP, then create a NAT rule for that port/TCP to the WAN IP of pfSense. The traffic will probably still hit the WAN side of the ISP router "but you won't see it any more" - except the VPN port traffic ;)And call facebook, see what they want.
-
@johnpoz said in traffic in wan:
are you asking about the traffic to port 31599?
yes
@gertjan said in traffic in wan:
Your WAN IP is RFC1918, so you have an upstream ISP router ?
yes
@gertjan said in traffic in wan:
If so, you were a bit lazy, and activated the DMZ of that router ?
NO DMZ
@gertjan said in traffic in wan:
If you use the pfSense OpenVPN server on port 443 TCP
NO
To confirm, my vpn client does not have any problem, they can access facebook and whatsapp or any other web site without any problem.
-
@silence Dude is that UDP is it SYN, is SA, what is that traffic... Can not tell if this unsolicited inbound or an answer to something that is out of state.
Go into the full firewall log other than the widget..
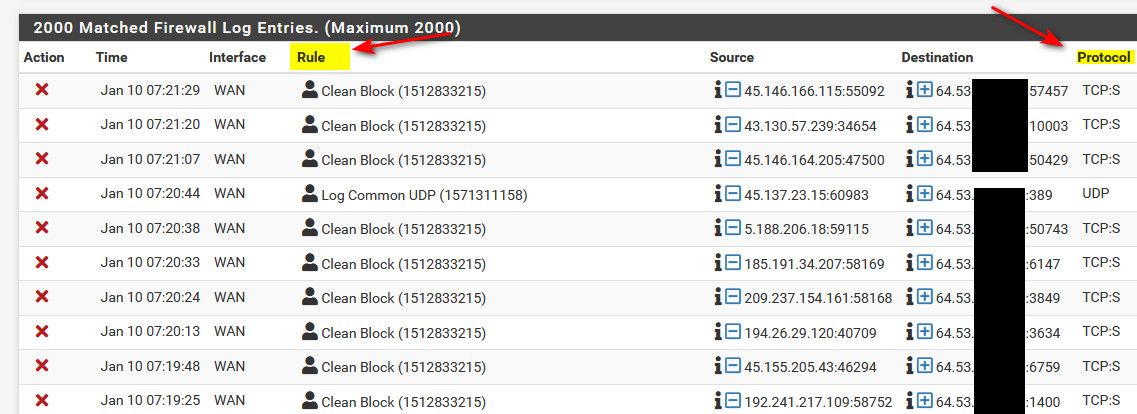
So can see what rule blocked that, and also what protocol and state.
It just seems really odd to me that you have a connection you allowed to that IP on https port (443) on your vpn interface. But that is a server connection not a client connection. So if I had to guess that was an inbound connection from that 72 address to your 31.13 address listening on 443..
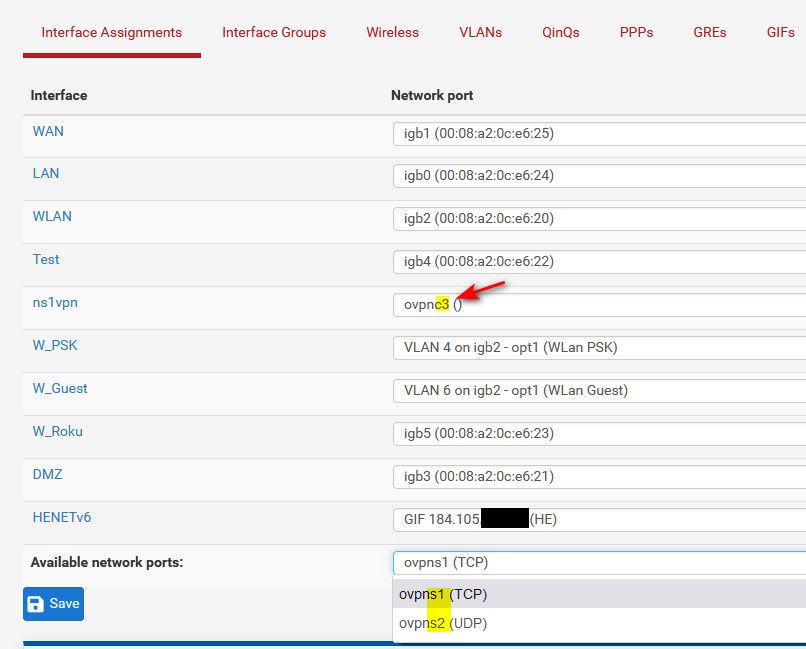
If you use the pfSense OpenVPN server on port 443 TCP
That a vpn SERVER.. see the s2 on the end.. That is server, client (ie you talk to some service) would be cX
example..
