Directing outbound traffic
-
@pfsense1921 hm, I thought that were 3 different ISPs.. So you have a /29 in your WAN, and pfsense is getting 3 IPs from the same subnet in WAN0, WAN1 and WAN2?
Check if this can help you:
https://docs.netgate.com/pfsense/en/latest/firewall/additional-ip-addresses.htmlIf this can't help you, unfortunately we will have to wait for someone else to help you because I don't have experience with AT&T..
-
-
@pfsense1921
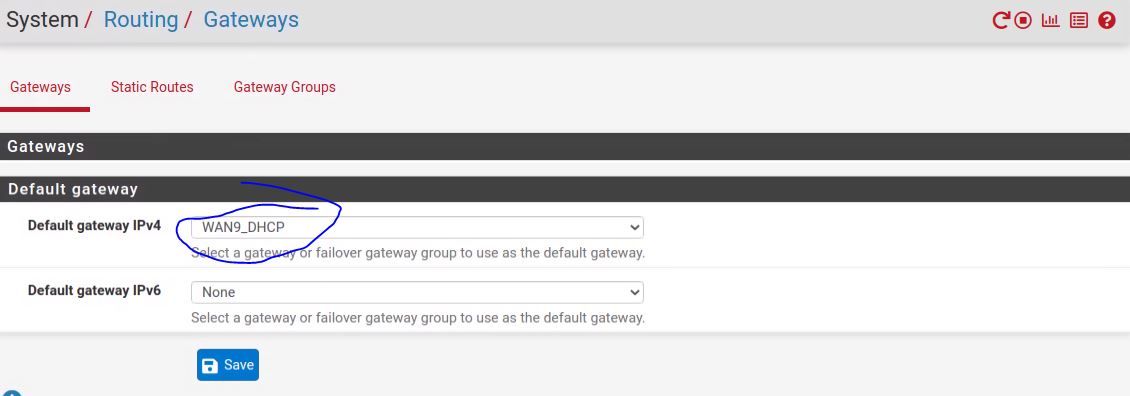
Setting default gateway to none, that did not fix it, not 100%. it improved some things, but not all.If I connect a pc directly up to the ATT ports where WAN1 and WAN2 ports are connected. When I check "whatismyip" from that PC they come back with the ip address for WAN1 and WAN2 like we expect.
When I connect the M400 with Pfsense to those WAN as previously described, PC on those LAN checking whatismyip still show WAN0 ip.
I am sure this is a simple setting I am missing. I can post all the settings if someone is interested. Thanks
-
@pfsense1921
So are all your WANs using the same common gateway?
If so, policy routing won't work, cause it's based on the gateway.You need to configure the outbound NAT to translate the source address in outgoing packets as desired.
If you outbound NAT is working in automatic mode, switch to hybrid mode first and save that. Then add a new rule to the top:
interface: outgoing WAN
protocol: any
source: LAN1 net
dest: any
translation address: select the WAN1 address from the drop-down
This requires, that WAN1 is already assigned to the interface. If not, you can select "other" and enter the IP below with a /32 mask. -
@viragomann
That option for the source was not available. Also, when I choose Hybrid with auto it made rules to allow everything everywhere so I made it all manual. I got more to work, but still have one strange issue. I am temporarily going to post all my details. (There is nothing on these networks yet, but don't think I am sharing any security details.)So, From the diagram linked to below, LAN_Email <--> WAN10 I can ping everywhere, ping www.google.com success. But I can not browse anywhere from any pc. (I can move that PC to LAN_office and LAN_web and everything works. )
To me this says I have some setting wrong in pfsense. The link below has many screenshots of my pfsense config. I am sure I am missing something simple. I have reset states and rebooted several times. Thanks for your help, I just can not find the issue.
http://salesleads.live/zup/network.pdf
-
@pfsense1921
The outbound NAT rules don't allow anything, they only do S-NAT (masquerading) on traffic that is allowed by your firewall rules.When you run it in hybrid mode, you can add custom rules, while you keep the automatic rules. Custom rules which match to the same traffic overrides the automatically generated.
From the diagram linked to below
Maybe you want to hide your WAN IPs.
