Permission errors running commands as Admin?
-
Hmm, where is the other subnet that does not show errors?
-
The other subnet, without errors, is a vlan carried by a LACP bond.
-
So both are locally connected but one is WAN side?
What NIC/driver type is the WAN?
-
It's an APU4c4 with intel i211AT chipset for all 4 ports.
And yes, both locally connected, 192.168.0.0/24 is on the WAN side. My pfsense WAN interface is assigned my public IP via dhcp. So if looking at a PCAP of WAN interface I see traffic flowing between addresses in 192.168.0.0/24 to my public IP on WAN.
-
You see anything logged as blocked in the firewall logs?
I can't see why anything that passed for the VLAN would not be passed on WAN though...
-
I didn't see anything, I can't check anymore the logs have been overwritten. The permission error is not happening anymore, but I have not changed anything. This is typical with my last year or so of using pfSense. Strange, unresolved problems that come and go.
-
I looked again and am seeing a lot of weird entries... at least I don't understand them.
https://i.imgur.com/kub5EZB.png
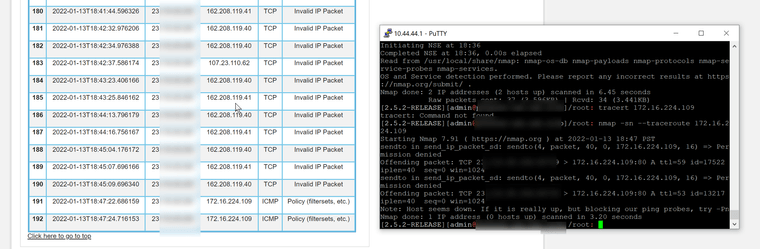
Here is my laptop @ 10.44.44.50 being blocked by default rule... I don't understand how that's possible. As in -- the default rule would not apply to that traffic. And I also don't understand the GUI lockout.
-
The traffic hitting the default rule is doing so because it's out of state TCP traffic. It's all ACK traffic to a SYN the firewall didn't see. It implies you have some asymmetry in your network and that can produce odd behaviour in other ways. You should remove the asymmetry.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.htmlThe traffic hitting the GUI lockout rules is because that IP has attempted to login incorrectly too many times. SSH guard is similar for SSH connection attempts.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/locked-out.html#locked-out-by-too-many-failed-login-attemptsSteve
-
@stephenw10 I've been able to re-create this error while scanning the same subnet (192.168.0.0/24).
Additionally, another private address gave permission errors and interestingly enough there was a corresponding log in my ATT gateway.