See my client instance, and my 2 server instances..
-
@johnpoz said in traffic in wan:
Go into the full firewall log other than the widget..
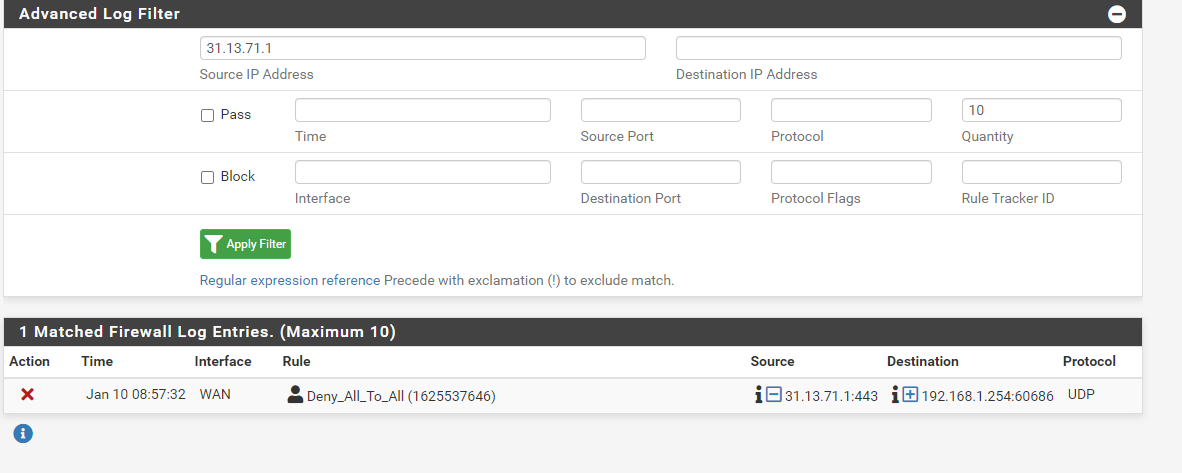
First registration of the same IP today
Note: I deleted the old records for other reasons.
-
@silence what is that rule, that is not the default rule..
So that is inbound traffic to your pfsense IP 192.168.1.254, from that 443 port.. Source of 443 is odd as source port, would be more like an answer to something you requested..
QUIC uses UDP over 443..
https://peering.google.com/#/learn-more/quic
So I would guess that is some answer to something you requested on that 31 IP. But its blocked because there is no state for that traffic.
edit: seems facebook is playing with quic
https://engineering.fb.com/2020/10/21/networking-traffic/how-facebook-is-bringing-quic-to-billions/ -
@johnpoz, The question is?
is this a problem or is it normal?
since my vpn client have no problem using facebook or any other apps.
-
@silence It seems odd that if you were using facebook app or website through your vpn that you would be seeing traffic to your wan interface. From IP y our talking to through the vpn.
So something is not quite right. If you were flowing outbound through a vpn.. How would it know your actual wan IP?
But then again not sure how you have your vpn setup, that sure looks like a server interface in your first log, but if you were using a vpn service it should be a client interface cX..
Without more details of your setup, and what your doing with facebook its hard to tell what is actually going on.
But that IP is for sure a facebook IP.
;; ANSWER SECTION: 1.71.13.31.in-addr.arpa. 3600 IN PTR edge-star-shv-01-lga3.facebook.com. -
@johnpoz, I always see the same sequence ...

-
@silence So how would you be sending traffic from that 72 IP to 31, and then 31 through some server connection, and then getting an answer back on pfsense wan.
How do you have your vpn setup... If you were using some vpn service, that would be a client setup in pfsense. Do you have some site 2 site setup with some server elsewhere?
If your flowing through a vpn, how would facebook know your wan IP to even send anything? Something in their client reporting something?
