allow traffic all traffic to and from port 80
-
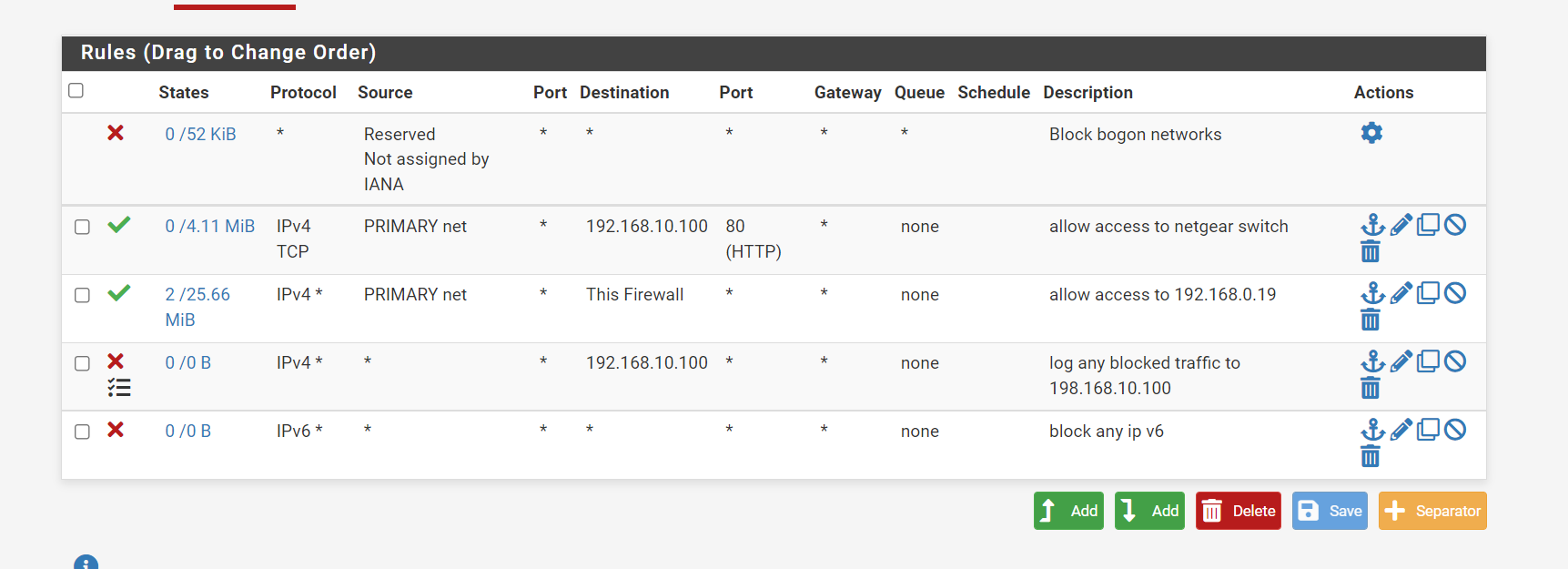
I'm a little lost with my rule set ? , I guess the rules should work top down , starting from the top working down .
1 rule allow TCP , source ( my switch ip ) , port 80 , destination , all any's
below
2 block and log TCP , source ( my switch ip ) , port 80 , destination , all any'sSo is allowing it and blocking it ?
Jan 17 13:15:58 LAN log any blocked traffic from 198.168.10.100 (1641677648) 192.168.10.100:80 192.168.0.4:52560 TCP:A Jan 17 13:15:58 LAN log any blocked traffic from 198.168.10.100 (1641677648) 192.168.10.100:80 192.168.0.4:52550 TCP:FPA Jan 17 13:15:58 LAN log any blocked traffic from 198.168.10.100 (1641677648) 192.168.10.100:80 192.168.0.4:52559 TCP:FPA Jan 17 13:15:58 LAN log any blocked traffic from 198.168.10.100 (1641677648) 192.168.10.100:80 192.168.0.4:52561 TCP:A Jan 17 13:15:58 LAN log any blocked traffic from 198.168.10.100 (1641677648) 192.168.10.100:80 192.168.0.4:52551 TCP:FPA -
@peter247 that is out of state traffic.. notice the A and FPA (which is a fin,ack)
Are you trying to do routing at this switch? That is return traffic your source is port 80, but it sent traffic to pfsense IP 192.168.0.4? Or was trying to route back through pfsense, when pfsense never saw the syn to open the state.