LAN_Email <--> WAN10 I can ping everywhere, ping www.google.com success. But I can not browse anywhere from any pc. (I can move that PC to LAN_office and LAN_web and everything works. )
You need to allow DNS access for this devices. The rules on the interface only allow HTTP and HTTPS.
You have also to obey this when you add a policy routing rule to allow any, but your devices are configured to use pfSense or any other internal DNS. @mcury mentioned this already above.
I set up a floating rule to aim this with a single rule on all interfaces.
-
@viragomann
Thank You (Plan to remove the file soon)I will add the DNS now, the other LANs work without the DNS listed
LAN_Office <--> WAN9 works no DNS listed
LAN_Web <--> WAN11 works no DNS listedLAN_Email <--> WAN10 Not working no DNS listed.
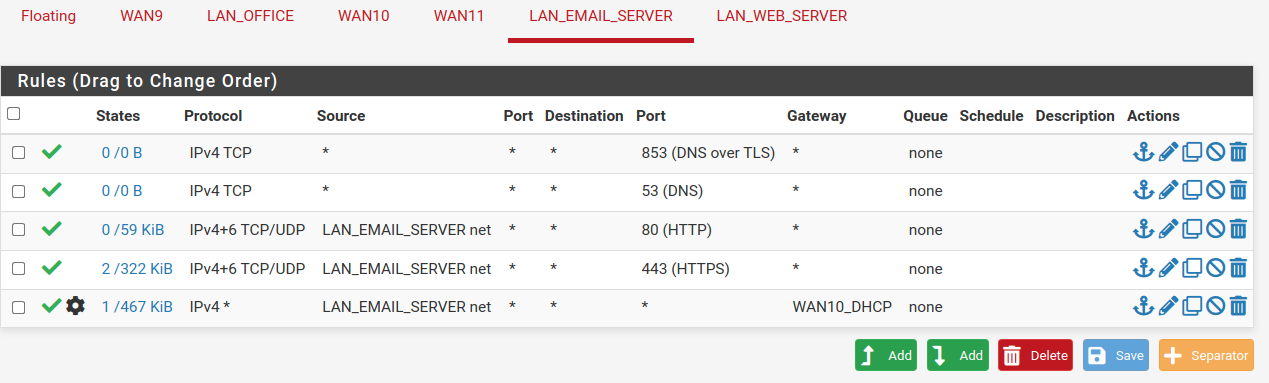
Added DNS
LAN_Email <--> WAN10 Not working with DNS listed.
Here was how I added DNS:
-
@pfsense1921 said in Directing outbound traffic:
@viragomann
Thank You (Plan to remove the file soon)I will add the DNS now, the other LANs work without the DNS listed
LAN_Office <--> WAN9 works no DNS listed
LAN_Web <--> WAN11 works no DNS listedLAN_Email <--> WAN10 Not working no DNS listed.
Added DNS
LAN_Email <--> WAN10 Not working with DNS listed.
Here was how I added DNS:

DNS/53 should be TCP/UDP, 99,99% of times it will use UDP, but sometimes it can use TCP.
