LAN Websites cannot be accessed
-
@gertjan what? You want him to route his own local traffic out to some vpn service and then back? What?
-
@johnpoz
Exact.I know : Method 1: NAT Reflection can do the trick- but then why @itzdaniel483 didn't find it ?
Method 2: Split DNS : is even better - would work but needs :For this to work using the DNS Resolver or Forwarder in pfSense software, clients must use the IP Address of the firewall as their primary DNS server.
Breaking local DNS is not a rare thing these days. People are spraying 8.8.8.8 first, and ask questions afterwards.
So I proposed a third solution. I'm pretty sure it works.
-
@gertjan If I do need to do critical work on them I do have to use a VPN it just slows my work down too much and I shoulnd't have to do that when I'm on the same network as the sites. I've tried all of the NAT types even the DNS splitting and nothing :/
-
@itzdaniel483,if it is on the same network? Why don't you access your sites with your lan domain?
-
@gertjan If your client or whatever is using some external dns and is hardcoded and or you want your client to use external dns so that there is no way to resolve the internal IP.
Then use nat reflection, or if you have your site setup via haproxy you don't need to worry about nat reflection you could just bounce off your own local reverse proxy.
At least then your not adding who knows how much latency, nor are you doubling up your wan bandwidth, and your not adding the overhead of the vpn..
-
@itzdaniel483 said in LAN Websites cannot be accessed:
DNS splitting and nothing
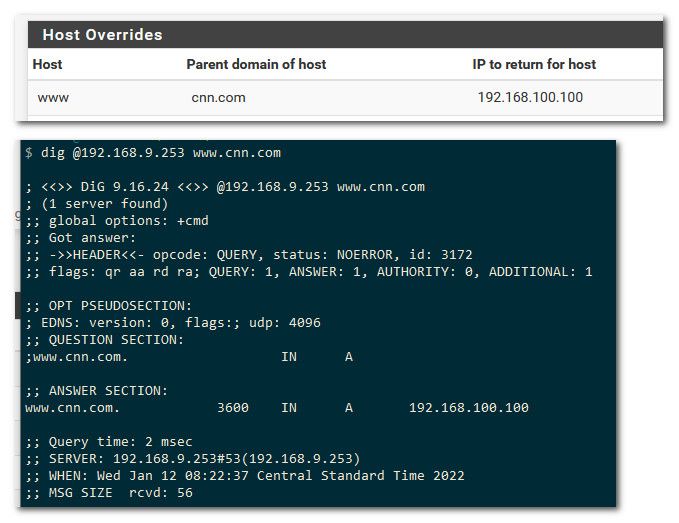
Is your client using pfsense for dns? Simple query locally via your fav dns tool, dig, host, nslookup will show you if your host override is correct for the split dns setup.
Did you set it up in the right section - not the first time would have seen user setup host override in dnsmasq when they are using unbound, or in unbound and they are using the forwarder.
That is why simple test to validate your host override is working is good.