Could you provide some details of how you have your network configured, what networks how its all connected together.. That traffic is out of state, so either its asymmetrical traffic flow, or your states got reset.
edit: Why are you blocking bogon on a what I assume is lan side network?
-
@johnpoz Sorry , you can call me new to pfsense , trying to have 2 lans and route between them. primary my main lan on the same sub net as my router and 192.168.10.x which I want to use for cctv camera on it's own sub net.
So it is very much learning by allowing all traffic to and from a ip address , seeing what's being passed and allowing what looks o.k and blocking the rest.
So if you think WHY are you doing this easy , because I don't know any different , I am always open to a you should do this ?. -
@peter247 if you have 2 networks on pfsense
its pretty impossible to have out of state traffic, unless your states were killed..
How you have it connected together would be helpful. You can't just run multiple networks over the same L2..
Also in what scenario would bogons ever be source of traffic into any of your lan side interface. Blocking bogon on anything other than a wan side public interface makes no sense. And could be problematic since for example rfc1918 is included in bogon along with 0.0.0.0/8 etc..
-
@johnpoz Before I start thank you .
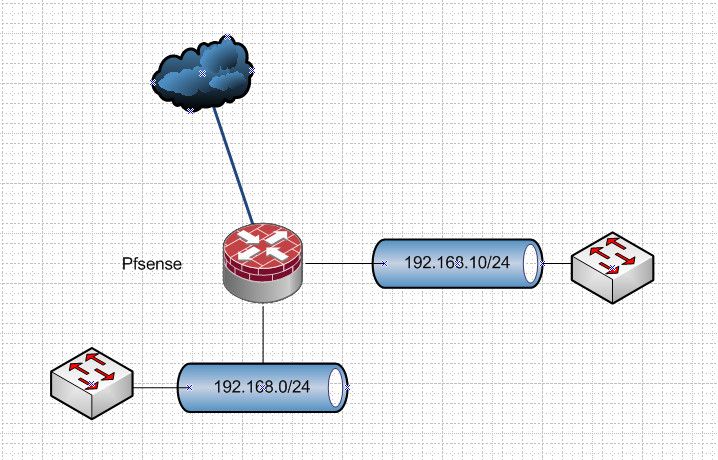
I'm not using pfsense as a direct connection to my internet.
I'm using a normal domestic router with routing to the 196.168.10.x network , I'm just using pfsense to routing to the other lan camera network .
So I guess you internet cloud should be connected to the 192.168.0.0 network directly and not to pfsense , because if the 192.168.10.x wants access to the internet it need to go through pfsense gateway, but 192.168.0.x as direct access to the router's gateway.
Now I know that it's ack and fin I can just add it to the o.k list to pass. -
@peter247 said in allow traffic all traffic to and from port 80:
normal domestic router with routing to the 196.168.10.x network , I'm just using pfsense to routing to the other lan camera network .
Yeah that just SCREAMS asymmetrical to me.. your typical soho router is not really capable of any routing.. Sure it might allow you to put in a route, but since it can not have more than 1 network its just going to provide a icmp redirect message for anything trying to go there.
Without connecting routers via a transit network (no hosts on this network) you are almost always going to run into asymmetrical flow, unless you do natting of downstream network and use port forwarding to access stuff behind the downstream router, or you do host routing on each hosts in the "transit" network..
I can just add it to the o.k list to pass.
No that does not fix the problem at all..
-
@johnpoz So if I have you right , what you are saying I need 3 networks / subnets , Wan , lan1 , lan2 , so lan1 could talk to lan2 and not to using the wan router as a loop back for the other subnet ?.
-
@peter247 when connecting routers there really should be a transit network (no hosts on this network) this prevents asymmetrical flow that can happen when you talk to devices that sit on the network between routers..
I have gone over this countless times... Here is old post with some drawings explaining the problem.
https://forum.netgate.com/post/865509
If you only have 1 router, pfsense and your networks all are connected to pfsense - then you don't have asymmetrical flow as long as these devices can not talk to each other in some other way that does not flow through pfsense.