-
@pfsense1921
The LAN_Office and LAN_Web can ping everywhere and browse internetThe LAN_Email can ping everywhere but Not browse internet
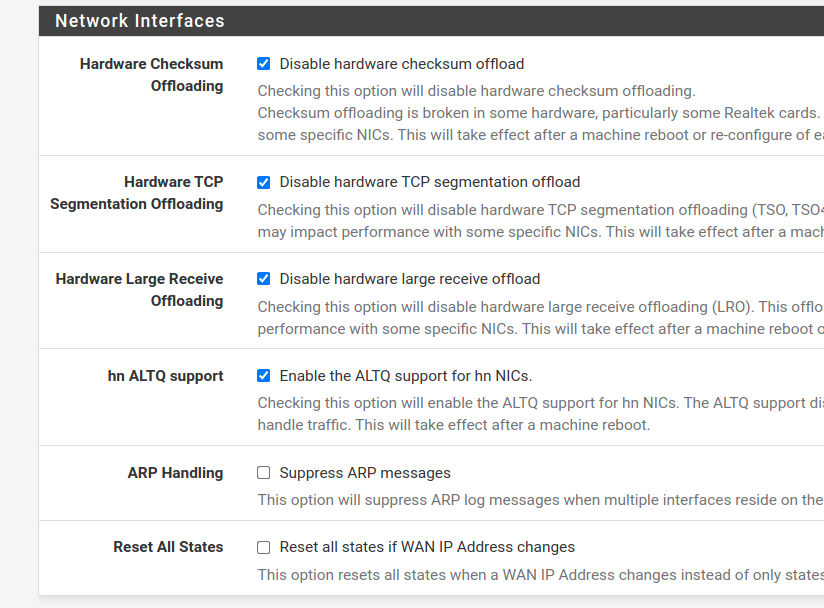
Also disabled the offloading:
-
@mcury
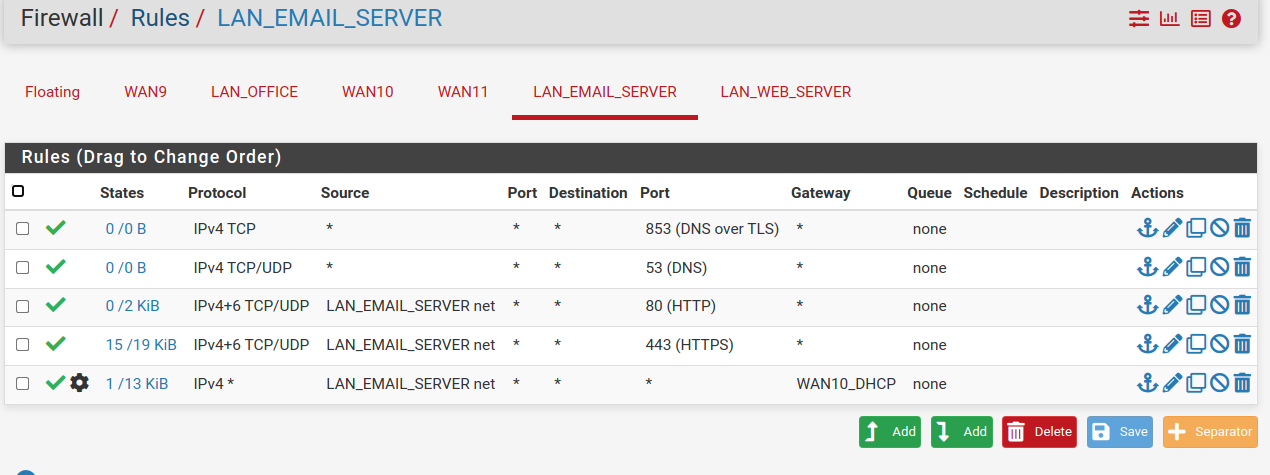
Thanks. Made the change, still did not work. Here is how it is now:
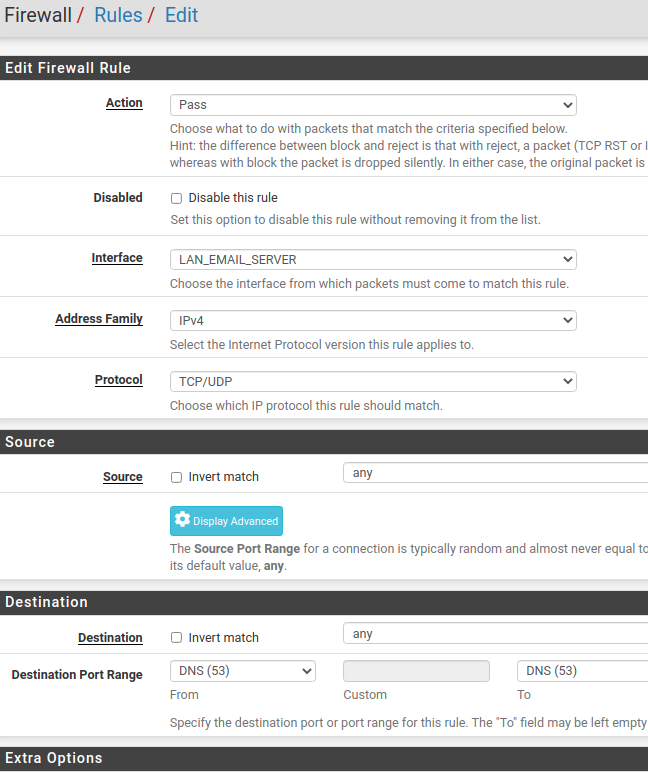
-
Open a prompt MS DOS in a machine from the LAN_Email network.