here I just made www.cnn.com resolve to 192.168.100.100
-
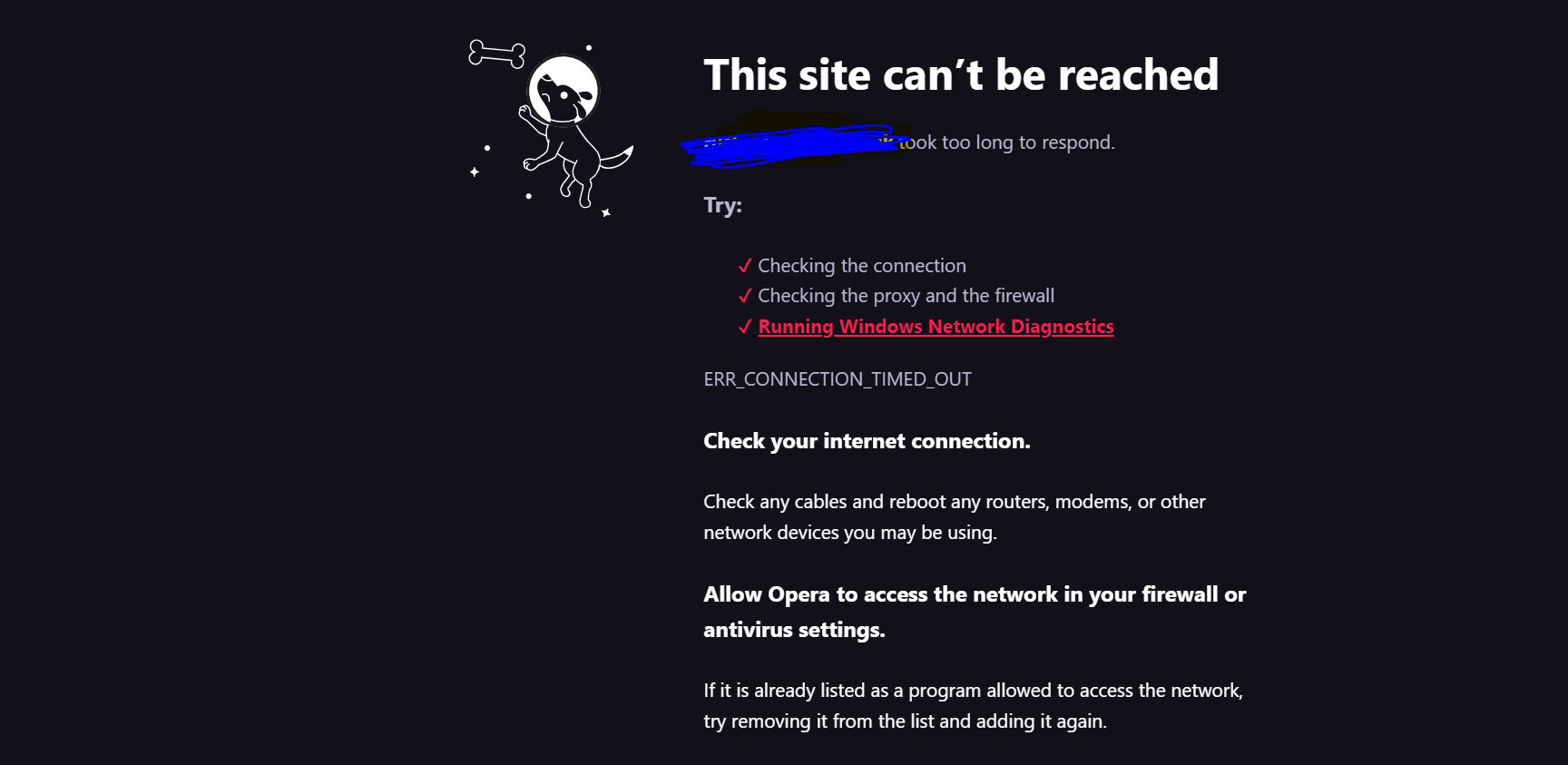
@silence Wdym, I try to access them through the domain itself but it doesn't work not even through the domains IP address
-
@johnpoz All the devices in the network are set to use PFsense as the DNS server. I've done a NS lookup and all seems good I'll try to tinker with the split DNS, I've done a DNS lookup on PFsense and it can see the domains are on 192.168.1.150. If I ping the domain from say CMD, it says (ping xxx on IP xx.x.x.xx, request timed out)
-
@itzdaniel483 see my edit, if your dns resolves to your local IP.. Then your host override is correct.
That you can not ping that local IP points to another issue, and devices talking to each other on the same network have nothing to do with pfsense. Is your client your trying to access this site with on a different local network/vlan than the server?