** **
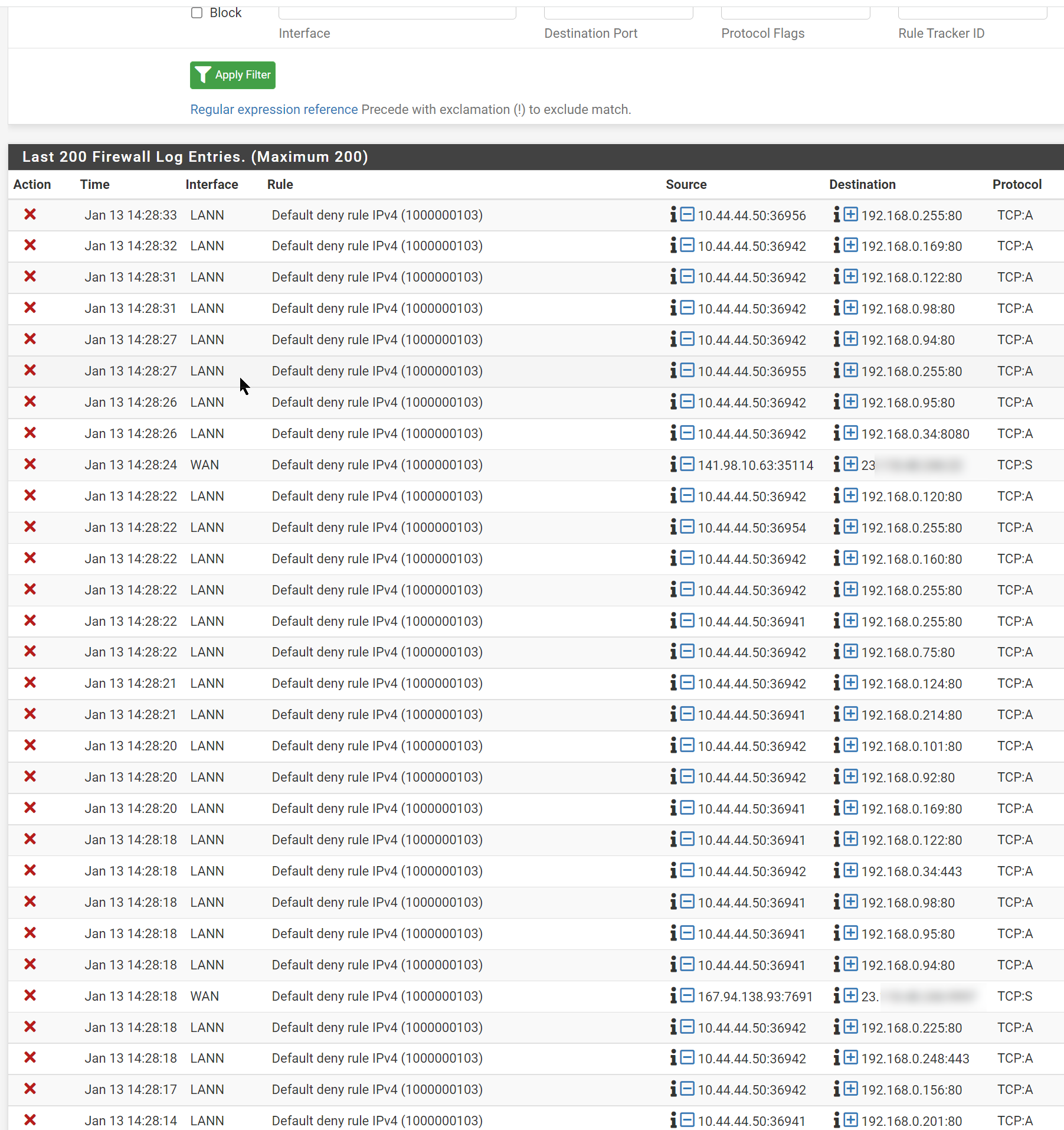
**Here's my laptop being denied on LAN...
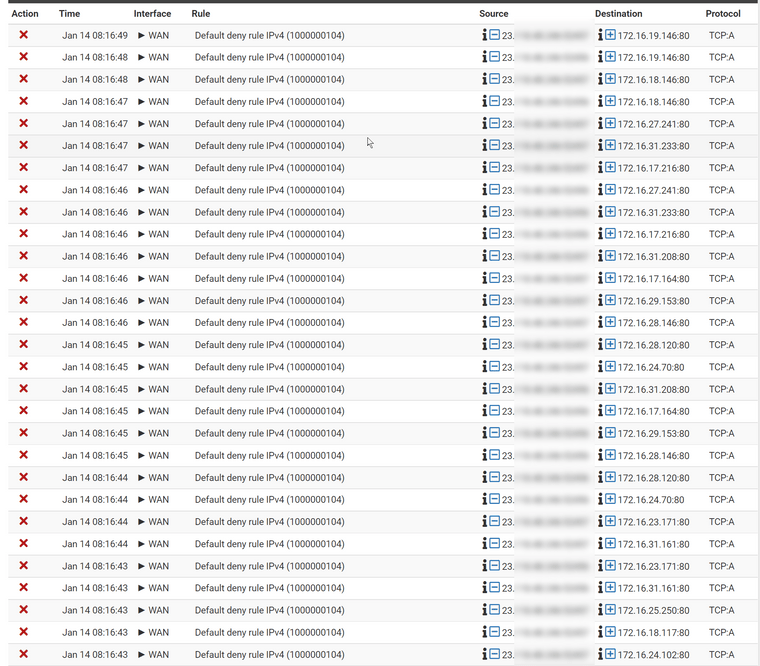
I tried to scan 172.16.0.0/16, but I'm doubly blocked by both the ATT gateway and pfsense
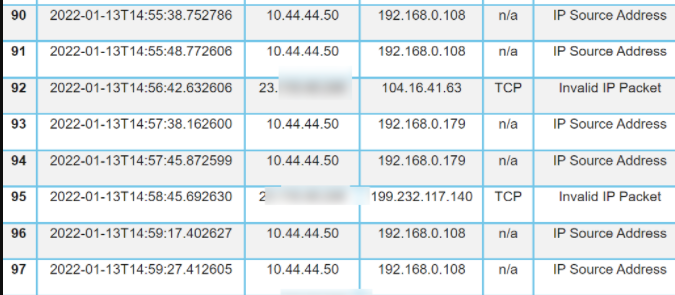
Finally, not sure if related or not, but my laptop's private address somehow is appearing in the logs of the ATT gateway.
-
Yeah, it looks like you have some alternative route happening somehow. Laptop connected with wifi and ethernet maybe.
The blocked ACK traffic on LANN in the pfSense log implies it has not seen the preceding SA and possibly not the S either.
The 23.x.x.x is the pfSense WAN IP I assume? The AT&T device is using a different public IP?
The permission denied could be from the AT&T router responding with that.Where is 172.16.224.109?
The AT&T device should never see traffic from the pfSense internal subnet unless you have something preventing outbound NAT for some traffic. It really looks like you have some second route between the laptop and the AT&T device that bypasses pfSense.
Run a pcap and see what traffic is actually passing pfSense when you see this.
Steve
-
@stephenw10 There's not an alternative route that I can see from laptop to pfSense. Not connected via anything but the access point.
Yes 23.x.x.x is the WAN IP passed through to pfSense.
I ran a pcap on pfsense WAN as pfsense scans 172.16.0.0/13 and is generating TCP:A blocks outbound on WAN in the firewall logs.
I look at a blocked TCP:A outbound entry timestamped 15:29:00 within the firewall logs, and filter for that destination in Wireshark. (ip.addr==172.16.56.89). I do not see any traffic to or from any of the destination IPs shown in the firewall logs.
Edit: Where is 172.16.224.109?
I don't know, it's not something that I've provisioned and well outside my address ranges. I use 172.16.0.0/24 for guest wifi access and that's not seen activity in some time. I saw that address in the AT&T gateway logs and was curious for this reason. AT&T gateway has everything related to firewalling and packet filtering disabled yet it was showing reason: filtering.
-
B Boethius referenced this topic on