Recommended public DNS over TLS
-
Hi,
I'd like to use DNS over TLS and wonder what services would you recommend and why?
Thx
-
@furom said in Recommended public DNS over TLS:
I'd like to use DNS over TLS and wonder what services would you recommend and why?
The TLS in "DNS over TLS" means the owner of the DNS can't be public. Beause running a public DNS is very expensive - adding an extra TLS layer in front of it x folds the costs for keeping that thing running.
So, sorry, no, you have to chose a "fortune 500" company that runs a freely accessible TLS resolver.
Even when you asks :
You get a first direct hit as an answer that says :
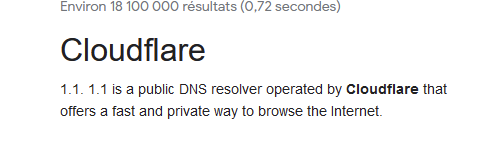
and that strange ..... they use the word Public and Cloudfare in one phrase.
Try walking into Cloudfare's main company's build, listen, smell and look : I'm pretty sure you will have this impression that it is NOT a public building.
Take note : the security agent are not the local police for, but private agents ...I think 'free accessible for everybody' is what they meant.
The usual conditions apply : you use a service without financial compensation. This means the payment, because there have to be one, is the data you send to them.If "public DNS servers" exist, then it should be them : https://en.wikipedia.org/wiki/Root_name_server
But they don't do TLS, they can't afford to do so. And I somewhat agree, as "they" would raise my and your taxes again.IMHO : DNS is fine as it is. Ones every year or so, I capture for a week or so all my DNS "port 53" traffic, and see it there was any traffic that I didn't want to go out to the public network, also called the Internet. Didn't find anything.
So, without surprise, I don't recommend using DNS over TLS. This recommendation is valid only if you do what I do : I don't care that something or some one knows I visited google.com - or duckdyckgo.tld or wikipedia.org or my bank or whatever. The simple fact that I visited is actually a far worse "private data security breach".
Or istagram - or facebook - and I could name them all. It's not the fact you ask : "where is google" ? It's what you do with 'twitter' when you got their IP, the interaction with that server.In case of doubt :
Stop using the Internet all together. The Internet is a society thing, and we, as a member of that society, using society assets, are subjected to the society rules. Like using a car on the road, or using your phone.
Or go for the onion browser (dark net) or something like that.
And don't stop with that thin foil hat, cover yourself completely.
If you don't want your private 'behind your front door' stuff goes out to the public, keep the front door closed while your discussing things in your home. When you're outside, or use out side facilities, keep your *@&¤ shut, and leave no traces.Assure me please : I didn't tell anything new here, right ? :)
My writing was of course not really entirely my opinion - it just wanted to make a point, as I'm seeing more and more pure concentrated BS these days. People have all the tools and time to document themselves, but the contrary seems to happen.
So, be careful, I might be wrong.Btw : If there was a good, free TLS ready DNS resolver available, it would have been build into pfSense as a 'DNS' choice.
You don't need an upstream resolver : pfSense comes with a resolver. -
@gertjan said in Recommended public DNS over TLS:
I don't care that something or some one knows I visited google.com - or duckdyckgo.tld or wikipedia.org or my bank or whatever.
To expound on this - just because you hide your dns request from your isp. Your isp, still would see the sni, which is in the clear, encrypted sni has been talked about for years.. the esni protocol is dead, long live ech (encrypted client hello).. But this is no where closer to becoming a real thing any time soon either. And its use would require all sites that run https to configure and support it..
So your isp still can see the fqdn your going to anyway, even with your https, and even if that was encrypted - they still would know what IP your going to.. While it might be some CDN that hosts a shit ton of stuff, so it really could be any of what they host.. It still gives them a bunch of info..
Until such time that ech/esni becomes a wide spread thing.. Hiding your dns provides nothing really, other than just handing your dns traffic over to some 3rd party on a silver platter.
-
I knew I wouldn't be dissapointed in the answer... Or, well, I learned a lot from this. I actually thought there was more to gain, but if my ISP can see it, it's still better than freely available to anyone. But I get the point. Thanks! :)
-
@furom said in Recommended public DNS over TLS:
it's still better than freely available to anyone
Who exactly do you think this anyone would be? Who would be sniffing your traffic either locally or on your isp network? Or even on the public internet?
When you resolve - you would be going to to all the authoritative ns for the domains you go to.. Or this who your talking to would have to be in line with your traffic flow to the roots.. Which is going to change depending on which root or tld servers your talking to, and then again when you talk to the authoritative for the domain in question.. So this who would really have to be real close to the source of your traffic.. Pretty much your isp, etc..
If your concerned with the roots and tld servers - you could setup Query Name Minimization, this would only send the roots and tld server the info your looking for, ie the NS for say .com or .net, etc. Then when you ask the tld ns for the domain, you would only send them say domain.net vs host.domain.net, etc.
Keep in mind, that once you talk to roots and learn the tld servers for say .org, you don't go ask roots again for .org anything until the cache has expired.. Same goes for the tld servers, once you ask them for domain.org, you never go ask them again for www.domain.org or ftp.domain.org or whatever.domain.org until that cache expires, etc.
So even when you send the fqdn to roots or the tld servers - your only really going to send them a small fraction of that actual amount of fqdns your going to be looking, just 1 to get the NSes your looking for that thing.. So while you might send www.something.org to roots, any other .org you look for would never go to roots, but only to the tld servers. Until the cache of the .org tld NS expire.