-
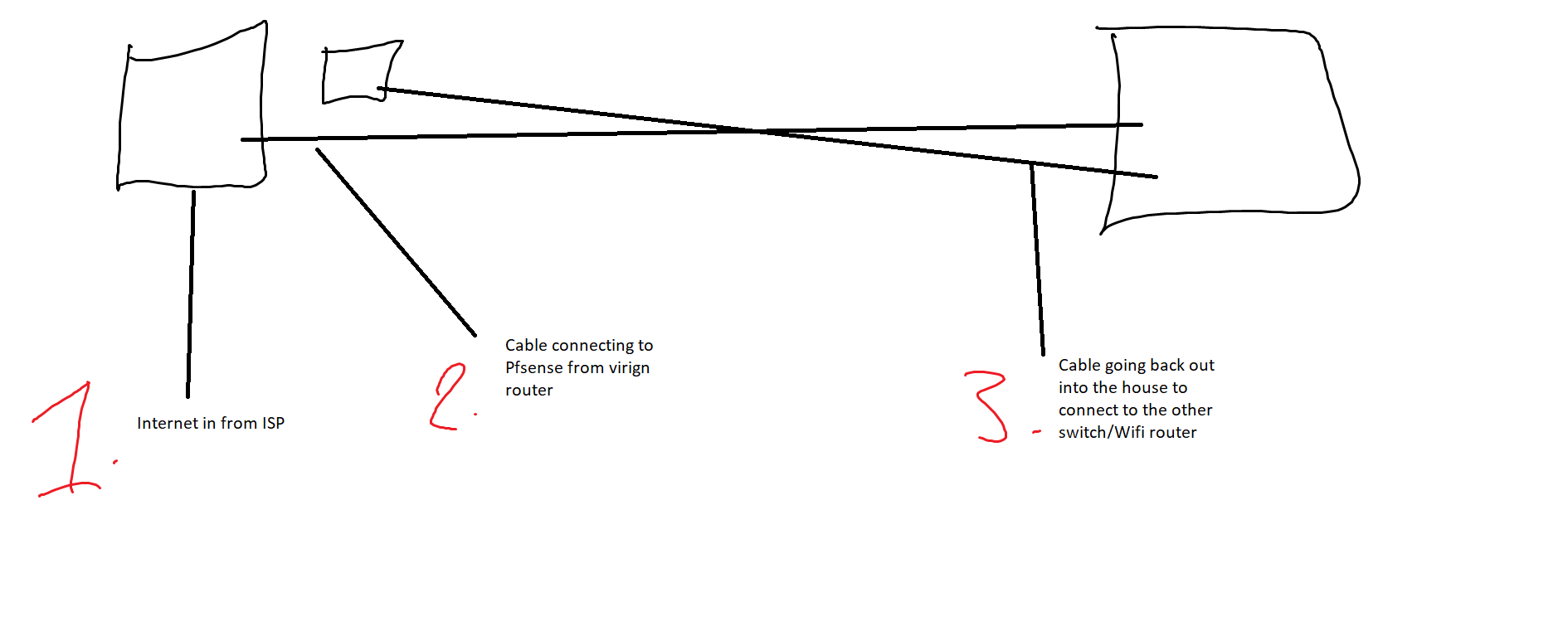
@johnpoz Nope, I'll try to explain my network.
Virgin Media in the house, that router is in router mode to allow us to use PFsense as our main router, there is a cable going into PFsense, then another coming out PFsense into a switch to connect to the servers, a cable going from the switch, to another switch in the house to connect up to a router so we can have WIFI but that router is in router mode so it gets all of its data from PFsense and is not its own network.
Edit, I've tried to make a diagram its very bad but this is as best as I can explain it as my laptop is too small to draw a decent diagram
-
@itzdaniel483 no drawing needed for such a basic setup.. So your devices are all on 1 network, since you don't mention any downstream router or vlans setup on pfsense.
Only question I would have - is this wifi router you mention doing nat?? Or are you using it as AP and all devices all on the same network.. Connected it your network via one of its lan ports, turned off its dhcp server.. etc..
So your wifi router is in router mode, doing nat.. And where is what trying to access what - if your on pfsense network and trying to access network behind pfsense - then you would have to setup port forwards on your wifi router.
-
@johnpoz said in LAN Websites cannot be accessed:
to resolve the internal IP.