Type nslookup press enter, then google.com and press enter and confirm if DNS is working. -
@mcury
It looks like it works, (Does "ping www.google.com" provide a similar test of dns?)
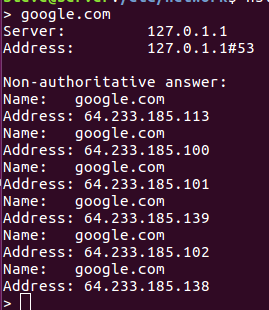
I can move the PC from lan_email to either lan_web or lan_office and browsing works.
And vice versa, no browsing on lan_email. I feel like deleting everything and starting over which would probably be faster, but now I want to learn what the problem is.Thanks for the help.
-
Very Odd this is. I can not pin point where the problem is.
IF, I only connect one WAN to pfsense, the corresponding LAN works.
I can do this with any WAN, All three LAN work, but only one at a time.
(Tested with all 3 static IP, and moved them around)IF I connect two WAN, the two corresponding LANs work perfect.
Again, I can do this with any combo of two WANEverything seems to be working properly. IF your corresponding WAN is not connected, you can Not ping outside your LAN.
Now, when I connect the third LAN everything goes to crap. I loose one LAN and sometimes two LAN.
How would I prove/find if the problem is with pfsense OR ATT. I have 5 public static IP addresses, I am only using 3. Those tests can prove that both systems are working, neither can prove which one is having the problem. Something is crapping when all 3 LAN are connected.
-
@pfsense1921
Your basic mistake is, that you have configured multiple WAN interfaces, which are all within the same subnet.
Routing doesn’t work this way.
You have to add all WAN IPs to a single interface. -
@pfsense1921 said in Directing outbound traffic:
It looks like it works, (Does "ping www.google.com" provide a similar test of dns?)
Yes, its the same thing..
@viragomann said in Directing outbound traffic:
Your basic mistake is, that you have configured multiple WAN interfaces, which are all within the same subnet.
Routing doesn’t work this way.
You have to add all WAN IPs to a single interface.I would be on it, I would like to know how he was able to configure three interfaces in the same subnet, I suppose this is not possible, he is probably using a /32 mask ?
-
@mcury
Yes, pfSense will throw overlapping networks errors, when doing this.
With a /32 musk it's possible. But I'm not sure if you can add the same gateway to multiple interface, even if one has the /29 mask. -
@viragomann said in Directing outbound traffic:
But I'm not sure if you can add the same gateway to multiple interface, even if one has the /29 mask.
He should be using only one WAN interface, getting the entire /29 subnet and using virtual IPs..
-
@mcury said in Directing outbound traffic:
He should be using only one WAN interface, getting the entire /29 subnet and using virtual IPs..
Yes, since he has only a single WAN gateway, that's the only option.
Routing is based on gateways, hence with the same gateway on multiple WAN interfaces any upstream packet can go out on any WAN interface and the outbound NAT rules will not work.
-
Hello,
Based upon what was said previously, In Theory:
Would the M400 with pfsense work like I am trying with 3 different ISP Providers?I apologize that my lack of understanding is making this a painful discussion for you. This is obviously far from a standard 1 WAN / 1LAN setup.
Thanks for trying to help me.So, AFAIK, on my ATT service I have 4 different static Public IP addresses, I can route traffic to the public internet, independently on each port.