-
-
@johnpoz said in traffic in wan:
So how would you be sending traffic from that 72 IP to 31, and then 31 through some server connection, and then getting an answer back on pfsense wan.
This is what I am trying to find out, what is really going on?
because everything seems to work 100%
-
-
@silence said in traffic in wan:
NO DMZ
Then how passes this traffic "destination port 31599" through your ISP router ?
No NAT rules on that router ?@silence said in traffic in wan:
Any suggestion?
Yep, a suggestion - not a solution.
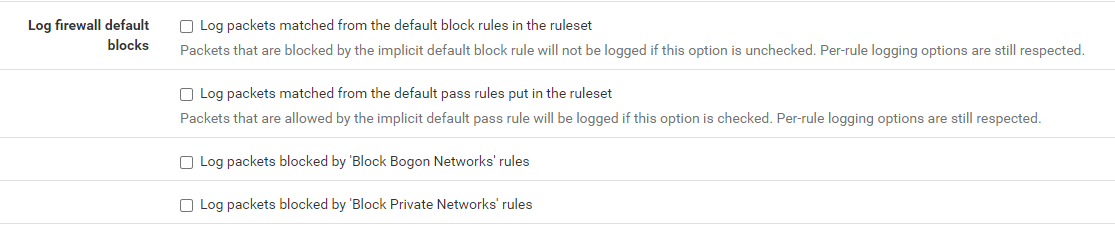
First things first : Status > System Logs > Settings :
Uncheck :
Rules on your WAN interface : don't make them log.
And enjoy the silence ^^
@johnpoz said in traffic in wan:
seems facebook is playing
My advise : refuse their 'games' ;)
-
-
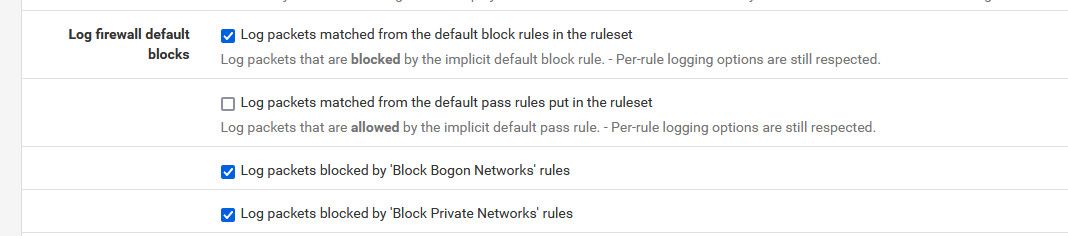
@silence no they weren't, the default is all checked except the default pass.
I have setup pfsense countless times.. And here this is a default VM setup not that long ago..
-
@johnpoz said in traffic in wan:
@silence no they weren't, the default is all checked except the default pass.
I think they are not understanding me,
first: from the beginning of the installation uncheck these options
second: I think they are straying a bit from the main question!
-
@gertjan said in traffic in wan:
My advise : refuse their 'games' ;)
@johnpoz dice
@gertjan said in traffic in wan:
seems facebook is playing
I don't understand what you mean by which facebook is playing?
I'm just trying to come to the conclusion!
-
@gertjan said in traffic in wan:
Then how passes this traffic "destination port 31599" through your ISP router ?
on router is open port 10443 1194 and 9022
NO USE DMZ.
I need help to determine if facebook is trying something unauthorized against my pfsense or just normal traffic.
-
@viragomann It can help me to get out of doubt ...
-
@silence
Obviously you get requests form 72.238.67.3 to 31.13.71.1:443 from a client connected to your OpenVPN server.
These are directed out to your WAN correctly and it gets your WAN address, which 31.13.71.1 is responding to. But for what ever reason pfSense obviously has not set a state and the traffic is blocked by your WAN Deny_All_To_Any rule. So presumably without this rule, it would by blocked by the Default_deny rule anyway.I'm wondering if the traffic from public source IPs is really desired on your VPN server.
However, basically this should work, but obviously pfSense has no state for the connection, when the response is coming back.
Maybe it has something to do with the scheduled rule, which is allowing it and the rule was just closed.
If that's the reason, ensure that System > Advanced > Miscellaneous > Schedule States is unchecked.