My turn to say What ?
No need to know the internal IP. A VPN and the fqdn will do.
We're talking basic@itzdaniel483 said in LAN Websites cannot be accessed:
my websites that I host on my LAN
I presume these web sites are accessible from the outside - and meant to be accessed from the outside, using some DMZ scheme or plain old NAT rules on every local router (ha proxy - whatever).
When @itzdaniel483 uses a VPN, he can "https://www.what-ever-server-he-hosts-right-next-to-him.tld" and be sure that fqdn resolves fine for him and thus all the other world wide visitors.
He'll be seeing what the others see, using the same path right back over his own WAN connection.
Of course, I agree, this is cumbersome.I would throw in a host over ride for every server / device and call it a day ....
edit : ...... Local APs doing routing .... that's a great way to make live harder
 .
. -
@johnpoz I believe the router has DHCP mode disabled and it uses PFsense but I am not 100% sure I will check when I am next back. But yes the router is is in AP mode as its just an extension of PFsense as I didn't want it to be on a seperate LAN
-
@itzdaniel483 said in LAN Websites cannot be accessed:
extension of PFsense as I didn't want it to be on a seperate LAN
If I had a nickel for every time I have heard that its an AP, and its really natting - prob have like 100 bucks something ;) hehehe
What local network are you using? 192.168.1?
Lets say PFsense is set to (example IP) 10.41.14.45. The web server as a virtual IP of 10.41.14.46 linking to a LAN IP of 192.168.1.150.
This is confusing - I have idea what that is suppose to mean, how does a 10.x address link to a 192.168 address if they are not vlans/network routed by pfsense? But you say you only have 1? Do you mean pfsense wan IP 192.168?
If pfsense wan is rfc1918, no wonder nat reflection would never work on pfsense, because pfsense isn't the public address. Nat reflection would have to be done on your upstream nat router, etc.
Is your web server running as a VM on something also doing nat? Here is the thing, when doing split dns were www.yourdomain.tld resolve to the local IP of your webserver pfsense has nothing to do with that communication other than handing out the IP for www.yourdomain.tld.
-
@johnpoz Sorry yes the 10.xxx domains were just examples of the 13 static WAN IP's that I have from my ISP, PFsense is set to one of those IP's. So PFsense WAN IP would be say 102.2.1.4.1 etc and LAN 192.168.xxx. My Web server is a physical machine in an R410, which has its NAT handled by PFsense
-
So that is not what your drawing is showing.. You state router, not modem as your cable connection - so this implies NAT with the term router. If pfsense wan is public, great this is where nat reflection would happen.
But again if you say you resolve www.yourdomain.tld locally to 192.168.x.x, and some device on 192.168.x.y talking to 192.168.x.x has nothing to do with pfsense..
Can you ping 192.168.x.y from 192.168.x.x ? If you client using pfsense as dns resolve www.yourdomain.tld to 192.168.x.x and you can not access this website this has nothing to do with pfsense. The only thing pfsense had to do in that scenario is hand your client the 192.168.x.x address.