I am only using 3.I am trying to do this:
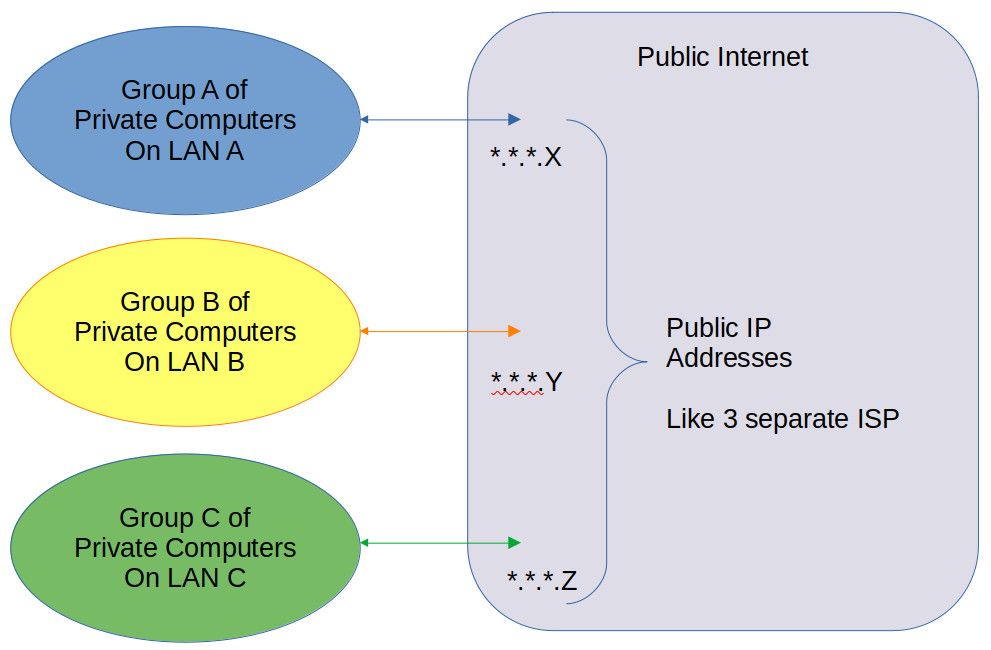
Not This:
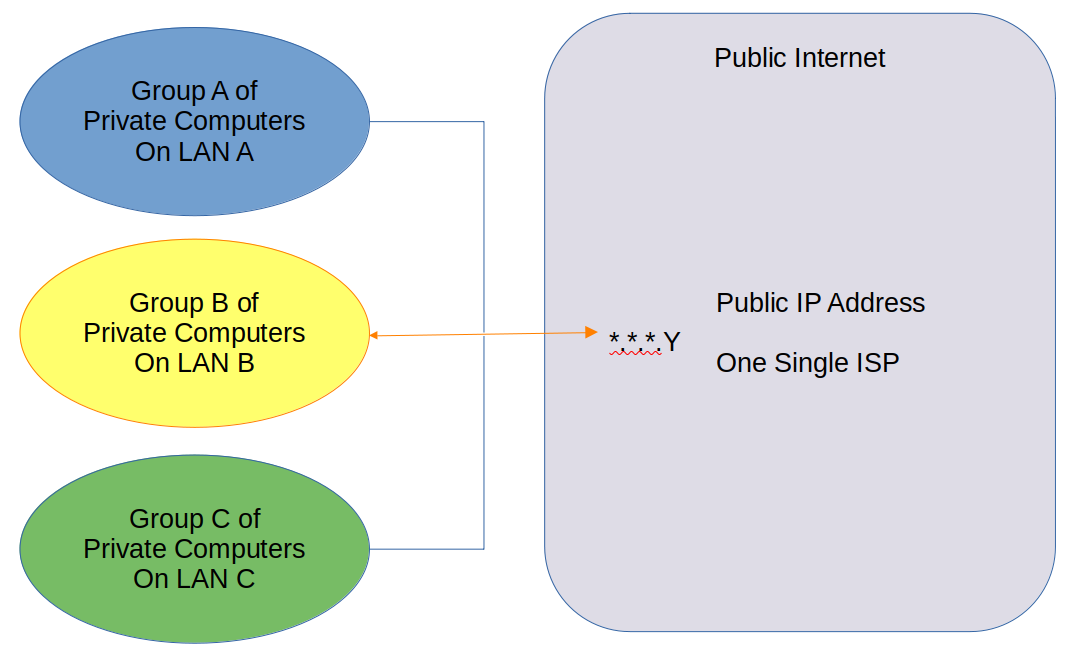
Attached below is my ATT modem.