-
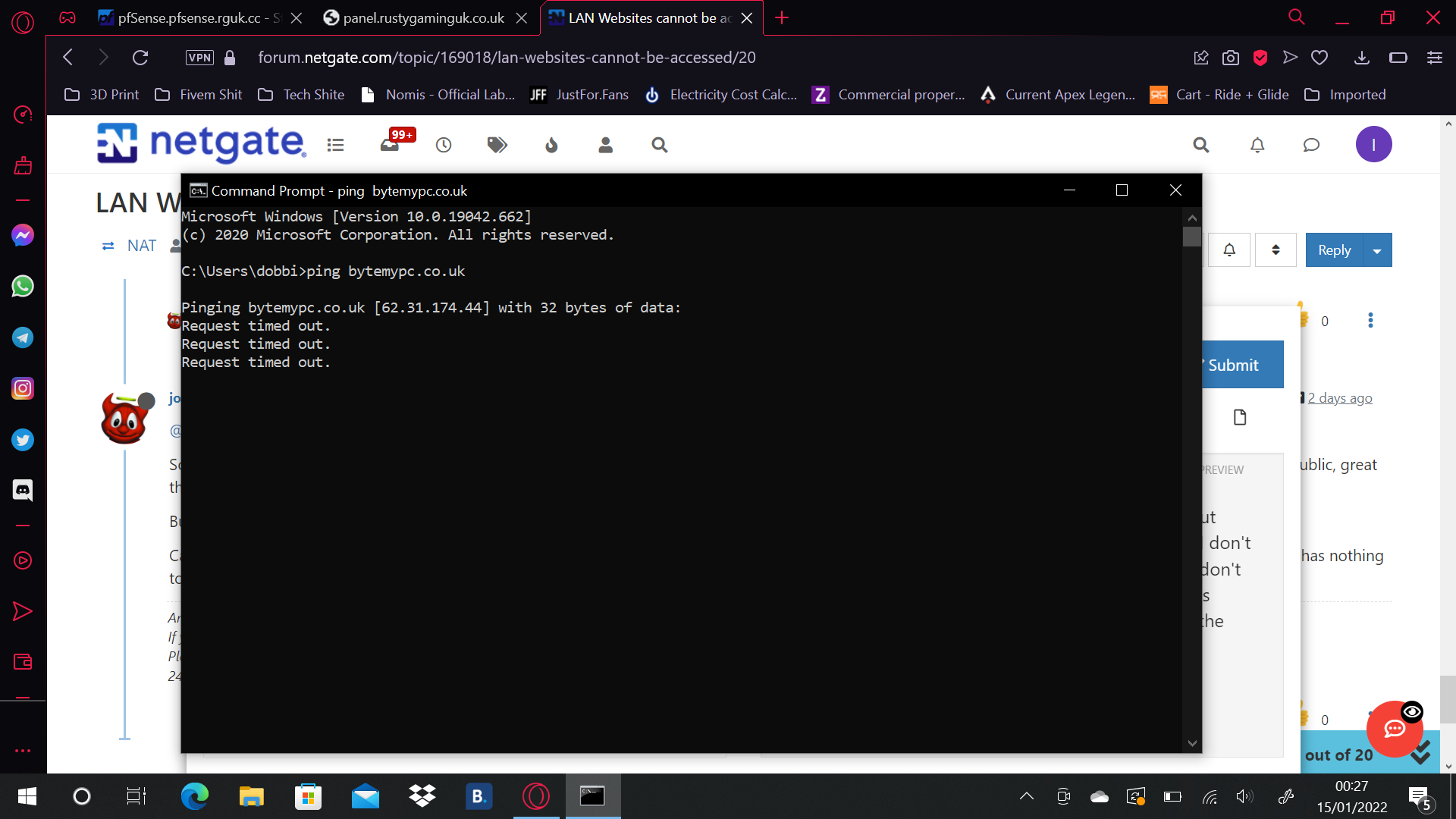
@johnpoz That's what I am trying to figure out. The network cannot access sites on the same LAN without some sort of VPN or editing the host file on my PC. I don't get why outside access works but LAN connections don't when they're on the same network. No idea what has changed but something has. Sure Pfsense can ping the domains but the devices cannot, It sees the IP but the request times out
-
@itzdaniel483 62.31 sure and the hell is not your same lan..
Again if your pfsense wan is some rfc1918 address, and your trying to hit some public IP that on the wan of your isp router - your isp router would have to send that back into pfsense wan 192.168 address.
Has zero to do with pfsense..
If www.domain.tld is local to your network, just set your dns to resolve www.domain.tld to your local 192.168 address.. This is a better solution anyway, it never makes any sense to have traffic transit your firewall just for your firewall to send it back to the same network your own for traffic that it should of never be involved with in the first place.
-
@johnpoz yeah don’t worry I know they’re not the same but I’ve even tried to route through internally through PFSENSE by the host overrides and still nothing I am baffled