Each one of the four yellow ports have individual public IP addresses.
Imagine as 4 different ISP, I am only trying to use 3.
I have verified that each port works like its own separate ISP.
(One test, I connected a PC directly to the port and "Whatsmyip" all said the public IP address for that port)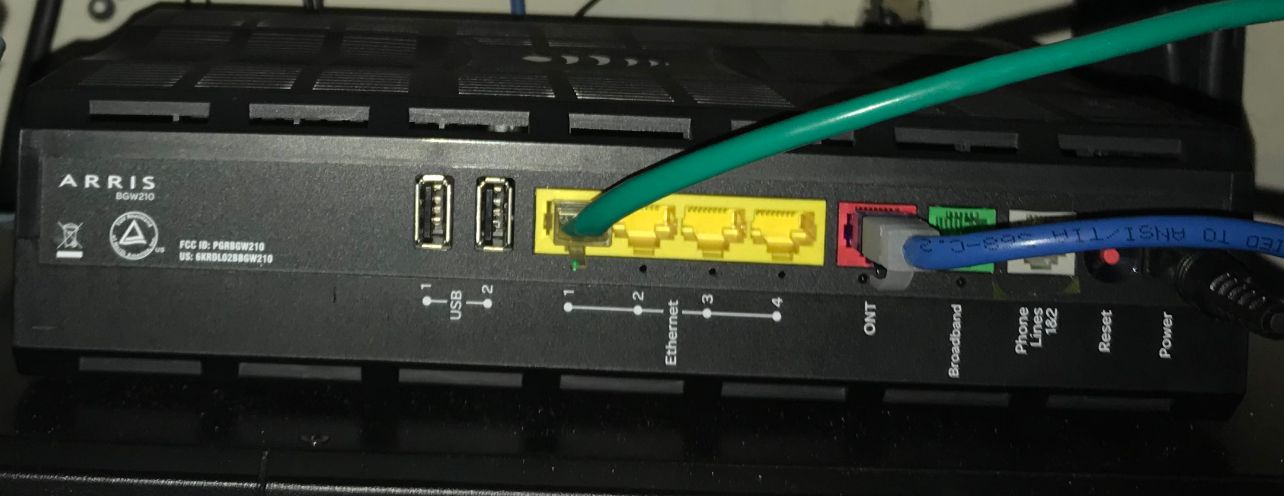
This last paragraph is me crying for help with the questions flying around inside my head. The best way for me to learn is to understand how to get from where I am to where you are. So I am sharing where I am

I do understand that my public IP addresses are on the same subnet, and they all use the same public gateway ( .14) - for the 4 IP addresses. (the addresses are public and not .14)
Prior Statement that I must use only one WAN because those IP addresses use the same One Gateway. Does that mean that every ISP with a public address would require its own separate gateway? And the gateway can not be shared with other ISPs? Soo, If two neighbors were using the same ISP Provider with public addresses on the same gateway, they would have to route thru the same WAN port on a firewall and not be able to use two different firewalls? Why is that different than what I am trying to do?I apologize if you had to read that last paragraph twice. Thanks for your help!
-
@pfsense1921 Try this:
Connect just one cable from ARRIS LAN1 to pfsense WAN0
If things are as I think they are, you will receive an IP like this: X.X.X.X/29 with the gateway X.X.X.14/29 as you stated.
Do not connect other ports from ARRIS to pfsense.Then create virtual IP, selecting IP Alias, WAN, Single address, put the IP and MASK accordingly, do not repeat the same IP that your pfsense WAN has, put the next one on the sequence.
Then change your NAT rule to hibrid, create a NAT OUTBOUND like this:
Interface WAN
Address Family: IPv4
Protocol any
Source network: GROUP B of computers: Destination: ANY
Destination any
Translation: Select the virtual IP address you created aboveThen test and come here to tell us if it worked.
I suppose this video is perfect for you:
Youtube VideoEdit: One observation here is that in the video he is doing a portforward, you will do Outbound ok? So that step is different.